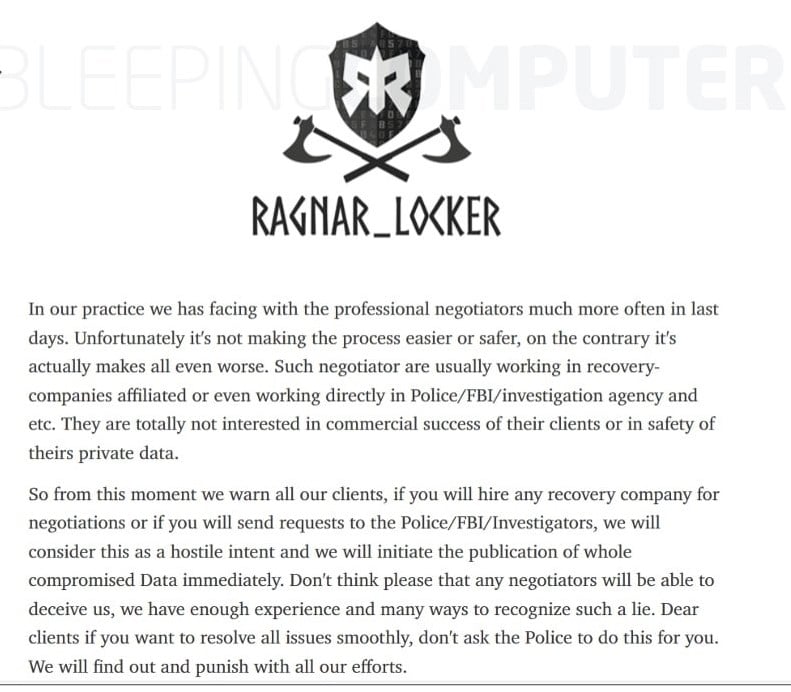
The cybercriminal gang behind the Ragnar Locker ransomware attacks is threatening victims that it will go public with data captured in an attack if they contact law enforcement agencies or hire negotiators.
The Ragnar Locker group posted on its darknet leak site a note outlining the warning, putting even more pressure on target companies (which the group calls “clients”) and increasing attention on the already high-profile debate about organizations paying ransoms.
In its announcement, the ransomware group said that “from this moment we warn all our clients, if you hire any recovery company for negotiations or if you will send requests to the Police/FBI/Investigators, we will consider this as a hostile intent and we will initiate the publication of whole compromised Data immediately.”
The gang added that victims shouldn’t think “that any negotiators will be able to deceive us, we have enough experience and many ways to recognize such a lie.” If law enforcement gets involved, the Ragnar Locker bad actors wrote that they “will find out and punish with all our efforts.” The warning was first reported by Bleeping Computer.
Ragnar Locker has been behind other novel ransomware attack methods, such as one of the earliest documented uses of virtual machines (VMs).
To Pay or Not to Pay?
The note represents a continued escalation of threats from ransomware groups, which for the past few years have used the threat of data leaks to ramp up pressure on victims to pay the ransom demands. Some groups have moved beyond simply using ransomware to encrypt a company’s data and demanding payment before releasing a decryption key and now try to steal the data and threaten to publish the data if the ransom isn’t paid.
The latest warning from the Ragnar Locker gang is just a continuation of efforts by cybercriminals to convince victims to pay the ransom, according to Dustin Warren, senior security researcher at SpyCloud, a company whose products aim to prevent account takeovers by bad actors.
“Ransomware operators are paid by putting high amounts of pressure on incident response and have many tools at their disposal to increase pressure, including posting threats like what we see here,” Warren told eSecurity Planet. “I don’t think that these threats are necessarily new and groups like Ragnar are already posting victim data if the ransom is not paid, even without further threats stemming from cooperating with investigators. It is not surprising that Ragnar is encouraging victims to forgo reporting these incidents, as any information shared with law enforcement could put ransom profits and affiliates at greater operational risk.”
Working with Law Enforcement
The threat is an indication that victims cooperating with law enforcement are working well enough that Ragnar Locker attackers were compelled to write the warning, he said. Many groups will become more aggressive if they themselves feel threatened.
Ragnar Locker has been creative in its efforts to get target companies to pay. Last year the group went as far as conducting a social media advertising campaign to get one victim – Italian drinks vendor Davide Campari-Milano – to pay the ransom.
The question of whether companies should pay the ransom continues to be a source of debate in light of the growing number of ransomware attacks. In a report last month, researchers with cybersecurity firm Fortinet’s FortiGuard Labs wrote that in the first half of 2021, they had seen a more than 10-fold increase in ransomware attacks year-over-year, pushed in part by the growing trend of ransomware-as-a-service.
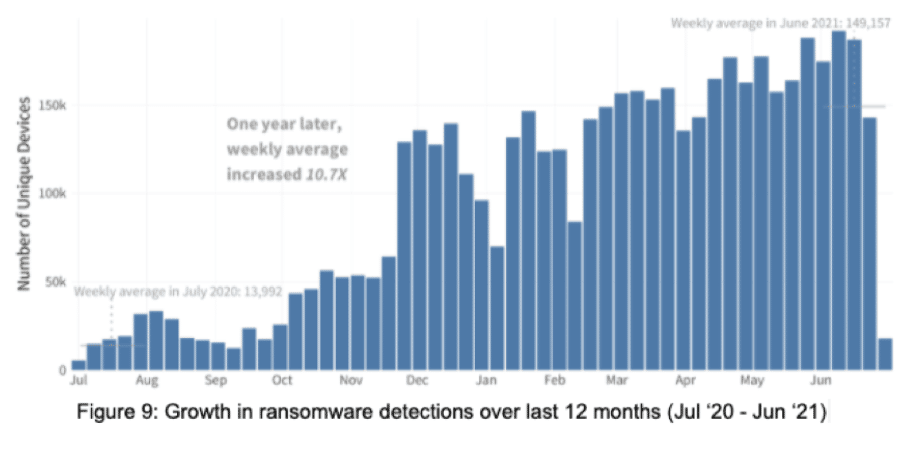
“In addition to renting ransomware, some operators have begun selling access to compromised corporate networks, making it that much easier for less technical criminals to get involved,” they wrote.
Ransomware on the Rise
Ransomware attacks have hit such high-profile sites as Colonial Pipeline, global meat processor JBS and Accenture. Ragnar Locker itself has been part of the trend, attacking Japanese game developer and publisher Capcom in November 2020 in a campaign that stole about a terabyte of confidential data – and demanding $11 million in ransom – as well as chip manufacturer ADATA (700GB of data stolen) in 2020 and aviation company Dassault Falcon Jet this year.
Colonial Pipeline paid its DarkSide attackers $4.4 million, with CEO Joseph Blount Jr. telling a Senate committee that he wanted to get the business back up and running as quickly as possible. Others, including Capcom and ADATA, did not pay.
Federal agencies like the FBI have urged companies not to pay ransoms, arguing that doing so could generate even more attacks and that sometimes the victims either don’t get a decryption key in return or the key they do get doesn’t work well enough to get all systems back running. The U.S. Treasury Department has suggested possible sanctions against some companies that pay a ransom.
However, FBI officials in July told the Senate Judiciary Committee that ransom payments should not be banned as a way of curtailing ransomware attacks, with one official saying that doing so could lead to even more extortion efforts on victims of the attacks.
Decryption Keys Often Don’t Work
SpyCloud’s Warren said the question of paying ransom is a difficult one, with every ransomware incident relative to the victim’s business continuity efforts at the time of the attack, which can determine how painful the incident is.
“I don’t advocate for anyone paying these groups in any situation,” he said. “There have been cases where victims have paid the ransom and the decryption tooling provided by the criminals was not reliable enough to decrypt all data, or it just didn’t work at all. Just about anything that can go wrong in these dealings with ransomware groups can and has gone wrong for victims in the past. While some victims who have taken the risk to pay the ransom have had their data decrypted, it is not the same story for each case.”
Given that the cybercriminals are looking for the ransom to be paid, “they are incentivized to make all sorts of promises with their demands when negotiating,” Warren said. “Not only that, but once the ransom is paid, there are things that can go wrong. If the group shuts down and no longer needs to maintain a reputation, what is to stop a ransomware affiliate with access to data from selling or leaking it?”
In its note to victims, the Ragnar Locker group talks about how even private negotiators are off limits to victims, arguing that such players often are working with law enforcement or recovery companies.
Further reading:








