The explosion in remote work that followed the COVID-19 pandemic has shifted corporate models from a main-branch focus to distributed corporate networks and vastly spread out remote employees. That in turn has shifted focus away from distributed networks and technologies like SD-WAN to the edge of the network – and to technologies like zero trust security and microsegmentation.
The next evolution of cybersecurity
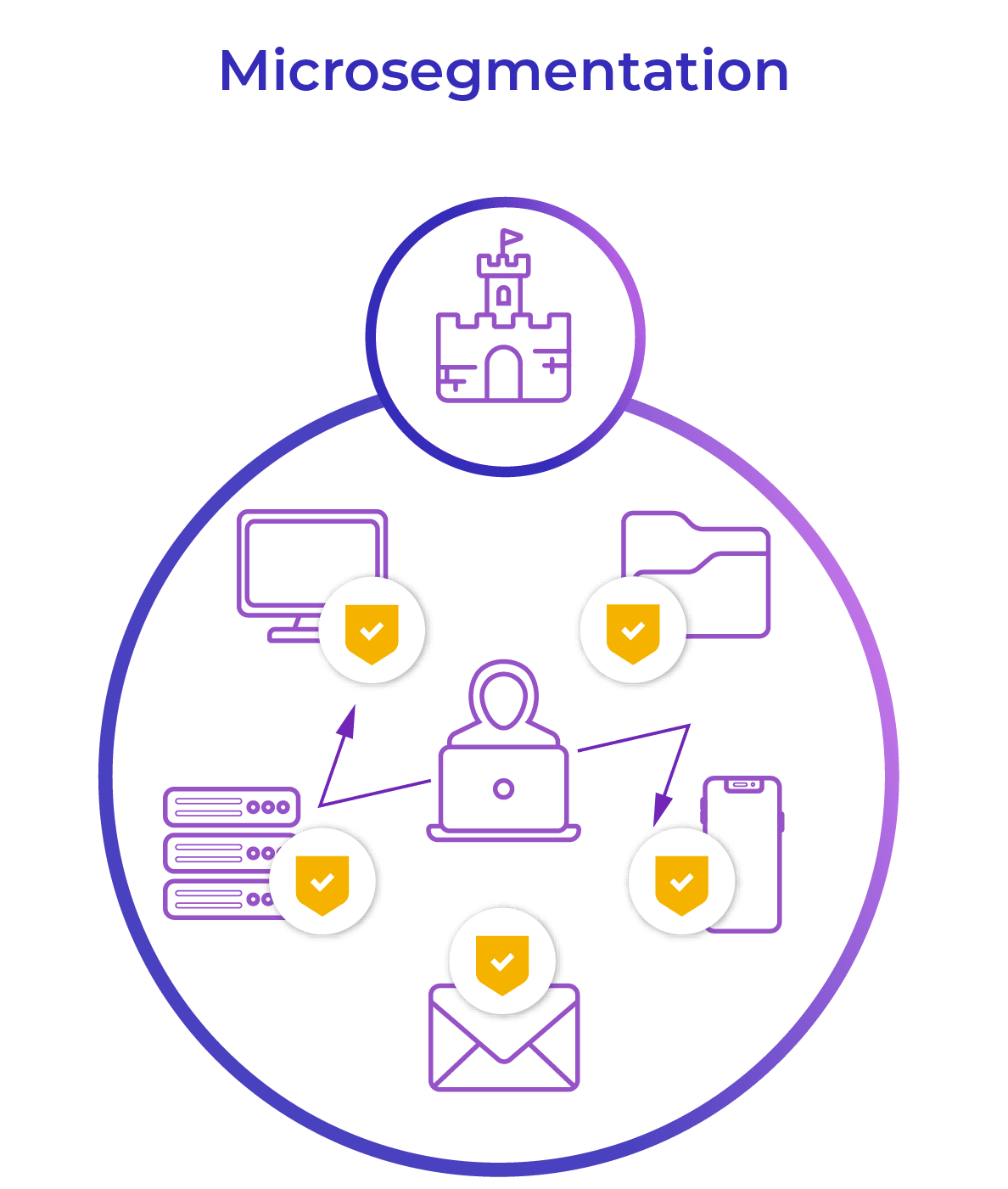
Microsegmentation uses virtualization technology to create increasingly granular secure zones in networks. By applying tightly-focused security policies, microsegmentation moves security away from simply identifying IP addresses and grants users access to only the applications and data they need based on their identity and role. Security then becomes about the individual user, limiting dangerous lateral movement within a network. Those policies can be further refined by location and device – an adaptive approach that takes into consideration current security risk. It’s a core technology for zero trust, the idea that no one should be trusted or given more access than they require.
See our picks for Top Microsegmentation Products
The benefits of microsegmentation
Microsegmentation offers organizations a number of benefits:
- Reduced attack surface: Microsegmentation limits attackers’ ability to move laterally through a network, ultimately reducing the potential attack surface.
- Threat detection and response: Even with optimized security practices in place, breaches are inevitable. But microsegmentation can drastically improve threat detection and response times. When policy violations are detected, microsegmentation tools can generate real-time alerts and even block unsanctioned activity.
- Regulatory Compliance: Microsegmentation can strengthen organizations’ regulatory compliance posture by creating segments that specifically store regulated data, typically the personally identifiable information (PII) of customers covered under laws such as General Data Protection Regulation (GDPR) and The California Consumer Privacy Act (CCPA). Compliance-focused policies can then be created for these segments. This also greatly simplifies the auditing process.
The Problem with traditional security techniques
More traditional security tools, such as firewalls, VPNs and network access control (NAC), have their limits because they focus primarily on securing the network perimeter. Security teams historically assumed the biggest threats were attacking from outside the network. But that approach overlooked insider threats – and the damage that hackers could do when they eventually got inside the network.
Complicating the network security picture is the rise in activity at the edge of the network, from consumers, remote workers and Internet of Things (IoT) devices. Edge traffic has prompted organizations to move data processing away from data centers to the edge of the network. That improves data center security and responsiveness – but shifts those problems to the network’s edge, necessitating new approaches to security. In response, edge security has become a new buzzword, and at its core is the concept of zero trust.
Authenticating users and devices with zero trust security
The zero trust framework relies on the philosophy of “trust nothing and verify everything.” This means that organizations must authenticate and authorize every single user and device connecting internally or externally to a network before allowing access to any applications or stored data. This method of “least privilege” access recognizes that too much trust is a vulnerability.
If a malicious actor gains access to a network, perimeter-focused security tools can’t prevent them from moving laterally through a network, giving them access to applications and data. That lateral movement is particularly dangerous because such advanced persistent threats are behind the most disastrous data breaches. Zero trust secures access across all applications and environments within a network.
So how can security teams authenticate the massive numbers of users and devices traveling throughout a network? One key is to create software-defined segments and define security policies for them at a granular level using microsegmentation.
Isolating networks and workloads with microsegmentation
Historically, organizations used network segmentation for security, which is a technique for creating sub-networks within a hardware-based environment. These network segments are built using traditional, parameter-focused tools, such as VPNs or firewalls, to provide north-south security – the flow of data entering or exiting a network.
Microsegmentation, on the other hand, offers protection for east-west, or lateral traffic – the flow of data inside a network. This includes server-to-server, application-to-server and web-to-server connections within the network. By creating security microsegments for individual workloads with granular policy controls, microsegmentation provides complete control over the traffic within and between software-defined segments.
Network segmentation vs microsegmentation
A common analogy for network segmentation versus microsegmentation is that network segmentation acts as the walls and moats surrounding your network castle. Microsegmentation acts as the guards protecting every single door and pathway inside the castle walls. Both are needed, but microsegmentation is the missing piece that can protect your most valuable data.
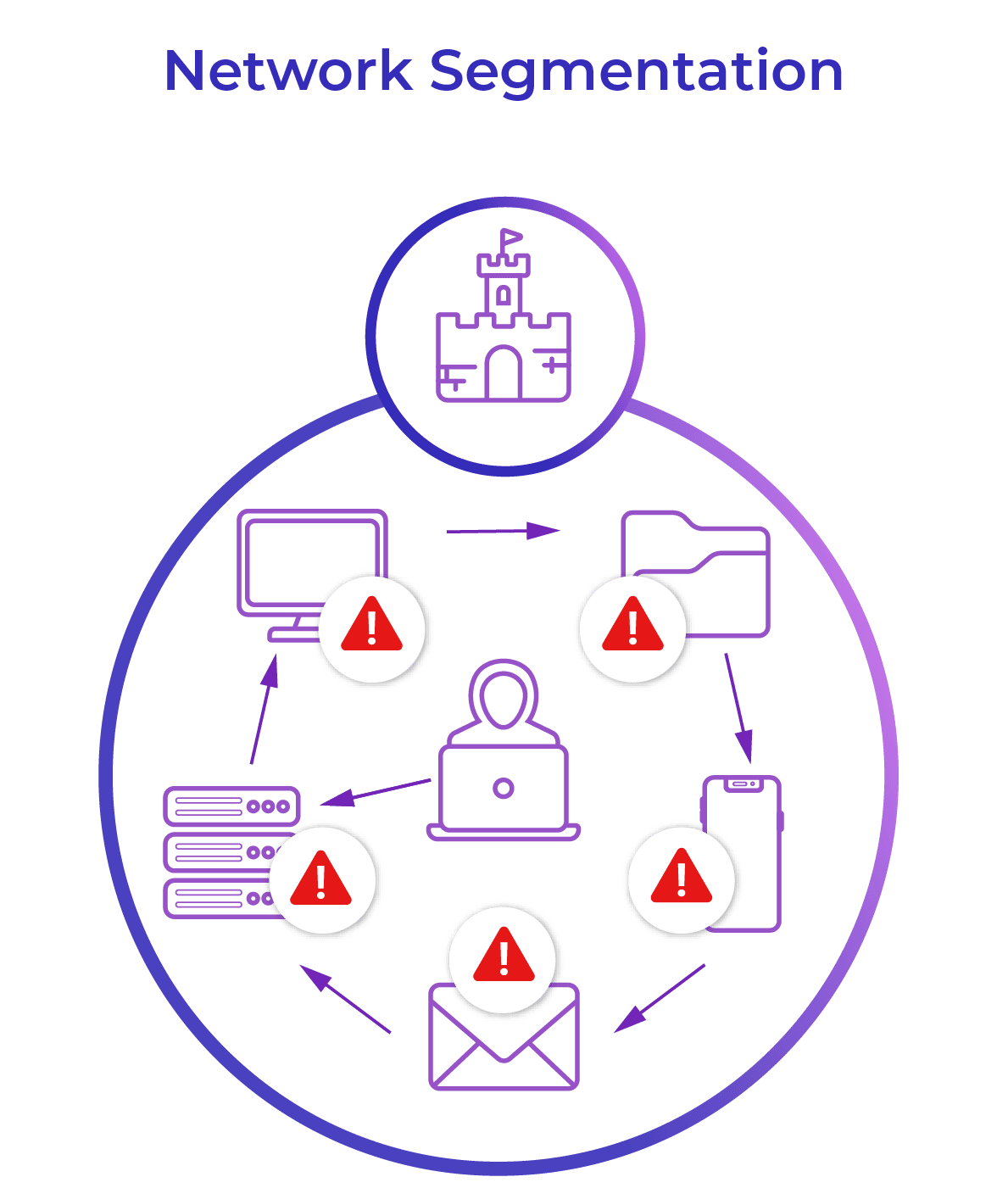
Problems with network segmentation
The theory behind network segmentation stands in stark contrast with zero trust, as it is only concerned with authorizing initial access to a network. This means that once a connection gains access, it is trusted to travel freely throughout the network, or at least that segment.
Another issue with network segmentation is its reliance on coarse policies for network segments that offer limited control. Software-defined segments in modern hybrid and cloud networks would require thousands of coarse policies for each segment to achieve some lateral traffic protection. This is far more than can be reasonably managed as new resources and users are continually added to a network.
The lack of comprehensive, detailed policies to protect lateral traffic is a particularly large issue in the case of advanced persistent threats (APTs). In these cases, attackers use stolen credentials to gain access to a network. Without a zero-trust framework in place, attackers can then navigate through a network undetected for long periods of time, mapping out an organization’s system and creating highly-customized malware for harvesting sensitive data. Zero trust and microsegmentation are critical new steps for preventing APTs from traveling openly throughout a network.
Reducing the attack surface with zero trust and microsegmentation
By isolating environments and segmenting workloads, a zero trust framework using microsegmentation greatly reduces the overall attack surface of a network by limiting movement from one potentially compromised workload to another. Once microsegmented, fine-grained security policies can be applied to workloads, all the way down to single machines, users or applications. These policies can be defined according to real-world constructs, such as user groups, access groups and network groups, and can be applied across multiple applications or devices.
How to assign policies
On the device level, policies can be used to assign certain restrictions to devices based on their functionality, so that only devices that require access to critical applications and resources can be granted authorization. These devices can also be isolated from each other so they cannot communicate unless authorized to do so. Devices can also be restricted based on location – say a coffee shop vs. a corporate network – and the security of the device itself, which may not be current on all security updates and patches.
Policies can also be based on source identities, another advantage microsegmentation has over previous methods of segmentation. Network segmentation can only tell you what information is being communicated between segments, whereas microsegmentation can pinpoint the identity of the resource requesting to communicate, whether it be a server, application, host or user. This provides far more granular segmentation, only allowing communication between resources whose identities have been granted proper permissions to do so.
With a comprehensive microsegmentation solution in place, any connection that cannot be verified by policy parameters is blocked from gaining access. Not only does microsegmentation protect against lateral movement, but it also gives security teams high-visibility and context for all network traffic. This allows teams to quickly identify malicious behavior and breaches, improving incident response and remediation.
Choosing zero trust and microsegmentation tools
While the zero trust framework is not a completely new concept, it has only recently gained traction as an enterprise security tool. Therefore, not all zero trust product offerings focus on microsegmentation. When shopping around for a solution, make sure to confirm that it offers microsegmentation so you get the most out of your zero trust framework. Here are a few of the more popular microsegmentation vendors to start your search:
- Amazon Web Services (AWS)
- Microsoft
- VMware
- Cisco
- Fortinet
- Palo Alto Networks
If you’re worried about implementing zero trust in your network, fortunately, this does not require a complete reinvention of the infrastructure. The most effective solutions should layer on top of your environment without the need to replace existing security investments. If you would like to gain a better understanding of what options are available to you, check out our list of the Top Zero Trust Security Solutions.








