For a security technology that’s only a few years old, microsegmentation is catching on quickly.
According to a new report from edge security vendor Byos, 88 percent of cybersecurity leaders believe microsegmentation is essential to achieving zero trust security, and 83 percent are currently leveraging microsegmentation in some form.
Despite such strong uptake, the market still has plenty of room to grow, the report found: only 17 percent have fully invested in microsegmentation to the point that they believe they’ve successfully achieved zero trust.
Those findings appear in The State of Microsegmentation in Network Security, a Byos report that details the results of a Q3 2021 survey of 100 cybersecurity leaders. In an interview with eSecurity Planet, Byos founder and CEO Matias Katz discussed the findings and their implications for network security in general.
Microsegmentation is needed, Katz said, because traditional security measures simply aren’t sufficient to meet many of today’s challenges.
“The whole idea of microsegmentation is to give customers more control – to get faster, more efficient access to controlled assets without having to choose between exposing them too much or not having access to them at all,” he said.
Also read: How to Implement Microsegmentation
Critical Infrastructure, IIoT a Good Fit
The idea of walling off the most critical assets in a network is a particularly good fit for critical infrastructure and industrial IoT, in which a wide range of legacy devices simply aren’t able to run traditional EDR software.
“You have energy, oil and gas, healthcare, defense, that have broader perimeters where you have 20, 30, 50 controllers that are controlling either human life or energy, and they have no protection,” Katz said. “The companies are reliant on the perimeter.”
In cases like that, an attacker just has to breach the perimeter and they’re one hop away from total control. “But you can create microsegments that isolate those controllers from the rest of the planet, so they’re not visible even if you breach the big perimeter,” Katz said. “And you also get different chokehold points where you can control the type of traffic that’s allowed in or out, in a microsegment as small as even one endpoint if you want to.”
Companies are increasingly aware of the importance of that kind of functionality. Fully 92 percent of survey respondents believe microsegmentation is more practical and efficient than alternatives, 93 percent say it’s integral for IoT security, 88 percent believe it helps ensure effective security policy management, and 89 percent view it as a way to streamline challenges associated with regulatory compliance.
Also read: Top Microsegmentation Solutions
Microsegmentation Benefits Misunderstood
Still, Katz said he was surprised by the survey results regarding top microsegmentation features by demand. Table stakes, according to respondents, include real-time threat management (76 percent), secure remote access (67 percent), a ransomware kill switch (62 percent), and zero-touch deployment (57 percent). Legacy technology protection came last, cited by just 43 percent of respondents.
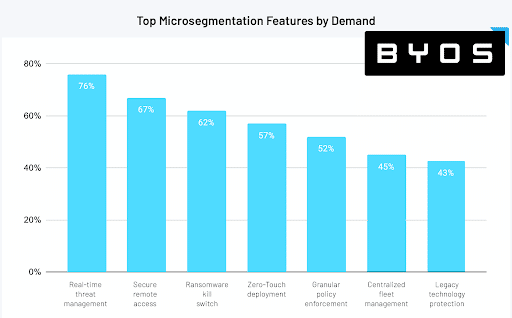
Katz disagrees with those priorities, which he ascribes to too many respondents simply parroting popular security vendors’ marketing strategies. “If you look at the last five big breaches, they had nothing to do with secure remote access, they had nothing to do with a zero-touch deployment,” he said. “They had more to do with the fact that they had legacy devices that handled critical infrastructure.”
And while real-time threat management is of course a key consideration for network security, Katz said, that’s also achievable from countless other security vendors and tools. “That’s great – we still need that – but there are other things like legacy protection that are being forgotten,” he said.
Telcos Falling Behind
The survey also found that while 95 percent of respondents in manufacturing, 92 percent in information and data services, 92 percent in finance and insurance, and 80 percent in healthcare and social assistance have already adopted microsegmentation, less than 30 percent in telecommunications have done so.
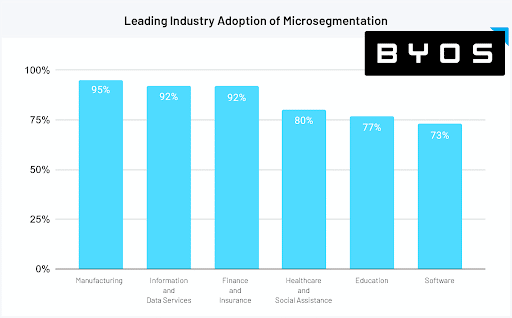
Katz suggested that’s attributable to that industry’s focus on communication, which inevitably makes those companies a little slower to implement barriers. “If you look at telcos, it’s all about the bigger picture,” he said. “It’s all about the broad network and communication, and the concept of creating microsegments goes against the current of what they’re trying to build. So I assume that it’s perceived as an operational or business risk to them.”
That’s a very different focus from, say, healthcare and social assistance. “If you’re a hospital, then you’re not in the business of communication – you’re in the business of protecting patients, and communication is just one of the checklists,” he said. “In telcos, it’s the number one: how do we keep this open and working? Adding roadblocks to that might be perceived as a challenge, and also expensive.”
A Necessary Cost
Expense is a common concern. Across all verticals, 29 percent of companies that haven’t yet implemented microsegmentation listed cost as the key barrier to adoption. Other barriers cited included lack of personnel (35 percent), network complexity (35 percent), and lack of time (29 percent).
Still, Katz said microsegmentation should really be seen as something like a seatbelt – you use it not because you want to, but because you know it keeps you safe. “It’s a little bit about biting the bullet and accepting that if you want to have a distributed workforce, if you want to have work-from-home, if you want to adapt to this post-Covid era where everyone works from wherever, there’s a couple of extra steps that you need to take,” he said.
Katz acknowledged that for most companies, doing so represents an added expense. “My recommendation would be that they accept that there’s going to be new money needed to be added to the budget to cover this, because of the newly added exposure caused by a distributed workforce and legacy equipment,” he said.
That new exposure is based both on a new focus on critical infrastructure as a target, and on a massive surge in remote working, which exposes company-issued computers to new threats. “If one of your employees has a barbecue and they invite 25 guests, now you as a CISO have 25 strangers that have direct access to a company-issue computer, which has to be allowed access to the corporate office because that employee works from home,” Katz said. “Those are new risks, and there needs to be new budgets for that.”
Further reading: Best Zero Trust Security Solutions








