No one can be an expert at everything, and very few organizations can afford to hire experts in every facet of information technology (IT). Yet without a solid foundation of IT fundamentals, even the most capable cybersecurity tools and experts will be undermined.
To ensure robust IT and security capabilities, most organizations turn to outsourcing to provide a wide variety of solutions to satisfy their even wider variety of outsourcing needs. To achieve the best results, corporations, non-profits, and government agencies must understand the ecosystem of vendors, purchasing models, pricing options, and how to find the right match for their specific needs.
Jump ahead to:
- 5 Steps to Engage Any Security or IT Outsource Partner
- The IT Outsourcing Purchasing Ecosystem
- 4 Security and IT Outsource Purchasing Models
- 6 Typical Security and IT Outsource Pricing Models
- Cycles of Outsourcing
- How to Find an IT Vendor
- Bottom Line: Careful Contracting Ensures Outsourcing Success
5 Steps to Engage Any Security or IT Outsource Partner
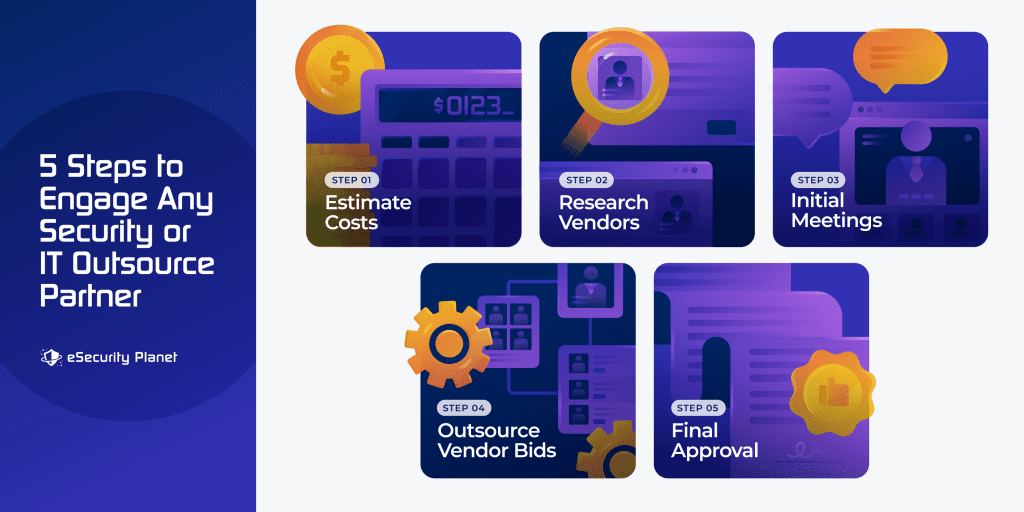
Engaging any IT outsourcing vendor will progress through 5 basic phases:
- Estimate costs for performing the work to be outsourced using internal resources for comparison with bids and for future return on investment (ROI) calculations
- Research Vendors that will be contacted to participate in the scoping and bidding for the outsourcing
- Initial meetings with potential vendors about needs; be prepared to discuss in detail to enable accurate bids
- Outsourcing vendor bid and contract drafts will provide a statement of work (SOW) drafts and service level agreement (SLA) and pricing for the specific engagement based on the described needs of the organization
- Final approval of the winning bid will occur once the organization reviews, approves, selects, and signs the contract with the winning outsource partner
Contracts may include options for the expansion of services or price lists that cover activities beyond the scope of the current engagement. All IT vendors understand that scope creep will often occur and therefore provide pricing to avoid delays caused by contract negotiations in the event those additional services will be required.
All organizations enter new relationships with the highest expectations. Unfortunately, some executives will believe that simply engaging an IT outsourcing vendor will deliver improved security and internal IT department performance. To ensure expectations come close to reality, the organization should ensure accurate communication of needs to the IT service vendor – after all, no one is obligated to deliver on unreasonable expectations.
The IT Outsourcing Purchasing Ecosystem
To the new executive or small business exploring IT outsourcing for the first time, the huge variety of potential outsource partners can be quite confusing. Sales reps and marketing teams just entering into the industry often add to the confusion because they will be unable to explain how their services compare with other options.
The broad categories consist of:
- IT Distributors typically sell one-off IT equipment such as firewalls, Wi-Fi routers, network access controllers (NACs), and servers that do not require significant modifications for installation and integration; distributors outsource some selling and installation functions, but not much for IT departments.
- VARs or value added resellers sometimes will appear on IT tool websites as integration partners; these vendors can handle installation and integration of purchased tools for an IT department.
- MSPs or managed IT service providers can absorb more of the IT department’s duties, from full outsourcing to focused IT services such as email, network management, cloud migration, or patch management.
- MSSPs or managed IT security service providers focus specifically on network security outsourcing, from the replacement of entire IT security departments or specific services such as email security, penetration testing, or incident response.
- MDRs or Managed detection and response (MDR) vendors focus specifically on the MSSP subcategory of monitoring IT systems, investigating potential incidents, responding to recognized incidents, and containing attacks. Post incident recovery, reporting, and IT system hardening may be included in the services, depending upon the type of agreement.
- SOCs or security operations centers focus on the MDR subcategory of monitoring IT security systems and investigating potential incidents; they hand off detected incidents to a separate incident response team inside the organization or at another MDR or MSSP for resolution.
- Cloud as-a-service offerings for infrastructure (IaaS), platforms (PaaS) or software (SaaS) also provide a form of standardized outsourcing, with a spectrum of IT functions from physical security to software updates pulled into the cloud provider’s realm of responsibility.
- Hosting provides specific server, website, or application hosting in an environment with less flexibility than modern cloud offerings.
- Colocation offers companies the most control over their hardware and IT systems as IT outsourcing will allow, and colocation facilities only absorb the infrastructure such as security, power, internet backbone connection, temperature, and fire control management.
To make matters somewhat confusing, there is often blurring between the different categories; some categories can offer services in other categories, and some vendors operate in multiple categories. For example, an MSSP could offer both onshore and offshore MDR or SOC services – more on this in the next section.
Geolocated Outsourcing
When selecting IT and security outsourcing, an organization will need to decide what type of geolocation option will be acceptable.
- Onshore security or IT services will be within the same country as the organization (for example, a U.S. company outsources onshore within the United States and an Indian company outsources onshore within India).
- Nearshore IT outsourcing typically refers to IT services outsourced to neighboring countries (French organizations can outsource nearshore to IT services providers in Spain, Italy, or Belgium).
- Offshore IT outsourcing applies to any country further than a neighboring country.
Multinational IT outsourcing companies and multinational organizations can cause onshore, nearshore, and offshore definitions to blur. However, in general, the term will be applied based on the bulk of the needs versus the bulk of the provided services.
4 Security and IT Outsource Purchasing Models
When creating a more formal relationship with an IT outsourcing partner, an organization will need to select the type of service model required for the services they need. This will depend not only on the needs of the organization but also the type of vendor with which the contract is made.
- Break-fix: contracted IT vendors only appear or provide services to fix broken equipment, reset passwords, respond to a cybersecurity attack, and other specific IT disruptions; no regular services are included.
- Consulting: Under these contracts, IT experts will provide advice, strategic planning, management, or design services; these services include fractional chief information officer (CIO) or chief information security officer (CISO) services.
- Maintenance and monitoring support: Under these subscription contracts, IT outsourcing vendors monitor operations and cybersecurity systems for signs of issues and will perform preventative maintenance or emergency incident response as required by the situation.
- Transactional: Transactional relationships apply to specific purchases or projects such as:
- buying a router from a distributor
- buying and installing a firewall through a VAR
- working with an MSP to design and implement a network in a new office
- contracting with an MSSP to resolve a ransomware incident.
6 Typical Security and IT Outsource Pricing Models
Just as an organization determines their preferred type of IT outsourcing vendor and service model, an organization will also need to determine their preferred pricing model.
All-inclusive pricing delivers all listed services in the contract for a flat fee, typically a monthly subscription. Similar to an all-you-can-eat buffet, the IT service provider charges one fee and expects to gain profit through efficiencies and because the customer will not use too many of the services within any time period. All-inclusive pricing, typically offered with maintenance or monitoring support contracts, will usually be offered with limitations for a maximum number of users, devices, and for excluded services (such as hardware purchases or incident response).
Contracted or ad hoc pricing will typically be offered in break-fix, consulting, and transactional relationships where the vendor will provide the services and products the organization requires under the terms and prices defined by the contract.
Cost-plus pricing may apply to specific transactions in a contract or for entire contracts – usually related to resold third-party tools or services. The IT outsourcing agent will deliver the basic service or product at their cost, with additional services and agreed upon margins added to the bill.
Per-device pricing provides scalable pricing where the IT provider offers services for a flat fee for each of the customer’s devices under management. Both vendors and customers enjoy the simplicity of per-device pricing, but executives often dislike being singled out for high consumption when they have larger numbers of devices (office computer, laptop, tablet, mobile phone, etc.).
Per-user pricing provides customers with a fixed flat fee for each of the organization’s users under management through the IT outsourcing vendor. Per-user pricing tends to be preferred in environments where the typical user will have more than one device (PC, mobile phone, etc.).
Subscription pricing will be seen most commonly with SaaS and monitoring-only contracts where the consumption and prices will be consistent and predictable.
Service Level Agreements
In addition to the type of pricing, any service will also come with associated service level agreements (SLAs) that detail the level of service for the contract. Pricing for SLAs will often be tiered by level of responsiveness and service. For example, a response within 48 hours of the initial request using only email communication will often be less expensive than the option to use voice or text messages or email communication and receive a response within four hours.
Additionally, costs for in-person IT services will often be higher than remote services because in-person labor must capture travel costs. Remote service will be much faster, but can be less secure, so in-person work can be required to work on sensitive systems such as servers or equipment within research labs. Other services also will simply always require in-person work such as pulling network cables or installing new storage devices in the data center.
Cycles of Outsourcing
IT outsourcing usage often can be seen to evolve in cycles. Most businesses will adopt or stop using outsourcing as their needs and strategies evolve.
Initially, a lack of IT requirements leads an SMB to hire “an IT guy” to help with IT setup and remain on-call for problems. As needs grow, the organization will adopt a more formal contract with a vendor to perform the work needed on a regular basis (patching, new computer setup, maintenance, etc.).
As the organization grows even larger in size, the organization may terminate outsourcing relationships or limit outsourcing to specific roles as the organization brings IT capabilities in-house. Naturally, as the organization grows even larger, the organization may recognize that the IT department itself is the size of a company, which then leads to outsourcing IT to cut costs and maintain the organization’s focus.
These cycles will often be driven by the management team’s changing opinion about IT, especially the CEO and COO. If IT can provide unique capabilities critical to the organization’s core mission, then those functions often will be seen as to be better controlled within the organization. If not, the organization’s resources should be freed up to focus on the core mission and IT functions will be outsourced.
How to Find an IT Outsourcing Vendor
Understanding the type of IT vendor and preferred purchasing models helps to define the scope, but then comes the task of locating suitable vendors. Buyers need to perform a variety of searches, such as web searches, obtaining referrals, pursuing opportunities through partners, or attending conventions.
After finding potential candidates, the buyer must then evaluate their capabilities to determine if the vendor will be a suitable match. It is OK for the vendor to lack the identical experience that matches the organization’s needs. In many cases technology expertise and a willingness to perform the work will be sufficient to deliver a good outcome. When in doubt, the organization can obtain a short-term contract with escape clauses to minimize commitments to poor choices.
For a more detailed exploration, consider reading How to Find & Choose IT Outsourcing Services.
Bottom Line: Careful Contracting Ensures Outsourcing Success
For any specific IT outsourcing need, there will be dozens, if not thousands of potential solutions and the vendors ready and willing to implement them. Every search should begin with a careful analysis of the needs of the organization and followed with a search for potential vendors that match those criteria. A careful search can lead to a successful relationship with an IT outsourcing partner that will enable both parties to thrive and grow.
Further reading: