Most organizations use email as a basic communication method. Unfortunately, text-based email protocols are extremely vulnerable to hacking and email has become the primary vector for cyber attacks. Organizations that understand email security in detail can adopt email security options that are a good fit for their needs and resources.
This article explores:
- What Is Email Security
- Best Options to Secure Business Email
- Email Security Best Practices
- How Email Security Blocks Threats
- Bottom Line: Email Security
What Is Email Security
Email security is a concept that protects email accounts, servers, and communications from unauthorized access, data loss, or compromise. Email security consists of the policies, tools, and services deployed to protect against threats specific to email such as spam, phishing attacks, malware-infested attachments, impersonation, and email interception.
Microsoft estimates that 94% of cyberattacks begin with a malicious email — a horrific statistic that can be dramatically reduced by adopting email security standards, tools, and services. Cybercriminals target email because it is an easy entry point and a single misguided click can potentially enable access to an entire organization. Cybercriminals use email to deliver a host of attacks such as business email compromise (BEC) attacks, malware delivery, and credentials harvesting.
Email security solutions help to:
- Protect an organization’s brand and reputation by flagging spoofing emails trying to impersonate the brand
- Protect an organization’s bottom line by limiting the devastating recovery costs, business disruption losses, business reputation damages, and forensic investigation costs associated with a successful attack
- Enhance productivity by limiting potential disruptions to operations and downtime because of a cyberattack
- Ensure compliance with data protection laws such as the General Data Protection Regulation (GDPR) and avoid the legal fees and regulatory fines associated with the breach of regulated data
Key Features for Email Security
Different email security protocols, tools and services provide both critical and nice-to-have features to secure email.
Critical features provide the base requirements of email security. Every organization should look for solutions that include:
- Antivirus and basic threat detection looks for and neutralizes known malware signatures within emails
- Anti-spam filters unwanted email bulk emails and spam messages
- Attachment analysis examines attachments for malicious or suspicious links and malware to disarm potentially malicious content
- Authentication systems evaluate the validity of senders using DMARC and other email protocols
- Reputation analysis analyzes the message header data and sender IP addresses to compare against IP and mail servers lists of known threat actors
- URL filtering provides uniform resource locator (URL) reputation analysis and some tools can even scan websites for malicious links, content, and attachments
Nice-to-have features provide additional security features at a cost that may be out of reach for some organizations:
- Account takeover protection attempts to detect and block attackers from obtaining credentials and accessing a user’s account to send spam, malware, BEC, or other types of attacks
- Advanced threat detection scans files for malicious code or other patterns associated with malicious threats beyond signature analysis
- Behavior analytics examine the content of emails and the behavior of users to detect unusual behavior that may indicate insider threats or compromised accounts
- Content analysis analyzes the text of the email for urgency terms or other words and phrases associated with phishing or BEC attacks
- Data encryption secures mail communications from interception by cybercriminals or from unintended recipients reading the message
- Data loss protection (DLP) technologies check outgoing emails for content or attachments that may include proprietary or regulated data to flag or even block intentional or accidental insider threat activities
- Image and content control capabilities can scan attached or embedded images or content to block malware
- Integrated threat protection can provide unified protection across apps, devices, email, identities, data, and cloud workloads
- Sandboxing provides detonation capabilities for malicious links and attachments within a controlled environment
Best Options to Secure Business Email
Email security may be critical, but every organization faces unique budget constraints, threat profiles, risk profiles, and labor capabilities. These aspects will define the type of tools, services, and protocols that the organization can realistically adopt to protect emails against threats.
Organizations typically select a combination of the following options to suit their email security needs. In some cases, the options will have overlapping capabilities, but redundancy isn’t typically a bad thing for security. Organizations seeking to bolster their email security should examine several options with features that fill in gaps in their current capabilities.
We will present these options in two categories: a priority tier and an advanced capability tier. Smaller organizations need to start with priority options and then adopt more advanced options as they grow and their needs and resources develop. We will cover main tool categories, but keep in mind that specialty tools exist for specialty roles such as attachment inspection that will often be features of more sophisticated tools.
The priority tier includes:
- Email authentication protocols
- Email security tools
- Next generation firewalls and unified threat management
- Secure access service edge
- Secure email gateway or secure web gateway
The advanced capability tier includes sandboxing, encryption, and secure browsers that can provide additional layers of protection for more sophisticated needs.
The more sophisticated a solution, the more it tends to require expertise to install, configure, manage, and maintain. Organizations can offload some expertise requirements to managed IT service providers (MSPs) or managed IT security service providers (MSSPs). Keep in mind that each category also contains a spectrum of basic-to-advanced tools and capabilities and that service providers can often offer advanced capabilities to smaller organizations through service bundles.
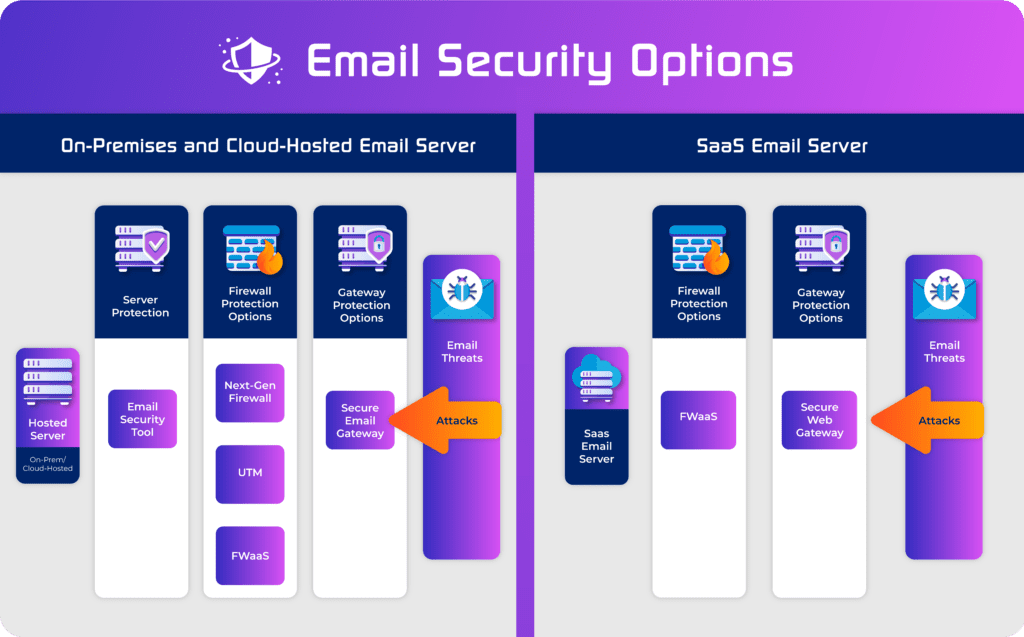
Priority Tier to Improve Email Security
When starting out, organizations should focus on adopting these fundamental email security options. These options provide the basic security features needed for fundamental email security and often will offer options to even upgrade to more advanced security as well.
Email Authentication Protocols: SPF, DKIM, DMARC
The three mutually-reinforcing email authentication protocols, Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication Reporting and Conformance (DMARC) verify the authenticity of emails. Enforcing these protocols will block spam, help identify spoofing emails, and help with reputation analysis for security tools.
It is very affordable for an organization to enable their security tools and web servers to check for and enforce these protocols. It can be time consuming to establish these protocols on an organization’s DNS servers, but doing so will provide two key benefits. First, the protocols improve the reputation of an organization which boosts the deliverability of marketing emails. Second, email servers and security tools can use the protocols to flag emails that try to spoof the organization’s domain and brand.
The smallest organizations may not have the resources to establish these protocols. However, adoption of these protocols should be a priority for growing organizations and is already a federal requirement since 2018 as part of the Department of Homeland Security (DHS) 18-01 binding operational directive.
Email Security Tool
A number of tools present themselves as email security tools to protect local email applications and email servers. These tools are generally good options for smaller organizations with a limited number of on-prem email servers. More advanced versions of these tools can be installed on the cloud to extend their reach and puts them in direct competition with other cloud-based solutions (see below)..
An organization can select from a spectrum of tools from inexpensive and basic tools to robust, feature rich, and expensive tools. Email security tools offer features that screen emails for malicious content using antivirus, anti-spam, DNS, attachment, and other analytics. More advanced tools may include additional options such as threat feeds, sandboxing, and AI-enhanced analytics.
Next Generation Firewalls and Unified Threat Management Systems
Firewalls with advanced capabilities can typically perform application-layer packet inspection that allows for the tool to screen emails for malicious links, spam, and malicious attachments. Both Next Generation Firewalls (NGFW) and Unified Threat Management (UTM) tools will have some capabilities, but an organization will need to check the specific tools under consideration to check both the specific features available and how the tool will integrate with the existing security stack and IT environment.
As with email security tools, advanced firewalls tend to be placed at the edge of local networks and thus are more appropriate for protecting a small number of local email servers. For larger or geographically diverse organizations, cloud-based firewall-as-a-service (FWaaS) may provide more cost-effective and unified protection.
Secure Access Service Edge
Secure Access Service Edge (SASE) tools, also called security service edge (SSE) solutions, control access outside of the corporate network and tend to be cloud-based. Some tools only control access, but other tools also will incorporate secure web gateway (SWG) and firewall capabilities that permit the tools to detect and block spam as well as malicious websites and attachments. SASE solutions provide good solutions for large and geographically diverse organizations looking for centralized control and protection.
Secure Email Gateway or Secure Web Gateway
Secure email gateway (SEG) or secure web gateway (SWG) solutions provide dedicated solutions to screen emails and website traffic. These tools scan attachments, check for malicious links, and can incorporate blacklists to block known-malicious domains. These tools can also include DLP capabilities to block insiders from intentionally or accidentally leaking sensitive information.
SEGs will focus more specifically on protecting email systems, particularly on-premises email servers, and SWGs may be better to protect SaaS environments. Both options can be installed locally to protect local email servers or in the cloud to enable broader coverage.
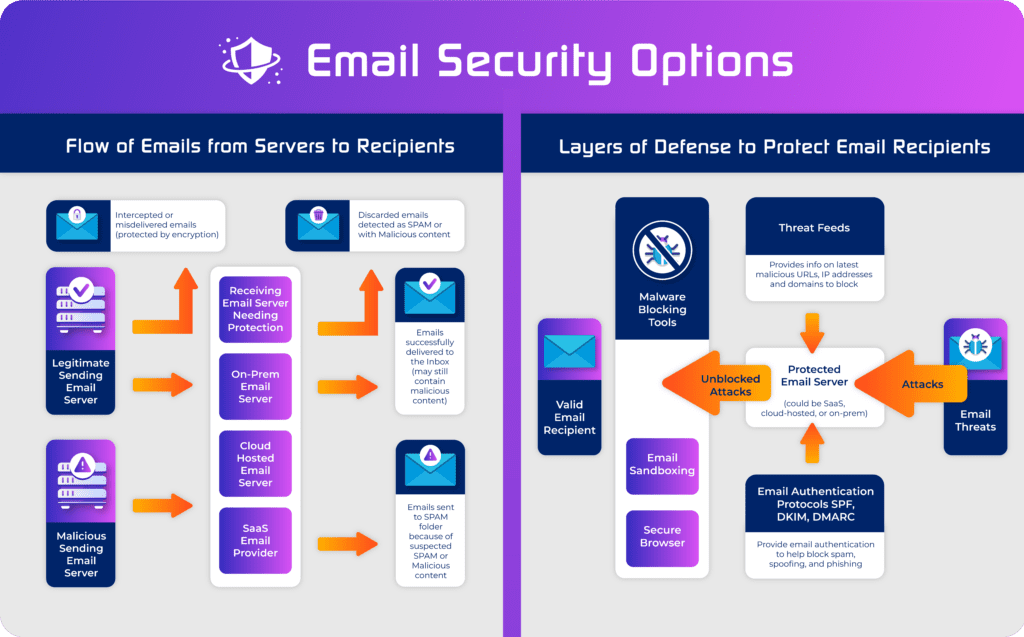
Advanced Email Security Capabilities Tier
Organizations with more sophisticated needs or more resources may consider additional capabilities to provide additional layers of security for email. Some of these capabilities will be obtained through specific, specialized tools, but others will be obtained through more advanced features or add-ons to tools listed in the priority tier above.
Email Sandboxing
The delivery of malware through email remains a high concern, even for organizations deploying layers of email security to prevent malware delivery. Attackers can modify code too easily and develop new types of attack too quickly for most IT security teams to put all of their faith in anti-malware solutions.
Many email security solutions now provide sandboxing capabilities to enable security teams to launch attachments in a safer environment. However, while these capabilities can improve confidence in attachment analysis, IT security teams must also be aware that some malware will attempt to detect sandboxing environments to prevent analysis.
Encrypted email
Despite many advancements in email tools, the email format itself remains a text-based protocol. Many email tools will enable the encrypted delivery of emails, but some of these encryption options will be undone if the sending email server detects a receiving email server that may not support the option. For more ensured protection against the interception of emails, organizations can adopt an email encryption solution.
Secure Browser
A secure browser, also known as browser isolation, creates a sandboxed environment on the endpoint device. Within this sandboxed environment, the user can perform their normal business activities with less concern about malware and malicious attachments. If the user accidentally launches malware, the malware will affect the sandboxed environment and allow the user to simply close the sandbox with a greatly reduced risk for a long-term effect on the local endpoint or network.
Threat Feed
Attackers constantly develop new attacks and methods and new vulnerabilities are discovered regularly. Threat feeds provide security teams with the latest news and can be integrated with security tools to update malware signature files more frequently and provide indicators of compromise used by advanced analytics to detect new malware in action.
Email Security Best Practices
Ultimately, the point of any security is to reduce risk for the organization. Email security should fit into a broader security strategy to reduce the risks of attack on an organization and the related risks of data breaches, operational disruption, and financial loss.
The best practices for email security reflect these overarching risk reduction requirements of an organization. Although we will provide best practices for a generic organization, every manager with IT, security, and risk responsibilities must modify these best practices to fit the context of their specific needs. For example, even a very small stock broker will have US Security and Exchange Commission (SEC) or Financial Industry Regulatory Authority (FINRA) regulatory requirements for email security, monitoring, and retention.
Good, Better, and Best Security Best Practices
The Good, Better and Best levels of email security best practices reflect the adoption of increasing levels of sophistication and capabilities in the adoption of formal email policies, layers of email security, employee email security training, use of email for high-risk functions, and the related security stack.
Good Email Security Best Practices:
- Adopt a written email security policy
- Enable security options in email software
- Use at least one priority tier email security tool (email security tool, advanced firewall, SASE, or secure gateway) with basic functionality to reduce spam and inspect email and attachments for malware
- Have a basic security stack that includes hardened IT infrastructure and protected endpoints
Better Email Security Best Practices:
- Adopt a written email security policy and use it actively to measure success for email security through regular reports
- Enable security options in email software
- Enable email authentication (SPF, DKIM, DMARC)
- Use at least one priority tier email security tool (email security tool, advanced firewall, SASE, or secure gateway) or multiple security tools that deliver stronger capabilities to reduce spam, inspect email and attachments for malware, and perform URL filtering
- Have an email security tool with capabilities for at least one advanced tier email security function (sandboxing, encrypted email, secure browser, threat feed) to protect against attacks
- Perform basic annual employee security training to reduce risk
- Limit your use of email for high-risk functions (financial transactions, regulated data exchange, etc.)
- Purchase a hardened security stack that includes DNS security, encryption at rest, hardened IT infrastructure, multi-factor authentication, and protected endpoints.
Best Email Security Best Practices:
- Adopt a written email security policy and use it actively to measure success for email security through regular reports that reflect risk reduction
- Enable security options in email software
- Email authentication (SPF, DKIM, DMARC) enabled
- Use a robust priority tier email security tool or tools (email security tool, advanced firewall, SASE, or secure gateway) implemented with strong capabilities to reduce spam, inspect email and attachments for malware, perform URL filtering, perform reputation analysis, and several nice-to-have features such as behavioral analytics, advanced threat detection, or sandboxing
- Have an email security tool with capabilities for one or more advanced tier email security function (sandboxing, encrypted email, secure browser, threat feed) to protect against attacks
- Conduct regular employee security training to create a security-focused organization
- Highly restrict or block the use of email for high-risk functions (financial transactions, regulated data exchange, etc.)
- Have a robust security stack that provides a full spectrum of overlapping protection
To understand the context of these best practices, we’ll explain the formal email policy, multilayered email security, employee security training, email use for high-risk functions, and related security stack in more detail.
Formal Email Policy
Organizations should have two types of formal email policies. A corporate email use policy for employees and an email security policy for the IT or IT security team.
Most organizations already have a corporate email use policy developed by the HR department to ensure that employees are aware of their responsibilities when using company email, guidelines on personal usage of corporate email, use of personal emails accounts, email use on corporate and personal devices. These policies also typically cover email retention, attachment guidance (permitted file types, file sizes), prohibited email content, regulated or confidential data in emails, and corporate monitoring of employee emails for compliance and other purposes.
Many organizations have email security strategies in place, but without any written documentation or formalized reports that would help an IT security team to prove the implementation and ongoing functionality of an acceptable level of email security. A written email security policy for IT security formalizes the risk reduction expectations, minimum acceptable security features, and reporting requirements.
Both types of email policies provide protections and penalties. As long as employees and IT teams conform to the requirements of the email policy, the organization and the employee will be protected in the event of a security incident or breach. However, both policies should also provide for penalties and processes to investigate employees and IT staff who actively undermine or simply choose not to comply with the security policies.
Employee Security Training
No security software is 100% effective or immune from breaches. Employee training can provide basic security skills for employees to use to avoid becoming victim to email attacks.
Simple rules that should be taught include:
- Never click on links in emails received from unknown sources
- Never open attachments from unknown sources. If an unexpected attachment is received from a known sender, an employee should call the sender to verify the contents of the attachment before opening
- Never follow links to financial institutions contained within emails. Instead, type the address directly into a browser or use a search engine to locate the financial institution’s official websites
- Always consult a senior manager before transferring money on instructions in an email. Business email compromise scams often instill a sense of urgency and imply that the sender is out of phone contact but a wire transfer must be carried out immediately without telling other staff members for “reasons of confidentiality”
- Never connect to the corporate email system from a public Wi-Fi spot without using a VPN to ensure that the link is secure
Many organizations use third-party cybersecurity training programs to help minimize the risk of human error and ensure that employees understand the importance of email security.
Email Use for High-Risk Functions
Email can be difficult to secure and email servers can even undo some security features, such as encryption, if the receiving email server indicates that it cannot support the feature. High risk processes and transactions should be moved to systems with stronger authentication and security functions.
For example, the following processes should not be conducted via email and should only be performed using secured websites or applications after verifying the user’s identity:
- Requesting patient data (regulated by HIPAA)
- Obtaining credit card numbers (regulated by PCI DSS)
- Authorizing financial transactions (at least over a certain dollar amount)
- Authorizing payments to employees or vendors
- Delivering the results of medical exams or tests (regulated by HIPAA)
Related Security Stack
Email security cannot operate alone to protect an organization. Email security must fit into a security stack of related and overlapping network security controls that limit the impact of breached email security such as data loss protection, DNS security, data encryption, hardened IT infrastructure, identity and access management (IAM), multi factor authentication, and protecting endpoints.
Data Loss Protection
Data loss protection (DLP) monitors the use and movement of important or regulated data. Corporate secrets, personal identifying information (PII), personal health information, and other regulated information can be detected, monitored, or even blocked from inclusion in emails, chat applications, or file-sharing applications.
Email tools can offer limited capability DLP that focuses on the use of protected data in email. However, a more robust DLP solution will include many other applications outside of email to deliver more general protection.
DNS Security
DNS security involves two key aspects: the investigation of URLs and domains within emails, and protecting the corporate DNS from attack and corruption. Many email security programs will perform basic DNS security such as checking URLs against a blacklist of known-malicious websites. The email security programs should be further enhanced by tools and techniques applied to protect corporate DNS.
Encryption At Rest
Malicious emails, especially modern ransomware, use data exfiltration programs to steal data from local and network hard drives. The adoption of encryption at rest will limit the access and availability of data stolen from such attacks and provide an additional defense should email security fail.
Harden IT Infrastructure
Default installations of firewalls, networking equipment, server operating systems, and local operating systems will not block any protocols or ports to allow for maximum utility. Unfortunately, maximum utility also means maximum security risk.
Organizations should disable unneeded protocols, block unused ports, and enable options for improved security across the IT infrastructure. These hardening techniques limit the ability of successful email attacks to expand across the organization.
Identity and Access Management
Identity and access management (IAM) hardens the organization with regards to access by enabling an organization to apply the principle of least privilege access to limit unnecessary access by specific users and user groups. Effective use of IAM will limit the ability of attackers to use stolen credentials or compromised devices to expand an attack against the organization.
Multi-factor Authentication
Compromised credentials stolen from a phishing campaign can be quite dangerous. However, the adoption of two-factor (2FA) and multi-factor authentication (MFA) provides additional barriers for an attacker to navigate.
Protecting endpoints
A breached email security will often result in an attack on the end user’s computer. A strong antivirus or endpoint detection and response (EDR) solution protects the local machine against infection or even isolates a compromised local machine to protect the network.
How Email Security Blocks Threats
Email can contain a wide variety of potential threats including business email compromise, data exfiltration, impersonation, malware, and phishing and spam emails. Deploying various email security tools can detect, contain, or even block these threats using a variety of techniques and features.
Business Email Compromise
Business email compromise (BEC) attacks are a subcategory of phishing or impersonation attacks that attempt to impersonate trusted business partners or employees in order to trick the organization into sending products or cash payments to the attacker. Email security can block this type of attack because they:
- Use DMARC email authentication to catch discrepancies between the From field shown to email recipients and the From field in the header
- Analyze email sender reputation (URL, Domain)
- Apply text sentiment analysis looking for suspicious text trends such as urgency (reply now) or secrecy (do not contact others for verification)
Data Exfiltration
Data exfiltration occurs with the unapproved transfer of data from an organization. Email security tools use data loss prevention (DLP) technology to identify and track proprietary or regulated data within email text or attachments.
Most DLP programs will have a limited number of default detections such as US social security numbers and credit card numbers. Organizations may have to define other information for the DLP to track and monitor.
Impersonation
Attackers try to fake the “from” fields in emails to impersonate a trusted person or brand. Impersonation, also known as spoofing, lends credibility to phishing and can be accomplished through misleading graphics, text, and look-alike domains (ex: m1cr0s0ft.com).
Email security tools can catch impersonation attempts because they:
- Use SPF email authentication to verify if the sending domain is an authorized email sending address (for spoofed domains)
- Use DMARC email authentication to catch discrepancies between the From field shown to email recipients and the From field in the header
- Analyze email sender reputation (URL, Domain)
- Apply text sentiment analysis looking for suspicious text trends such as urgency (reply now) or secrecy (do not contact others for verification)
Malware
Common types of malware include viruses, worms, ransomware, and spyware and email attacks will often attempt to disguise malware as PDF files or within compressed files (.zip, etc.). Email security tools detect malware using one of several features:
- Antivirus signature comparison against known malware
- Analysis of email sender reputation (URL, Domain)
- Open attachments in sandboxes to verify file contents
- Advanced malware detection by checking file content for malicious or suspicious programming
Phishing & Spam
Phishing attacks are a malicious subcategory of spam emails that can also include spear phishing, vishing, and whaling. The main difference between the phishing and spam is if the links and attachments of the unwanted email lead to malicious websites.
Email security tools detect phishing and spam emails because they:
- Use DMARC email authentication to catch discrepancies between the From field shown to email recipients and the From field in the header
- Analyze email sender reputation (URL, Domain)
- Analyze URLs and websites linked in the email for malicious code or credential stealing tactics using advanced malware detection capabilities
- Appy text sentiment analysis looking for suspicious text trends such as urgency (reply now) or secrecy (do not contact others for verification)
Bottom Line: Email Security
Email security tools are available in a wide spectrum and variety that can meet the varied needs of an equally wide spectrum of organizations. As each organization grows, it will need to regularly check if their existing email security solution continues to satisfy the current needs of the organization now and for the next few quarters. If additional capabilities are needed, organizations should explore their options and adopt new tools before an attacker can exploit any gaps.
For additional insight into email security tools, consider reading:
- What Is DMARC Email Security Technology?
- 9 Best Next-Generation Firewall (NGFW) Solutions for 2023
- 8 Top Unified Threat Management (UTM) Software & Hardware Vendors
- Firewalls as a Service (FWaaS): The Future of Network Firewalls?
- Top Secure Access Service Edge (SASE) Providers
- Top Secure Email Gateway Solutions
- 9 Best Secure Web Gateway Vendors
This article was originally written and published by Paul Rubens on March 13, 2018 and updated by Chad Kime on June 8, 2023.








