Encryption software are security tools that obfuscate data to render it unreadable without a decryption key. Encryption protects data against unauthorized access or theft, yet the best tool to pick depends heavily on the use case and the solution’s fit with existing needs and resources. In my evaluation of tools, I selected three top solutions in five encryption categories: free file sharing, business file sharing, email, application layer, and end-to-end encryption.
The top encryption solutions are:
Top Free Encrypted File Sharing
- 7-Zip: Best for worldwide use
- GnuPG: Best for passwordless sharing
- VeraCrypt: Best for ultra-private sharing
Top Business File Sharing Encryption
- AxCrypt: Best for simplified business file sharing
- NordLocker: Best for cloud-based business file sharing
- Trend Micro Endpoint Encryption: Best for managed business file sharing
Top Email Encryption
- Cisco Secure Email Encryption Service: Best for Microsoft Email
- Paubox Email Suite: Best for HIPAA compliance
- Proton Mail: Best for full-domain email encryption
Top Application Layer Encryption
- Opaque Systems: Best multi-party AI collaboration
- Thales CipherTrust: Best for in-house app data encryption
- Vaultree: Best for fully-encrypted database queries
Top End-to-End Encryption
- IBM Security Guardium Encryption: Best for app data encryption
- OpenText Voltage: Best for self-hosted encryption
- Virtru: Best for zero-trust access governance
Table of Contents
Top Encryption Software Comparison
The following table provides the type of data encrypted and the pricing for each top solution:
| File & Folder Encryption | Full-Disk Encryption | Email Encryption | App Layer Encryption | Monthly Cost | |
|---|---|---|---|---|---|
| 7-Zip | ✔️ | ❌ | ❌ | ❌ | Free |
| GnuPG | ✔️ | ❌ | ❌ | ❌ | Free |
| VeraCrypt | ✔️ | ❌ | ❌ | ❌ | Free |
| AxCrypt | ✔️ | ❌ | ❌ | ❌ | $12/user |
| NordLocker | ✔️ | ❌ | ❌ | ❌ | $29.99/2 TB |
| Trend Micro Endpoint Encryption | ✔️ | ✔️ | ❌ | ❌ | • Perpetual License: $100/user • Annual Renewal: $20/user |
| Cisco | ❌ | ❌ | ✔️ | ❌ | $2.08/user |
| Paubox | ❌ | ❌ | ✔️ | ❌ | • Standard $37.70/user • Plus: $76.70/user • Premium: $89.70/user |
| Proton Mail | File sharing only | ❌ | ✔️ | ❌ | • Essentials: $7.99/user • Business: $12.99/user • Enterprise & Non-Profit: contact for custom quotes |
| Opaque | ❌ | ❌ | ❌ | ✔️ | Contact for pricing |
| Thales | ❌ | ❌ | ❌ | ✔️ | Contact for pricing |
| Vaultree | ❌ | ❌ | ❌ | ✔️ | Contact for pricing |
| IBM Security Guardium | Application Servers | ❌ | ❌ | ✔️ | Contact for pricing |
| OpenText Voltage | File sharing only | ❌ | ✔️ | ✔️ | Contact for pricing |
| Virtru | File sharing only | ❌ | ✔️ | ❌ | • Starter: $119/5 users • Business: $219/5 users |
✔️=Yes ❌=No/Unclear
Top Free Encrypted File Sharing Software
The top free encrypted file sharing software provide a solution to encrypt single files or folders for secure sharing with others. Small office and home office (SOHO) users or users with limited resources should choose one of these three free file sharing encryption tools: 7-Zip, GnuPG, or VeraCrypt.
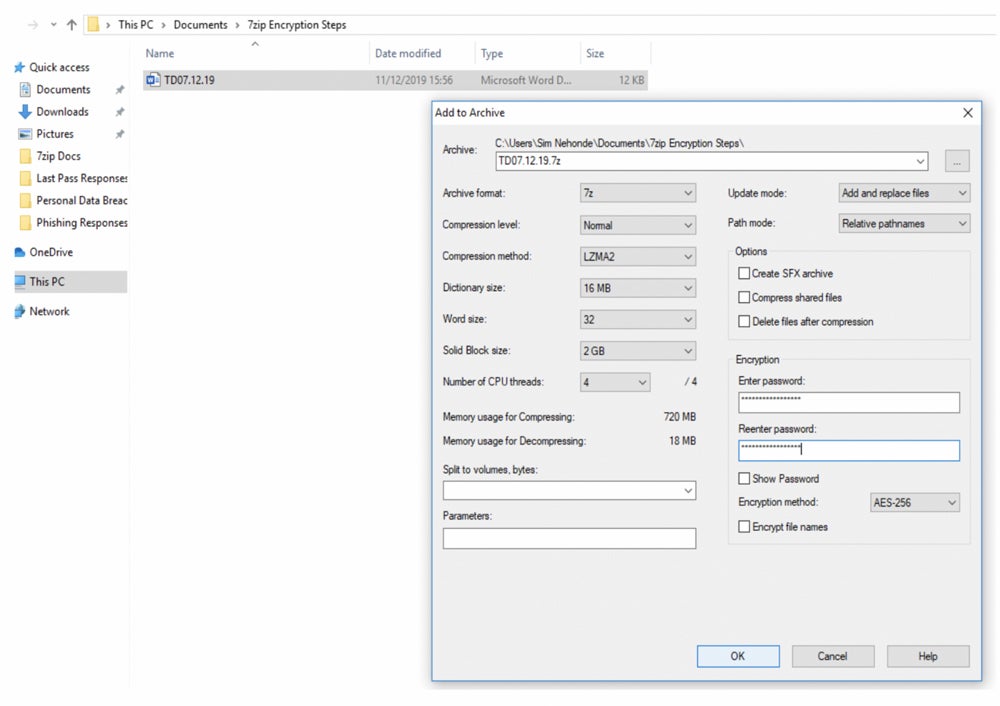
7-Zip – Best for Worldwide Encrypted Free File Sharing
7-Zip is a free file sharing tool that delivers strong encryption security with worldwide acceptance. It offers support for 89 different foreign languages and most major character sets. First released in 1999, the tool regularly updates to fix bugs, add features, or increase the number of supported languages.

Pros
Cons
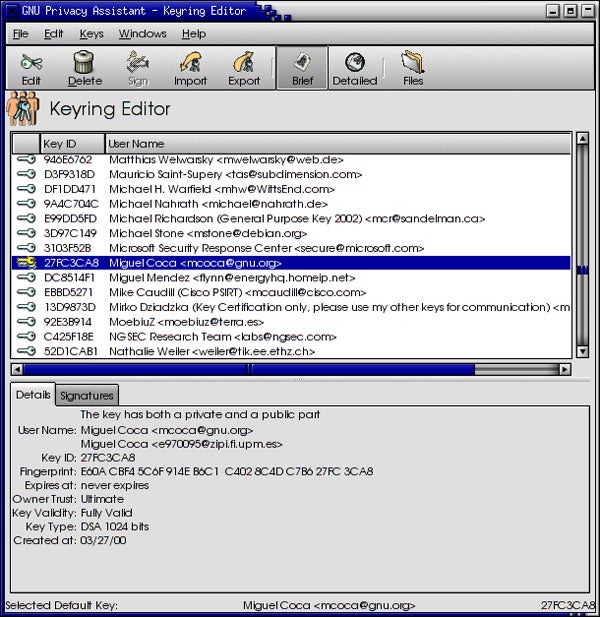
GnuPG – Best for Passwordless Encrypted Free File Sharing
The GNU Privacy Guard (GnuPG or GPG) is a free file sharing tool that also provides a unique option to generate public encryption keys to share files without exchanging passwords. With a track record of nearly 30 years of use, the tool continues to be trusted, updated, and built into other commercially available tools.

Pros
Cons
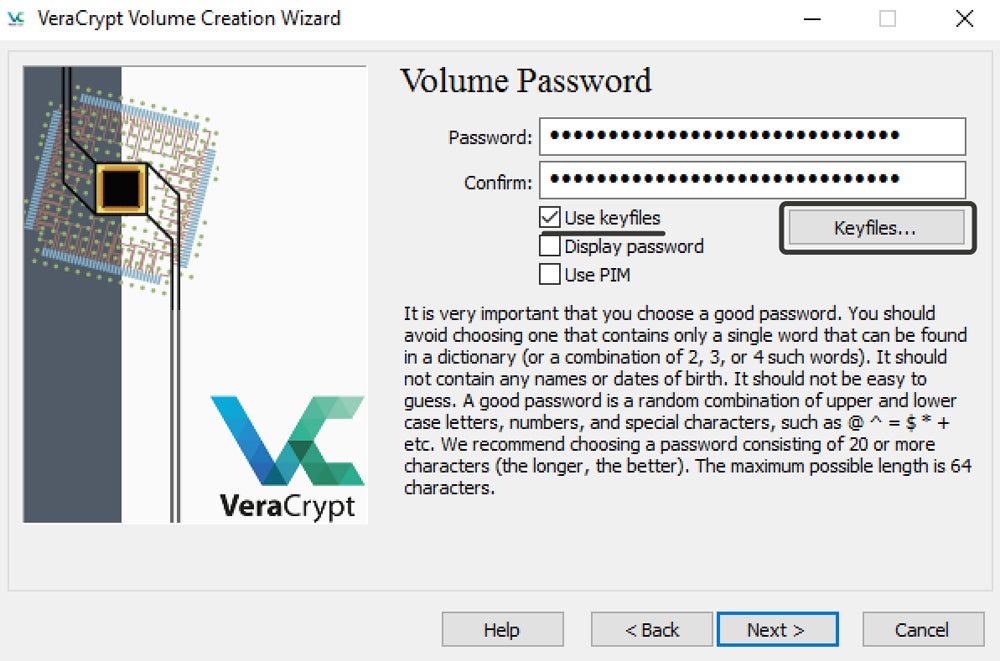
VeraCrypt – Best for Ultra-Private Free File Sharing
VeraCrypt is an open-source free file sharing encryption software with unique capabilities. One feature can obfuscate file types, which labels the encrypted file to appear to be a different file type. Another option uses two different passwords for an encrypted container to show different content depending upon the password used. Users with strong secrecy needs can combine features to hide data effectively even against potentially involuntary password disclosure.

Pros
Cons
Top Business File Sharing Encryption Software
The best business file sharing encryption software delivers centralized control and additional features required for more professional network security, which are unavailable from free solutions. The top three options include AxCrypt, NordLocker, and Trend Micro Endpoint Encryption.
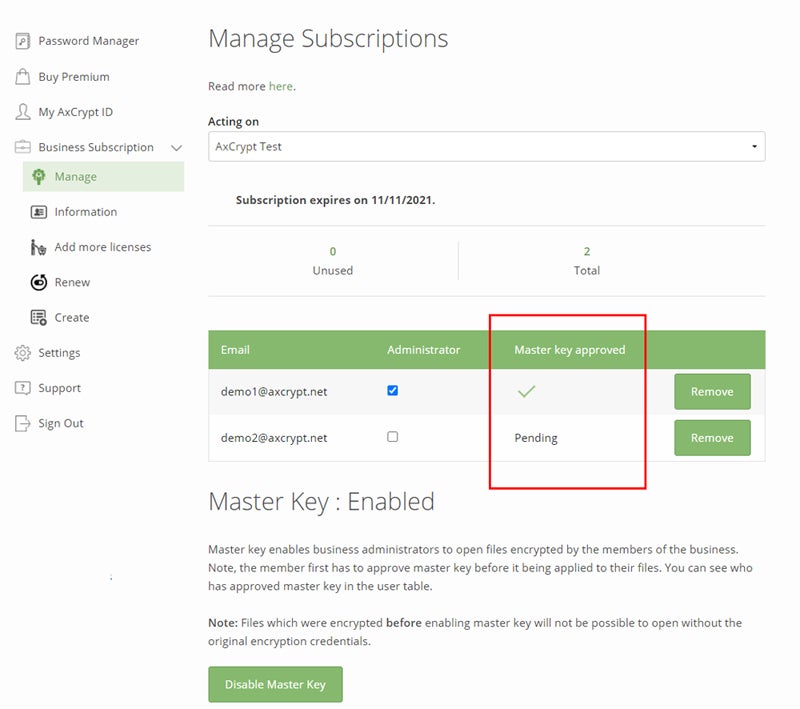
AxCrypt – Best for Simplified Business File Sharing
AxCrypt is a local file encryption and sharing tool that provides simplified administrator management of encryption master keys and subscription licenses. The tool supports laptops and desktops using Windows or macOS as well as iOS or Android mobile devices. AxCrypt encrypts local vaults on the devices or specific files and folders for sharing.

Pros
Cons
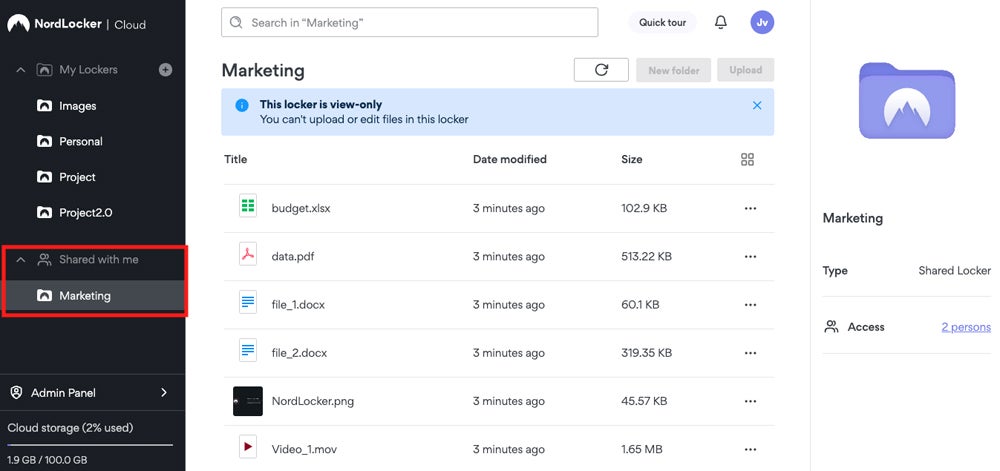
NordLocker – Best for Cloud-Based Business File Sharing
NordLocker is a business file sharing encryption tool that deploys a software-as-a-service (SaaS) solution for businesses allowed to use cloud-hosted file sharing platforms. The management console enforces policy and provides recovery options for forgotten passwords. NordLocker synchronizes cloud vaults with designated user vaults, which makes it a good choice for small businesses that want quick deployment and centralized control.

Pros
Cons
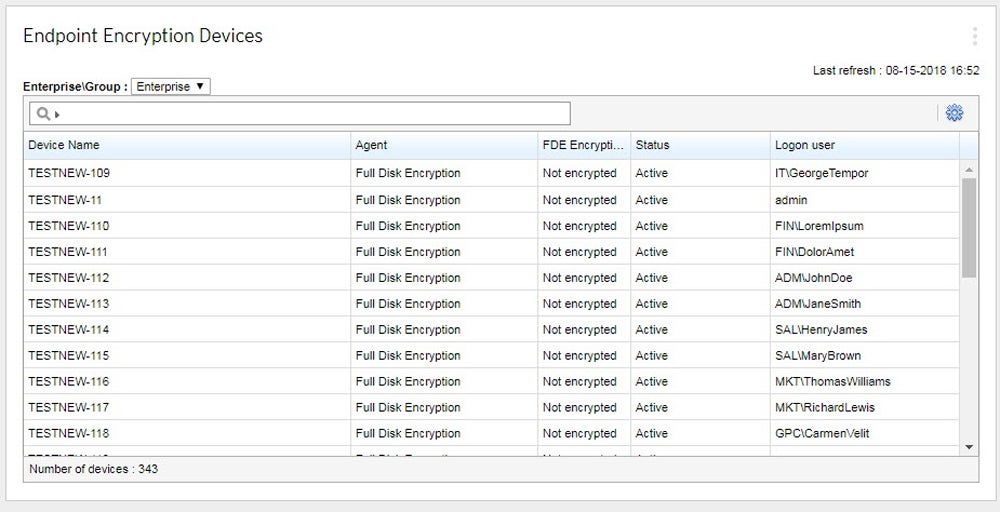
Trend Micro Endpoint Encryption – Best for Managed Business File Sharing
Trend Micro Endpoint Encryption is a full-disk encryption tool that can also provide secure business file sharing. It deploys as an agent to deliver enterprise-wide, centrally managed, and fully enforceable full disk, file, folder, and removable media encryption. Admins can deploy agents to both company and user-owned devices to meet formal encryption and compliance reporting requirements.

Pros
Cons
Top Email Encryption Software
The top email encryption software provide secure email, seamless integrated experiences for users, and centralized reporting and control. The top general email products, Microsoft 365 and Google Mail, offer encryption options that fail to encrypt email sent to incompatible mail servers. To satisfy secrecy or compliance requirements without investing in a secure gateway, consider an email encryption tool from Cisco Secure Email, Paubox Email Suite, or Proton Mail.
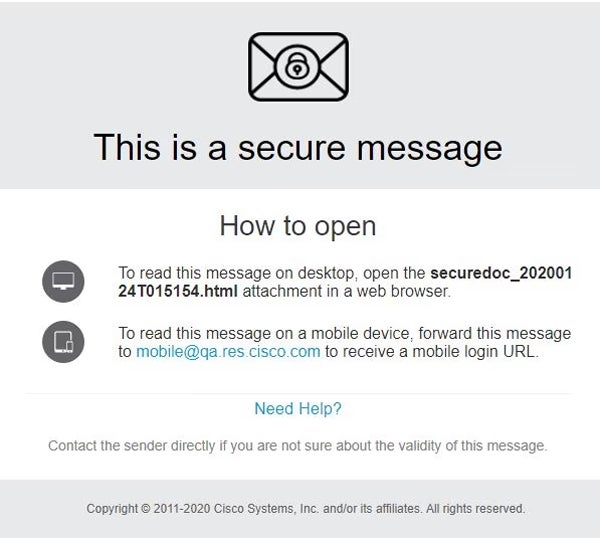
Cisco Secure Email Encryption Service – Best for Microsoft Email Encryption
Cisco’s Secure Email Encryption Service provides a quick, easy, and inexpensive plug-in solution for the many users that rely on Microsoft Outlook and 365 email. It uses registered envelopes and a Cisco-hosted temporary vault to ensure that only the correct recipient receives both the message and the decryption key needed to read the encrypted message.

Pros
Cons
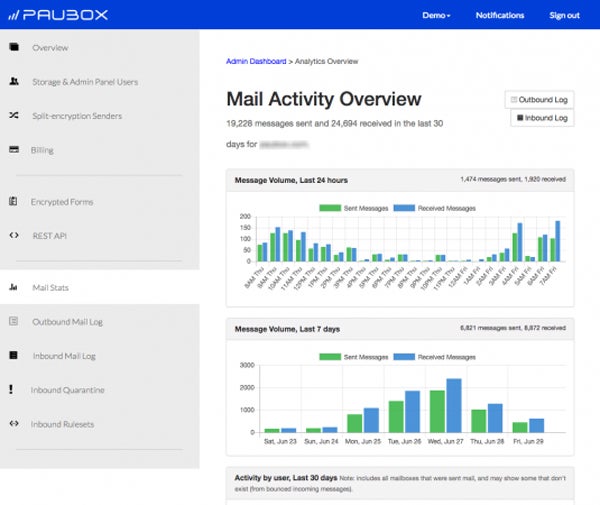
Paubox Email Suite – Best for HIPAA-Compliant Email Encryption
The Paubox Email Suite is an email encryption tool optimized for compliance with the United States’ HIPAA regulations to protect healthcare information from unauthorized access. Although the Standard option provides effective email encryption, the Plus and Premium licenses add additional features such as geofencing, spam filtering, malware protection, data loss prevention (DLP), and voicemail transcription.

Pros
Cons
Proton Mail – Best for Full-Domain Email Encryption
Proton Mail is an encrypted email solution to secure an entire email domain or company. The business license for this Swiss-based vendor bundles secure email, privacy, calendar, and VPN solutions to enable additional options for secure access and encrypted file sharing.

Pros
Cons
Top Application Layer Encryption (ALE) Software
The best application layer encryption (ALE) solutions encrypt application data to protect the modern app environment against breaches from exposed containers, web servers, database servers, and third-party services (shopping carts, credit card processing, etc.). The top ALE solutions to consider include Opaque Systems, Thales CipherTrust, and Vaultree.
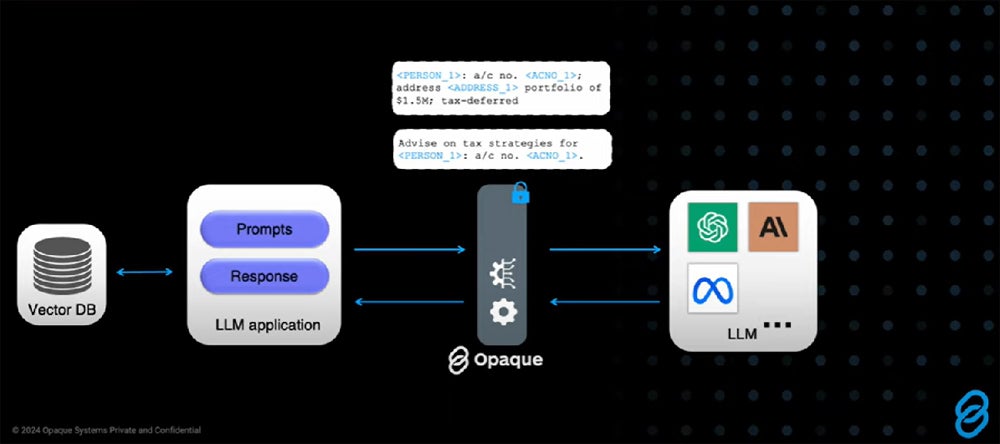
Opaque Gateway – Best ALE for Multi-Party AI Collaboration
Opaque Systems’ Gateway provides a novel ALE solution through encryption defense in depth. The solution delivers a platform to share encrypted data collaboratively that starts with hardware enclaves that segregate encrypted data in memory, even from the operating system or the hypervisor. It then adds additional layers of encryption unique to each party for collaborative calculations and analysis of sensitive data without sharing the data itself.

Pros
Cons
Thales CipherTrust – Best ALE for In-House App Data Encryption
The Thales CipherTrust Data Security Platform is an ALE solution that not only encrypts databases, but also tokenizes data inside the application and enables encryption key management. These capabilities extend encryption coverage further along data flows between apps, databases, and storage for more complete security. Customers can purchase components individually for partial solutions or purchase pre-packaged or cloud-services bundles.

Pros
Cons
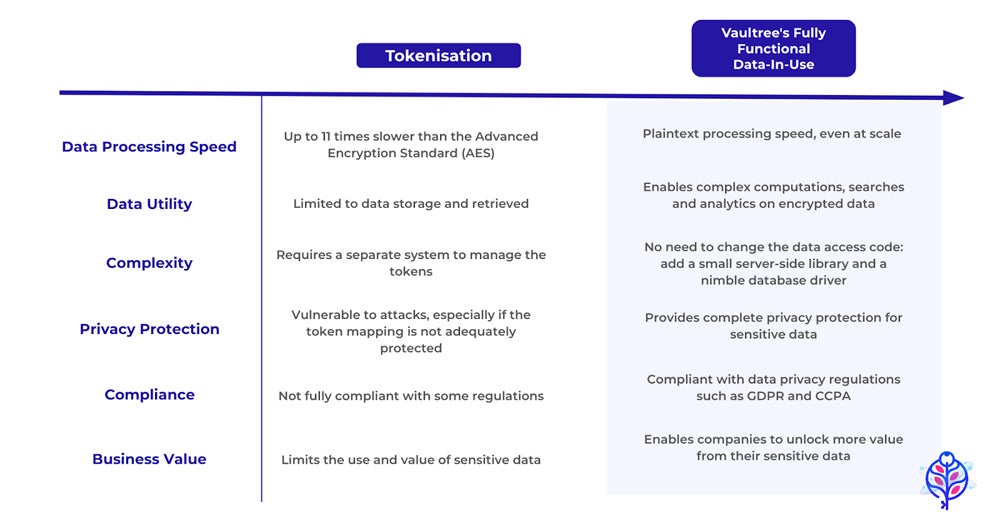
Vaultree – Best ALE for Fully-Encrypted Database Queries
Vaultree encrypts data for storage in databases and then encrypts future queries as well to perform encrypted searching. The Vaultree software development kit (SDK) provides plug-and-play encryption for any database client.

Pros
Cons
Top End-to-End Encryption Solutions
The top end-to-end encryption solutions not only protect data at rest, through transit, and even during use, they also provide centralized management, encryption key management, and security tool integrations. These top multifaceted solutions include IBM Security Guardium, OpenText Voltage, and Virtru.
IBM Security Guardium Encryption – Best for End-to-End App Data Encryption
IBM’s Security Guardium Encryption suite provides end-to-end protection for application data across servers, applications, databases, and containers as well as options to manage encryption keys. These tools combine to fully encapsulate application data at rest, in motion, during analytics, and upon receipt from websites. They also integrate with other IBM enterprise offerings such as certificate management and data security solutions.

Pros
Cons
OpenText Voltage – Best for End-to-End Self-Hosted Encryption
The OpenText Voltage end-to-end encryption solution encompasses a full range of enterprise needs such as file encryption, encrypted email, mobile encryption, secure file collaboration, PCI payment encryption, key management, and more. OpenText provides flexible licensing options and customers can deploy the software locally, in the cloud, or in hybrid environments.

Pros
Cons
Virtru – Best for End-to-End Zero-Trust Access Governance
The Virtru end-to-end encryption solution provides transparent pricing and zero-trust access by wrapping data with trusted data format (TDF) format files. TDF files granularly track permissions, expirations, and revocations as well as remain fully encrypted to provide end-to-end access governance even after delivery.

Pros
Cons
Quantum Encryption Solutions
Despite some availability, quantum chips suffer errors and stability issues, so encryption cracking with quantum computers remains a few technology generations away. However, many organizations with high security concerns look to develop quantum-safe cryptography ASAP in preparation for this eventuality.
The US National Institute of Standards and Technology (NIST) approved quantum-safe cryptographic algorithms, and other research informs the following initial quantum resistant encryption solutions:
- Entrust Public-Key Infrastructure (PKI) as-a-Service: Offers post-quantum product trials to test migration to quantum-resistant algorithms.
- IBM z16 Mainframes: Supports lattice-based digital signatures based on polynomial matrix calculation-based CRYSTALS-Dilithium Digital Signature Algorithms.
- Toshiba Quantum Key Distribution: Delivers physics-based quantum-decryption-proof and one-time encryption keys for unhackable information delivery over short distances.
For those unwilling to become an early adopter, current encryption standards can remain quantum-resistant through larger key size use, layers of encryption, and careful encryption key management.
How to Choose the Best Encryption Software for Your Business
The top benefit for all encryption is that the software scrambles data to render breached information unreadable. However, encryption tools focus on specific types of data and different tools offer different levels of protection, compliance support, integration complexity, maintenance, and control.
The best encryption software will maximize the pros (improved security and decreased breach damages) as well as minimize the cons (slower performance and increased resource drain). Fortunately, the four-phased process to identify, match, compare, and test potential solutions provides an effective guide to identify the best encryption software for your business needs.
1. Identify True Encryption Needs & Minimum Requirements
The first step requires an internal needs assessment to determine the requirements that any potential encryption solution must meet.
- Key data: Examine and classify the data that requires protection, locate data storage, track data transmission channels, and determine what or who accesses key data.
- Systems: Check for opportunities to enhance encryption in key-data-related systems such as encrypting the storage drives that host sensitive databases.
- Compliance regulations: Compare data against potential regulations (privacy, payment information, etc.) and determine required encryption, tests, and reports.
- Organizational needs: Consider that minimum compliance requirements (ex: AES-128) might not meet internal risk reduction needs compared to stronger encryption.
- Technical resources: Examine internal resources realistically to determine the available bandwidth, skills, and infrastructure limitations into which a solution must fit.
2. Match Encryption Candidates Against Identified Needs
After internal need identification, check the potential solutions in the market to determine what encryption tools satisfy the requirements.
- Encryption category: Select a solution that fits the identified data, system, compliance regulations, and corporate needs (file encryption for files, etc.).
- Encryption requirements: Choose encryption solutions that match minimum requirements and provide options for even stronger encryption algorithms or techniques.
- Reporting requirements: Examine reporting options to check if the solution can adequately detect usage or produce documentation to satisfy compliance requirements.
- Technical resources: Contrast the tool requirements against the bandwidth and technical capabilities of internal teams and service provider partners.
- Financial resources: Compare initial and ongoing licensing costs, expected labor costs, and any potential additional infrastructure costs against expected budgets.
3. Compare Encryption Solutions That Matched Requirements
A good number of tools should match the requirements, so the next step is to compare these solutions against each other to create a ranked list of contenders.
- Adoption requirements: Estimate installation, integration, and deployment requirements for time, difficulty, technical level, and expense.
- Maintenance requirements: Investigate the components to maintain, internal resources needed, update trends, and what will be maintained by the vendor.
- User experience: Examine the user installation and use experience and then check against the user base technical level and tolerance for process changes.
- Non-essential options: List the options and features above minimum requirements that may improve security or admin and user experience.
- Resource demands: Total the adoption, maintenance, and licensing financial costs and time demands.
4. Test the Top-Ranked Encryption Solutions
A comparison yields a short list of contending encryption solutions, so now comes the test drive to see if the theory matches the actual performance.
- Admin experience: Verify that the level of complexity to manage users, enforce encryption, and manage encryption keys matches expectations and requirements.
- User experience: Confirm that users can easily adopt the new encryption tool and check to ensure users can’t easily evade the tool.
- Performance hit: Install the solution on typical user and infrastructure systems to verify minimal or at least acceptable system resource slowdown.
- Customer service: Check that the help a vendor can provide in case of trouble matches the needs and expectations of the users and admin team.
- Security stack fit: Verify that the encryption solution can integrate with the existing security stack for protection, monitoring, and reporting.
At the end of this process, pick your favorite solution that passed all of the remaining tests. Just keep in mind that encryption only provides one layer of security and doesn’t provide a magic solution that eliminates all other security risks.
How I Selected This List of Encryption Solutions
To develop this list of 15 solutions, I first researched encryption categories to determine the major business needs and encryption types. Then, based upon product reviews, industry discussions, and industry rankings, the list was narrowed to the top candidates based on tool features, price, prominence, integrations, centralized encryption controls, key management, and other available options.
Encryption is frequently added as features of other tools such as endpoint detection and response. Encryption accelerating hardware can also be added to various computer systems as options to enhance security. However, this article expects potential encryption tool buyers to be focused on standalone solutions instead of features or options. Therefore, I excluded such partial solutions from this list.
Bottom Line: Start with Today’s Requirements, but Look Ahead
Breached data costs so much more to a company when unencrypted. Encrypted breaches protect against regulatory disclosure requirements, lawsuits, regulatory fines, and more. Put encryption in place now to protect against a breach.
However, future quantum computing advances will break the minimum encryption standards in place today. Today’s safe encrypted data breach may become tomorrow’s exposed data. Start investigating opportunities to apply more advanced encryption, multiple layers of encryption, or other additional safeguards today to defend against future threats.
To deploy effective encryption, consider learning about best practices for strong encryption.