PowerShell was the source of more than a third of critical threats detected on endpoints in the second half of 2020, according to a Cisco research study released at the RSA Conference today.
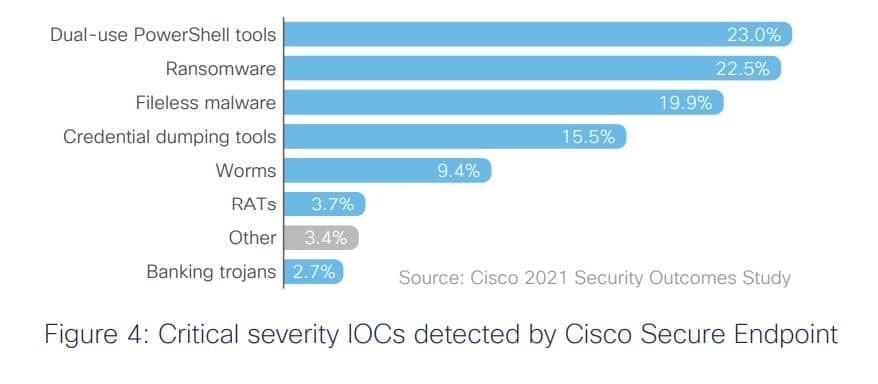
The top category of threats detected across endpoints by Cisco Secure Endpoint was dual-use tools leveraged for exploitation and post-exploitation tasks. PowerShell Empire, Cobalt Strike, PowerSploit, Metasploit and other such tools have legitimate uses, Cisco noted in the report, but they’ve become part of the attacker toolkit too. Such “living off the land” tactics can avoid detection when deploying foreign tools or code to compromise systems.
In second place was ransomware, and after the recent Colonial Pipeline hack probably needs no further comment.
The third most frequently detected critical Indicator of Compromise (IoC) group was fileless malware – also a common PowerShell threat. This type of malware does not use executable files and has no signature, making it challenging to detect. Fileless malware often manifests itself via suspicious process injections and registry activity. Common fileless malware types include Kovter, Poweliks, Divergent, and Lemon Duck.
Dual-use tools were also responsible for the fourth most common threat: Credential dumping, which is used by hackers to scrape login credentials from a compromised machine. The most commonly detected tool was Mimikatz, which Cisco Secure Endpoint caught dumping credentials from memory.
Those four categories are responsible for more than 80 percent of critical IoCs. The rest include threats like worms, remote access trojans (RATs), and banking trojans, with a mix of various downloaders, wipers, and rootkits.
“Based on Cisco’s research, PowerShell is the source of more than a third of critical threats,” noted Gedeon Hombrebueno, Endpoint Security Product Manager for Cisco Secure.
Protecting PowerShell from Hackers
Hombrebueno told eSecurity Planet that a “layered approach” is needed to secure PowerShell and other tools and utilities:
- Employing multiple prevention techniques to stop memory injection attacks that can penetrate endpoints by exploiting vulnerabilities in applications and operating system processes
- Protecting against script-based attacks to prevent certain DLLs from being loaded by some commonly exploited desktop applications and their child processes
- Using behavioral analysis to match a stream of activity records against a set of attack activity patterns to protect against malicious use of living-off-the-land tools
- Running complex queries and PowerShell activity monitoring on endpoints to gain deeper visibility on what happened to any endpoint
- Applying one-click or automated response actions to remediate the problem
Hombrebueno said Cisco Secure Endpoint can help with all those practices “without the added complexity.”
Cisco Secure Endpoint is one of our top endpoint detection and response (EDR) products. EDR tools are generally effective against PowerShell attacks.
See also: MITRE Protection Tests Shed New Light on Endpoint Security
How To Secure PowerShell
The Center for Internet Security offers a number of steps admins can take to help secure PowerShell, Microsoft’s command-line interface management tool for Windows and Windows Server.
First, only network admins and other IT pros need access to the Microsoft command-line interface tool, so prevent or restrict its execution and allow execution of signed scripts only. Disable or restrict Windows Remote Management while you’re at it.
CIS includes a tutorial for for managing Script Execution in Group Policy Settings.
To Turn on Script Execution in Group Policy settings:
- Click Start Menu > Control Panel > System and Security > Administrative Tools
- Create or Edit Group Policy Objects > Windows PowerShell > Turn on Script Execution
To Turn on Script Execution policy settings:
- Disabling Turn on Script Execution will mean that scripts do not run and PowerShell is disabled
- If you enable Turn on Script Execution, you can select the execution policy Allow only signed scripts
Digital risk management vendor Digital Shadows also offers a number of PowerShell security tips, including using Constrained Language mode, and NetSPI discusses 15 ways that PowerShell execution policies can be bypassed. PowerShell Protect is a downloadable tool that integrates with the Antimalware Scan Interface to audit and block scripts before they execute.








