Network security architecture is a strategy that provides formal processes to design robust and secure networks. Effective implementation improves data throughput, system reliability, and overall security for any organization. This article explores network security architecture components, goals, best practices, frameworks, implementation, and benefits as well as where you can learn more about network security architecture.
Table of Contents
Components of Network Security Architecture
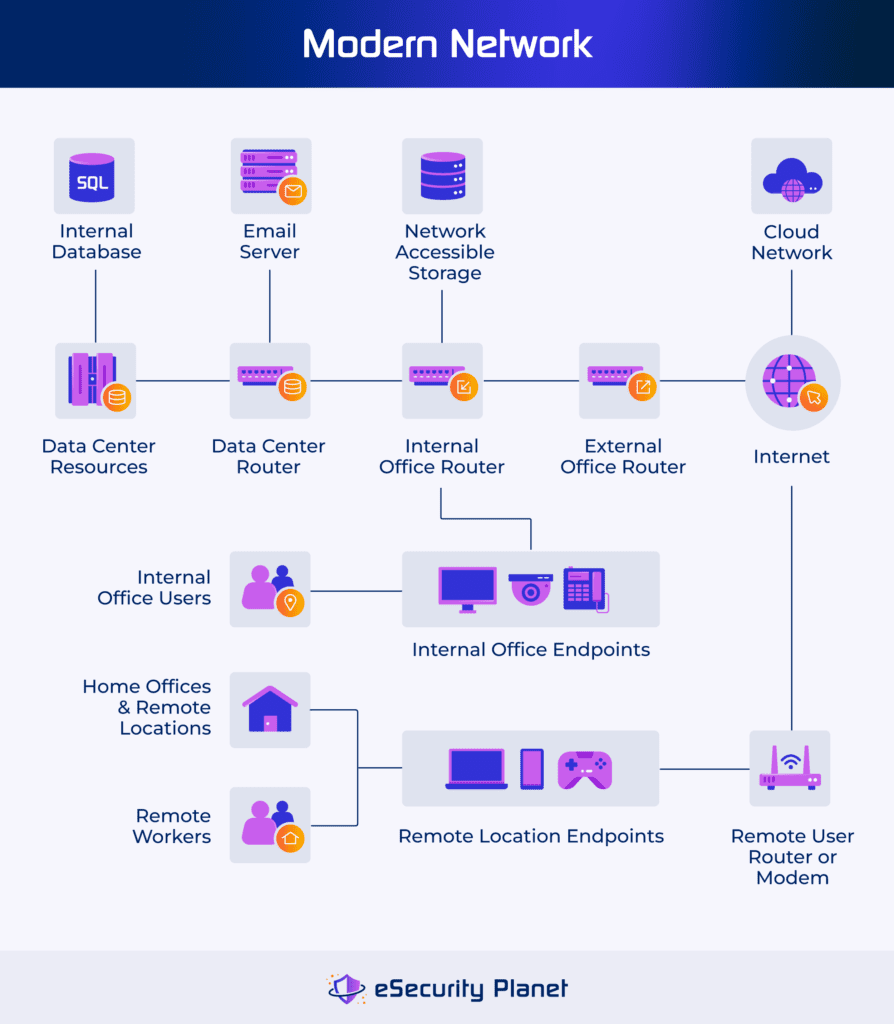
The fundamental components of network security architecture consist of the core network elements, the security elements to protect them, and related security elements.
Network Elements
Networks connect physical and virtual assets and control the data flow between them. The basic elements of a fundamental network include:
- Network equipment: Controls data flow between devices and commonly includes physical and virtual switches, wired or wireless routers, modems, and hubs.
- Server: Provides powerful computing and storage in local, cloud, and data center networks to run services (Active Directory, DNS, email, databases, apps).
- Endpoint: Enables access for human users and computer services and commonly includes PCs, laptops, Internet of Things (IoT), and operational technology (OT).
- Storage: Contains user and application data at rest; can be integrated with other elements (server, etc.) or segregated as cloud or network attached storage (NAS).
- Cloud infrastructure: Consists of the virtualized versions of network components that reside in as-a-service environments (software, platform, infrastructure).
- User, service, and application: Connects to the network via endpoints and then connects through network connections to other network assets and data.
Security Elements
Security elements protect each component of the network, network access, and the data transmissions. Security elements include defenses against unauthorized entry (perimeter defense and access control), techniques to misdirect attackers (obfuscation defense), and specialized controls for specific assets (services, clouds, applications, virtual assets, endpoints, and networks).
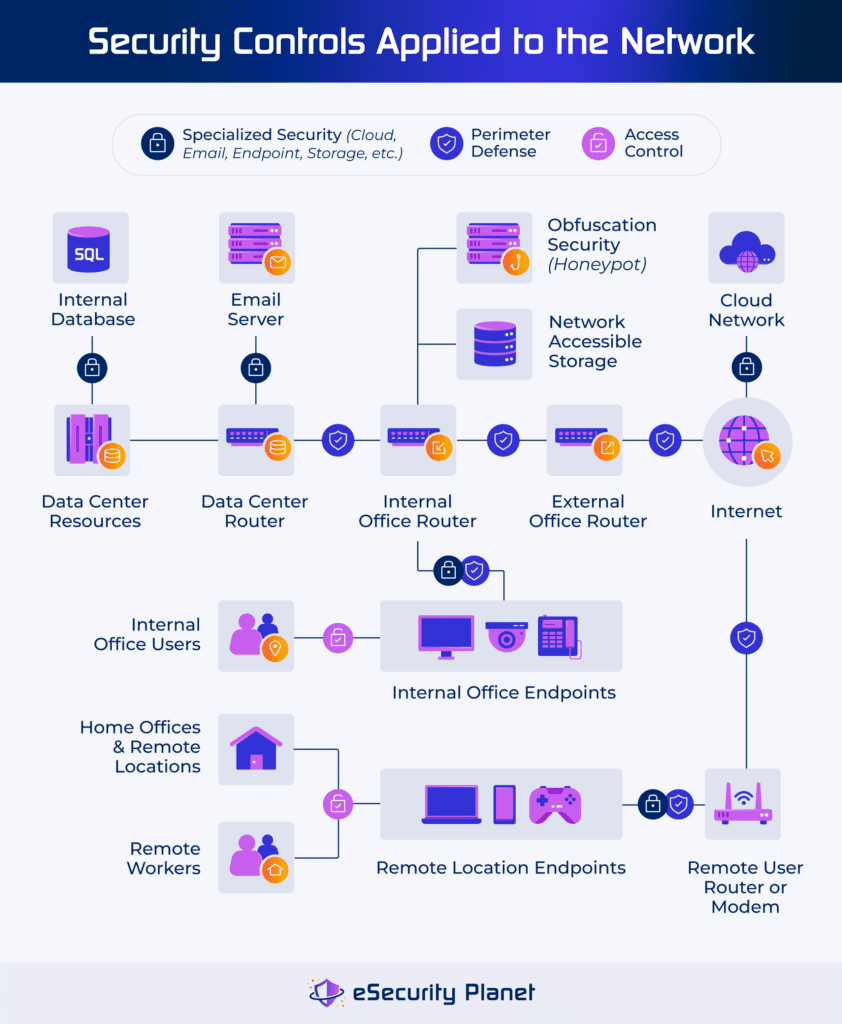
Perimeter Defense
Perimeter defense blocks threats at the network’s edge. Traditionally, this technology implicitly distrusts external traffic and implicitly trusts internal traffic. Zero trust technology also acts as a perimeter defense, but it applies for each asset separately without any implicit trust for any traffic or connection. Perimeter security tools include:
- Firewalls: Filter traffic and monitor access based upon firewall rules and policies for the network, network segment, or assets protected by different types of firewalls.
- Next-generation firewalls (NGFWs): Improve the general security of a firewall with advanced packet analysis capabilities to block malware and known-malicious sites.
- Firewall-as-a-service (FWaaS): Deploys cloud-hosted and scalable protection enterprise-wide for all resources (networks, branch offices, remote users, etc.).
- Network security policy management (NSPM): Centralizes control and management of policies to be enforced across network firewalls, routers, and other equipment.
- Unified threat management (UTM): Consolidates multiple perimeter and application security functions into an appliance suitable for small and mid-sized enterprises (SME).
Access Control
Access controls add additional authentication and authorization controls to verify users, systems, and applications to define their access. These controls include:
- Active Directory (AD): Manages users, groups, and passwords as a fundamental access control for an organization and the basis for most other security tools.
- Identity access management (IAM): Simplifies, centralizes, and expands abilities to manage AD and other lightweight directory access protocol (LDAP) tools.
- Multi-factor authentication (MFA): Uses at least two (2FA) or more methods to authenticate a user, such as biometrics, device certificates, or authenticator apps.
- Network access control (NAC): Inspects and can quarantine devices prior to permitting access to the network for signs of compromise, missing patches, and other issues.
- Privilege access management (PAM): Provides a specialized form of IAM that controls access to privileged resources such as administrator credentials and sensitive systems.
- Virtual private networks (VPNs): Secure remote user or branch office access to network resources through encrypted connections to firewalls or server applications.
- Virtual desktop infrastructure (VDI): Replaces VPN or remote desktop access with virtual desktops in fully controlled environments with additional protections.
- Zero trust network access (ZTNA): Enables more granular levels of access to network assets based on users, locations, time of access, and asset requested.
Deception & Obfuscation Defenses
Deception and obfuscation techniques hide network assets from discovery, block exploration, or use decoys to trigger alerts. These techniques can use built-in software features (for firewalls, operating systems, etc.) or specialized tools to deliver obfuscation defenses such as:
- Honeypots: Provide tempting targets for attackers that contain no valid information as one of several similar deception technologies to trigger alerts for early attack detection.
- Port knocking: Closes ports for communication (including detection) until provided with a code using multiple specific packets or a special single-packet authorization (SPA).
- Proxies: Replace direct communication with a software or hardware intermediary that hides the discovery of assets (servers, endpoints, segments, etc.) behind the proxy.
Services Security
Services security applies to specialized controls for the system services within the network. Examples of services security include:
- AD security: Adds layers of security to Active Directory to eliminate unneeded access or permission levels, detect unauthorized changes, and block other attacks on AD.
- Communication protocols (TCP, HTTPS, etc.): Apply encryption protocols and other security measures to connections between computers.
- Dynamic Host Configuration Protocol (DHCP) snooping: Tracks IP addresses assigned to resources to detect untrusted devices and IP address spoofing.
- Domain name system (DNS) security: Protects the DNS service from attempts to corrupt DNS information used to access websites or to intercept DNS requests.
Cloud Security
Cloud security provides focused security tools and techniques to protect cloud resources. While many network security tools can be deployed in virtualized cloud environments, specialized tools provide tailored security functions such as:
- Cloud access security broker (CASB): Replaces direct logins to cloud-hosted resources with a single, protected CASB access to mitigate leaked credential threats.
- Cloud firewalls: Implement cloud-based firewalls to protect the cloud-based networks in infrastructure-as-a-service (IaaS) or platform-as-a-service (PaaS) environments.
- Cloud infrastructure entitlement management (CIEM): Manages compliance, risk, and security with controlled user, system, and app cloud resource access.
- Cloud native application protection (CNAP) platforms: Secure applications and cloud resources with cloud-native and integrated security.
- Cloud security posture management (CSPM): Finds gaps and misconfigurations, secures access, and enforces compliance policies in deployed cloud environments.
- Cloud workload protection platforms (CWPPs): Monitor and secure applications, app components (databases, etc.), and app infrastructure (containers, etc.) in the cloud.
- Secure access service edge (SASE): Combines software-defined wide area network (SD-WAN) network controls with security controls for local, remote, and cloud assets.
- Secure service edge (SSE): Applies security controls to local, remote, and cloud assets to extend robust security protection and monitoring beyond the local network.
Application Security
Application security focuses on protecting the applications within local, data center, and cloud-based networks. These tools include:
- Application programming interface (API) security: Secures the connections between applications by inspecting API connection requests and communication.
- Database firewall: Inspects traffic to databases, blocks unauthorized access, and provides specialized defenses against database attacks.
- Database security: Applies a variety of security controls specialized to protect database access, data integrity, and specialized database attacks.
- Email security: Detects viruses or attacks hidden in emails and attachments, blocks SPAM, or authenticates emails that originate from an organization.
- Secure email gateway (SEG): Deploys as a physical or virtual appliance with specialized inspection and security features for emails and attachments.
- Secure web gateways (SWGs): Provide consolidated protection for networks and users to access emails, connect to SaaS or cloud resources, or browse websites.
- Web application firewall (WAF): Provides application-layer protection for websites and apps to block specialized attacks and unauthorized access.
Virtualized Security
Virtualized security tools protect virtual environments or create virtualized environments to protect physical assets. Examples include:
- Browser isolation: Creates virtualized containers on an endpoint to isolate the browser contents, including potential malware attacks, from the physical endpoint environment.
- Container firewalls: Deploy with code to protect on-demand access and monitor communication to containers and their contents.
- Container security: Protects containers from attack using a variety of threat detection, vulnerability scanning, traffic monitoring, and incident response capabilities.
- Sandboxing: Generates a virtual desktop environment with enhanced security to launch suspicious files to test for malware or to observe malware behavior.
- SD-WAN: Uses software to create virtual networks, network segments, and even microsegmentation independent of the physical networks and locations.
- Virtual desktop infrastructure (VDI): Provides virtual desktop infrastructure or VDI-as-a-service (VDaaS) for fully isolated and controlled remote user access.
Endpoint Security
Endpoint security protects the physical and virtual endpoints connected to the network. The security controls include:
- Antivirus (AV): Scans for malware based on a database of known-malicious file signatures to provide basic defense against common attacks.
- Device management: Maintains minimum levels of security and controls apps on remote devices through enterprise mobility management (EMM) and similar solutions.
- Endpoint detection and response (EDR): Provides more advanced security than AV with more intelligent analysis of endpoint activity and automated remediation.
- Endpoint protection platform (EPP): Enhances AV protection with verified indicators of compromise, memory monitoring, and other malware detection techniques.
- Host-based firewalls: Provide virtualized firewall protection on a specific device such as a router or within the operating system of an endpoint computer or server.
- Internet of Things (IoT) security: Encompasses a variety of tools and techniques to secure IoT, operations technology (OT), and other similar categories of endpoints.
Network Security
Network security tools monitor and secure the connections between assets on the network and protect against specific network attacks. These include:
- Distributed denial of service (DDoS) protection: Detects and controls DDoS attacks on networks designed to overload systems and deny access to resources.
- Intrusion detection systems (IDS): Inspect network packets for malicious activity and indicators of compromise to generate alerts for security teams.
- Intrusion protection systems (IPS/IDPS): Add automated packet block or quarantine to IDS for more proactive defense for network traffic.
- Network packet broker (NPB): Delivers automated packet monitoring to filter and distribute packets to improve load balancing, efficiency, and analysis.
- Network monitoring: Expands IDPS to connected devices to track behavior, traffic loads, and component health for operations issues as well as malicious activities.
- Segmentation or microsegmentation: Segregates networks to apply different permissions and access rules or to block attempts for lateral network exploration.
Related Security Elements
Related security elements don’t apply specifically to networks, but networks benefit from the application of these controls such as:
- Data loss protection (DLP): Detects potential exfiltration of sensitive data (regulated, personal, or corporate secrets) to generate alerts or proactively block attempts.
- Data protection: Protects against breach or theft using encryption tools, tokenization, or data masking techniques to render exposed data unreadable to outsiders.
- Disaster recovery: Implements redundancy and data backups to improve resilience from inevitable device failures, cybersecurity attacks, or natural disasters.
- IT security policies: Establish benchmarks, goals, and standards that can be used for measuring successful implementation of security controls.
- Governance, risk, and compliance (GRC) management: Aligns security goals with business goals and regulatory requirements that apply to the data or the organization.
- Monitoring and incident response: Detect and respond to attacks, device failure, and other incident categories to reduce negative impacts and accelerate recovery.
- Patch and vulnerability management: Apply maintenance principles to assets to prevent compromised security controls or inadvertent gaps in network security.
- Penetration testing: Tests security controls to verify correct implementation, detect vulnerabilities, and confirm adequate security controls for risk reduction goals.
- Threat intelligence feeds: Monitors vendor announcements and attacker behavior to update security tools or to inform security teams of the latest threats, targets, and trends.
- Cybersecurity training: Educates employees regarding basic best practices to recognize attacks, avoid scams, and protect against breaches or data loss.
The 6 Goals of Network Security Architecture
Network security architecture matches security elements to network elements in a rigorous and intentional manner based on the six key goals or principles focused on risk, data confidentiality, data integrity, data availability, effective controls, and measurable efforts.
Accept Reasonable & Appropriate Risk
The goal to accept reasonable and appropriate risk acknowledges that perfect security isn’t possible. Instead, invest reasonable budgets to implement security controls that reduce risk to acceptable levels based upon risk analysis and tolerance.
Enforce Data Confidentiality
The goal of data confidentiality protects data against unauthorized or inappropriate access. Limit access, secure transmissions, and protect data storage so that appropriate users can access the correct data only when needed.
Ensure Data Integrity
Data integrity focuses on maintaining unaltered data and only allowing intentional changes. To verify integrity, consistently check for unauthorized changes, including data corruption.
Maintain Data Availability
Data availability requires that data remains accessible when needed. This goal requires effective disaster recovery plans to recover corrupted data as well as scalability and redundancy of systems for continuous availability during high demand.
Implement Effective Controls
Effective controls require security measures that work as intended, consistently over time. Implement usable security controls that prevent bypass, circumvention, or tampering without compromising other network security architecture goals.
Apply Measurable Efforts
The goal of measurable efforts requires testable and verifiable security controls. To satisfy this control, conduct penetration tests to verify that established controls function as intended and to issue security status reports for compliance and stakeholder reporting purposes.
8 Best Practices for Secure Network Architecture
Network security architecture goals define what to do, but best practices offer guidance on how to implement those goals effectively. Best practices address one or more goals and will reinforce other best practices, starting with iterative planning. Others seek centralized control, employee training, defense in depth, efficient design, least privilege access, resilience, and testing.
Iterative Planning
Iterative planning addresses the goal to accept reasonable and appropriate risk. Tie plans to business objectives and risk to create verifiable key objectives and milestones. Future incidents and testing results inform future iterations for adjustments or additions to existing plans.
Centralized Control
Centralized control promotes data integrity and effective control goals through consistent security measures. Centralization to a small number of experts eliminates ad hoc and inconsistent security that introduces risk.
Cybersecurity Training
Cybersecurity training ensures effective controls throughout the organization. General employee training creates a security-oriented organization aware of key threats and trends. Specific training on security tools reduces barriers to adoption and improves their effectiveness.
Defense in Depth
Defense in depth assumes that any single security control may fail. Additional security layers implement effective controls and assure data confidentiality by adding additional insurance against breaches, zero day vulnerabilities, or tool failure.
Economic Design
Economic design improves the effectiveness of controls. Components of economic design include virtualization to maximize asset utilization, simplifying into easy-to-test components, and attack surface minimization.
Least Privilege Access
Least privilege access enforces data confidentiality through specified levels of access from non-privileged (public, DMZ) to most privileged (top secret). Least privilege should default to denial of access and functions should separate from the objects they act upon for granular access control. Similarly, resources should be segregated by security, with security controls applied between trust levels.
Resilience
Resilience, also known as disaster recovery planning, maintains data availability. Data backups and recovery processes are cited as key components of resilience, but resilience also requires redundancy of operations and security devices in case of failure.
Testing
Tests deliver measurable efforts through vulnerability scans, log analysis, or monitoring. The detection of corrupted data, device failure, or indicators of compromise will trigger incident response mechanisms to limit damage, recover the network, and provide information needed for iterative planning.
How to Create a Strong Network Security Architecture
Strong network security architecture applies security tools effectively to meet the needs of an organization in an iterative process of regular inspection and improvement. Start with the existing state of the organization for each best practice, determine the target state to be achieved, and prioritize improvements based on risk.
The best practices cover a range of basic and advanced options to satisfy evolving needs. The specific ‘best’ solution will vary because it’s fully dependent upon the specific network architecture in place, available resources, and appetite for risk.
Basic to Advanced Iterative Planning
Effective iterative planning balances operations goals, business risk, and security objectives in a written plan. Testing verifies objectives and incidents provide feedback for adjustments.
Basic iterative planning focuses on documenting existing controls and creating fundamental IT policies to document goals and objectives. Start with a risk register and draft a patch management or vulnerability management policy and build out from there.
Initial iterations for improvement can start annually, but quarterly or more frequently tends to be a more reasonable update cadence. In addition to scheduled updates, each security incident, control failure, and significant network change should trigger a review of existing policies, risk values, and plans.
Advanced iterative planning formally integrates risk registers or risk management tools into the process. Governance, risk, and compliance (GRC) tools help to prioritize the most valuable or the most damaging data and systems for additional layers of protection.
Basic to Advanced Centralized Control
Effective centralized control puts critical decisions into the hands of experts and delivers consistent results throughout the network and its attached assets.
Basic centralized control deploys management modules for network equipment and firewalls for centralized management of existing infrastructure. For ease of deployment and management, consider deploying cloud-based network-as-a-service (NaaS), firewall-as-a-service (FWaaS), or zero trust network access (ZTNA) services that provide centralized and managed infrastructure.
Advanced centralized control will manage local, remote, and cloud resources through unifying technology such as SD-WAN, SASE, or SSE. The most sophisticated organizations will also consider centralized and more granular zero trust implementations.
Basic to Advanced Cybersecurity Training
Effective cybersecurity training improves overall awareness of security threats and advances understanding and effectiveness of existing security controls. Cybersecurity training should apply equally to basic users and advanced security professionals and be tailored to their needs.
Basic cybersecurity training uses cybersecurity training courses to educate about common issues such as phishing and ransomware. IT team training ranges from basic tool training to cybersecurity certification. Threat feeds also fall under the basic cybersecurity training umbrella.
Advanced cybersecurity training utilizes more active training for security professionals and relevant non-security employees. Use table top exercises or simulated attacks (red, blue, or purple teaming) to gain valuable experience and test controls and processes under stress.
Basic to Advanced Defense in Depth
Effective defense in depth prevents any single point of failure through reinforcing security controls and increases the work for potential attackers. It also applies to people and procedures so highly sensitive tasks should require multiple people in order to mitigate insider threats.
Basic defense in depth applies multiple controls starting with key, high-value assets and adding others as budgets and time allow. For example, in addition to the existing security stack, a data center might add additional MFA, a web application firewall, and a honeypot.
Advanced defense in depth continues to explore and adopt additional layers of defense or more sophisticated defense throughout the network and related assets. For example, EDR might replace antivirus and SASE might replace non-integrated firewalls, CASB, and more.
Basic to Advanced Economic Design
Economic designs maximize the value of the components and minimize costs through simplicity. Reductions in attack surface similarly reduce monitoring costs and complexity. Additionally, economic designs boost operations data throughput to maintain high availability.
Basic economic designs often start with improvements to existing architecture. Examine existing controls, operations, and security processes for opportunities to gain time and reduce expenses through simplification and consolidation.
Advanced economic design may deploy automation (sometimes AI-powered) to improve speed and consistency. Cloud environments use code to efficiently deploy virtualized servers, containers, networks, and security controls at scale and on demand.
Basic to Advanced Least Privilege Access
Least privilege access prevents abuse of resources or data by granting only the minimum resources necessary for the user or application to perform expected tasks. They must also protect and monitor the tools that manage security levels.
Basic least privilege access requires assignment and regular maintenance of users, groups, apps, and API access. Apply Active Directory security tools to simplify maintenance and to monitor AD for unexpected or unauthorized changes.
Advanced least privilege access starts with IAM or PAM tools to manage access at scale. Zero trust implements a granular version of least privilege that requires explicit trust for each user, on each data request, and for each asset access.
Basic to Advanced Resilience
Effective resilience anticipates failure of systems, controls, or services and develops methods to maintain operations or to rapidly recover. This requirement also includes operations components (load balancers, etc.) that improve network performance and reduce system loads.
Basic resilience starts with data backups and redundancy for key components such as firewalls, routers, and data servers. Basic DDoS protection and load balancers also will be early controls applied to protect websites, application servers, and key networks.
Advanced resilience will backup more than just data (security settings, router configurations, etc.) and deploy disaster recovery solutions for more comprehensive and robust recovery. Add internal incident response teams to provide rapid response and accelerate recovery.
Basic to Advanced Testing
Effective testing verifies effective security controls, continuously monitors for failure, records system status, and generates reports. This provides detailed feedback for compliance audits, incident investigations, and improvements for iterative planning.
Basic testing starts with vulnerability scans, log analysis, and monitoring. Smaller teams may prefer to fully outsource to vulnerability management as a service (VMaaS), managed detection and response (MDR), or managed security services providers (MSSPs).
Advanced testing requires more rigorous penetration testing. Growing organizations may also adopt security information and event or monitoring (SIEM) solutions or security operations centers (SOCs) to manage the growing volume of information and incidents.
Network Security Architecture Frameworks
Formal network security architecture frameworks provide models and methods developed to formalize best practices, provide common terminology, and align teams. They also assure participants with proven recipes for success.
Frameworks tie into the entire business and link specific controls to specific business components and risks. The most popular frameworks are vendor independent and created by governments, non-profit standards organizations, and associations of IT professionals.
Check Point Enterprise Security Framework (CESF)
The vendor-specific Check Point Enterprise Security Framework (CESF) combines zero trust concepts and the Sherwood Applied Business Security Architecture (SABSA). Check Point guides customers through the framework and provides managed services.
Control Objectives for Information Technologies (COBIT) 5
The ISACA COBIT 5 framework provides free resources for self-guidance, training, and four levels of practitioner certification and also certifies trainers. COBIT is designed to integrate into other frameworks and focuses on business logic, process requirements, and risk.
Department of Defense (US) Architecture Framework (DoDAF)
The United States Department of Defense Architecture Framework (DoDAF) links operations to information security. It also coordinates security and manages interoperability issues across independent IT networks for multi-organization data sharing requirements.
Federal Enterprise Architecture Framework (FEAF)
The United States Federal Enterprise Architecture Framework (FEAF) provides a structure to develop controls integrated with objectives. The framework uses five stages: identify and validate, research and leverage, define and plan, invest and execute, and perform and measure.
NATO Architecture Framework Version 4 (NAFv4)
The North Atlantic Treaty Organization (NATO) released their fourth version of their architecture framework for military and business use. It provides enterprise architecture that aligns with ISO/IEC/IEEE international standards to help NATO members onto a common framework.
The Open Group Architecture Framework (TOGAF)
Over 925 vendor, consulting, academic, and other organizations make up the Open Group, and the Open Group architecture framework (TOGAF) provides stable and enduring scaffolding for initial and ongoing architecture development. Many enterprises deploy this framework, and the organization offers a variety of certification programs for practitioners, tools, and products.
Sherwood Applied Business Security Architecture (SABSA)
The Sherwood Applied Business Security Architecture (SABSA) helps to design, deliver, and support security services for risk management and information assurance. The dedicated SABSA Institute manages ongoing development, training, and certification.
4 Benefits of a Network Security Architecture
A superficial embrace of network security architecture may lead to more work than results. However, a rigorous pursuit of best practices will improve incident response and operations, meet regulatory obligations, and reduce damages from incidents.
Improve Incident Response
Despite the many possible types of incidents (attack, device failure, etc.), best practices add controls to limit spread, improve resilience, and actively monitor for failure. Combined, these capabilities enable fast detection, response, and recovery.
Improve Operations
Although typically pursued as a security practice, best practices also centralize, simplify, and test information systems rigorously. As a result of this process, operations will similarly streamline, eliminate bottlenecks, and reduce downtime.
Meet Regulatory Obligations
Regulations will require security controls to be in place and the reports to prove it. Formalized network security architecture ties controls to data and systems and provides the tests and reports to verify effective controls needed to comply with regulations and audits.
Reduce Damages From Incidents
Best practices add layers of security that limit damage from any single control failure and rigorous testing checks for gaps and overlooked issues. Combined with training to reduce the number of incidents and resilience to recover faster, the number of incidents to cause damage and the overall damage from any single event will be reduced.
Where to Learn More About Network Security Architecture
You can learn about network security architecture at a high level in computer science curriculums at universities around the world. For more targeted education, take an online course such as those provided by:
- Coursera: Offers over 240 online courses from beginner introductions to network security to advanced instruction in cloud infrastructure design and security.
- edX: Offers 21 courses related to network security architecture from the Linux Foundation, Check Point, Oracle, AWS, Purdue University, and more.
- Udemy: Offers over 10,000 online courses related to network security architecture including courses specifically related to COBIT and TOGAF.
Also consider a cybersecurity certification that can verify existing skills and help develop a career. Notable network security architecture certifications include:
- Certified Network Defense Architect (CNDA): Extends an existing Certified Ethical Hacker (CEH) certificate with additional qualifications for government and military roles.
- GIAC Defensible Security Architecture (GDSA): Provides a DoD-approved certification for mid-career security pros and associated SANS training.
- Information Systems Security Architecture Professional (ISSAP): Prepares IT executives to become system architects through a program designed by ISC2.
Bottom Line: Implement Network Security Architecture for a Secure Business
Formal network security architecture delivers a systematic approach for continuous improvement tied to business risks. Implement these frameworks and best practices to help other business units understand threats, contribute to planning, and support security initiatives.
For more specialized network security architecture information, consider reading about cloud security best practices and tips.








