The growing remote workforce has challenged organizations to find cost-effective and secure remote and home-based internet connections for employees. Three of the most common remote access approaches are virtual desktop infrastructures (VDIs), virtual private networks (VPNs), and remote desktop protocol (RDP).
They each have their own security challenges and require their own security controls, but understanding the distinctions between VPNs, VDI, and RDP can help you choose the best way for your remote employees to connect to company resources. Note that remote access can also refer to software used to deliver IT support services, but here we’re concerned simply with connecting remote employees as securely as possible.
We’ll go into more detail below, but here’s a high-level overview of each approach and its best use case:
- VPN: Best for organizations that value direct control over local hardware and need to connect to local resources, or for individual users valuing privacy and security
- VDI: Best for standardized, scalable remote access
- RDP: No longer considered a secure or safe connection method
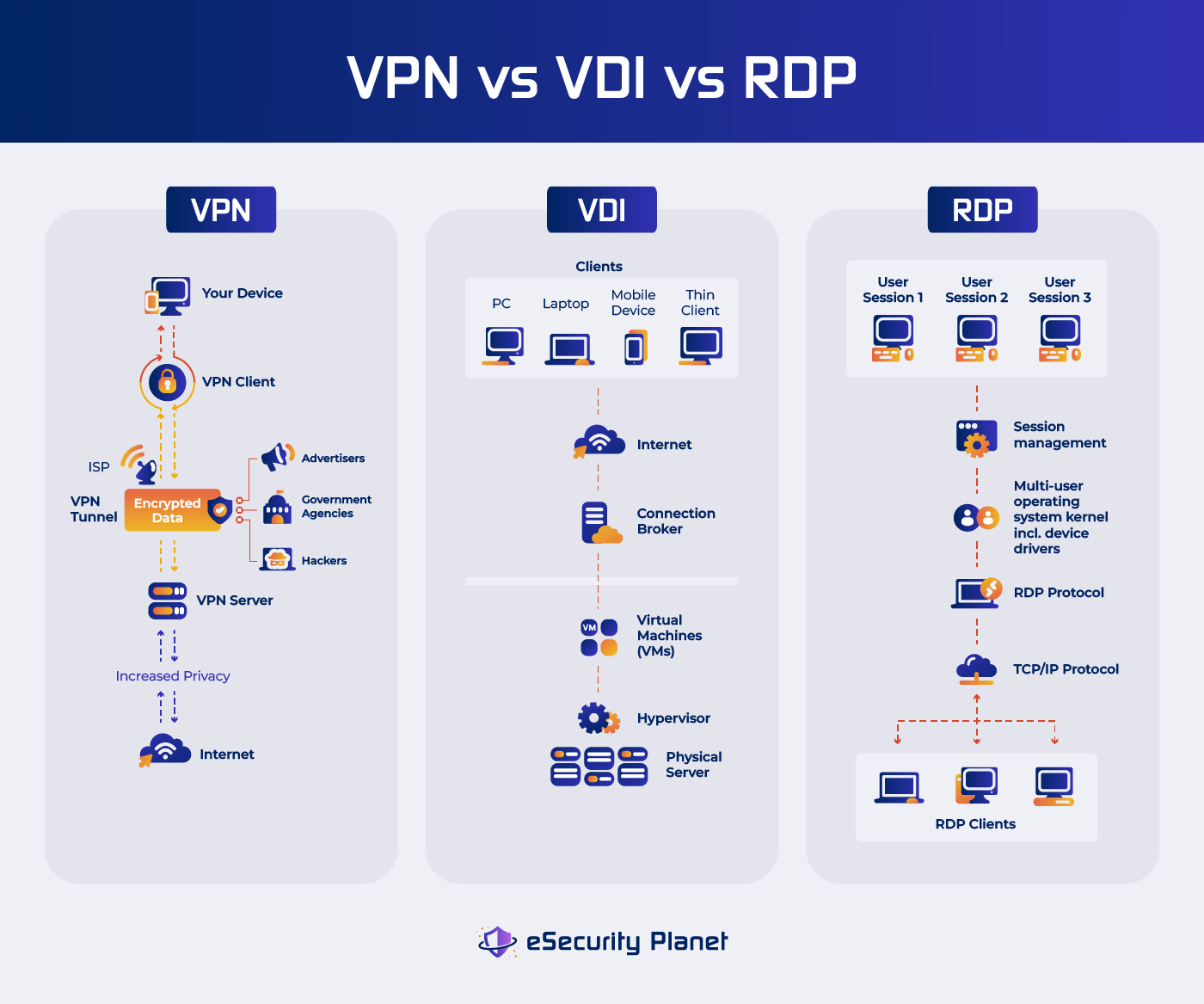
Virtual Private Network (VPN)
Virtual Private Networks (VPNs) provide an extra degree of protection for your apps and internet connections, whether you use a personal VPN or one hosted on a server within your organization. A VPN protects your internet connection and data from prying eyes, hackers, and other dangerous actions. It does so by establishing a secure tunnel between the user and the corporate network and encrypting data in transit. This encryption helps ensure that sensitive information stays private and secure while traveling across the internet.
VPNs are a good choice for organizations that place a high priority on encryption capabilities — provided they use additional security measures such as proper access control and monitoring.
Also read:
- Best Enterprise VPN Solutions
- What Is Secure Remote Access?
- 16 Remote Access Security Best Practices to Implement
How VPN Works
A VPN redirects your internet traffic through a distant server managed by the VPN provider, or perhaps through a server within your own organization. When you use a VPN to connect to the internet, your data is sent through an encrypted tunnel, making it difficult for third parties to intercept or decode your online activity or even your location.
- Your data is encrypted before it leaves your device when you begin a connection to a website or service. This encryption assures that even if your data is intercepted, it can’t be read without the decryption keys.
- The encrypted data is then sent to the VPN server. This server might be in a different city or even a different country than your current location.
- Once the data arrives at the VPN server, it is decrypted and transferred to its intended destination. The website or service you’re visiting sees the IP address of the VPN server rather than your own, preserving your privacy.
Pros of VPN
- When using a VPN, you may transfer files with confidence since you know that your data is secure throughout transmission.
- VPNs let you access the internet without being tracked. Your online activity is routed through a VPN server, which hides your IP address and makes it challenging for websites and online services to monitor your surfing patterns or location.
- VPN services protect your IP address, passwords, location, and other identifying information from hackers and organizations collecting data, protecting you from potential online risks and ensuring that your personal information is kept private and secure.
- VPN offers a strong defense against corporate monitoring and profiling activities if you’re concerned about their methods of data collection and wish to keep your information private.
- When connecting to public Wi-Fi networks, which are frequently targets of cyber attacks, VPNs provide an additional layer of security. Your critical data, including passwords and financial information, are protected from possible hackers thanks to the encryption offered by a VPN.
- VPN services are reasonably priced, with minimal monthly subscription fees available. This makes the security and privacy benefits of a VPN available to a broader group of users.
- VPNs are user-friendly. Even if you’re unfamiliar with the whole idea of internet privacy and security, VPN programs are often simple to use.
- VPNs are versatile since they can be used on a variety of devices, including computers, smartphones, tablets, and even routers. This adaptability helps you secure your online activity across several platforms and devices.
- VPNs enable you to access resources and services that may be restricted or prohibited in your region by concealing your IP address and enabling you to pick the location of the VPN server you connect to.
- VPNs can help you reduce the amount of targeted ads you see online. Your true IP address is concealed, making it more difficult for marketers to follow and target you based on your online activity.
Cons
- The encryption technique that VPNs use to protect your data might result in slower internet connections. This encryption adds a layer of processing, resulting in data transmission delays and, on occasion, failed connections.
- While most devices are typically compatible with popular VPNs, older or less prevalent operating systems may have difficulty setting VPNs. This problem could affect earlier versions of macOS, iOS, Linux, Android, and Windows.
- VPNs aim to improve online privacy, but in some circumstances may still reveal your identity. DNS leaks or sudden VPN disconnections, for example, might possibly disclose your real IP address, jeopardizing your privacy. Even with features like DNS leak prevention and kill switches, your data might be compromised.
- Although VPNs can be advantageous and scalable for some firms, they may not be suitable in all situations. Many VPNs aren’t designed to handle the massive and constant network traffic that enterprises rely on. This can lead to bottlenecks, when concurrent or parallel traffic becomes crowded at specific spots. Addressing this issue may need large investments, which may not be possible for every firm.
- As with any remote access, if a user endpoint is hacked, those remote connections become vulnerable too, so endpoint security, zero trust controls and behavioral monitoring are important for preventing and limiting breaches.
Who Should Use VPN?
VPNs are versatile tools that cater to a wide range of users, offering benefits for both individuals and organizations:
- Remote workers
- Privacy-conscious individuals
- Public Wi-Fi users
- Users who need access to geographically restricted content
- Businesses and enterprises providing remote and hybrid work setup
- Individuals living in regions with heavy censorship or surveillance to access the open internet
Also read: NSA, CISA Release Guidance for Choosing and Hardening VPNs
Virtual Desktop Infrastructure (VDI)
VDI enables enterprises to develop and manage virtualized desktop environments within a centralized server architecture or in the cloud. VDI allows users to remotely view their individual desktops from a variety of devices, including laptops, tablets, and thin clients, while the real computation and data storage takes place on a server. This method lets users receive desktop computing experiences in a flexible and secure manner without being bound to a single physical device or location. VDIs are ideal for organizations that value adaptability and standardized environments for their remote workforce.
Virtual desktop infrastructures offer greater security features. For example, hacking a virtual desktop doesn’t put you inside the firewall or give you network access, and there’s no hardware sitting around for hackers to ping. However, VDI implementations are typically managed by third parties because self-managed instances are expensive and difficult.
How VDI works
The VDI process involves several key components:
- A powerful server contains a number of virtual machines (VMs), each of which represents a single user’s desktop experience. These virtual machines are segregated from one another, protecting user privacy and data security.
- The hypervisor is a software layer that handles the server’s virtual machine creation, allocation, and operation. It guarantees that each VM has optimal resource consumption and performance.
- Each user is given a virtual desktop that is modeled like a standard physical desktop environment. The operating system, apps, settings, and data are all included.
- Users can access their virtual desktops via remote access protocols from client devices such as laptops or mobile devices. These protocols communicate between the client and the virtual desktop by sending screen changes, keyboard inputs, and mouse movements.
- Centrally controlled and managed virtual desktops allow IT managers to deploy new workstations, update software, and enforce security controls.
Pros of VDI
While careful preparation and early investment are required, the benefits of VDI make it a viable choice for businesses looking for safe and customizable remote computing options.
- IT departments may handle software upgrades, security patches, and user profiles more efficiently from a centralized place, minimizing administrative cost.
- Data is kept at the data center or in the cloud, lowering the risk of data loss due to device theft or local hardware failure. Data can also be more safely protected with strong security measures.
- Users may access their virtual desktops from a variety of devices, allowing for greater flexibility in remote working circumstances.
- VDI optimizes hardware resources by distributing server capacity over several virtual desktops, resulting in higher resource usage and cost savings.
- Companies may simply scale up or down by adding or removing virtual desktops as needed to meet changing workforce demands.
Cons
- VDI implementation requires careful planning, hardware investment, and knowledge of virtualization methods, or outsourcing the work to a VDI provider.
- While VDI can result in long-term cost reductions, initial expenses might be substantial.
- VDI is heavily dependent on a stable and fast network connection. Slow or unstable connections can affect user experience and performance.
- Server load and the resource needs of various apps and users might have an impact on performance.
Who Should Use VDI?
VDI is particularly beneficial for:
- Organizations with a need for standardized desktop environments, enhanced security, and centralized management and control.
- Companies with remote or distributed teams that require secure access to desktop resources from various locations and devices.
- Sectors such as healthcare, finance, and legal, where data security and regulatory compliance are critical.
- Temporary or contract staff who need access to controlled environments without compromising data integrity.
- Organizations looking for robust disaster recovery solutions to keep operations running amid unforeseen disasters.
Remote Desktop Protocol (RDP)
Remote Desktop Protocol (RDP) is a Microsoft-developed proprietary protocol that allows users to remotely access and operate a computer or server from a different location as if they were physically there at that place, resulting in a smooth and familiar user experience. RDP allows users to communicate with a remote system as if they were sitting in front of it, giving them access to the distant machine’s programs, files, and resources.
For businesses that want direct control over remote computer systems, RDP is a low-cost option, but it’s now generally regarded as insecure.
RDP Security Issues
In its default configurations, older versions of RDP do not use encryption to pass through credentials and session keys. This makes the protocol vulnerable to man-in-the-middle attacks where an attacker can intercept and see all information packets. Administrators can enable transport layer encryption to mitigate this issue, but this is just the start of the problems.
A main weakness is credentials. RDP sessions often store credentials in memory, where they can be stolen by an attacker who gains access. However, even without access, attackers often gain success using credential stuffing, which is when attackers use stolen credentials on other sites where users might have reused passwords. Administrators do not typically manage RDP and therefore users may pick their own credentials.
Additionally, many users don’t keep their RDP software updated. A year and a half after Microsoft released patches for the BlueKeep RDP bug, researchers detected hundreds of thousands of RDP devices unpatched and vulnerable. Attackers frequently target open firewall ports commonly used for RDP to take advantage of exposed vulnerabilities and gain access to both the endpoint and the network.
However, these security weaknesses can be countered. Admins can use multi-factor authentication (MFA) or single sign-on (SSO) to reduce issues from weak credentials or RDP desktop passwords, and can be managed to improve user authentication security.
To limit attacks on the firewall, IP address ranges can be limited to approved locations. However, this approach is labor intensive. For every employee on the road, each hotel, airport, and coffee shop require a new IP address to be whitelisted and then later removed when the employee moves on. It is just easier to run RDP through a secure tunnel instead.
Related: Addressing Remote Desktop Attacks and Security
How RDP works
RDP operates on a client-server model:
- Client: This is the user’s device that starts a connection to a distant system using an RDP client application. The client sends keyboard and mouse inputs, as well as screen changes, to the remote server.
- Server: The remote computer, referred to as the server, receives the incoming RDP connection. It processes the client’s inputs and refreshes the screen accordingly, providing the user with a unified experience.
- User Interaction: The user may interact with the remote system by doing activities, accessing apps, and working with files as if they were physically there at that place.
RDP Pros
- RDP allows users to remotely access and use powerful computers or servers, even from less capable client devices.
- IT administrators may oversee and manage distant systems from a single place, streamlining maintenance and upgrades.
- Users can utilize the computational capacity of remote systems without investing in high-end hardware.
- RDP offers a consistent and familiar computing environment, allowing users to remotely access their chosen apps and settings.
Cons
While RDP offers benefits like efficient resource use and centralized control, possible security threats and network dependencies must be properly examined and managed:
- Without strict controls and configuration settings, RDP might expose systems to security vulnerabilities. Unauthorized RDP session access can result in data breaches and other cyber dangers.
- RDP is dependent on a steady and high-speed network connection. Slow or inconsistent connections can cause latency and a subpar user experience.
- While RDP clients are available for a variety of operating systems, some devices may not be entirely compatible with certain protocol capabilities.
Who Should Use RDP?
RDP offers lower cost and convenience, but with greater security risks. For those who remain interested, there are possible use cases.
- RDP allows IT administrators to manage servers and troubleshoot technical issues from anywhere.
- Teams that need to provide remote assistance and troubleshoot problems for end-users or clients can benefit from RDP.
- Collaborative work on remote systems, such as teams required to work together on projects that require direct access to specific software or resources.
- Developers who need to access development environments or servers for testing and coding purposes. Again, tight security controls are cautioned.
- Organizations that rely on software applications that are resource-intensive or require specialized configurations.
Who Shouldn’t Use Any of These Solutions?
While VPNs, VDI, and RDP are useful remote access solutions, they may not be appropriate for many organizations with some specific considerations, such as significant compliance requirements, sophisticated cybersecurity threats, limited budgets, technological complexity, or particular access demands. If these technologies are incompatible with their goals or limitations, organizations must examine their particular circumstances and explore alternate options.
VPN
- Organizations in highly regulated industries, such as healthcare and finance, may be required to conform to stringent compliance rules governing data management and privacy. While VPNs offer encryption, certain restrictions necessitate stricter security measures.
- Government agencies and major organizations that are prime targets for advanced cyber attacks may require more complex security solutions such as zero-trust architectures or specialist cybersecurity tools.
- For organizations frequently dealing with a high number of remote users at the same time, VPNs might cause a bottleneck in network traffic. When an organization’s network resources are constrained, performance suffers.
VDI
- VDI implementation demands a substantial initial investment in hardware, software, infrastructure or services. This initial expense may be costly for smaller enterprises with limited funds.
- VDI setup and administration may be complicated, necessitating IT experience as well as committed resources. Organizations that lack the required technical capabilities may struggle with setup and maintenance.
- VDI may be excessive for businesses with occasional remote access demands, since it is better suited for circumstances where remote access is a continual necessity.
RDP
- Cybercriminals have targeted RDP to exploit vulnerabilities and launch attacks. When employing RDP, organizations with weak security measures might encounter higher risks.
- Without suitable security measures, exposing RDP to the public internet might result in brute-force attacks and illegal access attempts.
- RDP users may not have the same amount of control over the remote system as they would with physical access. This constraint may limit their ability to install specific applications or perform specific activities.
Choosing the Right Secure Remote Access for You
Consider factors such as the amount of security necessary, the nature of the remote duties, and the devices your users will be using. Consultation with IT specialists and consideration of any scalability issues might aid in making your selection. Ultimately, the best choice is determined by your organization’s specific circumstances, demands, and goals. Here are some recommendations and considerations in choosing the appropriate secure remote access for your organization.
- Assess the sensitivity of the data being accessed remotely, as well as the level of protection necessary.
- Compare expenses of deploying and maintaining VPN, VDI, or RDP solutions.
- Consider both the initial expenses (hardware, software, and licensing) and the continuous operational costs.
- Consider doing pilot tests or proofs of concept with a smaller user group to evaluate the performance and user experience of the chosen solution.
- Consider how effectively each solution connects with collaboration and communication tools if they are important.
- Consider if your consumers require resources to be accessible from several places and devices or primarily from a single site.
- Determine which resources (applications, files, databases) remote users require access to.
- Consider the user experience. Evaluate if the users require entire desktop environments or only specialized application access.
- Consider your organization’s projected expansion and how effectively the chosen solution can expand to meet rising remote access demands.
- Determine if you require outside support or if your IT team can manage the installation.
- Determine if your IT environment is capable of handling the needs of VPN, VDI, or RDP, taking into account issues like server capacity and network bandwidth.
- Determine the number of remote users and their organizational responsibilities.
- Examine the credibility and trustworthiness of suppliers providing VPN, VDI, or RDP solutions.
- Examine the risk factors associated with each solution. Consider issues like data disclosure, security flaws, and the possible impact of downtime.
- Examine your remote users’ locations. Due to network slowness or connection limitations, some solutions may perform better for users in specific locations.
- Examine your organization’s technical skills for deploying, managing, and supporting the chosen solution.
- Understand any industry-specific compliance rules that your company must follow.
Finally, consider a mix of these solutions to satisfy the needs of your organization’s various use cases. For instance, VPN for secure file and application access, VDI for standardized desktop environments, and RDP for technical assistance.
Bottom Line: Tailor Secure Remote Access Solutions To Your Needs
Finding the best remote access solution is a critical first step toward fulfilling your organization’s full potential. Whether you prioritize encrypted connections with a VPN, want flexible and standardized environments with Virtual Desktop Infrastructure (VDI), or opt for direct management with Remote Desktop Protocol (RDP), adapting your solution to your organization’s specific needs is critical. Regardless of which option you choose, strict security controls and best practices are essential.
Read next: Remote Work Security: Priorities & Projects
This updates a Nov. 2021 article by Chad Kime








