Vulnerability scans play a vital role in identifying weaknesses within systems and networks, reducing risks, and bolstering an organization’s security defenses. Here we’ll discuss how to perform a successful vulnerability scan, some key factors to consider when conducting a vulnerability scan, and distinctions between vulnerability scanning and vulnerability assessment.
- 10 Steps of a Vulnerability Scan
- Factors to Consider in a Vulnerability Scan
- Vulnerability Scanning vs. Vulnerability Assessment
- Bottom Line: Performing Vulnerability Scans for Continuous Improvement
10 Steps of a Vulnerability Scan
There are many different types of vulnerability scans, but each requires much the same process for optimal effectiveness. From defining the scope to maintaining a regular scanning schedule, these 10 steps cover the critical aspects of a vulnerability scanning process to strengthen organizations’ security defenses, detect and resolve vulnerabilities, and increase overall resilience against possible attacks.
Step 1: Define the Scope and Objectives
It is critical to specify the scope and objectives before beginning a vulnerability screening procedure. Determine which assets, systems, and networks should be tested for vulnerabilities. Determine the scanning process’s exact targets, such as exposing known vulnerabilities, analyzing patch management efficacy, or identifying configuration flaws.
Select the system or network to be examined. Define the boundaries and components of the system that will be evaluated. It could include IP addresses, hostnames, or network ranges.
Step 2: Choose and Install the Right Scanning Tools
Choosing the right scanning tools are critical for ensuring accurate and speedy vulnerability discovery. Organizations often utilize multiple vulnerability scanning solutions for assessing different aspects of their IT infrastructure like endpoints, cloud assets, databases, and network devices.
There are several commercial and open-source vulnerability scanning solutions available to meet a variety of needs. Study the tools’ features, capabilities, and compatibility to determine which tools best meets the needs of your company.
- Download the vulnerability scanner tool and follow the installation instructions. Install the program on a computer or server that fulfills the required system specifications.
- Certain parameters, such as the network interfaces to scan, credentials for authorized scans, and scheduling options, may need to be configured during installation. To complete the setup, follow the tool’s instructions.
- Locate the installed vulnerability scanner utility on your PC or server once the installation is complete and launch the application.
Also see our tutorial, How To Use Nmap for Vulnerability Scanning
Step 3: Configure the Tool Settings
To guarantee accurate scanning results, it is critical to select the proper target type and adjust the parameters correctly. Some tools will require configuration after installation to correctly or thoroughly scan certain assets, network segments, or applications.
Vulnerability scanners generally categorize vulnerabilities into three risk levels by default:
- Low: There is no direct threat to cybersecurity
- Medium: Measurable but minimal exposure to security threats
- High: Severe cybersecurity threat exposure
Step 4: Configure the Scan Settings
With the scope defined and the tool selected and configured, the specific vulnerability scan settings and policies need to be set up..
Each tool may have a different interface and terminology, so you may refer to the vendor’s documentation or user guide for specific instructions. For instance, Greenbone OpenVAS provides a variety of scan settings to meet different scanning needs. Based on your requirements, you may develop unique scan setups or change current ones. These configurations include choices such as port ranges, scanning strategies, and time parameters, which allow you to personalize the scans to your individual environment. Begin by setting the scanning tool for your specific environment:
- Create the target. The first step in setting a basic vulnerability scan is to identify the system or network to be scanned for vulnerabilities. This usually entails giving the target entities’ IP addresses, host names, IP ranges, or network ranges. By specifying a target, you define the scope of the scan, indicating which systems or networks will be examined for vulnerabilities.
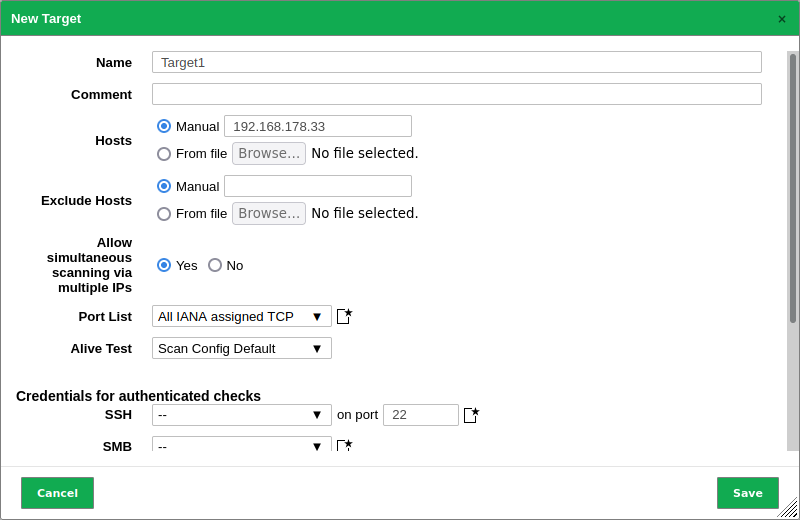
- Set the scan depth (full or targeted), scanning methodologies, and scan preferences. Customize the scanning parameters to meet your individual needs and goals. Adjust the scan intensity to fit your company’s demands and limitations.
- Create a task. Once the target has been defined, the next step is to create a task or scan configuration that details the scan’s unique parameters and settings. This involves deciding on the scan choices and techniques to be utilized (e.g., port scanning, web application scanning), and specifying any extra parameters such as time settings or exclusions.
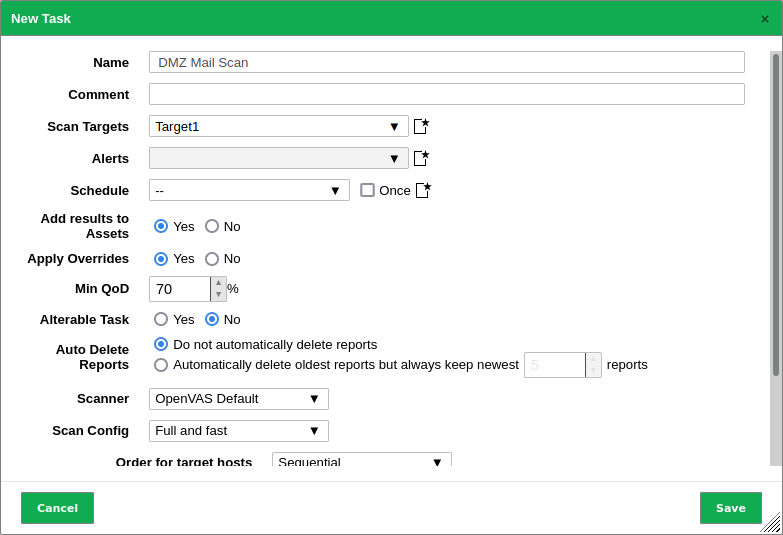
These settings specify which systems or networks to scan, which vulnerabilities to look for, and any special criteria or exclusions to use. Learn how to adjust the scan settings by exploring the tool’s menus, options, and documentation.
It is critical to organize your vulnerability scanning process by properly managing scan configurations. Multiple scan settings can be created for different circumstances or environments. Configurations may be simply renamed, duplicated, or deleted, allowing easier maintenance and modification.
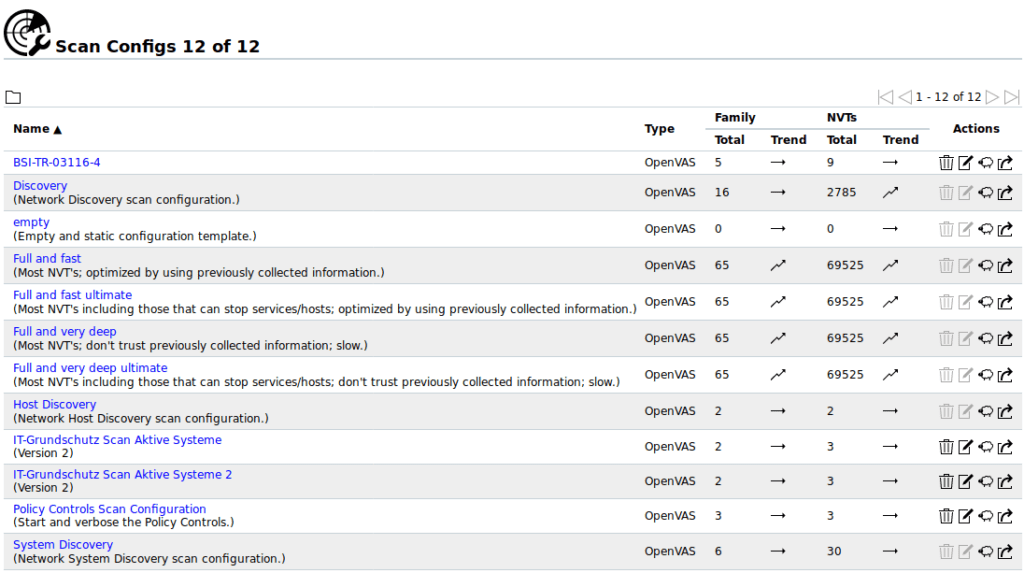
To accurately detect products and associated vulnerabilities, a full system scan should be done beforehand. This thorough scan with a comprehensive configuration helps in the identification of the software and services operating on the systems, which is critical for successful CVE scanning.
Performing a complete scan with authentication, which entails giving valid login credentials, may increase the number of CVE findings identified. Authentication enables the scanner to get access to additional system information to conduct a more comprehensive examination of potential vulnerabilities.
Asset Target Configuration
Before running the scan, ensure that the company has kept track of all of its assets, such as endpoints, servers, network devices, cloud instances, and other essential components. Relevant details regarding each item should be included in this inventory, including its IP address, hostname, operating system, and any other important details. It is critical that the vulnerability scanning tools are set up with the right set of assets to scan.
Manual changes to the asset list are required when automatic discovery is not possible or may not correctly capture all assets. This entails examining the current asset inventory, working with IT teams, and discovering any new additions, or environment changes. The asset list should be updated to include new assets, such as freshly deployed servers or network gadgets.
Some vulnerability scanning tools have the capacity to automatically find assets. To automatically identify assets inside the target environment, these technologies make use of a variety of methodologies, including network scanning, IP range scanning, or interaction with asset management systems. By doing this, manual work is reduced and the asset list is kept current.
Step 5: Initiate and Execute the Scan
After the target and task are configured, you are now ready to initiate the vulnerability scan by running the scan task.
Start the scan and wait for the tool to use the configured settings to examine the target systems for vulnerabilities. The total duration of the scan will be determined by demands such as network size, scan depth, and the complexity of your infrastructure. The scanner will actively explore the target, identifying potential weaknesses and gathering pertinent data for study. The scan findings will offer insight into the target environment’s security flaws.
Automated Vulnerability Scanning
Vulnerability scanning may also be conducted automatically by using automated vulnerability scanning solutions. In general, automated vulnerability scanners do port scanning, banner grabbing, OS and service detection, and signature-based detection. This helps the scanning tools gather information about the target systems. It compares the provided information against the tool’s vulnerability database using its signature-based detection technique to discover probable flaws. It then creates a detailed report outlining the found vulnerabilities and their severity levels.
A good vulnerability scanning tool should allow you to plan scans or trigger them depending on events or situations. This should enable users to schedule scans on a daily, weekly, or monthly basis, guaranteeing a consistent and proactive approach to vulnerability management.
When compared to manual scanning methods, automated vulnerability scanning is faster and more efficient. However, keep in mind that automated scanning may cause performance issues within the IT infrastructure if done during a wrong time period. To eliminate false negatives, it is critical to keep the vulnerability database up to date.
On-Demand Scan
In vulnerability scanning, on-demand scans are scans executed outside of the regular schedule or interval, generally in response to substantial IT changes. These modifications may involve the addition of new equipment, the deployment of a new architecture, software updates, network configurations, or any other significant changes to the IT environment.
Determine if these changes present new vulnerabilities or whether they alter existing vulnerabilities. If the changes are considerable, it is critical to update the scanning tool’s vulnerability knowledge base with the most recent information. This guarantees that the scan contains the latest recent vulnerability signatures and detection capabilities.
On-Demand Scans may be used to detect folder/file collaboration events and ensure that the appropriate remedial action is taken, hence facilitating collaboration/sharing-related remediation processes. You may use this to limit malware scans to new or updated files each time it runs a scan, or simply for specific users or folders.
Full scans are slower than incremental scans, so you can also opt to just scan for specified users before they are off-boarded. Use incremental mode as the data scope to scan only the modifications that have happened since the last scan.
Once you’ve configured the scanning tool to do an on-demand scan of the locations affected by the IT modifications, launch the on-demand vulnerability scan using the provided parameters. The scanning program will examine the selected locations, look for known vulnerabilities, and generate a report on any issues that are discovered.
Step 6: Monitor the Scan
Keep an eye on the scanning process to ensure that everything is going well. Some tools give real-time progress updates, indicating the number of assets scanned, vulnerabilities discovered, and estimated projected completion time. Monitor any faults or problems that might emerge throughout the scan.
The vulnerability scanning tools should be configured with the appropriate set of assets to scan when the asset list is updated. The asset list has to be frequently updated and maintained as a living document. To maintain accurate scanning coverage, any changes to the asset inventory, such as new deployments, decommissioned equipment, or modifications to IP addresses, should be quickly recorded in the asset list.
Some types of scans could result in application or IT equipment instability. Depending on the scan’s intent, it can cause a lot of network or system traffic, activate security measures, or even exploit vulnerabilities, which would interrupt operations.
In these situations, it is advised to put on hold and reschedule the scan for a time when it won’t interfere with regular activities. As an alternative, it could be helpful to remove some programs or pieces of equipment from future scans in order to prevent any potential instability to some systems. Balance the need for security assessments and the stability of operations.
It is important to be updated about the progress and results of vulnerability scans. A good vulnerability scanning program should allow you to customize notifications so that you receive alerts when scans are done or certain circumstances are fulfilled.
Email notifications may be configured to ensure that you receive the scan findings and any discovered issues as soon as possible. Your product should have documentation that walks you through the process of successfully customizing notifications, helping you stay on top of your vulnerability scanning operations.
Step 7: Interpret and Prioritize the Scan Results
While automated vulnerability scanners make detection easier, they are not perfect and can yield false positives. As a result, manually verifying the reported vulnerabilities and assessing their impact on the target systems is a critically important step.
Both automated and manual testing complement one another, so organizations should ideally perform both and not just rely on one technique over the other.
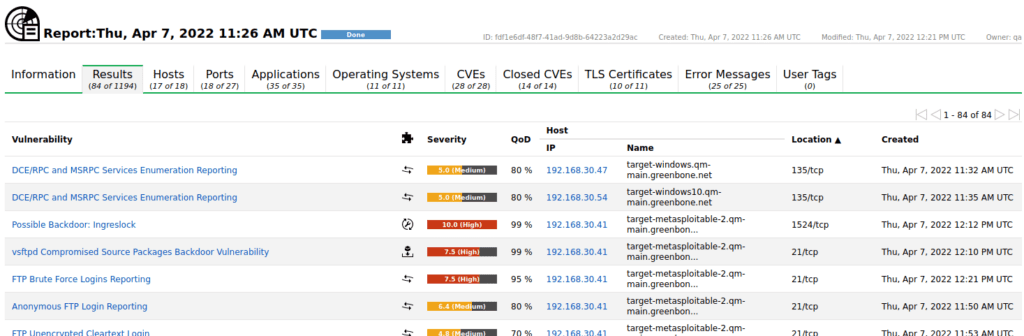
After running any scan, the report generated should include a list of items scanned. Check this list to ensure that all required assets (endpoints, applications, etc.) were successfully scanned.
To review the scan findings, go to the tool’s interface or the produced report. It should detail detected vulnerabilities, severity levels, and potential consequences. Examine and evaluate the scan data thoroughly to identify the potential harm and their severity.
Prioritize the vulnerabilities according to their criticality and the possible impact on your systems and data. The prioritization process may also consider relevant remediation methods such as patching, configuration modifications, or implementing security best practices. You may also create customized reports that are tailored to your needs, allowing for clear communication of discovered risks within your business.
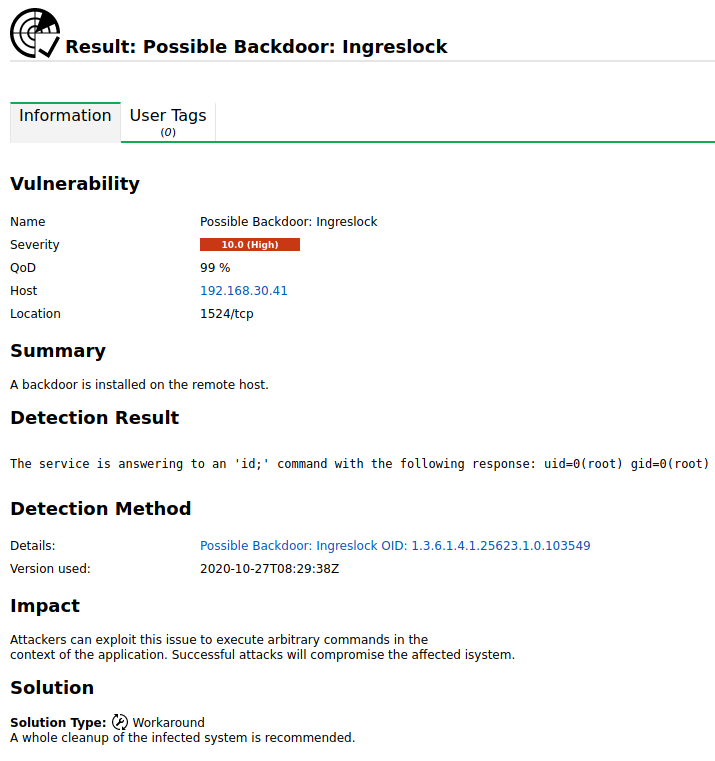
Step 8: Remediate and Mitigate Vulnerabilities
Create a remediation strategy based on the vulnerabilities discovered and their prioritization. Collaborate with your organization’s IT and security teams to fix the vulnerabilities by deploying software updates, changing settings, establishing security measures, or adhering to best practices advocated by tool and security experts.
Develop and implement suitable remediation procedures in collaboration with key stakeholders such as system administrators, network engineers, and security teams. Applying software updates, changing settings, adopting security best practices, or deploying extra security measures may all be part of this process.
Prioritize and then remediate the discovered vulnerabilities based on the scan findings. To remedy the vulnerabilities and enhance the overall security posture of the systems, follow the recommended mitigation measures generated in the report or consult other resources.
It is also important to note that while vulnerability scanning technologies give advice and mitigations for detected vulnerabilities, not all recommendations are appropriate or feasible for the organization’s unique IT infrastructure.
Some suggested mitigations may increase the risk of operational failure or conflict with current systems or requirements. To ensure that the chosen measures effectively address the vulnerabilities without introducing unintended consequences or disruptions, thorough consideration and evaluation of the best solution for each identified vulnerability, taking into account operational impact and compatibility with existing systems, is required.
Step 9: Rescan and Validate
Following remediation, you may opt to run another vulnerability scan to confirm that the discovered vulnerabilities have been resolved properly. This phase validates the success of the remediation methods you used and further assures the system’s security.
Vulnerability management teams frequently need to create thorough reports to indicate progress and effectiveness in resolving vulnerabilities, in addition to proving the efficacy of remediation operations. These reports are used for various kinds of tasks, including internal use, executive reporting, and compliance. The reports generally include information on addressed vulnerabilities, including specifics such as the detected vulnerabilities, their severity scores, the remediation work done, and confirmation of successful resolution.
Reports should also show any remaining unsolved vulnerabilities, assist in the prioritization of ongoing remediation operations, and track the organization’s overall security posture. These reports serve a vital role in delivering transparency, accountability, and compliance proof to organizational stakeholders, executive management, and regulatory agencies.
Step 10: Maintain Regular Scanning and Ongoing Security
Vulnerability scanning should be done on a regular basis. Schedule frequent scans to detect new vulnerabilities that may emerge as a result of software upgrades, system changes, or emerging threats. To maintain a comprehensive security posture, combine vulnerability scanning with additional security procedures like penetration testing, risk assessments, and security awareness training.
Vulnerability scanning should not be viewed as a one-time activity, but rather as an ongoing process. As new vulnerabilities emerge and systems change, it is critical to conduct frequent scans to detect and remediate emerging security flaws. Create a regular vulnerability scanning plan to enable continuous monitoring and quick vulnerability fixes.
Table 1. Recommended Scan Frequency for Average Businesses | |
| Risk Rating | Recommended Frequency |
| Infrastructure scans | |
| High | Monthly |
| Medium | Quarterly |
| Low | Semi-annually |
| Web Application Scans | |
| High | Quarterly or after significant change |
| Medium | Semi-annually |
| Low | Annually |
The frequency of vulnerability scanning recommended for an average company might vary based on several factors, such as the organization’s size, the compliance standards it must satisfy, and the availability of resources.
Larger enterprises with more income and a larger attack surface may need more regular scans to ensure complete coverage. Similarly, certain scanning intervals may be mandated by compliance rules. The availability of resources, such as dedicated security teams and scanning tools, might also impact scan frequency. Businesses must consider these variables and find a compromise between having a strong security posture and allocating resources efficiently.
Factors to Consider in a Vulnerability Scan
When using vulnerability scanning, various factors might influence the scan’s speed and accuracy. The speed of the scan is affected by the type of connection, authentication, number of hosts, and system resources.
Type of connection (Remote or Local)
The vulnerability scan’s speed and accuracy might be affected by the type of connection utilized. Remote scans are carried out over the network and may be slower as a result of inherent latency and other network limits. Local scans, on the other hand, are done directly on the target machine, which typically results in faster scans. When picking between remote and local scanning options, consider the network infrastructure and connection.
In the context of a large company, remote scanning usually refers to scanning from one office to another, whereas local scanning occurs within the same network. When picking between remote and local scanning solutions, evaluate network infrastructure and connection quality.
Furthermore, cloud-based vulnerability scanners have broadened scanning capabilities beyond local or remote limits. Cloud scanners use internet connection to scan multiple networks at the pace of available bandwidth, making them more flexible and scalable.
However, it is important to understand that remote scanning might pose difficulties, particularly in places with poor infrastructure or prone to weather or power outages. IT managers in high-bandwidth locations might overlook the problems that resources experience in such situations. These difficulties must be considered while assessing the practicality and dependability of remote scanning solutions.
Ultimately, when deciding between remote and local scanning, enterprises should thoroughly examine their network configuration, take into account connection availability and stability, and assess the possible influence on scan speed, accuracy, and overall dependability.
Authentication (Authenticated or Unauthenticated scans)
Vulnerability scans may be performed both with and without credentials. Scans performed with or without credentials may yield different results, and both processes should be employed to achieve a full evaluation. To reach the target system or network, authenticated scans require valid login credentials. Because they have better access to system information and can do deeper analysis, these scans can deliver more thorough results. Unauthenticated scans are faster and provide the perspective of a potential external attack, but they may give restricted visibility into some vulnerabilities and a false sense of security. To achieve a thorough review, it is advised that both authorized and unauthenticated scans be used.
Number of hosts being scanned
The number of hosts scanned might affect the total scan duration and resource utilization. Scanning a higher number of hosts will naturally take more time. When choosing the scope of the scan, it is critical to consider the available resources as well as the time restrictions. To successfully manage the workload, you may need to prioritize scanning essential systems or run scans in groups.
System resources
Some vulnerability scanners are resource-intensive, requiring a large amount of computing power, memory, and network bandwidth. It is critical to examine the scanning system’s available resources as well as the scanner’s potential influence on other processes. Resource constraints may have an impact on scanning system speed, accuracy, and even stability. Check that the scanning system has enough resources to support the vulnerability scanner of choice.
Vulnerability Scanning vs. Vulnerability Assessment
| Vulnerability Scanning | Vulnerability Assessment | |
| Definition | Vulnerability scanning is the process of identifying known vulnerabilities in systems, networks, or applications using scanning tools. It is a component of the larger vulnerability assessment process. | Vulnerability assessment is a systematic process of detecting, assessing, and prioritizing vulnerabilities in computer systems, networks, or applications. |
| Goal | The primary goal of vulnerability scanning is to find vulnerabilities and misconfigurations in a target environment as fast and efficiently as possible. | The fundamental goal of vulnerability assessment is to evaluate the entire security posture, consider any holes that attackers may exploit, and determine vulnerability management strategy. Some vulnerabilities, based on risk, will require prioritization and others may need to be accepted. |
| Method | Automated programs that search for known vulnerabilities based on a database of vulnerability signatures or patterns are primarily used in vulnerability scanning. | Involves a thorough examination of systems and networks using both automated and human technologies. |
| Scope | Vulnerability scanning focuses on identifying and generating reports of existing vulnerabilities without requiring an in-depth analysis of system setups or rules. | Vulnerability assessment comprises an examination of system settings, rules, and controls in addition to scanning for known vulnerabilities. |
| Results | A vulnerability scan often produces a list of detected vulnerabilities, their severity ratings, and occasionally remedial recommendations. | A thorough report summarizing found vulnerabilities, their severity, and suggestions for remedy is frequently included as part of the results of a vulnerability assessment. |
Bottom Line: Performing Vulnerability Scans for Continuous Improvement
Vulnerability scanning is critically important for maintaining a secure and resilient IT infrastructure, along with appropriate remediation techniques. Understanding how to conduct a vulnerability scan is an important skill for firms looking to improve their cybersecurity posture. Keep in mind that vulnerability scanning is a continuous activity that should be combined with other security procedures to provide a safe and resilient network environment.
Also read:








