Email spoofing forges the sender address on emails to make the email appear to be from a trusted source or brand. Hackers commonly use spoofing in SPAM and phishing attacks to evade email filters and to improve the appearance of legitimacy to the users that receive the emails. To improve protection against spoofing attacks, an organization should understand:
- What is email spoofing?
- How to identify a spoofed email
- How to prevent email spoofing
- Bottom Line: Keep Ahead of the Constantly Evolving Threat of Email Spoofing
What Is Email Spoofing?
Email spoofing is a hacking technique that forges or manipulates email metadata such asthe display name and email address to mislead the intended recipient about the identity of the email sender. While not all SPAM or phishing attacks use spoofed identities, the use of email spoofing techniques enhances the capabilities of SPAM and phishing emails. Spoofing is often used in conjunction with:
- Social engineering phishing attacks pretending to be other employees or associates known to the recipient
- Business email compromise (BEC) attacks attempting to commit fraud while impersonating business executives or business partners
- Domain impersonation such as changing only one or two letters in a brand name or URL such “Arnazon” instead of “Amazon”
Phishing, social engineering, and other email based attacks that use stolen credentials to send fraudulent emails from legitimate accounts do not qualify as spoofed emails. The sending domain is not manipulated in those cases and the sender, while compromised, is legitimate.
How to Identify a Spoofed Email
To catch a spoofed email, first read the subject line as well as the sender’s name and email address. Next, open the email and determine whether the footer seems legitimate, then read the body of the email and note any unclear verbiage or grammatical issues. Finally, note whether your email client marked the message as spam, and inspect the email header if needed.
Consider the email in the screenshot below:
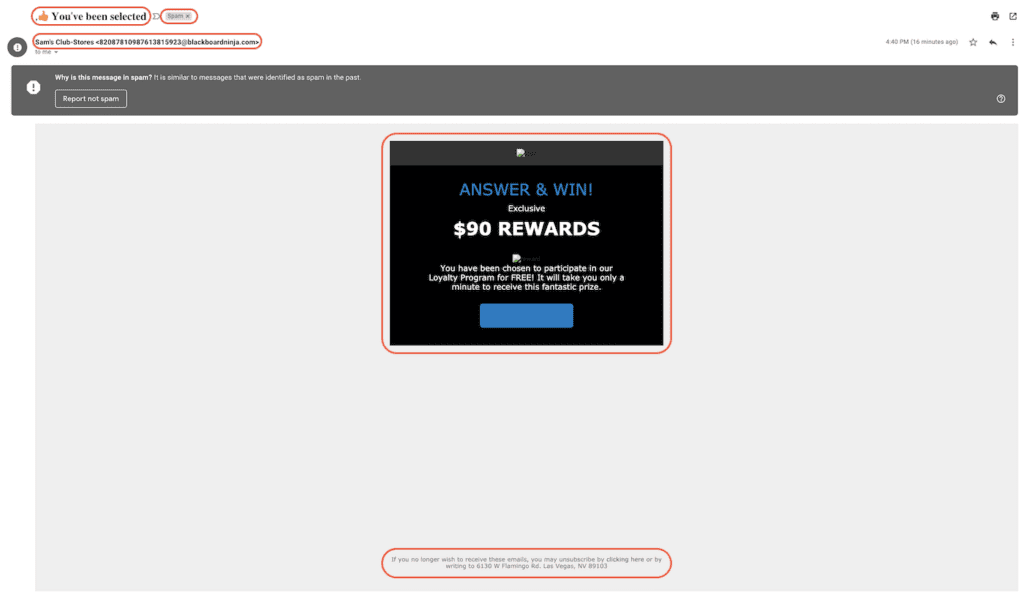
First, the subject line, sender email address, and footer are all indicators that the email is illegitimate. If it was a real email from Sam’s Club, the subject line should be free of errors and strange formatting. The domain of the sender email address would be samsclub.com or some variation thereof instead of blackboardninja.com, and the mailing address in the footer would be the Sam’s Club headquarters address instead of an address in Las Vegas.
Additionally, the body content of the email has a vague call to action—what is the “Loyalty Program” and what must one do to earn the so-called “prize”? Unless the recipient is expecting an email like this, there is very little context that indicates where the link leads. This is typical of phishing emails.
Finally, the fact that Gmail automatically categorized this email as Spam doesn’t necessarily mean it’s a spoof, but it’s definitely a red flag. Spam filters can be overzealous at times, which is why important emails like order confirmations and shipping updates sometimes end up in the wrong folder. However, the purpose of a spam filter is to prevent gullible recipients from falling into a spoofed email’s traps.
Not all spoofed emails will be so easily recognizable. Others may require an inspection of the email header to check for discrepancies between the supposed sender and the actual sending domain.
Keep in mind that most email programs do not verify or perform authentication checks on the identifying fields within the body of the email such as Mail From, Reply To, From, Subject, Date, or To. An attacker can claim to be one identity in the From field and a different identity in the header and it will be difficult for the user to notice.
How to Prevent Email Spoofing
Email spoofing, often used in conjunction with phishing attacks, threatens organizations of all sizes. Common security techniques such as encryption, firewalls, and antimalware software cannot stop spoofed emails from being delivered to an inbox or help a user that clicks on a phishing link to harvest credentials.
Although email spoofing techniques are becoming more sophisticated with each passing day, there are a few tactics that can help prevent a successful email spoofing attack. These include email authentication protocols, email security tools, email server settings, secure email gateways, and regular employee training.
Email Authentication Protocols
Protocols exist to help authenticate email senders to reduce the effectiveness of spoofing. The Sender Policy Framework (SPF), Domain Keys Identified Email (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) protocols provide effective defense through public posting of company email server information in the domain name services (DNS) records and servers. Together, these protocols reduce the ability of an attacker to spoof an organization’s domain from being used for malicious purposes.
Email Security Tools
Many vendors offer email security tools that specifically guard against spoofing, spam emails, and phishing attacks. These tools use threat feeds, artificial intelligence–enhanced algorithms, and other features to detect, block, quarantine, or flag suspicious emails. These tools can be delivered in various ways such as appliances, on-premises software, or cloud-based software-as-a-service solutions.
Email Server Settings
Many email servers default for more permissive delivery of suspicious emails to prevent missing emails from customers and vendors. However, given the onslaught of phishing attacks, an organization may wish to adjust email server settings to be more strict. For example, when an email fails email authentication checks (SPF, DKIM, DMARC), instead of allowing the email to be delivered to a SPAM folder or delivered to an inbox with a ‘suspicious’ flag, simply discard the email.
Secure Email Gateways
Secure Email Gateway solutions provide advanced email filtering and protection capabilities such as email authentication checks (using SPF, DKIM, DMARC), reverse DNS lookups, active scanning of emails for malicious files, and robust tracking tools for security teams to investigate specific emails. Secure email gateways can be deployed locally, in the cloud, or obtained as a service. These tools can not only protect local email servers, but also web-based services such as Outlook 365 and GMail.
Employee Training
As with most cybersecurity and network security efforts, employee training helps create a safeguard against attacks that are able to slip past technical defenses. Organizations should set aside time at least once per year (if not more frequently) to teach employees what to look for in a legitimate email as opposed to a spoofed one. Then, perform follow up tests to see who may still fall victim to a spoofing attack. This will help ensure everyone on a team can act appropriately when a spoofed email inevitably lands in their inbox.
Bottom Line: Keep Ahead of the Constantly Evolving Threat of Email Spoofing
As long as an organization uses email to communicate internally and externally, email spoofing will be a threat. In fact, email spoofing accounted for more than $216 million in losses in 2020 alone, according to the FBI’s IC3 2020 Internet Crime Report. However, while spoofed emails may look different from one day to the next, applying available solutions can dramatically reduce exposure to receiving spoofed emails as well as prevent an organization’s brand from being used in spoofed email attacks.
This article was originally written and published by Kaiti Norton on July 13, 2021 and updated by Chad Kime on May 23, 2023.








