A virtual private network (VPN) is a must for any internet user connecting to business systems. It provides a secure tunnel protecting user identity, encrypts data in transit, and extends the identity and security of the home network to remote users. Use this guide to learn how to get a VPN provider, set it up, and connect your devices for a more secure and safe connection.
Table of Contents
Determining the VPN You Need
Whether it’s for protecting corporate spreadsheets, bypassing geographic blocks, or anonymizing your use of online services, choosing and installing the right VPN to provide robust network security to your application and device is your first step. Some things to consider:
Application
Business users might prioritize premium security features, like 256-bit keys for their Advanced Encryption Standard (AES) protection, kill switches to protect devices in case of a VPN failure, or multi-hop networks. Road warriors will value the number and location of VPN servers, as will surfers trying to access geo-blocked content. Gamers and streamers will put a premium on speed. Weigh the importance of features by how you’ll use the connected devices.
Use
Like most software, VPN clients are system-specific — Apple versus Windows, iOS versus Android. But under the hood, they also support different protocols for different types of devices.
- Open VPN: An open-source security protocol that is widely considered the industry standard for VPNs.
- Internet Key Exchange (IKE): It is the protocol for Internet Protocol Security (IPSec). It has native support for Extensible Authentication Protocol (EAP), which allows more seamless handoffs between mobile networks.
- WireGuard: Valued for its speed, it uses User Datagram Protocol (UDP) to tunnel over Transmission Control Protocol (TCP). This avoids issues that can occur when stacking TCP connections.
- Datagram Transport Layer Security (DTLS): Used in products from Cisco Systems Inc., it also works around the TCP-over-TCP issues sometimes experienced with Transport Layer Security (TLS) protocols like Open VPN.
- Open SSH (Secure Shell): Provides a limited number of secure channels in a client-server architecture. It is integrated into Windows, Mac, and most Linux operating systems.
There are several other protocols. Some are obsolete or feature too many vulnerabilities to be widely used.
Ease of Installation
If you don’t have your own IT department, this becomes particularly important. The quality of the VPN provider’s support is also a consideration if you’re operating on your own. (It might also be tempting to opt for a free VPN service if you’re in this position. We’ll discuss why you shouldn’t in our FAQ.) Though details may vary from provider to provider, installation processes are, for the most part, similar.
How to Get a VPN on PCs
Create a VPN Profile
For an account connected to your business, it’s best to let IT staff set up your VPN profile. If you’re doing it yourself, visit the Microsoft Store to download the app for the VPN service you’ve chosen to use. The VPN provider’s website will provide the connection settings.
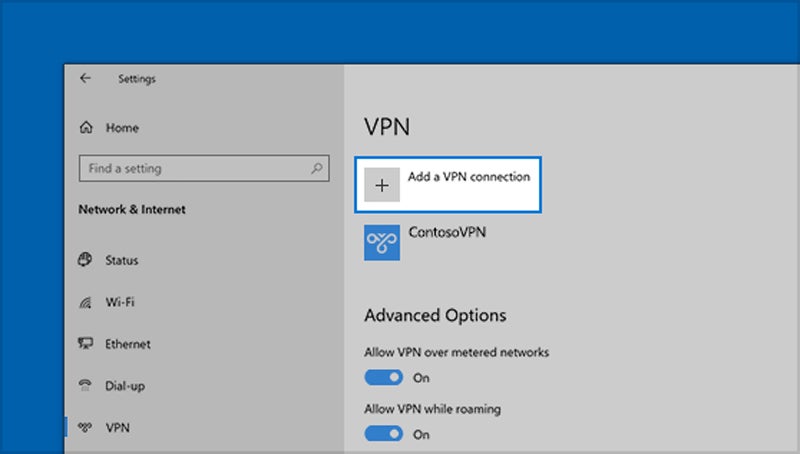
Go to the Windows Start Menu
Select Settings>Network and Internet>VPN>Add a VPN Connection.
- For the VPN provider, select Windows (built-in).
- Enter an easy-to-remember Connection Name.
- Enter the address of the VPN server under Server Name or Address.
- From the drop-down menu, select your VPN Type (you’ll have to know what protocol your service is using).
- Select your Type of Sign-in Info from the drop-down menu. Unless you have a smart card or certificate from work, choose User Name and Password.
- Enter your username and password.
- Select Save.
Connect to VPN
Click on the Network icon in the taskbar. A connect button should display; click on it. Alternatively, you can connect through the settings menu (Settings>Network and Internet>VPN). A pop-up box will request your sign-in information. While you’re online, you can check to see if the VPN is active by clicking the Network icon in the taskbar.
How to Get a VPN on Macs
Create your VPN Settings
For connections to your company VPN, contact your network administrator. If you’re setting up yourself, contact your service provider. In either case, you want the settings to be used. If you’re lucky, they will come in a click-to-open VPN Settings file. If not, you’ll have to enter settings manually.
Select the Apple Menu
- Select System Settings. Click Network in the sidebar.
- In the Action pop-up menu, select Add VPN Configuration and select the type of connection from the drop-down menu.
- Enter an easy-to-remember name in the Display Name field.
- Click the Configuration menu. Choose the type of configuration you want. If you don’t need multiple configurations on your computer, select Default.
- Enter the required settings. Depending on the service provider, this will include server address, account name and password, verification settings, etc.
- Select Create.
Connect to the VPN
Click the VPN Status icon in the menu bar. If no icon appears:
- Go to System Settings>Control Center in the Apple menu.
- Go to the Menu Bar Only pop-up menu and click on VPN.
- Select Show or Hide.
The VPN Status icon also offers options to show or hide connection status and connection time, and can switch between VPNs if you have multiple configurations.
How to Get a VPN on iPhones or iPads
Choose an App
Begin by choosing the iPhone-compatible VPN app that best suits your purposes. The app (or provider website) should allow you to create an account, log in, choose your server, and connect simply. If you must configure your iPhone VPN manually:
Go to Settings
- On your iPhone, click Settings>General>VPN.
- Click on Type and select your desired protocol. Since you’re using a mobile device, you’ll want to choose IKEv2, which makes network hops seamless.
- Enter your server name or address, account name and password, and remote ID provided by your VPN host. (If you have chosen a protocol option other than IKEv2, you will receive a pre-shared key.)
Connect to the VPN
Click Done to connect.
How to Get a VPN on Android
Good news for owners of Google’s Pixel 7 or later phones: these phones have built-in access to free Google VPN service wherever it’s available. For phones running Android 9.0 or later:
Download & Install the Required App
This could come from the Google Play store, or be a custom app developed in-house and distributed by your administrator.
- Go to the Settings app. Select Network & Internet>VPN.
- Tap Add. Enter the information and settings provided by your administrator or provider.
- Tap Save.
Connect to the VPN
Go to Settings>Network & Internet>VPN. Tap the saved VPN you want, enter your credentials, tap connect, and the associated app will open.
FAQs
How Much Does a VPN Cost?
Anywhere from a little to a lot. The price for a VPN subscription varies from provider to provider and reflects the feature set, speed, and geographic distribution of the network, among other things. The biggest factor in the price of a VPN is the length of the contract. A 24-month contract can cost you less than half per month than a monthly contract.
For a business, there’s the option of building and operating your own VPN server. There are obvious advantages to having control over features and accessibility. If you’re already operating in a cloud-based environment, hardware cost is minimal.
Can I Get a Free VPN?
There are many free VPN services on the market, and they should be approached and evaluated with caution. Speed, reliability, and availability are issues. And the provider has to pay for infrastructure somehow. Likely, that’s either by selling your information to third parties or serving ads. Neither is a good option.
Are Internet Speeds Slower on a VPN?
The short answer? Yes. Two factors primarily impede your speed. First, your traffic is going through at least one intermediary server, possibly several. Second, your traffic is encrypted and decrypted between points. The number of “hops” depends on the geography of the network and your location. (Multihop networks are designed to pass traffic through several servers for security purposes, as each pass offers further encryption of data.)
The slightly longer answer is: In a well-designed network, the slow-down will be negligible, in the low hundreds of milliseconds — not a serious problem unless you’re a gamer.
Can Anyone Access My VPN?
VPNs can be hacked. Hackers are forever looking for vulnerabilities in protocols, network management and configuration, encryption, etc. Even some of the biggest names in the VPN business have suffered breaches. On the user end, the usual precautions involving physical access, password security, and guarding against phishing and downloaded exploits apply.
Can I Be Tracked If I Use a VPN?
Data in transit is safe due to encryption, and your actual IP address can’t be read — the DNS server’s IP address appears instead. But in most jurisdictions, law enforcement can get court orders to have your provider turn over log files that can expose your traffic. And if you’re on a company VPN, of course administrators have access to your traffic.
When Shouldn’t I Use a VPN?
In some countries, it’s illegal to use a VPN, or there are complex laws regarding their use. Banks often forbid VPN use to prevent traffic from other countries. Some organizations, like schools and businesses, might deny connections from commercial VPNs, and some streaming services prevent VPN use to enforce geographic content blocks.
Bottom Line: A VPN is Part of a Layered Security Solution
VPNs provide a layer of security and anonymity that can be important to protecting your traffic and data, especially in a corporate setting. Any remote traffic to a business network should be cloaked in VPN security, either commercial or custom-built. Ensure that your devices are properly configured for VPN access to minimize hassle and disruption.
However, a VPN is only one component of a layered security solution. Your security suite, both as a user and as a corporate network, needs several other elements, like firewalls, intrusion detection, antivirus protection, and more to complete the picture. And, of course, a policy of user best practices is key.
Begin your security journey by investigating some of the available enterprise VPN solutions.








