Red, blue, and purple teams are designated security sub-teams that simulate cyberattacks and responses to test an organization’s cybersecurity readiness. Red teams simulate or actually conduct pentesting and threat hunting attacks to test organizations’ security effectiveness. Blue teams defend organizations from attacks and simulate incident response processes. Purple teams blend both roles as a mixed team or facilitate collaboration between the other two.
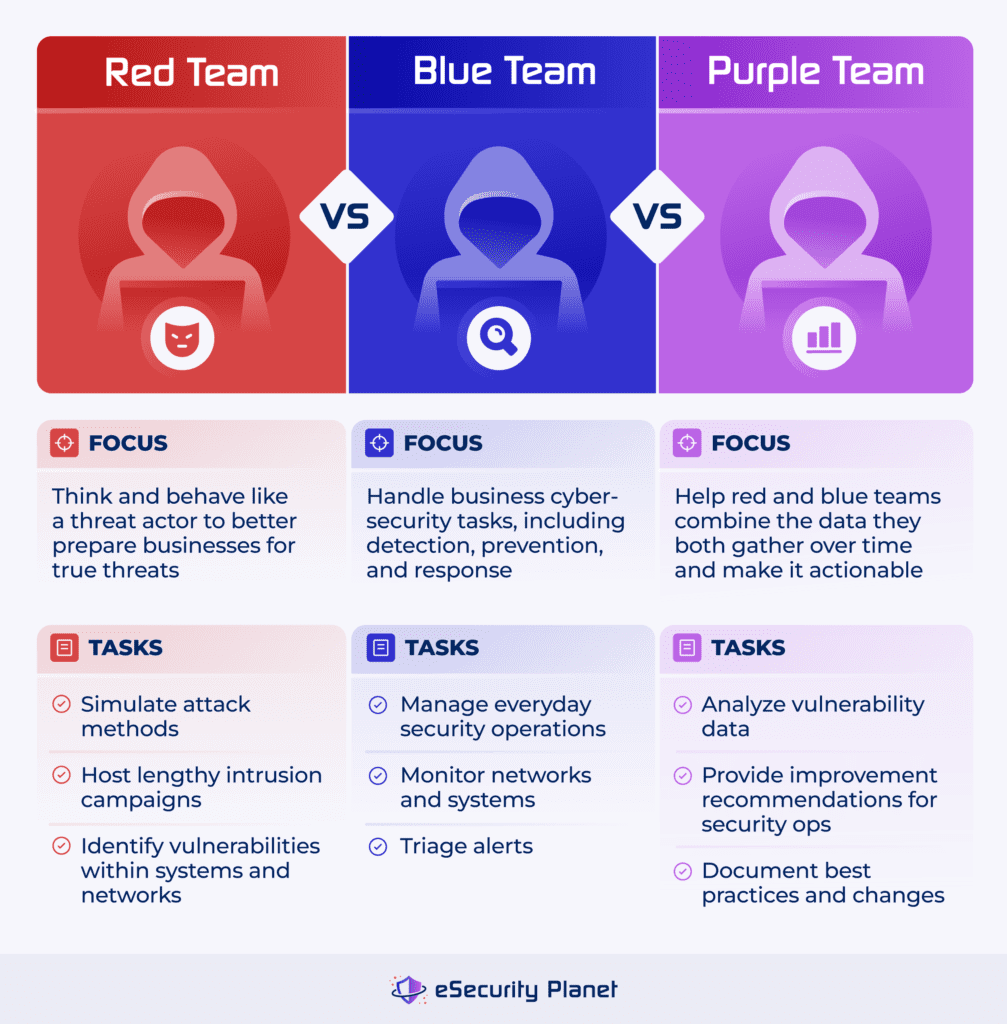
Understanding how the teams operate is important for organizations that want to test cybersecurity defenses before an adversary does. The ultimate goal is to understand the advanced threats a business may face in order to better combat threat actors. Splitting a security team into three subteams has both benefits and challenges. It’s also important to invest in your employees’ growth and consider the future of the industry when designating teams.
Table of Contents
Red Team Overview
Red teams simulate the tactics, techniques, and procedures (TTPs) an adversary might use against the organization. A red team’s activity can extend beyond cybersecurity attacks and vulnerability scanning to include phishing, penetration testing, social engineering, and physical compromise campaigns lasting weeks or more.
To perform intrusions and attacks, red teams will use tactics such as:
- Reconnaissance: They carefully explore computer systems and networks to look for weaknesses and backdoors.
- Malware deployment: Malicious software will often travel through computer systems somewhat autonomously, increasing an attacker’s reach.
- Vulnerability exploitation: Once the red team members find vulnerabilities in software and hardware, they’ll use them to attack and further access data.
- Phishing attacks: Red teams might also perform social engineering on current company employees to gain access to applications.
- Command and control servers: Once red teams have access to a server, they can then control that system.
Red teams employ intelligence on new and emerging threats as well as previous research on new attack techniques and offensive security tools.
Who Is Part of the Red Team?
Red teams are typically smaller groups compared to blue teams and often include a few members, such as ethical hackers, locksmiths, programmers, and social engineers. These members might be led by a director of penetration testing or a senior security consultant, and be organized into sub-teams based on the type of testing they’re performing.
Sometimes red teams are third-party contractors. This is ideal for businesses who want very few people inside the company to know what’s happening, including blue-team security personnel.
3 Objectives of the Red Team
Red teams’ main goals are to breach the network, successfully access their targets, and report their attack methods at the end of the process.
Breach the Business’ Infrastructure
Red team members tend to be recruited from the outside so that they have the true perspective of external adversaries. Whoever hired the red team will specify how many individuals within the organization know the attack is happening. Full-time security personnel may be aware, or they may not know so business leaders can gauge their incident detection and response capabilities.
Access Any Targeted Systems & Applications
Once a red team initially breaches the network, they’ll need to locate the data and systems they’re specifically targeting. This could be a specific piece of customer information or an entire database. Red teams typically have a set period of time in which they conduct an attack; this could range from a few hours to a few weeks or months.
Reconvene & Report
The red team will report their attempted attack methods to compare against alerts generated by existing security tools. Then they’ll be able to see whether there are gaps in configurations and overlooked issues. Business leaders and red teams will review successful attack findings and identify vulnerabilities and technology gaps to be addressed.
Challenges Faced by the Red Team
Red team engagements typically don’t have full coverage, unlike a standard penetration test, because they’re trying to genuinely test the company’s ability to block or detect an attack. They naturally won’t have as wide-ranging knowledge about the network because they don’t want the security team to suspect what’s happening. They want them to have as little information as possible going into the assessment.
This means that the red team doesn’t perform a full test of the company’s network. This type of engagement usually isn’t a completely thorough penetration test and won’t surface every vulnerability or weakness, nor is it a traditional vulnerability scan. If you’d like to learn more about penetration testing versus vulnerability scanning, read our guide to their differences.
Blue Team Overview
Blue teams simulate standard operations that protect an organization’s systems and networks from cyberattacks. Blue teams’ jobs include:
- Maintaining IT systems: Blue teams handle technical upkeep of computers, servers, and networking hardware and software.
- Handling alerts: They determine which potential vulnerabilities or issues need to be mitigated first.
- Patching vulnerabilities: Blue teams are responsible for tracking vulnerabilities and updating them as quickly as possible.
A blue team may be divided into sub-teams depending on the type of security controls it is responsible for, such as network security, endpoint security, or the security operations center (SOC).
Sometimes, blue teams are separate from the organization’s general security team, specifically designated to defend against red team attacks. They may be a specialized group in a cybersecurity simulation. But they may also just be the business’s everyday security personnel; this varies depending on how businesses want to run their internal testing.
Who Is Part of the Blue Team?
Blue team members might be led by a chief information security officer (CISO) or director of security operations, making this team the largest among the three. Blue teams tend to be larger because they must prevent all attacks, while red teams may simply select a few specific attacks to pursue. Blue teams consist of security analysts, network engineers, and system administrators.
4 Objectives of the Blue Team
Blue teams manage the everyday operations of IT and cybersecurity departments. They monitor systems for signs of suspicious activity, investigate alerts, scan for indicators of compromise (IoCs), and respond to recognized incidents.
Monitor IT Infrastructure & Computer Systems
Blue teams are responsible for standard security tasks like checking security alerts, deploying patches and fixing vulnerabilities, and reporting to company stakeholders and executives. In known internal testing scenarios, they work to combat any red team initiatives.
Handle & Triage Alerts
Blue teams also have to examine each alert and determine which are the highest priority and which can be addressed later. This process can involve manual decisions, but often it also involves automation — security products help teams process alerts, but blue team personnel also need a thorough understanding of each alert’s relative importance.
Scan Systems for IoCs
Consistently scanning your enterprise’s networks and computer systems for potential indicators of compromise is one of the most important responsibilities of blue teams. They review system logs and use security tools to find vulnerabilities so they don’t have to do it all manually.
Respond to Incidents
Blue teams are tasked with handling standard incident response procedures. When they locate an indicator of compromise, they’re responsible for blocking and mitigating them. This also includes analyzing and documenting how processes should be handled in the future.
Challenges Faced by the Blue Team
Often, blue teams have time-consuming manual work, like sorting through a barrage of security alerts and responding to incidents in a timely manner. This can be particularly challenging for smaller security departments.
Limited documentation and unclear processes can also detract from blue teams’ most important work. If security personnel don’t know exactly which team members are responsible for tasks and the order in which they should be done, they’ll struggle to mitigate vulnerabilities quickly, putting your business further at risk.
A blue team needs to focus on both detection and prevention to have a strong cybersecurity strategy. If you can’t locate vulnerabilities, you won’t be able to mitigate them. But focusing primarily on detection leaves the door wide open for successful attacks if some malicious indicators aren’t initially identified.
Purple Team Overview
Purple teams typically analyze the research of red teams and sync it with the operations for which blue teams are responsible. In enterprise environments, a purple team will typically be implemented in one of two ways:
- The same team serves as both red and blue: In a collaborative setting with small teams, the same team performs all tasks.
- The purple team sits between red and blue: In larger security departments, the purple team serves as a communication channel between the other two teams.
Alternatively, if a business designates a purple team just for a specific time period to find and solve vulnerabilities, the team could include personnel from any area of the security or IT department. These team members help consolidate information both of the other teams have gathered.
Who Is Part of the Purple Team?
The purple team might consist of incident response specialists, intelligence analysts, and security architects. These members are led by the director of security strategy or a chief security officer. Since the team is responsible for coordinating the efforts of the blue and red teams, the purple team may also be organized into subteams based on specific areas of responsibility.
3 Objectives of the Purple Team
Purple teams’ overall goal is information sharing and learning. The team should work to integrate the findings and recommendations of both blue and red team members by identifying areas for improvement in the organization’s defenses and ensuring that defensive measures actually work.
Improve Documentation Procedures
While businesses may already have existing security documentation, that’ll change as new vulnerabilities and attack data surface. Purple teams should help red and blue teams organize the most recent information they have and develop clear response and mitigation procedures with defined objectives and task owners.
Specify Opportunities to Improve
While red teams identify weaknesses and blue teams keep day-to-day security operations running, purple teams help both identify where they can improve. Vulnerabilities and indicators of compromise can be incredibly overwhelming, especially when there are too many alerts for security teams to keep up with on their own. Purple teams assist both blue and red teams as they make sense of the immense amount of information on their radar.
Develop Actionable Protective Strategies
Purple teams help security departments take valuable information about vulnerabilities and indicators of compromise and apply that knowledge to existing security operations processes. They improve communication and analysis between the two teams long-term, as they develop actionable strategies to apply vulnerability research to everyday security tasks.
Challenges Faced by the Purple Team
It can be challenging to find the right people. According to Ed Adams, the CEO at Security Innovation, purple teaming involves investing in your workforce. “Purple teaming… provides an opportunity to revisit job descriptions, learning journeys, and career construct retention pathways for your staff,” Adams said. “Strategically, organizations that embrace purple teaming are better positioned to withstand and mitigate the challenges posed by emerging threats.”
Finding people who view the red and blue teams’ work with an analytical eye and are skilled enough to transform those insights into actionable steps is critical for enterprises that decide to invest in purple teams. And if your business chooses not to have a purple team, you’ll still need personnel who can think strategically and have a knack for developing the rest of the security squad.
6 Benefits of Using Red, Blue & Purple Teams
The use of blue, red, and purple teams in cyber security can provide a comprehensive, proactive, and collaborative approach to cyber security, going well beyond regular scanning and testing for vulnerabilities. This can help organizations protect their assets and respond to security incidents more effectively. Here are six benefits of using these teams.
Tasks Divided Between Multiple Teams
If the entire cybersecurity burden is on one small team’s shoulders, they’ll easily get overwhelmed. It also helps large organizations to have multiple sets of eyes on the IT infrastructure and business network. While one team might miss something or feel overrun by alerts, another team can step in and assist.
Improved Security Posture
By combining the efforts of all three teams, a company may test, evaluate, and correct existing cybersecurity and incident response plans. These plans should address all areas of cybersecurity, including prevention, detection, and response. No area should receive the short end of the stick — they’re all important. This means configuring and using software that address prevention, detection, and response is important, too.
Effective Incident Response
Coordinating blue and red teams’ operations can increase an organization’s capacity to respond to attacks in a timely and efficient manner. The more infrastructure and network vulnerabilities you know exist, the better your security personnel can patch them. You’ll be better equipped to find attack paths and halt active attacks more quickly, too.
If you’re interested in learning more about incident response, read our ultimate guide to IR and check out the free templates available.
Enhanced Threat Intelligence
Red teams’ methods and research can provide practical experience to IT and security teams against new and emerging threats. Businesses can then utilize that concrete information — where are the vulnerabilities, and how specifically are they a threat? — to update and strengthen their defenses.
Compliance with Regulations & Standards
Using security teams can help organizations comply with penetration testing requirements within regulations and standards such as the Payment Card Industry Data Security Standard (PCI DSS) and the National Institute of Standards and Technology Framework (NIST). This does depend on the team’s specific actions and the individual regulations, since red teams sometimes perform actions that could be viewed as non-compliant or ethically dubious.
Improved Risk Management
Risk assessments help organizations prioritize devices or systems to patch and protect. Successful red team attacks can help identify overlooked risks, mis-prioritized security concerns, and ineffective controls to enable more effective security risk management.
4 Common Challenges of Security Teaming
While security teaming is beneficial for many enterprises, it has a few obstacles, including finding security procedures that actually work, identifying your company’s true needs, giving security leaders authority, and investing in each team. We’ve compiled some insights from cybersecurity experts on how to navigate security teaming and what it should actually look like for businesses.
Ensuring Your Security Works
Red, blue, and purple teams can help professionals understand the different security operations performed by businesses and third parties. But they’re only helpful constructs if your standard security procedures work. Successful cybersecurity processes should be every business’s first priority before worrying about color-coded team names.
According to Tyler Farrar, the chief information security officer at Exabeam, teams are largely buzzwords. “At the end of the day, you have to ask yourself: does any of that matter?” Farrar said. “Does the attacker care if you have a red team? Do they talk that way, do they structure themselves that way? The answer to all the above is no.” For Farrar, if people are mainly focused on the labels for teams, they’re hung up on the wrong initiatives.
Farrar also emphasized the importance of legitimately working technology and processes. “Are you able to do any of this?” he asked. “Do you have a SOC, a SIEM? Are you able to put these defenses in place?” These are all questions organizations need to ask — and answer — in conjunction with deploying red, blue, and purple teams.
Knowing & Meeting Your Business’s Actual Needs
Security teams can be useful constructs for large organizations to structure their personnel’s jobs. If you follow a strictly team-based approach, however, you’ll run into some limitations.
Dave Spencer, the director of technical product management at Immersive Labs, highlights one of these weaknesses. “A red team cannot tell you that you are secure, only that you are vulnerable, and provide an example,” he said. “If you already knew that, then it probably wasn’t of value for you to get a red team. A more effective use would be a purple team, which has the added value of increasing the detection and response rate.”
While large enterprises with built-out security strategies may be able to support all three teams, you may not need all of them. Pay attention to your company’s security needs. Additionally, red teaming is only successful when the rest of the security infrastructure has been structured well.
“Attack simulation of any flavor is a valuable exercise to run, but only when performed as part of a layered security strategy that addresses people, process, and technology,” Spencer said. “Red and Purple Teams are not silver bullets — they are just another layer of defense and verification.” Good strategy has to come first; any teaming is only secondary.
Giving Leaders the Command They Need
Full cybersecurity teams are a relatively new fixture in the corporate world, compared to teams like finance. And if the executive team or company leadership isn’t invested in cybersecurity, then security teams won’t succeed.
Exabeam’s Farrar believes that part of the reason security teams aren’t always successful is because chief information security officers don’t receive enough power. Farrar drew on his military experience when speaking about CISOs and business cybersecurity as a whole, including the decision-making process for security departments.
“You should always aspire to command. When I take that same thought process outside of the military and apply it to cybersecurity, and to the CISO, I ask myself, ‘Do CISOs have command? Are they truly equivalent and have the same responsibilities as the CFO or the Chief product officer? Do they have full command over their entire area? Can they truly make decisions?’ Probably not,” Farrar said.
Farrar also emphasized the responsibility of CISOs and other leaders to keep executives updated. “Is executive leadership truly bought into cybersecurity? Is it truly that important to them? I think that’s where we see a lot of underinvestment and under-resourced and under-trained teams in companies,” he said.
Ensuring Teams Have Relevant & Current Experience
Once enterprises have developed a team, they can’t just stop there. Security teams have to be on the ground, consistently learning and putting relevant knowledge into practice. Otherwise, they won’t be prepared to respond quickly and confidently to indicators of compromise and threat actors.
Dave Spencer emphasized the importance of making sure your teams actually know what to do when an event happens. “Exercising your teams is a key aspect of any security strategy,” he said. “Developing muscle memory over numerous drills means that security teams will know what to do when under attack… Business security teams should train how they fight.”
Genuine understanding is important here, too, not just cybersecurity theory. “It doesn’t matter if you can see an alert on your SIEM if you don’t know what it means or what to do with it,” Spencer said. “It doesn’t matter if you can see an attacker on your network if you don’t know how to neutralize them. And it doesn’t matter how many qualifications your security team gains if they aren’t being regularly exposed to current tactics, techniques and procedures.”
Training & Skill Development for Each Teams
If your enterprise is still building out teams or developing your security personnel’s skill sets, there are multiple courses and certifications available focused on different areas of cybersecurity or even specific teams.
- Training for red teams: Penetration testing and ethical hacker certifications help red teams learn how to simulate attackers’ strategies and find vulnerabilities in networks.
- Training for blue teams: Courses like SOC Levels One and Two are helpful building blocks to learn more about standard cybersecurity operations. CompTIA Security+ is also a great starting point.
- Training for purple teams: Any major security courses focused on purple teaming, like SANS SEC599 and SEC699, will help personnel better understand their team’s function.
Check out our list of cybersecurity certifications for personnel and aspiring security professionals if you’re interested in pursuing a certification.
The Future of Cybersecurity Teams
As more businesses recognize the importance of security to protect their finances, resources, and reputations, more will also implement security teams and departments. Developing a strong foundation for cybersecurity, including using the right products and technologies and training your personnel, is paramount if you want to protect your business:
- Implementing the standard security functions: Teams may not use a red-blue-purple format, but they’ll still need detection, prevention, maintenance, and incident response functions.
- Finding tools that actually work: Cybersecurity teams need products that work in general but also work well for their specific networks and applications.
- Investing in personnel: This includes taking time to train professionals on both procedures and products. An expensive EDR solution doesn’t do much good without team members who can understand the data in front of them.
- Determining how to use or not use AI: AI is still a buzzword in the security industry to some degree, but it would be short-sighted to not mention it as a potential tool. Your individual team will have to decide how beneficial it will be for you.
The future of cybersecurity looks like preparing teams to use the right technology while focusing on the building blocks of security: detecting, preventing, responding, and maintaining.
Bottom Line: Why Each Team Matters
Every organization needs everyday system and network monitoring and standardized security processes. But companies also need a second pair of eyes — sometimes from outside the business — to step in and say, “Here are the weaknesses and vulnerabilities you’ve missed.” And finally, businesses need to identify practical ways security personnel can patch vulnerabilities and stop attacks quickly.
This is security teaming in a nutshell. It doesn’t have to be complicated, but it does need to be comprehensive. Integrating blue, red, and purple teams offers a holistic approach to securing an organization’s systems and networks. Combined, teams can offer insight and knowledge sharing that increases awareness of cybersecurity roles, defenses, and adversaries.
To learn more about security recommendations for your enterprise’s networks, read our guide to securing your network next.
Kaye Timonera contributed to this article.








