The best way to prevent ransomware is also the best way to prevent any malware infection – to implement security best practices. Of course, if best practices were easy, no ransomware attacks would occur.
All organizations, even the most prepared, will be vulnerable to ransomware attacks to some degree. The most resilient organizations must not only prevent ransomware attacks by implementing security to prevent infections from occurring, but also use strategies to limit the damage of successful attacks, alert teams promptly of potential infections, and effectively react to attacks.
Table of Contents
What is Ransomware?
The term ransomware applies to a broad spectrum of attacks and tools that seek to encrypt data and then hold the data ransom in exchange for a decryption key. Over the past couple of years, attackers have evolved their attacks to also include data exfiltration and extortion schemes that threaten public release of the victim’s data unless the ransom demand is paid.. Ransomware attacks hit the headlines every week, with governments, school districts, healthcare providers, and private companies forced to admit attacks after ransomware disrupts their operations. Healthcare ransomware attacks have even been linked to patient deaths.
While most attackers typically use ransomware to extort money, some attackers instead use ransomware to camouflage other types of attacks such as:
- Russian hackers deployed the 2017 NotPetya ransomware attack against companies doing business in the Ukraine. No ransoms could be paid, the malware solely sought to disrupt operations.
- The North Korean Lazarus group deployed ransomware to erase forensic evidence in its 2017 attempt to steal money from the Far Eastern International Bank of Taiwan.
- Attackers deploy the ONI ransomware on critical assets to wipe and conceal the true targets of the attackers within the Japanese corporate victims.
Recently, ransomware gangs seek to move faster and avoid detections that focus on the encryption process. While these attacks technically no longer count as ransomware, businesses still need to guard against similar attacks that seek to corrupt data after exfiltration or simply extort businesses based on the threat of leaking stolen data.
Ransomware recovery resources:
- How to Recover From a Ransomware Attack
- Best Ransomware Removal Tools
- Best Ransomware Removal and Recovery Services
- How to Decrypt Ransomware Files – And What to Do When That Fails
How to Identify Ransomware
Once inside a business, malicious hackers can deploy many types of malware or attack systems in many different ways. For many victims, they only recognize a ransomware attack once their data is encrypted and the ransom notes are found, as in the screen and text messages from the infamous REvil ransomware group below (Sources: Arista Networks and Qualys).
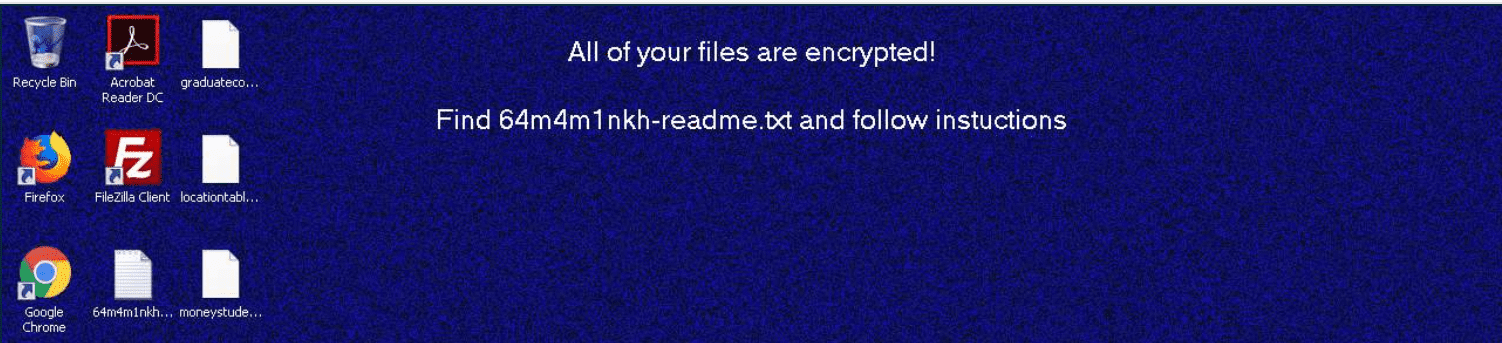
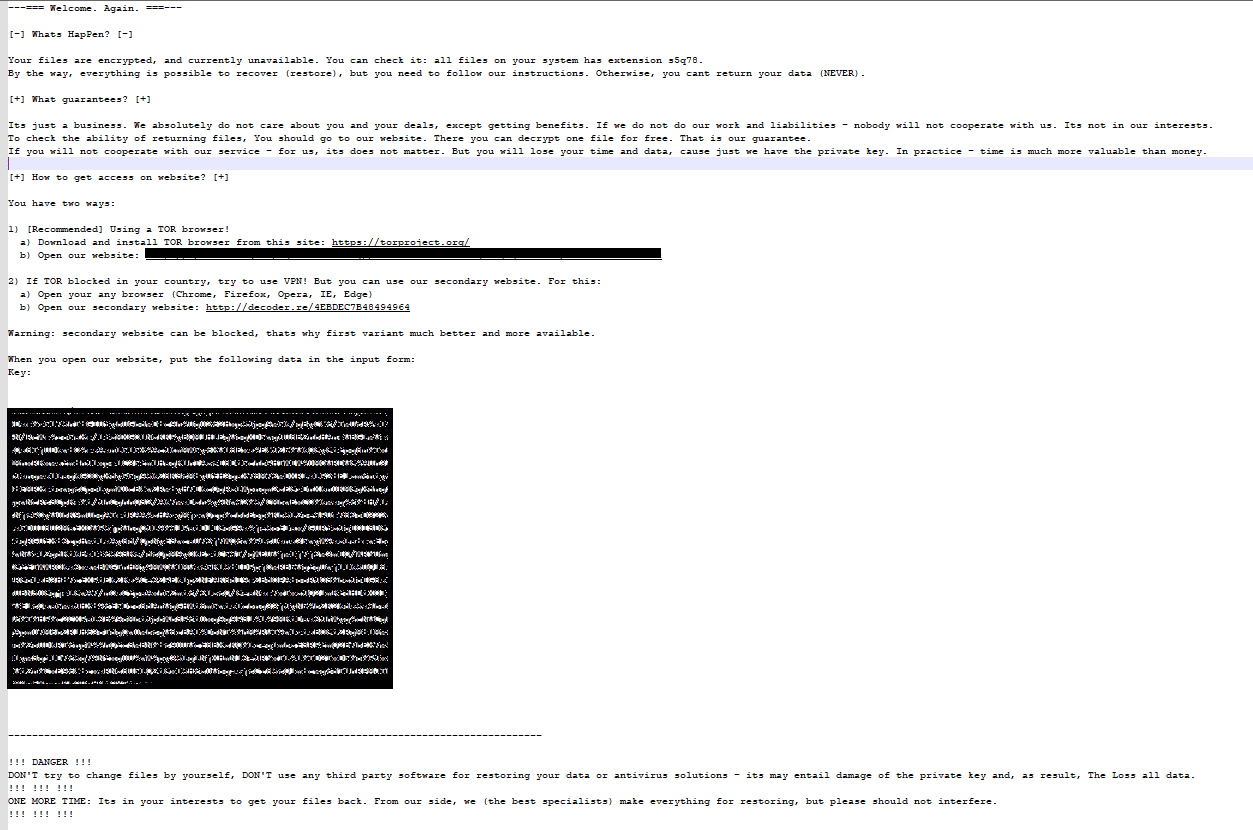
When trying to catch ransomware attacks earlier in the process, defenders watch for indicators of compromise such as:
- Known malware, such as viruses or malware signatures captured by email, endpoint, firewall, or network monitoring software
- Data copied outside of the environment in large quantities
- Attempts to delete local or network backups
- Active encryption of data
- Attempts to download or execute hacking toolkits
- Unusual attempts to use PowerShell
Simple ransomware attacks use semi-automated malware to spread itself through networks and execute the ransomware. Sophisticated attacks use command and control servers, PowerShell commands, and active exploration of the network by attackers in combination with malware and malicious use of standard tools.
Also read: Exfiltration Can Be Stopped With Data-in-Use Encryption, Company Says
Am I Vulnerable to Ransomware?
Everyone is vulnerable to ransomware.
Regardless of the amount of training, people keep clicking on phishing emails and opening holes in security. Regardless of the quality or quantity of layers of security deployed, zero-day vulnerabilities, deployment mistakes, and human error can create security gaps that attackers will eagerly exploit.
The effective questions that need to be asked should be:
- What does the organization have in place to prevent a ransomware infection?
- What does the organization have in place to limit the damage of a successful attack?
- What does the organization have in place to alert against infection?
- What does the organization have in place to react to an attack?
We will explore these questions and provide suggestions for suitable answers in the next sections to follow.
The Bare Minimum Ransomware Prevention
Implementing all possible IT security best practices is beyond the resources of many organizations, but even small organizations can find ways to implement a significant number of best practices at low cost through open-source tools, adopting software-as-a-service (SaaS) products, or by engaging service providers such as:
- Managed security service providers (MSSPs);
- Managed IT service providers (MSPs); and
- Managed detection and response (MDR) vendors.
The smallest organizations with the most limited resources should at least implement effective backups and endpoint protection software. This combination will prevent many types of ransomware infections and allow the company to recover as quickly as possible from those that succeed.
Also read:
Ransomware Infection Prevention Best Practices
Ransomware prevention requires creating reinforcing layers of security to prevent an attacker or malware from entering the secured spaces of the organization. Key components of this strategy seek to protect devices, block common infection vectors, minimize human error, and check for gaps in the security.
Secure Devices
Many ransomware attacks launch on the endpoint. Effective endpoint security implements defense in depth to add layers of security to increase the difficulty for ransomware attacks to launch or to avoid detection.
- Endpoint Security: Antivirus provides a baseline level of protection against established ransomware malware. However, to defend better against new variants or new malware, organizations should consider upgrading to next-generation antivirus (NGAV) or endpoint detection and response (EDR) tools.
- Multi-Factor Authentication (MFA): Critical resources, such as servers that host key applications or services like Active Directory (AD) and Domain Name Systems (DNS), should be protected by multiple factors and methods of authenticating the user.
- Device Management and Bring-Your-Own-Device (BYOD) Restrictions: Devices should be inventoried and monitored and maintain specific security controls to be permitted to connect to the network. Network access control (NAC) and device management solutions can authorize and verify the security status of devices with sufficient antivirus and operating system updates among other options.
- Windows and Email Settings: Software can be configured to block or require additional authorization to permit the download or launch of executable files. Similarly, Windows Script Host can be disabled as a defense against JavaScript malware.
- Disable Autorun: Disable autorun for mounted media and prevent the use of removable media if not needed. This will block attackers who try to trick users into using malware-infected media.
- Configure Desktop Extensions: Windows should be changed from the default, so it always displays extensions. Employees can then be trained on .exe and other potentially malicious file types that should not be launched or downloaded.
- PowerShell and Hacking Software: Most users don’t know hacking tools, what PowerShell is, or how to use these tools appropriately. Use of these tools should be restricted or at least immediately generate alerts. Whitelisting, mobile device management (MDM), or other tools that restrict software only to officially approved software can also help prevent the launch of unauthorized software.
Secure Common Infection Vectors
Before ransomware launches, it must first enter the network. Organizations need to defend against the primary vectors of infection.
- Email Security and Spam Filters: Most malware infections start with phishing attacks with malicious links and attachments. An effective spam filter enhanced by cloud-based threat intelligence can prevent many attacks, and implementing effective DMARC, DKIM, and SPF email security tools can block even more. Email gateways are another effective first line of defense.
- Sandbox Testing: Some emails may be quarantined, and other emails may escape filtering, but users or email security tools may flag potentially malicious attachments. Security teams can examine these files utilizing a sandbox to examine the file and confirm if it may be safe for the user to open.
- Disable Macros: Microsoft now disables Office Macros by default, but some companies may still be using legacy files. Macros should only be enabled for users that absolutely need them and users should only enable macros on trusted files.
- Block Malicious Websites: Phishing emails may contain links to malicious sites, or malware may contact malicious sites to download additional malicious software. Known malicious websites can be blocked by domain-name filtering features on firewalls, web gateways or through DNS strategies.
- Browser Security: Users can be tempted by phishing attacks to visit malicious websites or by ads placed on legitimate websites. Browser security can automatically block pop-up ads and only allow connections with websites with valid security certificates. Even more security can be provided by using browser isolation that acts as a sandbox for web browsing.
- Secure Remote Connections: Attackers often exploit exposed vulnerabilities in Remote Desktop Protocol (RDP) and Virtual Private Network (VPN) connections. RDP should be disabled and VPN should be hardened and well maintained (fully patched, regularly upgraded, etc.). Cloud technologies even offer Virtual Desktop Interfaces (VDIs) and other methods to secure remote users.
- Firewall and Secure Gateway Security: Advanced security settings on firewalls and secure gateways can be used to filter malicious URLs, block malicious attachments, quarantine suspicious network traffic, and generate alerts of suspicious or anomalous traffic. The inspection features of these tools also help to add a layer of security for email and browser security.
Secure Humans
Many ransomware attacks begin with a user falling for email phishing that launches malware or leads to malicious websites. The number of “bad clicks” can be reduced through cybersecurity training for users. While some users may remain a potential source of infection, training can also help security recognize these users that may need additional layers of security to help protect them.
Attackers value IT administrator credentials because of their comprehensive access to IT systems. Admins should regularly use non-privileged credentials for everyday tasks such as email, web browsing, etc. Privileged credentials can be term-limited and highly restricted to limit their value and opportunities for compromise.
Patching And Maintenance
Attackers will quickly take advantage of exposed vulnerabilities in any way they can. Often, the announcement of a security patch or a zero-day vulnerability will be followed with malware attacks targeting that exposed weakness within a few days and sometimes within a few hours.
IT teams for organizations of all sizes must promptly patch software and hardware vulnerabilities and implement mitigation to protect devices or software that cannot be patched quickly. Updates for security software and infrastructure with the latest security updates (malware signatures, malicious urls, etc.) must also be prioritized to prevent attacks and organizations should maintain up-to-date asset systems and software lists to know what to update.
Check For Mistakes
The best plans often become unwittingly sabotaged by poor implementation or simple error. Organizations need to regularly check their systems with vulnerability scans and penetration tests to verify that all layers of the security stack operate as expected without any detected vulnerabilities or misconfigurations.
Ransomware Damage Limitation Best Practices
The best security tools can still be circumvented by human error, misconfigurations, and zero-day vulnerabilities. However, effective IT design and basic security principles can be put in place to limit the effectiveness and slow the spread of ransomware.
Data Encryption
One key tactic in many ransomware attacks uses data exfiltration to extort companies with the threat of releasing that data to the public or to competitors. The effectiveness of this threat can be blunted significantly by encrypting sensitive data or even all data in the organization. However, encryption keys must also be managed and protected to prevent their theft by the ransomware attackers.
Backups And Offline Backups
The damage a ransomware attack can cause for an organization will be limited by the maintenance of disaster recovery solutions such as frequent immutable backups. Most ransomware attackers will seek to destroy backups and restore points for systems, so at least one version of the backup should be offline or unreachable from the network.
Backup tools and processes should be tested regularly to practice restoration techniques. Organizations should also verify the capacity of the backup provider to operate at scale in the event of a widespread ransomware attack.
In addition to data, backups should periodically capture the full operating system, installed software, and settings in the event that a full system backup is required. Backups should be retained for up to six months to enable the restoration of pre-infection data and operating systems as well as enable forensic investigation of long-term attacks.
Segmentation And Microsegmentation
In line with least-privileged principles for users, devices can be isolated using segmentation and microsegmentation to create limited size networks in which a network can spread or an attacker can perform lateral movement. By implementing strict policies at the application level, segmentation gateways, firewalls, zero-trust architecture, and software-defined wide area network (SD-WAN) tools can prevent widespread ransomware attacks.
Prioritize Assets
Using risk assessments, organizations can identify key assets and data for the organization and assign additional protections or alerts on these key assets.
Utilize A CASB
Cloud access security brokers (CASBs) provide additional visibility, compliance, data security, and threat protection in securing cloud resources and data against attacks.
Ransomware Infection Alert Best Practices
Despite the best efforts of security teams to prevent malware from entering the network, a simple mistake can lead to a ransomware infection. To limit the ability of the ransomware attack to damage the organization, security teams need to receive alerts regarding malicious activities as well as have the capabilities to recognize those alerts and the capacity to act on them.
- Security Tool Alerts: Security tools (endpoint detection and response, intrusion detection / prevention systems, network detection and response, firewalls, etc.) should be configured to detect and send alerts to the security team for malicious, potentially malicious, and anomalous activities.
- Segmentation Monitoring: Many security teams only monitor between the network and the external environment. High value network segments should also be monitored and controlled with segment-specific firewalls and similar controls.
- Data Alerts: Security teams can deploy data loss protection (DLP) tools or user and entity behavior analytics (UEBA) solutions to generate alerts of malicious activities or anomalous large-scale copying or data transfers.
- Deception Technology: One way to set off a flare to warn of malicious activity is to use honeypots and other deception technology to lure attackers into setting off alarms.
- Active Monitoring: The best alerts from the best security tools can still lead to serious trouble if there is no one monitoring those alerts.
Effective security requires the use of security information and event management (SIEM) tools, security operations centers (SOC), managed detection and response (MDR), and attentive security professionals to quickly recognize the alert and be able to take action. These professionals will also need to fine-tune the tools to minimize false alarms that might otherwise waste time and lose critical alerts in the noise of false-positive warnings.
Ransomware Reaction Best Practices
Advanced tools may be configured to take automated action to quarantine infected devices or block malware from executing. However, other attacks may only generate alerts.
Once a ransomware alert has been recognized, the incident response teams will have very little time to react to prevent the ransomware attack from spreading or encrypting the data. We list a number of resources for recovering from a ransomware attack at the top of this article, but the short version is:
Incident Response
The security team should already have specialists assigned or vendors contracted to perform incident response. These teams should develop and practice a playbook for responding to a ransomware attack, so they can respond immediately to an actual event. The incident response team’s reaction can include:
- Incident response tools can help with investigation and recovery, but teams should already be practiced with their use in the local environment to enable the teams to act promptly, confidently, and effectively.
- Endpoint isolation can contain attacks to specific devices and prevent it from spreading throughout the network.
- Network isolation may be required if the attack has already spread to multiple devices within the network.
- Hard shut-down or the physical disconnection of devices can be warranted in large attacks that cannot be contained by other methods. This is the most disruptive response, so this action cannot be taken lightly.
Forensic Analysis
After any detection of ransomware, there needs to be an investigation into the entry point(s), time in the environment, affected system(s), data exfiltrated, and data corrupted. Only once the investigation is complete can the organization confirm the ransomware attack is contained.
What to Do When Attacked by Ransomware
Ideally, ransomware reaction best practices will allow the incident response practice to kick into gear and lead to a speedy resolution. For those organizations without incident response plans, the general steps should include:
First Phone Calls
- Cybersecurity Insurance Provider: Cybersecurity insurance policies often require organizations to use vendors required by the insurance company to be eligible for coverage. If the organization intends to seek coverage, the insurer should be the first call.
- Incident Response or Ransomware Recovery Experts: If the organization does not have in-house expertise, they should call in experts experienced with investigating, containing, and remediating ransomware attacks.
- Other Stakeholders: Incident response and disaster recovery policies should contain current lists of executives, members of the board of directors, law enforcement, and legal counsel for the organization that must be contacted in the event of an incident. These parties may need to authorize any unusual steps and expenses that may be required to resolve the situation.
Execute The Ransomware Reaction Best Practices
As noted above, the first steps will be to contain the attack followed by stopping the malware. Once the attack has been controlled, the incident response team will need to perform a forensic investigation of the systems to remove any malware, system back doors, or other traces of the attack to prevent recurrence.
Recover The Data
Once the systems are verified as sanitized, the organization can start the process of recovery.
- Version Restore: Some simple ransomware attacks leave system restore version intact and will allow the recovery team to roll back the system to a previous version. This is the best case scenario that will rarely be possible.
- Restore From Backup: Organizations with good system and data backups will likely want to pursue this route because it can be the fastest to implement. However, if the last known “good” state for the system was a considerable time in the past, the recovery team will need to compare two options:
- Roll back the operating system (OS) and data, and go through all of the patching and updates since that time and restore data separately.
- Reinstall the OS and software from scratch, and then, restore data.
- Decryption Attempts: Organizations without available backups will need to attempt to decrypt the data. Unfortunately, decryption does not have a good success rate, and critical data will often be lost.
Post-Event Analysis & Recommendations
After the successful recovery of systems and data, the organization should do a post-event review to:
- Evaluate the cause and controls to prevent or mitigate a repeat event.
- Review the incident response process and recommend potential adjustments or improvements.
- Determine if additional training should be developed and provided to users or cybersecurity staff.
- Develop and approve reports to executives and stakeholders outlining the damages incurred, costs to remediate, steps taken to prevent future attacks, and recommendations for further controls.
Bottom Line: Effective Preparation is the Best Ransomware Protection
Ransomware attackers continue to evolve and develop their skills. Some attacks may be inevitable and unavoidable — especially from determined and skilled attackers. However, the hardening of IT environments to make attacks difficult and tedious can cause active attackers to prioritize easier targets of opportunity.
Faced with the threat of negative publicity – and often unrecoverable data – non-technical executives and board members often ask their security teams or service providers to explain ransomware and how their organization might prevent ransomware attacks.
While security professionals can write entire books on ransomware, executives need concise, high-level information that provides the essential information in language free of acronyms, trivia, or technical details they may not understand.
IT executives need to explain that the best protection against ransomware attacks remains effective preparation. Organizations that limit access within their IT environment, implement effective security tools, monitor alerts for signs of attack, and respond quickly will dramatically reduce the damage from ransomware attacks.
If enough organizations can harden their environments and limit their damage, the ransomware business will certainly fade into the background. Ransomware has faded in the past and the current boom of ransomware is simply a resurgence of an old attack method that has gained traction in a target-rich environment.
Skilled attackers will always pivot to a new style of attack designed to extort or steal money, and IT teams will need to adjust their security tactics to address those new threats as they arise. Only strong fundamentals can prepare for the current attacks as well as attacks to come.
Read next: How One Company Survived a Ransomware Attack Without Paying the Ransom








