Network security creates shielded, monitored, and secure communications between users and assets. Despite the rapid evolution of what constitutes the users, assets, and connections, the fundamentals of networking security remain the same: block external threats, protect internal network communications, monitor the network for internal and external threats, and ensure that users only access authorized parts of the network.
Securing the expanding, sprawling, and sometimes conflicting collection of technologies that make up network security provides constant challenges for security professionals. We will examine these fundamentals as well as the shifting nature of networking security through the following sections:
- Network Security Defined
- How Network Security Works
- Network Layers & Security Models
- What Are the Main Network Security Threats?
- Best Practices for Protecting Your Network
- Types of Network Security Solutions
- What Are the Benefits of Network Security?
- 6 Core Network Security Challenges
- Starting a Network Security Career
- Bottom Line: Network Security
Network Security Defined
To understand the shifting requirements and technologies, we must examine the contrast between earlier simple networks and newer, complex networks.
Older Simple Networks
The original simple networks connected individual users and their computers (originally terminals) to a router or switch. The router or switch then facilitated communication between the other devices on the network such as other servers, network storage, and printers. When the internet arrived, the network added a firewall to protect networks and users as they connected to the world wide web.
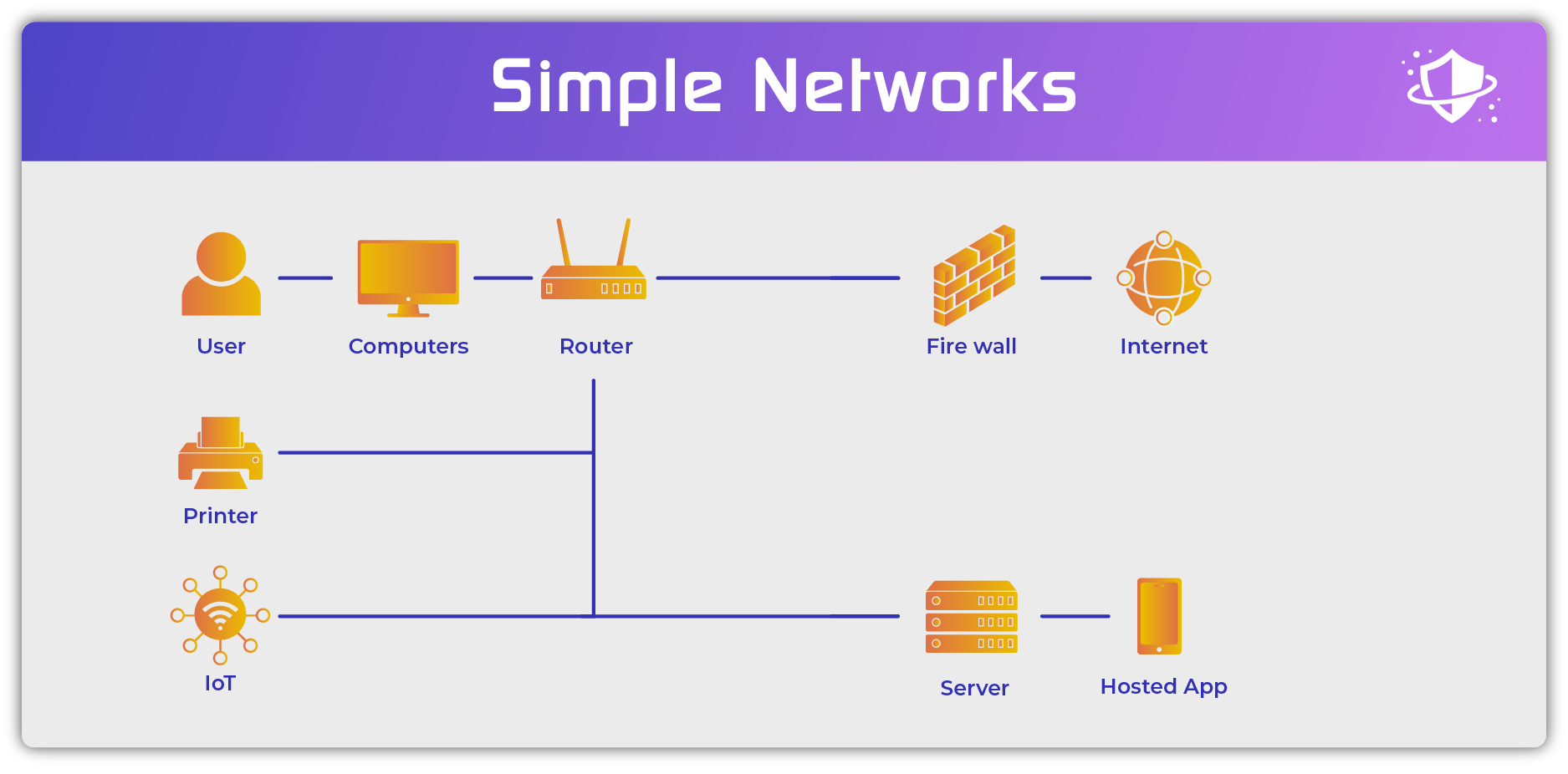
In this simple environment network security followed a simple protocol:
- Authenticate the user: using a computer login (username + password)
- Check the user’s permissions: using Active Directory or a similar Lightweight Directory Access Protocol (LDAP)
- Enable communication with authorized network resources (servers, printers, etc.)
- Monitor local communications: using passive intrusion detection systems (IDS) or active intrusion prevention systems (IPS)
- Monitor authorized and block unauthorized connections outside of the network: using firewalls
This structure assumed that all needed resources resided within the network, all communication within the network was authorized, and all users were authenticated. In a complex, modern network, this assumption falls apart.
Newer Complex Networks
Modern networks encompass far more users, assets, and types of connections than originally envisioned. Some of the basic steps remain the same, but the details have become far more complicated.
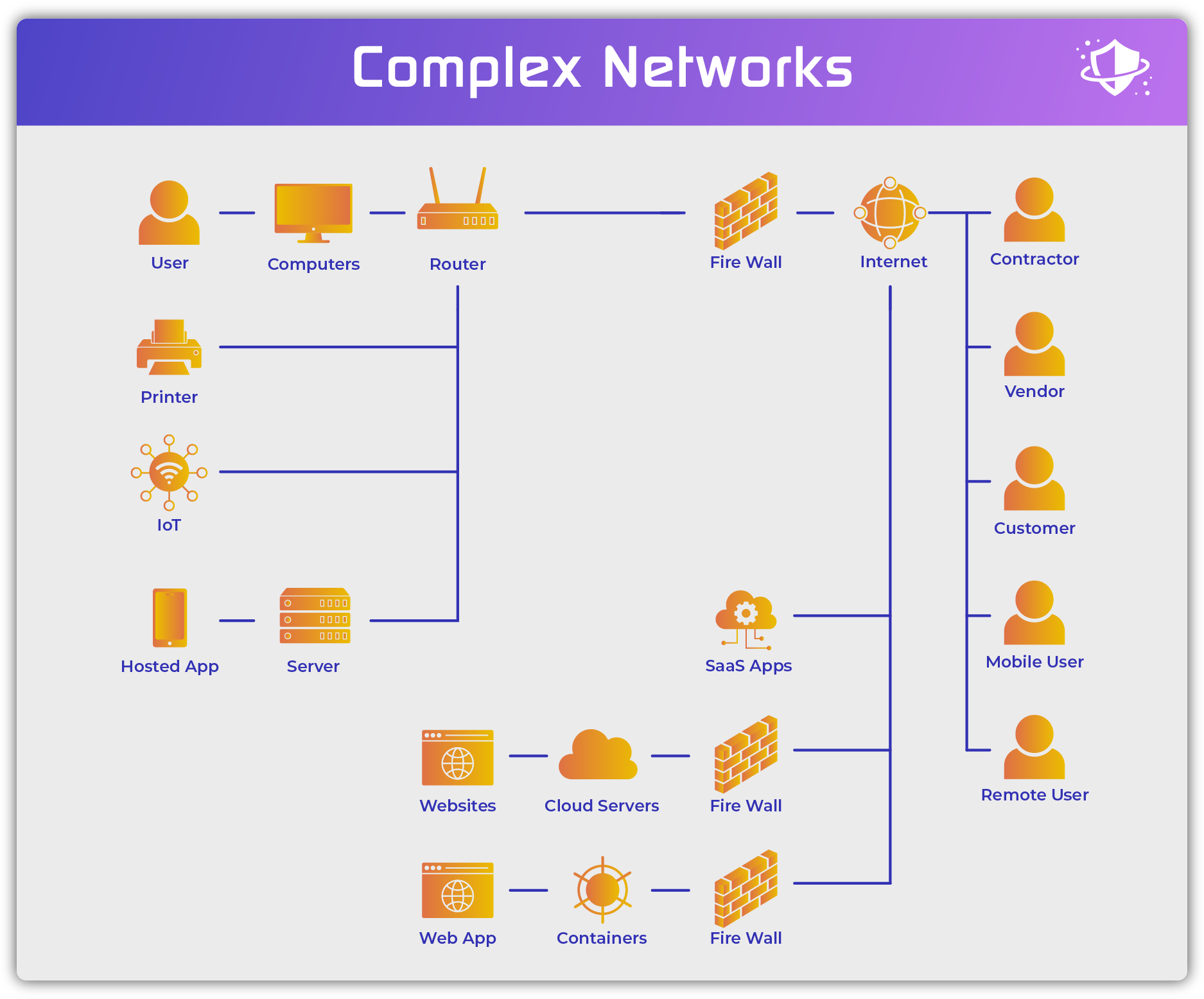
Users now encompass both local and remote employees. Vendors, customers, and contractors also frequently access resources within or directly connected to the network. Applications and services now act as users as well since they make active connections to devices, databases, and applications inside the network directly or through APIs.
Devices now consist of both corporate devices and uncontrolled BYOD devices consisting of computers, laptops, tablets, and mobile phones. Both virtual and physical servers, endpoints, and containers can be located in local data centers or remotely in branch offices or hosted in the cloud. The internet of things (IoT), operations technology (OT), and the industrial internet of things (IIoT) also now connect to networks.
Connections still encompass hard-wired physical switches and routers, but also now include wireless cellular networks, wi-fi networks, virtual networks, cloud networks, and internet connections.
Access points still require firewalls, but often include methods for external connections into the network such as virtual private networks (VPNs), remote desktop protocol (RDP) and network controllers for securing remote users using remote resources (secure gateways, secure access service edge (SASE), etc.).
Data now exists across the organization inside applications (databases, email, etc.), in cloud repositories (S3 buckets, data lakes, etc.), in Software-as-a-Service applications (CRM, file-sharing services, etc.), on mobile devices, home and international offices, and much more. Network security controls and tools should ideally shield, monitor, and secure the data in all of these environments.
How Network Security Works
Networks connect assets for the purpose of communication. Network security ensures the integrity and confidentiality of the communication as well as verifying appropriate connections based upon the identity of the user, type of device, and classification of data.
Network Security Controls
Network security accomplishes these mandates through the implementation, maintenance, and enforcement of physical, technical, and administrative controls to facilitate authorized use and deny access to threats and inappropriate use of network resources.
Most network security vendors focus on providing hardware and software solutions to deliver technical controls that use applications to authorize, authenticate, facilitate, protect, and monitor networking traffic. Technical controls may be implemented by:
- Hardware appliances: switches, routers, firewalls, etc.
- Software: virtual routers, intrusion prevention systems (IPS), etc.
- Configuration: closing ports used for peer-to-peer traffic, dropping malformed communication packets, etc.
Organizations bear the responsibility to ensure that physical controls ensure only authorized access and changes to networking equipment such as routers, cables, switches, firewalls, and other networking appliances. This requirement may be implemented by vendors in hosted or colocated environments, but the organization maintains the responsibility to verify satisfaction of the requirement.
All organizations implement at least rudimentary administrative controls by adding user names to an LDAP or Active Directory. However, many organizations can improve network security capabilities through more detailed policies. Network security enforces policies through the technical tools and detailed policies enable granular access controls based upon user groups, user-specific needs, time-specific restrictions, or other rules that can limit authentication and access to the network or to allow network changes.
To secure communication, networking equipment use a variety of protocols to verify packet integrity and to deliver packets to the correct devices. Encryption will regularly be used to protect the data from interception. To ensure appropriate connections, networks match users, devices, resources, and permissions based upon policies established within Active Directory or similar LDAP solutions.
Network security excludes any unauthorized access to assets or communication. Better network security monitors for attempts to exceed permissions, unusual behavior from authorized users, and network activity that may indicate compromise or malware activity.
To verify the effective and appropriate implementation of network security, auditing should be performed to verify successful implementation of policies and controls. Often auditing will be performed through the review of networking logs, but penetration testing and vulnerability scanning can also be used to check for proper implementation and configuration.
Network Layers and Data Encapsulation
The Opens Systems Interconnection (OSI) model divides communication into seven different layers. In practice, these layers may often become blurred, but the model helps with conceptualization and the development of standards. Network security professionals understand that communication occurs throughout the range of layers and security solutions need to encompass all layers in some fashion.
- Physical: bits flowing through wires or within wireless signals
- Data Link: Parses communication into data frames, or smaller chunks of data, containing a portion of the data communication between two nodes: any sending or receiving device within the network such as computers, routers, switches, gateways, etc.; smaller frame sizes allow for more efficient transmission and error checking
- Network: data packets adding addressing, routing, and traffic control data to a data frame
- Transport: variable-size data frames transmit from host-to-host across the network maintaining quality-of-service
- Session: Creates, controls, and ends communication between the sender and receiver
- Presentation: Establishes the data formatting and translation, including functions such as encryption, compression, and graphic commands
- Application: Direct interaction with the software application initiating and receiving the communication such as a browser, file-sharing program, etc.
The internet protocol suite (TCP/IP) uses a simplified model that describes the encapsulation of data transmitted by the protocol:
- Application: creates the data to be sent
- Transport: performs the host-to-host communication
- Internet: Takes the transport-layer data and encapsulates it with an IP address header that obscures local network connection information and routes the data to the end host
- Link: Breaks the data into frames and adds frame headers and frame footers; manages the local network links for transmission
Security Principle: Defense in Depth
Defense in depth applies to all cybersecurity. The concept acknowledges that no single security control will likely address all threats, all of the time. Instead, multiple types of controls will need to be implemented that reinforce each other so that risks will be mitigated even if a single control fails.
In the broadest sense, defense in depth uses:
- Data security: protects data at rest and in transit such as encryption, database security, message security, etc.
- App security: security for local and remotely hosted apps (web application firewalls, workload security, local access controls, etc.)
- Endpoint security: protects endpoints with antivirus, endpoint detection and response (EDR) tools, etc.
- Network security: controls access between resources and ensures safe communication using firewalls, network access control (NAC), intrusion detection systems, etc.
- Access security: Control access between assets inside the corporate network or even to cloud assets using firewalls, virtual private networks (VPNs), secure web gateways, etc.
- User authentication: verify users, authenticate identities, and authorize levels of access using passwords, biometrics, multi-factor authentication, active directory, etc.
- Policies, procedures, and user training: educate users, IT staff, and security teams regarding expectations, rules of behavior, standards, and methods of maintaining security and addressing incidents.
In addition to these layers, defense in depth requires verification of all layers using:
- Design: create a robust architecture for operational and security resilience
- Testing: verify all components working correctly through penetration testing and vulnerability scanning
- Monitoring: watch for unusual, unapproved, and malicious actions through security incident and event management (SIEM), security operations centers (SOCs), and network operations centers (NOCs)
- Maintenance: patch management, replacing obsolete technology, etc.
- Training: employees need to be continuously trained to keep up with the latest tools, technologies, tactics, and controls
- Auditing and reporting: checking logs, generating reports for key performance indicators (KPIs) or compliance
Security Principle: Least-Privilege Access
Least privilege access ideally requires that users should access only the data, devices, and applications required for them to perform their work at exactly the time that those resources are required and at the lowest level of privilege they need. Of course, such dynamic and fine-grain control currently is not technically feasible for most organizations.
However, organizations should still enforce the principle of least-privilege access through Active Directory groups, database and server folder restrictions, device controls, access credentials, and more. Many organizations tend to provide generous levels of access to avoid operational delays, but from a security perspective, the opposite tact should be enforced. An organization should only provide access when, and if, required — and even then, the access granted should be the minimum access level needed to perform the specific task.
What Are the Main Network Security Threats?
Threats to network security endanger the operational or security integrity of the network or its data. Threats fall into the following main categories:
Bad Users
Bad users consist of misconfigured apps, hackers, and other unauthorized users that intentionally, or unintentionally attempt to access network resources. This can occur through stolen credentials, fired employees with active credentials, command-and-control viruses on endpoints, stolen laptops, misconfigured API connections, and much more.
Bad Devices
Bad devices consist of unauthorized devices or devices in a compromised state. Unauthorized devices could be more innocent such as an employee connecting an unauthorized personal computer to the ethernet network, the marketing department installing a wi-fi-connected TV in a conference room, or the industrial pump motor vendor connecting their latest delivery to a 5G cellular network for remote monitoring.
Far more dangerous devices would be workstations missing critical security updates for the operating system, a virus-infected laptop, or a hacker’s laptop connecting to the wi-fi network from the public parking lot. Networks need to constantly monitor for unknown connections, unusual behavior, and compromised devices.
Bad devices can also include attacks that attempt to steal or redirect network traffic to connect to malicious resources. For example, hackers can use packet sniffers or a phishing link using a man-in-the-middle attack. Other hackers might use a spoofed domain name system (DNS) or IP addresses to redirect users from legitimate connections (to websites, servers, etc.) to attacker-controlled endpoint resources in order to steal login information or infect the endpoint with malware.
Malicious Traffic
Networks intend to connect valid users with valid assets. However, when malware or attackers seek to penetrate the organization, their traffic also passes through the network and can sometimes be detected. Other traffic is not itself malicious, but instead suggests malicious intentions such as the warehouse shipping computer connecting to the Human Resources (HR) server or a wireless security camera attempting to connect to the cloud credit card processing database.
Malicious Intentions
Insider threats occur when legitimate users connect to legitimate assets to perform unauthorized actions using authorized permissions. For example, the VP of sales has legitimate access to the salesforce CRM and the internal customer database, but downloading the full client list from each source would be a sign the VP is ready to change jobs and steal the information.
Other users might attempt to exceed their intended access, such as when the marketing intern attempts to access an R&D file server and download IP in development. Not all insider threats need to be malicious; some might simply be sloppy or simple mistakes such as when IT operations accidentally overwrites a firewall website whitelist and suddenly blocks all internet traffic.
Poor Maintenance
The best security tools and architecture will be undermined by poor maintenance practices. Organizations that lag in performing software updates, or replacing obsolete components will struggle to prevent attacks.
Operations Disruption
While most attacks target endpoints (user computers, servers, etc.), some attacks seek to disrupt operations instead. Distributed denial of service (DDoS) attacks currently will be used more often against internet-exposed resources, but can also be used by an attacker to take down networks and internal servers. Unintentional or malicious misconfiguration of segmentation or network equipment can also result in fragile or non-functioning network connections, unstable traffic flows, and similar operations disruptions.
Related Cybersecurity Threats
Many cybersecurity threats indirectly affect networks through related assets. For example, malware, spyware, adware, computer worms, botnets, trojan horses and similar malware do not normally impact network equipment (routers, firewalls, etc.) or network traffic. If it doesn’t affect the network, it is not a network threat. Instead, these attacks harm endpoints (user computers, servers, containers, etc.) and threaten applications and data hosted on those endpoints.
While network security should examine network traffic to catch indicators of these types of attacks and prevent them when possible, the primary responsibility to stop these attacks relies upon the relevant security for the point of attack: email security (phishing, malicious attachments), application security (cross-site scripting, SQL injection, etc.), endpoint security (antivirus, Endpoint Detection and Response, etc.), DNS security (IP address redirection, etc.), and Active Directory security (credentials promotion, adding users, etc.).
Best Practices for Protecting Your Network
Best practices for network security directly counter the major threats to the network with specific technologies and controls.
User Access to Control Bad Users
To protect against unauthorized users, network security needs to implement effective access control and effective remote access control to the network. At a minimum, an organization should use Active Directory (or an equivalent LDAP), two-factor authentication, and VPNs. Organizations should also coordinate IT and HR functions for simultaneous activation and deactivation of employee credentials and employment status.
Organizations can implement better security through:
- Improved user management with more detailed access controls
- Multi-factor authentication
- Improved remote access to control access to resources hosted outside of the network such as OneDrive, SaaS solutions, etc. Secure remote connections can also prevent certain types of packet interception and packet re-routing attacks such as man-in-the-middle or packet sniffing.
- Cloud-based VPN Services
- Secure web gateways
- Updated local VPN solutions (do not use RDP)
- Secure Browsers
Asset Discovery to Control Bad Devices
To protect against unauthorized or compromised devices, organizations at a minimum must perform periodic inventories of devices connected to the network, install and maintain updated endpoint antivirus software, and monitor key assets (financial databases, HR files, key intellectual property, etc.) for unauthorized access.
Organizations can implement better security through:
- Tight asset access management
- Continuous scans for unauthorized devices prevent unauthorized access using IT Asset Management (ITAM) tools
- Network access control (NAC) solutions test for outdated or vulnerable software on endpoints and redirect devices to quarantine until remediated
- Mobile Device Management (MDM) restricts applications on mobile devices and can also check the status of the device for jailbreaking, obsolete OS, or malware
- Limit device and application access
- Associate devices with specific users and specific access
- Create whitelists or allow lists of specific assets allowed to make connections, particularly for critical resources
Far more dangerous devices would be workstations missing critical security updates for the operating system, a virus-infected laptop, or a hacker’s laptop connecting to the wi-fi network from the public parking lot. Networks need to constantly monitor for unknown connections, unusual behavior, and compromised devices.
Bad devices can also include attacks that attempt to steal or redirect network traffic. For example, hackers can use packet sniffers or a phishing link using a man-in-the-middle attack to steal network traffic. Also, spoofed domain name system (DNS) and IP addresses can redirect users from legitimate connections to dangerous and malicious websites and endpoints for the purpose of stealing information or infecting the endpoint with malware.
Packet Analysis and Monitoring to Control Bad Traffic
During an attack, network traffic may contain known indicators of compromise (IoCs), known malicious file signatures, or direct traffic to known malicious URLs and IP addresses. Firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), network detection and response (NDR), extended detection and response (XDR), and similar systems can inspect the packets to detect, block, or quarantine the malicious traffic.
Other times, the traffic itself may not be recognized as malicious, but monitoring by a security incident and event management (SIEM system), security operations center (SOC), or similar monitoring solution may detect unusual connections. See also Activity Monitoring to Control Bad Intentions, below.
Activity Monitoring and Segmentation to Control Bad Intentions
Malicious and accidental insider threat activities can be detected using tools such as data loss prevention (DLP), user entity and behavior analytics (UEBA), or artificial intelligence-enhanced behavior analytics built into firewalls and IDS/IPS solutions. Deception technology using honeypots and similar subterfuge can trigger proactive alerts of both hackers and authorized users that might be attempting to perform malicious actions.
Unexpected accidental or malicious changes to network systems will be caught more quickly and more effective when using change control. Change control tracks changes associated with users and devices to ensure that all changes are authorized, approved, and reported.
With the rise of software defined perimeters (SDP), software defined wide-area-networks (SD-WAN), and zero trust network access (ZTNA) organizations further control access at a granular level to prevent internal threats. Not only can virtual networks expand the scope of a network to encompass cloud resources or resources in geographically dispersed locations, they can also create segmentation and microsegmentation based on user groups (vendor, consultant, marketing department, etc.), access levels (basic user, admin, etc.), or even specific users or applications. If adequately defined by identity and access management tools, microsegmentation can even limit the ability for stolen credentials to harm the network or reach unauthorized resources.
Patching, Updating, and Testing Controls Bad Maintenance
To prevent maintenance-related issues, organizations should implement regular patching, updating, and testing (vulnerability scans, pen tests, etc.) of their network. Vulnerability scans and penetration tests should also catch misconfigurations, unapplied or incorrectly applied encryption, sloppy encryption key management, weak passwords, missing authorization, and other common issues.
Monitoring and Resilience Controls Operations Disruption
Operations disruptions can be detected, mitigated, or controlled through network monitoring through solutions such as network operations centers (NOCs), security operations centers (SOCs), and security incident and event management (SIEM) tools. Some anti-DDoS software and other resilience capabilities will also be built into routers, firewalls, etc. Change control tracking can also help security and operations teams to quickly analyze disruptions originating from changed network settings.
Beyond software, physical security and resilient architecture design also play a large role in preventing network disruptions. Resilient architecture using load balancing and redundancy can absorb initial volumetric DDoS attacks to give incident response a chance to mitigate the attack without business disruption.
For cloud-based networks, organizations can also implement hyperscale architecture that combines security, storage, compute, and virtualization layers into a modular resource that can be deployed automatically and at scale. However, hyperscale architecture should also be monitored to ensure that it does not deploy financially unreasonable resources.
Read more: Network Protection: How to Secure a Network
Types of Network Security Solutions
Many tools and solutions contribute to the various layers and requirements of network security. This section provides a brief overview of common tools.
Cloud Access Security Broker (CASB)
Whether implemented as a separate tool or incorporated into other tools, cloud access security broker (CASB) solutions provide cloud-based authentication and authorization for users and applications. These tools were originally developed for controlling access to software-as-a-service (SaaS) applications and are commonly integrated into secure access service edge (SASE) solutions.
Data Loss Prevention (DLP)
Organizations deploy data loss prevention (DLP) solutions to detect and prevent internal and external threats that attempt to steal or alter critical data.
Deception Technology
Deception technology creates false data repositories, users, and other assets and plants them within the IT ecosystem. When attackers attempt to access or investigate these assets, also known as honeypots, alerts will immediately be generated to enable security teams to recognize inappropriate behavior and take action.
Enterprise Mobility Management and Mobile Device Management (MDM)
Similar to ITAM solutions, enterprise mobility management (EMM) and mobile device management (MDM) solutions focus on the management and control of mobile devices. Some enterprise mobile management (EMM) solutions control both the device as well as mobile application management (MAM) for additional control.
Encryption
Security teams should no longer assume that networks are safe. The data flowing through networks should be encrypted for transmission inside and outside the network.
eXtended Detection and Response (XDR)
Extended detection and response (XDR) tools merge endpoint protection and network security functions to provide a unified security solution. Depending upon the vendor other capabilities for security response or user behavior analytics will be included.
Firewalls
Firewall technology acts as a gatekeeper and guardian of network traffic. Modern firewall technologies can perform deep packet inspection and filtering to detect viruses, block known malicious websites, and many other protections. Commonly used technologies include:
- Firewall-as-a-Service (FWaaS) tools host scalable firewalls on the cloud for global reach and control
- Next-Generation Firewalls (NGFW) tend to be local physical or virtual appliances that add threat detection, intrusion prevention, protection for newer types of assets (containers, IoT, etc.), threat intelligence, artificial-intelligence enhanced analytics, and capabilities for virtual networks
- Unified Threat Management (UTM) solutions combine firewalls, secure web gateways, secure email gateways, remote access, intrusion detection and prevention capabilities, and other security functions
- Web Application Firewall (WAF) can be installed in front of specific websites, web servers, and applications to add additional layers of security tailored for the specific asset
Identity and Privileged Access Management (IAM/PAM)
Active Directory and other LDAP solutions can be difficult to manage at scale, but network security requires strong user management. Identity access management (IAM) tools enable organizations to integrate IT and HR systems to quickly onboard, categorize, manage, and offboard employees. Privileged access management (PAM) tools (or features integrated into some IAM tools) specifically manage privileged access to key resources: data, applications, and infrastructure.
IT Asset Management (ITAM)
IT Asset Management (ITAM) tools assess the assets connected to the network and help to manage patching and updates on standard devices. To ensure a good fit for network security needs, ITAM tools should detect more than just PCs and laptops. Preferably, ITAM should also detect network equipment, cloud assets, Internet of things (IoT), Industrial Internet of Things (IIoT), Operational Technology (OT), and mobile devices (phones, tablets, etc.).
Intrusion Detection Systems / Intrusion Prevention Systems (IDS/IPS)
Intrusion detection systems (IDS) inspect network traffic for malicious activities and send alerts to network operations centers (NOCs), security operations centers (SOCs), and security incident and event management (SIEM) tools. Intrusion prevention systems proactively block and quarantine malicious or suspicious network traffic.
Combined detection and prevention solutions (IDPS) offer both capabilities, and IDPS features are often incorporated into firewalls and other security solutions. Specialized wireless IPS (wIPS) solutions focus on securing wi-fi networks.
Multi-factor Authentication (MFA)
To protect a network against stolen credentials, organizations should require at least two-factor authentication (2FA) to confirm identity. SMS should be avoided, especially for critical resources, because of its weakness to interception, spoofing, and SIM-card swap attacks. Multi-factor authentication (MFA) adds additional biometric, device, user, and other characteristics to confirm identities and authenticate users.
Network Access Control (NAC)
Network access control (NAC) solutions can provide a range of capabilities to detect all assets connecting to the network, quarantine devices that do not meet security requirements, and block unauthorized devices. More sophisticated NAC solutions will enable risk assessments, onboarding processes, and event reporting.
Network Operations Center (NOC)
Network operations centers (NOCs) tend to focus on operational concerns such as maximizing uptime, bandwidth, and eliminating choke points. However, NOC teams can often detect unusual traffic patterns that may come from malicious activity.
Network Segmentation
Network segmentation and more granular microsegmentation create segregated sections of the network. Traffic from one segment cannot directly flow to other segments without passing through routers or firewalls, which can perform security inspections.
Penetration Testing
To verify sufficient security in place for networks and other IT infrastructure, organizations can perform penetration testing. Penetration tests test the capabilities and effectiveness of existing controls to confirm if they sufficiently reduce the risk of attack for the organization.
Role-based Access Control (RBAC)
Role-based Access Control (RBAC) can be implemented as a specialized tool or deployed as a feature in IAM to assign access control to specific roles and their requirements.
Secure Access Service Edge (SASE)
Traditionally, the firewall marked the beginning of the network and corporate assets. However, modern use of cloud resources, remote work, and SaaS solutions place many corporate resources outside of firewall protection. Secure access service edge (SASE), also known as the security service edge (SSE), extends security to encompass cloud resources.
Secure Remote Access
Most organizations require some form of remote work and need safe ways to grant secure access to network resources. Remote desktop protocol (RDP) can no longer be considered safe, so other solutions should be considered instead:
- Secure web gateway (SWG) technology allows both internal and external network users to benefit from the protection of a consolidated cloud-hosted gateway to access internal and external resources
- Virtual private network (VPN) technology creates encrypted tunnels between the endpoint and the network; this technology can cause operational bandwidth issues unless adopting cloud-based VPN services
- Virtual desktop instance (VDI) and desktop-as-a-service (DaaS) technology treats the user’s machine as a terminal to log into a thin-client service that contains access to all applications and network resources
Security Incident and Event Management (SIEM)
Security incident and event management (SIEM) tools collect logs and alerts from endpoints, network equipment, and monitoring solutions. Security teams in Security Operations Centers (SOCs) or in managed detection and response (MDR) teams can use SIEM tools to analyze alerts to detect and stop attacks in progress.
Security Operations Center (SOC)
Security operations centers (SOCs) centralize security teams to monitor systems for signs of attack, respond to recognized threats, and stop attacks. SOCs use a variety of security tools to receive alerts and log information throughout the IT infrastructure.
User Entity and Behavior Analytics (UEBA)
Dedicated user entity and behavior analytics (UEBA) tools and UEBA features incorporated into other tools monitor user, device, and data trends to detect unusual and malicious behavior. Advanced tools can incorporate artificial intelligence (AI) or machine learning (ML) to accelerate detection.
Virtual Networks
Software defined perimeter (SDP) technology such as software defined wide area network (SD-WAN) solutions create virtual networks that can be subsections of existing wired networks or globally-spanning networks of specific assets. These tools expand the scope and definition of networks, yet they also introduce new tools for security and operations management.
Vulnerability Scanning
Security teams cannot assume proper maintenance or configuration for IT infrastructure. Vulnerability scanning should be performed on networks and other assets to verify appropriate levels of maintenance and security.
Whitelisting
Also known as allowlisting, whitelisting creates finite lists of allowed users, devices, IP addresses, or services allowed to connect to a network or specific network asset. Whitelists tend to be fragile and tedious to maintain in modern environments with changing employees, new equipment, and virtual devices that can be launched with variable IT addresses. However, for the most critical assets, whitelists can effectively lock-down security.
Zero Trust Security
Zero trust security holds that nothing should be assumed to be trusted. All users, devices, apps, and traffic should be continuously verified for authentication and authorization. Zero trust network access (ZTNA) is popular, but only one of the possible zero trust tool categories and techniques that can be applied to network security.
Complementary Security Solutions
Network security plays an important role, but it is not independent from the rest of the security stack. Effective network security depends upon the proper application and implementation of complementary security solutions such as:
- Active Directory Security
- Application Security
- API Security
- Cloud Security
- Container Security
- Database Security
- Digital Rights Management (DRM)
- DNS Security
- Email Security
- Endpoint Security (antivirus, EDR)
- Sandboxing (investigation tool)
- Workload security
- Web security
What Are the Benefits of Network Security?
Effective network security decreases the two key risks to the organization: disruption of operations and compromised data. Reducing the risk of operational disruption protects the organization against downtime and inaccessible resources that lead to business losses and reputation damage.
Reducing the risk of compromised data avoids damages resulting from several types of data such as:
- Intellectual Property Theft
- Personal Identifiable Damage (PII)
- Healthcare data
- Customer data
- Financial information (bank accounts, credit card payments, etc.)
Some types of data theft threaten future revenue (IP, customer) and other data thefts expose the company to fraud or phishing attacks (financial, customer). Most organizations will be most concerned about PII, healthcare, credit card, and other regulated data that typically results in formal investigations, regulatory fines, and public notices.
All damages noticed by employees, customers, vendors, regulators, or the public result in damaged business reputations.
6 Core Network Security Challenges
Regardless of the types or comprehensiveness of an organization’s network security, each organization faces similar challenges. These challenges affect the implementation, maintenance, and ongoing effectiveness of existing network security.
Balancing Conflicts
Implementing network security can affect operations and user experience — typically to the detriment of performance. For example: Inspecting packets can add transmission delays, adding jitter to video and audio calls or playback. Security and operations teams need to balance the conflicting stakeholders needs to achieve a compromise that meets the risk reduction goals of the organization.
Evolving Attacks
Ten years ago, most outside of IT never heard of ransomware. Even though it is an older technology, ransomware had fallen out of favor because hackers found it too difficult to execute at scale for years. Attackers improved their technologies and now ransomware poses a critical threat with high awareness.
Similar evolutions also expand the scope of network security such as remote work, SaaS applications, containers, data lakes, IoT, etc. Evolution will continue to occur and security tools will need to keep pace with attackers, new vulnerabilities, and new asset classes.
Encryption
Encryption provides critical security for data in transmission through the network, but encryption also poses significant threats from current and future attacks. Currently, attackers also incorporate encryption into their malware to protect the malicious traffic against network inspection, which puts more burden on security monitoring, endpoint protection, and other technologies to detect attacks.
New protocols and algorithms also continue to be updated as vulnerabilities become exposed. Older transport layer security (TLS), Transmission Control Protocols (TCP), and many different encryption standards should no longer be used and the arrival of quantum computing puts other encryption standards at risk.
Dependence
All types of security depend on other security implemented correctly. Network security is no exception and any missed software update, unprotected endpoint, or improperly classified user could undermine strong and effective network security.
Human Error
The best technology can be rendered useless by a human mistake during installation, maintenance, monitoring, or configuration. While uneducated users will often create the most problems, administrators also suffer from simple mistakes — especially when working long hours or responding to sudden emergencies.
Staffing Troubles
Technical talent for IT and security remains at a premium. Recruiting, retaining, and training an adequate staff poses expensive and difficult challenges for most organizations. Without adequate staff, organizations may need to turn to expensive tech solutions or accept higher levels of risk.
Third-Party Exposure
Technology enables tighter relationships and intertwined IT between an organization and its vendors, suppliers, and customers. However, as data sharing and access becomes more common, the risk of an intentional or unintentional data breach through non-employees also continues to grow. Similarly, organizations must try to monitor and control for technology supply chain corruption, unpatched vulnerabilities, and compromised service providers (hacked MSSP, etc.).
Starting a Network Security Career
The best network security teams contain expertise in network infrastructure, network security tools, and strong familiarity with malware and attack methods. Prospective network security engineers often start in networking operations or on the help desk. Understanding basic networking and device management will be critical in addressing typical daily tasks.
Penetration testing and IT architecture design can also be useful skills, but some organizations will outsource these specialties. Related specializations such as endpoint security, incident response, or application security could also be useful, but often these experts will make up the broader security team and not generally transition to network security.
To obtain a position as a network security engineer, novices can help their cause through certificates that demonstrate academic understanding of security or networks. Vendor specific networks can be useful for organizations that deploy that technology, but broader, vendor-agnostic academic cybersecurity certifications will be more universal.
- Vendor-specific certificates
- AWS Advanced Networking
- Azure Network Engineer
- Cisco Networking (5 levels)
- Fortinet Networking Security Expert
- Google Cloud Engineer
- Juniper Networking (Design, Security, Cloud, etc.)
- Palo Alto Networks
- Vendor-agnostic Certification
- CompTIA (Ethical Hacking, Network+, Security+, etc.)
- EC Council (Certified Hacker, Network Defender, etc.)
- ISACA (CISA, CISM, etc.)
- Offensive Security (penetration testing)
- SANS (Cloud, security management, pen testing, etc.)
Bottom Line: Network Security as a Critical Component of a Broader Cybersecurity Plan
Network security plays an important role in supporting and reinforcing a comprehensive cybersecurity stack. Even for organizations attempting to pursue a pure-SaaS environment without a formal network, the principles of network security will still apply to controlling access and protecting against data leaks from their SaaS and cloud resources.
However, while extremely important, network security must be integrated into a full security stack of complementary security tools, supported by a well-trained IT security team, and regularly monitored by a security operations team. The best organizations will also bolster both network security and their broader cybersecurity program with risk assessment, business continuity plans, and security awareness training to drive security awareness and operational resilience throughout the organization.
For better or worse, security can never be finished. New vulnerabilities and attack methods will constantly require new tools and techniques. Organizations must build continuous testing, monitoring, and improvement into their security stack — including network security.
For more on network and other cybersecurity, see:








