The Remote Desktop Protocol (RDP) has long been essential for IT service management and remote access. Still, in the wrong hands, RDP attacks and vulnerabilities related to remote desktop software are a severe threat.
Recent years presented a torrent of research showing how vulnerable RDP systems are for organizations not taking additional cybersecurity precautions. Because RDP server hosts can access and manage remote devices, including sensitive clients, the threat posed by RDP attacks can’t be overstated. As remote desktop solutions are prevalent among IT and managed service providers (MSP), downstream clients can be at risk, as Kaseya experienced in 2021.
This article looks at the remote desktop protocol, how RDP attacks work, best practices for defense, the prevalence of RDP attacks today, and how remote desktop software vendors are securing their clients.
Table of Contents
- What is the Remote Desktop Protocol (RDP)?
- What are RDP Attacks?
- How Do RDP Attacks Work?
- Defending Against RDP Attacks
- Examples of Notable RDP Attacks
- Remote Desktop Software and Cybersecurity
- Secure Remote Desktop Solutions
- The Importance of Remote Monitoring and Management
What is the Remote Desktop Protocol (RDP)?
Available on Windows servers since the turn of the century, the remote desktop protocol (RDP) is Microsoft’s proprietary protocol for allowing an administrator to access and manage remote devices. RDP is widely popular for IT technical support and MSPs as it provides a host to take over a customer’s machine running client software for issue resolution and troubleshooting.
Though RDP is a Microsoft protocol, many commercial remote desktop software solutions offer added security capabilities for enterprise to SMB organizations.
What are RDP Attacks?
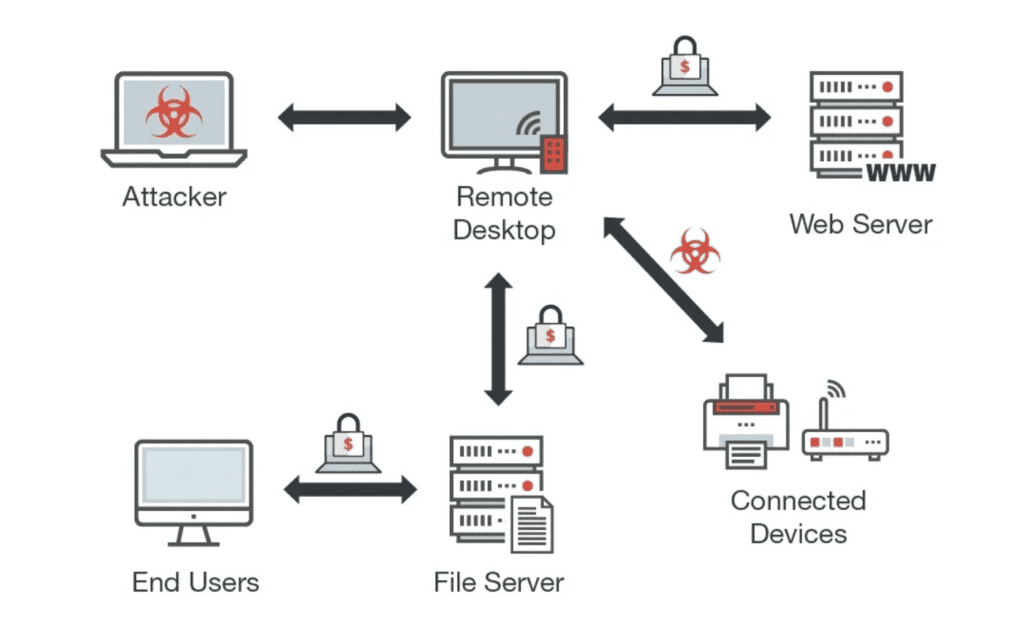
RDP attacks are attempts by threat actors to access a remote desktop host or client’s administrative privileges for reconnaissance, command and control, and lateral movement. With administrative control over a remote desktop system, perpetrators can do anything or access whatever data is available to the administrator or specific end-user. RDP attacks are often difficult to detect as no user input is necessary for the threat actor to get to work.
Read more: Best Network Monitoring Tools
How Do RDP Attacks Work?
Intrusion: Meddler-in-the-Middle and Brute Force Attacks
RDP intrusions are typically the result of two attacker methods: brute force authentication attempts or a meddler-in-the-middle (MITM) attack. Remote desktop software’s sensitive influence over other devices means identity and access management (IAM), password security, and multi-factor authentication are critical for risk management.
Reconnaissance
After obtaining the proper authentication credentials and gaining initial access to client devices, attackers have an incentive to navigate victim networks with caution. This reconnaissance period is a staple of the most sophisticated attacks as advanced persistent threats can evaluate their permissioned access, scan network activity, and attempt to escalate access.
Extended Stays and Attack Execution
Like in the case of SolarWinds in 2020, masked threat actors aren’t afraid to linger for months during reconnaissance. These stays can mean extended exposure to sensitive client data or proprietary information or enough time to parse through a managed service provider’s client network.
With lateral movement across a victim’s IT infrastructure, threat actors can escalate privileges, spread malware, extract data, and disrupt IT services as with ransomware attacks. As long as actors go undetected, the timing of attacks is on the perpetrator’s terms.
Also read: Best Internet Security Suites & Software
Defending Against RDP Attacks: Best Practices
- Multi-factor authentication and complex access credential requirements
- Establish account lockout policies for brute-force attempts
- Role-based access control (RBAC) for RDP consoles
- Firewall-based restrictions of RDP access
- Only allow connections with Network Level Authentication (NLA)
- Patch management for removing known vulnerabilities
- Virtual Private Network (VPN) for shielding client device traffic
- Close TCP Port 3389 for devices not using RDP
- Microsegmentation and zero trust network access models
Examples of Notable RDP Attacks
Calling into Robinhood
In November 2021, an unauthorized third party called a Robinhood customer support employee and, through social engineering, gained access to the company’s customer support systems. The online financial brokerage contained the intrusion, at which point the threat actor demanded an extortion payment. While no user financial information leaked, upwards of 5 million users’ email addresses and 2 million names were obtained.
SamSam Ransomware: Malware Specializing in RDP
Between 2016 and 2018, the malware strain SamSam made brute force RDP attacks an integral part of its attacks on several public organizations. By exploiting weak server vulnerabilities, the Iran-based hackers were able to gain access, move laterally, encrypt IT systems, and demand ransom payment.
| Attacks in 2018 | Victim Organization |
| January | City of Farmington, New Mexico |
| February | Colorado Department of Transportation (CDOT) |
| March | City of Atlanta, Georgia |
| July | LabCorp, U.S. clinical labs company |
| September | U.S. Port of San Diego |
Colorado Taken for a Ride
Two years after the attack on the Colorado transportation agency, the Colorado Sun revisited how SamSam infiltrated CDOT, the immediate aftermath, and the steps taken since to harden security. On a Sunday in February 2018, the Colorado CISO’s office set up a temporary server to test a new cloud-based business process. A few days later, IT systems started malfunctioning with ransom messages following.
The system administrator did not configure standard security controls when installing the server in question. Meanwhile, the suspect server was connected to the CDOT domain with an administrator account and the internet. As CISO Debbi Blyth put it, “The server was discovered almost immediately by the attackers.” After 40,000 attempts, SamSam had access to explore CDOT’s core network.
Read more: Compare the Top Threat Intelligence Platforms
Remote Desktop Software and Cybersecurity
As remote desktop capabilities have grown beyond Microsoft’s protocol, a range of software vendors compete to meet the needs of the digital workplace generation. Remote desktop software enables clients to scale remote IT operations, integrate essential applications, and secure communications for clients and personnel.
Below are some of the foundational cybersecurity features and solutions offered by leading providers.
Remote Desktop Software Features
- Encrypted communication using TLS, RSA public-private key exchange, and AES 256
- Identity and access management and network access control, including SSO and MFA
- Session, video, and log management for routine and targeted audits
- Support for specific regulatory compliance and reporting requirements
- Reliable update cycle removing bugs and known vulnerabilities
Also read: Top Database Security Solutions
Secure Remote Desktop Solutions
- BeyondTrust
- Check Point
- ConnectWise
- N-able
- Splashtop

BeyondTrust
Cybersecurity company BeyondTrust specializes in privileged access management (PAM), cloud security, and secure remote access. For remote desktop software, BeyondTrust offers Remote Support for essential help desk capabilities and Privileged Remote Access to control, manage, and audit access to critical IT systems.
In addition to granular role-based access control, BeyondTrust PRA creates audit trails and session forensics for compliance reporting. Additional security features include privileged password vaulting, cloud, and virtual infrastructure security, and integrations with existing security information and event managers (SIEM).

Check Point
Check Point is a veteran enterprise security vendor that integrates remote access capabilities into every next-generation firewall (NGFW). For the generation of remote work and operations, Check Point Remote Access VPN offers central management and policy administration for controlling access to corporate networks.
The Remote Access VPN enables more robust security with the encryption of transmitted data, system compliance scanning, and multi-factor authentication. The SSL VPN Portal for web-based access and the IPsec VPN for corporate network access support Windows, macOS, iOS, and Android devices to ensure access and security across diverse IT environments.
Read more: Best Intrusion Detection and Prevention Systems | Guide to IDPS

ConnectWise
ConnectWise offers a portfolio of MSP solutions for remote monitoring, business management, integrated services, cybersecurity, and more. Under the company’s unified monitoring and management stack, ConnectWise Control is a secure remote access solution for MSPs, help desks, remote workers, and IT teams.
ConnectWise’s solution comes with a bundle of built-in security features and tools to give clients the necessary control over sensitive data. Internally, this means role-based access control, logging of videos and session activity, the option to self-host, server-level auditing, and AES-256 encryption for all transmitted data. Additional security features include IP login restrictions, session timeouts, 2FA, and account lockouts for brute force attacks.

N-able
N-able – formerly SolarWinds MSP between 2013 and 2021 – has over two decades of experience in integrated monitoring and management tools for enterprise organizations. N-able’s remote monitoring and management (RMM), ticketing, and remote access tools are familiar solutions to industry veterans, but it also extended its security capabilities over the last few years.
Partnering with SentinelOne, N-able launched its endpoint detection and response (EDR) and password management solutions in 2019. Other cybersecurity tools offered include DNS filtering, disk encryption, backups, and email security for Microsoft-oriented infrastructure. The N-central platform is the most comprehensive solution, bundling these capabilities in a single console managing hundreds of thousands of devices.

Splashtop
Splashtop is a dedicated remote access and support software company with on-premises and cloud-based solutions for individuals, small businesses, and enterprise organizations.
Serving 30 million end-users and 200,000 businesses, Splashtop offers a swath of security features to meet the motley needs of private and public organizations managing sensitive data. Fit for clients with rigid regulatory requirements, Splashtop is SOC 2 and GDPR compliant and supports compliance reporting frameworks for HIPAA, PCI, FERPA, and ISO 27001.
Essential security features include TLS 1.2 and AES 256-bit encryption, 2FA, session and activity logs, and authentication for devices and proxy servers. Enterprise Splashtop goes further for the most administrative control, offering SSO integration, scheduled remote access, group-based access control, and automatic user provisioning.
Also read: Top XDR Security Solutions | Extended Detection and Response
The Importance of Remote Monitoring and Management
While IT infrastructure continues to expand and remote operations for workers and critical systems become more acceptable, remote monitoring and management capabilities are essential to consider. Several top vendors of RMM solutions naturally include remote desktop software, integrations to leading third-party security systems, and added features to safeguard enterprise data.
RDP attacks remain a dangerous threat, so it’s paramount for organizations small and large using remote desktop systems to follow the above best practices and bolster security where necessary.








