A vulnerability management policy sets the ground rules for the process, minimum standards, and reporting requirements for vulnerability management.
An effective vulnerability management policy can help with the cyclical process of discovering and managing vulnerabilities found within IT hardware, software, and systems. A documented policy enables IT teams to create a trackable and repeatable process that meets the expectations of executives and conforms to compliance requirements.
This article helps organizations of all sizes to start the policy creation process with a fundamental overview and a downloadable template.
- Free Vulnerability Management Policy Template
- How to Create a Vulnerability Management Policy in 4 Steps
- Common Vulnerability Management Policy Sections
- Top 5 Vulnerability Management Policy Best Practices
- Top 6 Benefits of an Effective Vulnerability Management Policy
- Bottom Line: Adopt Vulnerability Management Policies Today to Gain Benefits
Free Vulnerability Management Policy Template
As both an example and a starting point, eSecurity Planet has developed a free vulnerability management policy template for organizations to download, modify to meet their needs, and use. Notes of explanation or how to use the template are enclosed [between brackets] and these sections should be removed from final drafts.
The sample patching policy contains many sections, but not all sections will be required for all organizations and others might require more details. See Common Vulnerability Management Policy Sections below for more details.
How to Create a Vulnerability Management Policy in 4 Steps
All security policies share the same four key steps to create a policy, and they are explored in detail in IT Security Policies: Importance, Best Practices, & Top Benefits. For a functional patch management policy, we summarized these steps as:
- Determine the Vulnerability Management Policy: Determine the responsible parties, who or what is covered, basic processes, validation methods, and reports.
- Verify the Vulnerability Management Policy: Formally check that basic policy developed in step 1 satisfies the complete needs of the organization and any compliance requirements.
- Approve the Vulnerability Management Policy: Draft official language and circulate the policy for approval by affected stakeholders and executives.
- Review and Modify the Vulnerability Management Policy: Periodically review the policy to ensure it remains updated and continues to satisfy the evolving needs of the organization.
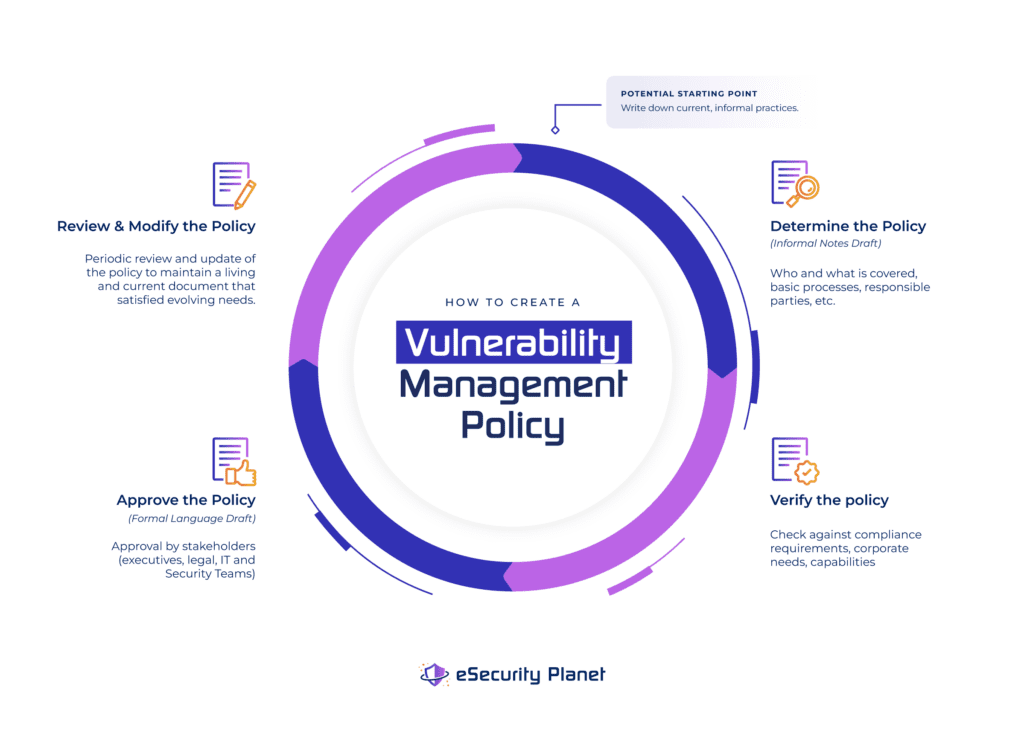
Don’t know where to start? Write down the current practice. Most IT teams have at least an informal process for obtaining and applying updates and patches, even if they are not written down or monitored.
While updates and patching remain a subset of vulnerability management, it at least provides a starting point for a more comprehensive policy. If the organization already has processes for double-checking configurations for networking equipment or open ports for server firewalls, those can also be added and broadened into a more comprehensive policy that encompasses more IT systems.
Although the basics of all IT security policy creation remains the same, vulnerability management is a frequently regulated requirement and organizations will need to apply extra caution in verifying compliance requirements. Additionally, the organization may be forced or choose to comply with compliance frameworks (NIST, PCI DSS, etc.) and industry standards. The policy development team needs to check these external regulations and revise any rule that does not meet the compliance requirements.
Some compliance standards will be broad and vague, others will be detailed or have specific requirements. For example, for the CIS Critical Security Controls, the requirements are broad:
- 7.1 Establish and Maintain a Vulnerability Management Process: Create and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this safeguard.
- 7.2 Establish and Maintain a Remediation Process: Establish and maintain a risk-based remediation strategy documented in a remediation process with monthly, or more frequent, reviews.
The CIS requirement specifies a need for the existence of a vulnerability management process, but does not specify the content or requirements for what might need to be included in the vulnerability management process or risk-based remediation strategy.
The credit card industry PCI DSS requirements will be more specific. For example, a restaurant chain may already have a patching process and policy that covers their computers. However, PCI DSS may require vulnerability scanning for a network, evaluation of point of sale (POS) terminals, and periodic penetration testing.
Practical limitations also apply. In the restaurant chain example above, perhaps the patch management tool managing the current patch management policy cannot scan for network vulnerabilities or for updates on the POS terminals. The current patching tool will need to be upgraded or complemented by a vulnerability management tool, a vulnerability management service, or a penetration testing service that can meet the PCI DSS regulatory requirements.
Common Vulnerability Management Policy Sections
In the most effective vulnerability management policies, there are required, recommended, and bonus (aka nice-to-have) sections.
Required Sections
These core sections should be part of every policy related to Vulnerability Management:
- Scope: What IT assets and systems are covered by the policy.
- Vulnerability Management Authority: Who is in charge and responsible for the vulnerability management policy and its execution.
- Vulnerability Identification: Determine the type of vulnerability scans, penetration tests, and other methods required to identify vulnerabilities for mitigation.
- Vulnerability Evaluation: How to verify, evaluate, and rank the severity of the discovered vulnerability.
- Vulnerability Priority: How to prioritize vulnerabilities in the context of the risk of the exposed assets.
- Vulnerability Mitigation Guidelines: Define the vulnerability mitigation process from mitigation design and testing, scheduling the mitigation, and verifying successful mitigation.
- Mitigation Tracking and Exceptions: Requirements for tracking new, ignored, and mitigated vulnerabilities.
- Vulnerability Management Reporting: How to measure success and compliance with vulnerability management with reports, plus how and what to report.
Recommended Sections
These sections help to flesh out the vulnerability management policy with additional rules to protect the organization and to help prepare the IT department:
- Asset List: A list of resources or links to asset lists to help define the scope of systems and software tracked for patching and updating.
- Audit Controls and Management: Outline what reports, logs, and information can satisfy internal and external auditors to track vulnerability management success and verify vulnerabilities have been successfully mitigated.
- Enforcement: Penalties that the IT department may incur for failure to execute the vulnerability management process.
- Distribution: Who must or should receive the vulnerability management policy.
- Policy Version: Tracking versions and approvals of the vulnerability management policy.
See Top IT Asset Management Tools for Security to discover the best ITAM software and their key features.
Bonus / Nice-to-Have Sections: These sections do not change the core elements of the vulnerability management policy, but can make the policy more usable or comprehensive.
- Overview: Sets expectations and goals for the policy.
- Definitions: Technical term and acronym definitions can be useful to help non-technical readers understand the policy; generic terms can be defined for clarity.
- Compliance Appendix: Copies or links to relevant compliance frameworks with which the organization must comply.
Top 5 Vulnerability Management Policy Best Practices
All security policies share the same five best practices to create a policy, and they are explored in detail in IT Security Policies: Importance, Best Practices, & Top Benefits. For a functional patch management policy, we summarize these steps as:
- Focus on What to Do, Not How: By focusing on goals and objectives, a policy can set standards while allowing the vulnerability management team the flexibility to determine the best solution to meet those goals and objectives.
- Make Policies Practical: The vulnerability management team needs to be able to understand and implement the policy.
- Right-size Policy Length: Too short and the policy may not have sufficient requirements to be verified; too long and the policies may become over prescriptive or hard to understand.
- Keep Policies Distinct: Overlapping policies can introduce conflicts or become more difficult to keep current.
- Make Policies Verifiable: Effective policies require reports that prove the policy is both in place and effective.
The eSecurity Planet template seeks to be more comprehensive than some organizations may need, so every organization should review the template and add or remove content to fit their needs.
Beyond the standard best practices, vulnerability management benefits from additional considerations. For example, to maintain practical policies, exhibits or additional reports can be used to provide details that may need to be changed more frequently than the policy itself. For example, in the sample template, the IT team is required to maintain a list of the types of vulnerability scanners used to detect potential vulnerabilities.
Although every organization should begin drafting policies based upon existing practices and capabilities, this can lead to a trap of preserving incomplete processes into written policies. The organization should carefully examine their environment and ensure the policy reflects their true needs.
For instance, an IT team of a hospital may use a commercial tool to conduct vulnerability scanning of their IT environment, but the tool may only scan PCs, network devices, and servers, which leaves an enormous range of healthtech devices unscanned for vulnerabilities. Their policy requirements should not reflect the limited devices currently scanned, but the full range of devices that need to be included in the vulnerability management process.
Top 6 Benefits of an Effective Vulnerability Management Policy
Organizations of all sizes tend to avoid the hassle of documentation because the task seems overwhelming, tedious, and constraining. However, any effective security policy delivers six key benefits:
- IT Hardening: Creating and reviewing a security policy forces the IT and security teams to evaluate and potentially improve security practices.
- Employment Defense: In the event of a breach, IT and security teams can be protected if they can show compliance with an executive-approved written policy.
- Executive & Board Member Peace of Mind: Plain-language reports required by effective policies can illustrate the security posture of the organization clearly to executives and the board.
- Litigation Protection: Breaches happen, but lawsuits and regulators will be less of an issue if the organization can provide reports and other evidence showing compliance with policies that encompass reasonable security efforts.
- Compliance Easy Button: When the policy encompasses the compliance requirements, policy-required reports will automatically be available for auditors.
- Improved Operational Efficiency and Resilience: Effective policies ensure stronger security postures, eliminate configuration issues, and decrease the opportunities of attackers causing operational disruptions.
Bottom Line: Adopt Vulnerability Management Policies Today to Gain Benefits
No policy will be perfect, but organizations should start developing a vulnerability management policy as soon as possible so they can begin to reap the benefits, such as IT hardening and simplified compliance. The adoption of any policy will be an iterative process, so get a good version 1.0 in place and be prepared to revise it to meet real-world conditions.
More information on Vulnerability Management and Related Topics:








