Cybersecurity can be difficult to implement, and to make matters worse, the security professionals needed to do it right are in short supply. Managed IT security service providers (MSSPs) make life easier for organizations by providing outsourced expertise and tools at a fraction of the cost, time, and trouble of doing it yourself.
This article will explore the nature of MSSPs and how they can help businesses, nonprofits, governments, and other organizations have better security with less effort.
Jump ahead to:
- Why Businesses Need Managed Security Services
- How MSSPs work
- MSSPs vs MSPs
- 8 Benefits of MSSPs
- History of MSSPs
- 3 Top Managed Security Service Providers
- Bottom Line: MSSPs Help Clients Avoid Costly Breaches
Why Businesses Need Managed IT Security Services
Different companies develop IT management software, security tools, cloud infrastructure, and physical hardware, which makes it increasingly difficult to create a seamless security strategy. Organizations typically decide to outsource cybersecurity for a number of reasons:
- IT talent shortages make it difficult to hire and retain experienced cybersecurity professionals.
- Cyberattack sophistication and speed continues to increase, which puts additional pressure to detect and mitigate attacks earlier.
- Cybersecurity tool costs continue to increase and often require advanced training or cybersecurity experience.
- Expanding attack surfaces require additional skills to secure, maintain, and monitor an ever-expanding environment of assets such as mobile, cloud, and the internet of things (IoT).
- Poor integration of cybersecurity tools and IT infrastructure requires greater expertise to identify and close gaps in layers of security.
- Expanding compliance requirements and the growing number of regulations make it increasingly difficult for organizations to keep up.
What is a Managed Security Service Provider (MSSP)?
MSSPs are a subcategory of managed IT Service providers (MSPs) that specialize in the consultation, installation, configuration, monitoring, maintenance, and utilization of cybersecurity tools and techniques.
History of MSSPs
As internet service providers (ISPs) and telecommunications companies (telecoms) began offering commercial access to the internet in the late 1990s, they began to also offer firewall appliances and associated managed services. As cybersecurity needs expanded, so did the offerings and the variety of organizations that supplied them, such as ISPs, telecoms, MSPs, IT consultants, and independent cybersecurity specialists.
As cyber attacks continue to increase in number and sophistication, the need for MSSPs grows. Markets also continue to evolve in diversity of offerings and the variety of organizations providing services. Even the largest organizations with the most robust internal security teams will engage with MSSPs for specialty projects, penetration tests, and other specific needs.
MSPs vs MSSP Options
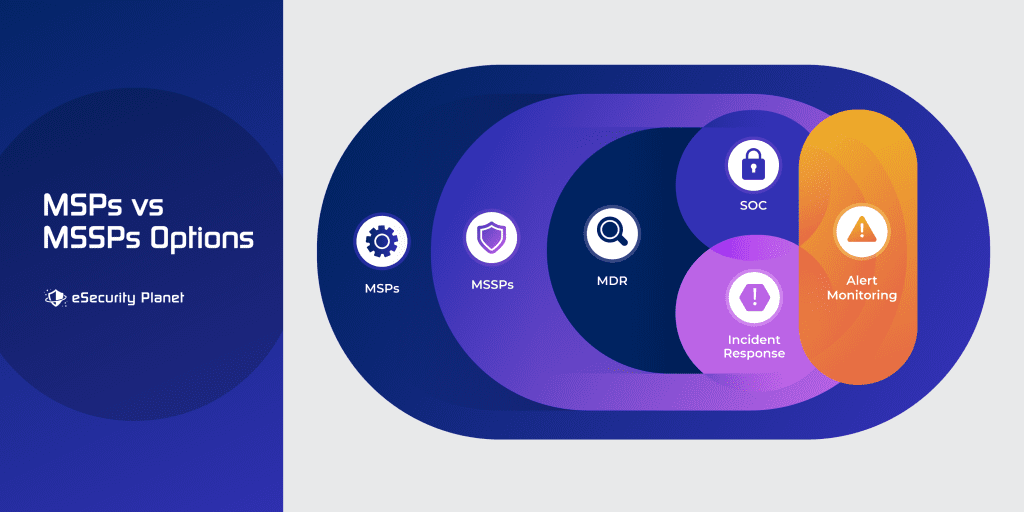
Some MSPs will also offer options for cybersecurity, but may not offer the full suite of options or the depth of expertise that a dedicated MSSP can provide. Other MSPs offer a full range of internally provided security services, while others subcontract to dedicated MSSPs for white-labeled security services.
Specialists have even evolved within the MSSP category to provide specific services. Corporations, MSPs, and even other MSSPs subcontract to specialists providing services such as:
- Alert monitoring focuses on the analysis of incoming alerts from security tools for networks, servers, or endpoints and the determination of which alerts are false alarms and which might indicate incidents in progress; sometimes offered as a service of SOCs or MDR.
- Incident response and remediation specializes in threat hunting, stopping attacks, blocking further attacks, and remediating affected systems; these specialists often offer forensics services to preserve evidence of attacks and can overlap with MDRs and SOCs.
- Managed detection and response (MDR) services monitor a broad array of alerts, often delivered to a security incident and event management (SIEM) tool or an internal SOC and then remediate any detected attacks.
- Security operation centers (SOCs) receive alerts and either respond directly to threats or provide validated alerts as a service to external MDR vendors, or even an organization’s internal incident response team.
For more options for IT solutions, consider reading Best Cybersecurity and IT Outsourcing Options.
MSSP Services
In addition to the type of MSSP, MSSPs provide a range of specific services. Organizations can outsource all cybersecurity needs to an MSSP or focus on specialty services such as:
- Access management uses identity and access management (IAM) and privileged access management (PAM) tools to control access to resources based on the profile of the users, devices, and services.
- Anti-spam services focus on eliminating dangerous and annoying SPAM messages from inboxes through configuration and monitoring of email security and similar tools.
- Application and website security monitors and manages tools to prevent incidents such as server attacks, distributed denial of service (DDoS), and cross-site scripting (XSS) attacks.
- Email security deploys tools, uses techniques, and implements protocols such as SPF, DKIM, and DMARC to prevent threats delivered via email and attachments.
- Managed endpoint security installs, configures, and maintains endpoint protection tools (antivirus, endpoint detection and response (EDR), etc.) and then monitors the endpoint alerts to respond to detected threats.
- Managed firewall services setup, configure, and maintain physical or virtual firewall appliances and then monitor alerts to respond to threats detected by the firewall.
- Intrusion detection and prevention system (IDS/IPS) services install, configure, and monitor tools on an organization’s network to detect (IDS) or automate responses (IPS) to threats; the services often also include MDR services to threats that cannot be automatically remediated.
- Penetration tests use tools and experts to probe cybersecurity defenses to locate weaknesses that should be fixed.
- Risk assessments and gap analysis of existing security controls provide strategic and technical evaluations of an organization’s cybersecurity strategy to determine if critical assets are sufficiently protected.
- Secure remote connection services can be provided by MSSPs through implementation and management of older technology such as a virtual private network (VPN) or through solutions such as virtual desktop interfaces (VDIs), desktop-as-a-service (DaaS), and browser isolation.
- Employee training and education services help to prepare employees for potential types of attacks, how to avoid becoming victims, and how to properly report incidents to security teams.
- Threat intelligence services provide information on the most recent vulnerabilities discovered, attackers, and attack trends.
- Vulnerability scanning and management helps organizations to detect, track, and resolve or mitigate vulnerabilities throughout systems (networks, Kubernetes platforms, etc.), assets (endpoints, servers, IoT, routers, etc.), and installed software (operating systems, applications, firmware, etc.).
- Web browsing security manages internal or local domain name service (DNS), secure web gateways (SWGs), firewall settings, and other techniques, tools, and protocols used to block dangerous or unwanted websites and URLs.
Most MSSPs will offer an array of these services, but some will also specialize in certain categories such as cloud, application, or email security. All MSSPs should be able to provide scoping, implementation, configuration, integration, and tool research capabilities within the specialities they provide. Reporting and auditing for compliance should also be available with most MSSPs as this requirement has become universal.
MSSP Pricing and SLAs
MSSP prices and service level agreements (SLAs) will be as varied as the potential solutions that are offered. In general, an organization can follow the tips in How to Find & Choose IT Outsourcing Services, but more emphasis will need to be placed on an MSSP’s ability to demonstrate, explain, and report on cybersecurity issues.
Keep in mind that no solution can be perfect and even a capable MSSP cannot prevent all threats. Some attacks will succeed and some breaches may occur. MSSP vendors should work with the organization to explain how they will limit the extent of the breach or attack.
Most SLAs are based on availability of the service itself, or how quickly the MSSP will issue an alert once a threat is detected. For example, a monitoring service may offer 24/7/365 monitoring and a 24-hour response time to detected threats. Premium services will reduce response times and add expert threat hunters, while low-cost services will increase response times or simply provide alerts for the organization to resolve.
How MSSPs Deliver Services
The MSSP will initially invest time to learn a client’s business processes and existing cybersecurity implementation before suggesting new managed security services or specific security tools. This audit of a client’s current security infrastructure and procedures creates a strategic gap analysis that provides a roadmap for improvement throughout the engagement.
While managed services might require switching tools or services, the MSSP must be able to explain the drawbacks, benefits, installation time, configuration challenges, and both the initial and ongoing costs of the new approach. MSSPs deliver their services directly through the tools, through the MSSP’s proprietary environments, and through remote access to the client’s environment.
Direct Tool Access
Many security tools offer multi-tenant capabilities and extend control of a customer’s system to the MSSP through the tool. Some commercial and proprietary tools will enable management by the MSSP through local or cloud-based consoles. In either case, the tool should create a secure tunnel between the tool and the environment under management without the need to create separate, secure connections such as VPNs.
Proprietary Environments
Many cybersecurity tools can be configured to send alerts out of the customer’s environment for analysis within the MSSP’s proprietary environment. For example, alert monitoring or SOC services will receive the alerts in their environment and generally will never need access to the client’s environment unless they are also providing incident response services.
Remote Access to Client Environments
Both cloud and locally hosted tools may need to create remote connections through indirect means. MSSPs providing configuration, maintenance, and incident response may also need to remotely access assets within an organization’s network.
Traditionally, this leads to the use of VPNs or remote desktop functions to enable remote access to specific machines. More integrated MSSPs may create management networks that connect to their clients’ networks using technologies such as software defined wide area networks (SD-WAN).
8 Benefits of MSSPs
The benefits of outsourcing to an MSSP are the same as they are for any IT managed service provider — with one notable exception (shared threat intelligence) that we’ll get to in a moment. But first, the seven benefits that MSSPs and MSPs share:
- Accounting and cost advantages enabled by an MSP splitting costs over multiple customers, elimination of upfront costs, partner discounts and the ability to use labor in less expensive regions
- Time advantages gained by bypassing training and evaluation time, fractional time use of experts, as well as obtaining 24/7/365 capabilities through a large staff or advantageous use of time zones
- Hiring advantages because MSPs can offer the salaries, consistent work, and challenges needed to recruit and retain IT and security experts or to scale up or down as a client’s needs fluctuate
- Instant expertise from employees with consistent and regular experience in installing, troubleshooting, and maintaining security tools, as well as configuration and reporting for compliance
- Organizational focus can be obtained when an organization eliminates the distractions of managing IT and security needs outside of the core objectives of the organization
- Competitive competence can rarely be obtained by internal professionals shielded from competition; however, MSPs and MSSPs face competitive challenges that force them to stay current and provide stronger punishments for mistakes
- Legal advantages for an organization can arise in working with outside vendors that can help to offset the costs of legal liabilities in the event of a breach or other cybersecurity incident.
- Leveraged threat intelligence allows the experience of protecting one customer to become experience that will be applied to all customers of the MSSP
Leveraged Threat Intelligence
Operations failures in IT tend to occur sporadically because of device failure or consistently because of IT architecture design flaws. However, security failures tend to occur because of an active adversary that uses a technique or tool to exploit vulnerabilities, misconfigurations, and other issues. These active attackers pose a much larger and more time-sensitive threat than simple device failure.
Fortunately, MSSPs defend a much broader environment than any one of their customers, so an attack on any one of their customers becomes leveraged as experience to protect all of their customers. Once an attacker is detected and remediated for one client, the MSSP can quickly make proactive adjustments or watch for indicators of compromise to disrupt similar attacks quickly and effectively.
3 Top MSSP vendors
Picking an MSSP is a bit like picking one’s favorite restaurant. The best choice for one type of organization may not be suitable for the tastes and needs of another organization. Many high-quality MSSPs are regional providers that will never make any top MSSP list, yet deliver services that fit the needs of their customers more effectively than a larger provider.
eSecurity Planet provides a list of the top MSSP providers as well as a guide for How to Find & Choose IT Outsourcing Services that will help smaller organizations locate potentially more suitable MSSP providers for their needs. Meanwhile, we will profile three top MSSP providers here to illustrate some common considerations for buyers.
Secureworks: Tech-focused Outsourcing
Atlanta-based Secureworks provides managed IT security services and a SIEM technology sold as a SaaS solution. Secureworks can provide outsourcing through ten global offices and focuses on assessments, testing, adversary exercises, and incident response. Organizations selecting Secureworks may view the company’s proprietary technology or the relationship to parent company Dell Computers as a deciding factor for a purchase.
WiPro: Global Outsourcing
As one of the largest outsourcing consultancies based in India, Wipro can offer a global reach with the advantage of low-cost resources within their home country. Many cost-sensitive organizations will favor outsourcing to WiPro or similar companies that use lower-cost tech labor overseas.
Verizon: U.S. Outsourcing
U.S. companies may trust U.S. vendors more in general and thus prefer working with well-known and established brands. Telecommunications MSSPs such as Verizon satisfy these needs and provide the financial security of a large corporate partner for equally large customers.
Companies in other regions often consider outsourcing to trusted telecommunication MSSPs in their home region for the same reason. For example, Europeans may consider BT (formerly British Telecom) a strong candidate and corporations in Asia might prefer NTT (Japan) or Trustwave (owned by Singapore Telecommunications, Ltd.).
Bottom Line: MSSPs Help Clients Avoid Costly Breaches
In an environment of increasingly sophisticated cyber attacks, organizations cannot hope that security threats will simply overlook their vulnerabilities. The cost of remediation and incident response outweighs the costs of preventive security so organizations should take preventive measures now.
Fortunately, MSSPs of all sizes exist to handle the varied security needs of organizations of all sizes. While not every MSSP will be a perfect fit, organizations can consider a variety of options to obtain distinct and tangible benefits from outsourcing to cybersecurity specialists.
Read next:








