Integrated risk management (IRM) is a discipline designed to embed risk considerations for the use of technology throughout an organization. In other words, it links technology spending directly to the value of the resource protected and the associated risks controlled by that technology.
To explain IRM, in the article I outline its key components, benefits, how IRM differs from other risk models, and IRM frameworks. Read also about steps needed to implement effective IRM, best practices, and where to take classes or get certified in IRM.
Table of Contents
7 Key Components of Integrated Risk Management
IRM tries to put an understanding of risk in each employee, at every level of an organization, at a similar level to each employee’s natural understanding of money, command structure, or ethics. To achieve this goal, an organization must understand and incorporate the seven key components of IRM: business needs, operations, risks, controls, monitoring, response, and reporting.
Business Objectives
Business objectives define the goals of an organization beyond simple financial measures of sales and profit. What objectives deliver maximum value to shareholders? For example, a clothing brand might select a business objective such as to develop unique and appealing designs. Meanwhile, a 911 (or 999) call center’s objectives will probably focus on high availability of services and quick response times for callers.
Operations Systems
Operations systems deliver the business objectives using people, processes, and technology. In the examples above, the clothing brand will use traditional and computer-aided design prototyping and marketing research. The 911 call center needs a robust phone system, trained staff, and a decision-tree process to understand how to route issues to the appropriate emergency or non-emergency agencies to address a caller’s needs.
Critical Risks
Critical risks define the significant and likely risks that threaten the operations systems or business objectives. For example, the clothing brand faces the risk that someone might steal their designs or destroy their marketing research. The 911 call center would be more concerned about utility disruption (electricity, phone) or a computer system crash that disrupts their ability to dispatch appropriate emergency responses.
Mitigating Controls
Mitigating controls prevent or reduce risks. In our examples, the clothing brand secures a segregated design team with physical locks on the doors, extra computer security to prevent digital theft, and a backup solution for their marketing data. The 911 call center guards against utility disruption with power generators and multiple phone systems, and against computer crashes they deploy redundant computer systems, load balancing, etc.
Threat Monitoring
Threat monitoring examines risks and controls to predict or detect potential issues. The design company will install surveillance cameras and data loss prevention (DLP) technology to monitor physical and digital theft attempts. The 911 call center will use weather forecasts to predict power outages and network monitoring software to watch for both operations and security issues to computer and phone systems.
Threat Response
After detecting a threat, an organization needs to respond to it. If the marketing data computer crashes, the design company will need to respond and restore the computer and the data. If the 911 center suffers a power outage, they must turn on the generators to provide temporary power.
Feedback Reporting
Feedback reporting delivers monitoring results to the correct people to take action or to adjust controls. At the clothing brand, the surveillance camera may catch people sitting in cars across the street and using binoculars to spy on the design team, which may require installing window covers. At the 911 center, a power outage may lead to the unfortunate discovery that the generators lack sufficient fuel and may lead to additional control to maintain fuel reserves.
Top 5 Benefits of Integrated Risk Management
Integrated risk management provides many repeatable and measurable benefits. These include new opportunities, clear priorities, and better security, performance, and resilience.
Additional Upside
Most risk strategies focus on controlling downside risks, but IRM also considers and promotes upside risk opportunities. For example, implementing peak-time computing resources to Amazon not only controls operations risk during the holiday season but also opens up opportunities to rent excess computing power and develop AWS cloud computing.
Clear Prioritization
The IRM process associates value for data, systems, and the risks that potentially threaten them. The values provide clear and justifiable prioritization easily communicated throughout the organization to align goals for operations, security, and finance.
Hardened Security
Thorough IRM will lead to effective network security with layers of physical and different types of network security solutions to protect assets against risk. These controls will be tested and continuously monitored and thus lead to more effective and hardened security overall.
Optimized Performance
System complexity can introduce fragility and obscure data paths for key or regulated data. Integrated risk management identifies and eliminates unnecessary complexities to simplify risk analysis and threat control and introduces optimized operational performance as a potential side effect.
Stronger Resilience
Effective IRM anticipates the most likely issues that would cause operations and security disruption and implements steps to control those issues. Systems become hardier and more efficient, break less often, and recover more quickly to improve general resilience.
ERM vs IRM vs GRC vs SRM: Is There Any Difference?
All risk management strategies strive to use threats to business processes to determine risk. Risk then prioritizes security controls with the goal to deliver truly effective security as opposed to checkbox compliance. The most common risk management practices include:
- Enterprise risk management (ERM): Focuses on minimizing tactical and operational risk to achieve business objectives without focusing on technology, strategy, or data.
- Integrated risk management (IRM): Evaluates daily risk impacts through the lens of specific technologies and less from a data, business objective, or strategy perspective.
- Governance, risk, and compliance (GRC): Tracks data risks in a daily regulatory context with less attention paid to technologies, strategies, and business goals.
- Strategic risk management (SRM): Places strategy at the core of risk analysis, with less concern for minimizing risk or a specific business goal, data type, or technology.
How to Integrate IRM with Compliance & Regulatory Requirements
All data security compliance and regulation requirements focus on specific risks for specific assets. To integrate these requirements into IRM, evaluate those risks, quantify them, and associate them with specific systems and controls.
For example, the Health Insurance Portability and Accountability Act (HIPAA) regulates personal health information and imposes fines for data breach or data inaccessibility. IRM accounts for HIPAA data by tracking associated repositories, transmissions, and systems, as well as increasing risks with HIPAA fine estimates. Escalated risks increase security budgets, and IRM tracks, monitors, and reports on each data type, system, or control to show compliance.
What Is an Integrated Risk Management Framework?
IRM frameworks provide rigorous processes to implement IRM throughout an organization in a formalized and repeatable fashion. Without frameworks, you can understand what makes up an IRM and its benefits but lack the means to implement it. IRM and other risk management tools can offer vendor-specific risk frameworks; however, tools provide only a partial solution. All frameworks need to include six key steps, covered below, to develop an effective IRM program.
6 Steps to Build an Effective IRM Framework
An IRM framework requires a cycle of six stages in three phases. In the planning phase, develop a strategy and assess potential risks. In the implementation phase, apply risk mitigation and monitor the results. In the management phase, respond to incidents and report status.

1. Develop a Risk Strategy
The IRM framework cycle begins with a planning stage that documents objectives and scope. Scope could be an entire organization, a division, a system, or specific data. Incorporate feedback from all stakeholders within the scope: operations, leadership, process owners, IT security, and in some cases vendors or customers. If every stakeholder understands how risk ties to their objectives and responsibilities, they’re more likely to buy into the IRM strategy.
In this stage, incorporate governance or compliance concerns and establish the risk appetite (maximum amount of losses tolerable). All business, operations, and cybersecurity risk management objectives should be concrete and measurable in the reporting stage and each component in the scope should be tied to a business objective to understand what is at risk in the event of component compromise.
2. Assess Risk
The planning phase continues with a risk assessment of the different elements determined to be within scope during strategic development. Risk assessments consider risks individually and in combination, and with respect to both negative risks (business losses) and positive risks (business gains). The goal will be to produce a risk register of data, people, processes, and systems associated with the IRM scope.
Make risk measurable, and preferably quantifiable, using probability and dollar amounts. Qualitative risks can be quicker to generate but lack tangibility and don’t assist in determining a true risk appetite. Both internal and external risks should be considered since both data breaches and hurricanes can significantly impact the business.
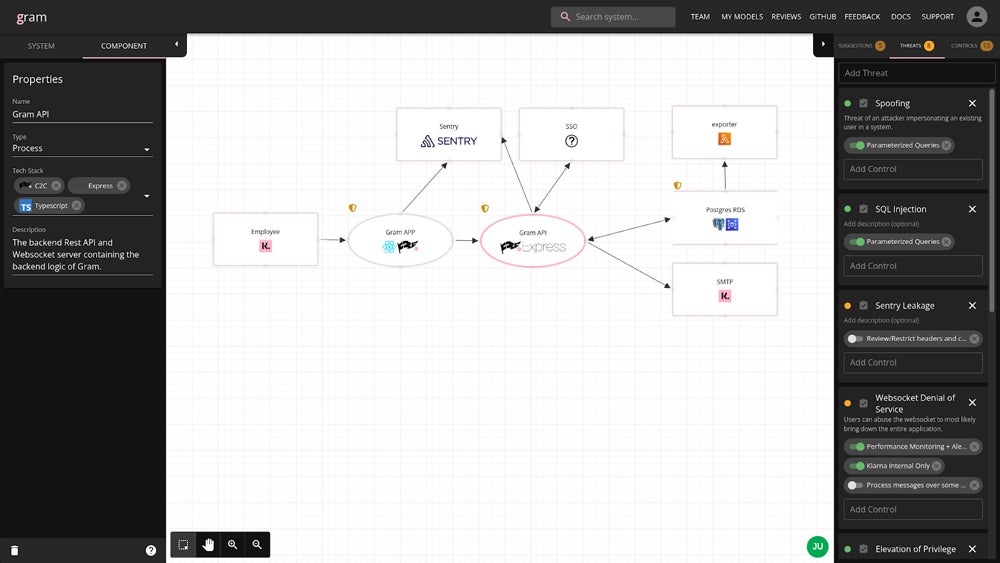
Many paid and free tools focus on enabling this stage of the IRM process. For example, Klarna recently published Gram, a visual tool for associating risk to systems and data flows free to download from GitHub. Whether using an automated risk assessment tool, an IRM tool, or a free-use program, map out data flows in detail and capture all possible points of failure.
3. Mitigate Risk
The risk mitigation stage of IRM moves the process from theory into implementation. The risk assessment stage creates a risk register of risks that can be compared with the risk appetite developed in strategic development. Risk that exceeds the business risk appetite must be eliminated or reduced during the risk mitigation stage.
Stakeholders should brainstorm how to manage risk through controls, process changes, insurance, or business decisions such as “stop taking credit cards for payment.” This stage seeks to develop a prioritized set of optimal risk control options.
4. Monitor the Status
Established security controls should mitigate risk, but set up status monitoring to check. This implementation phase of the IRM framework focuses on verifying that controls work or don’t work as expected. Monitoring detects system failures, indicators of compromise, vulnerabilities, and operations drift.
Vulnerability scans, penetration tests, compliance audits, and network monitoring provide components of network security monitoring. Each form of monitoring provides metrics and reports to be used to validate the effectiveness of existing controls, detect potential attacks, and predict operating system failure.
5. Respond to Events
When monitoring detects a risk event (device failure, potential attack, exposed vulnerability, etc.), event response determines the processes and procedures to respond to risk quickly and control damage. Develop this management phase of the integrated risk management framework in advance, even if it won’t be used regularly.
Prepare incident response plans in advance for likely events (ransomware attack, firewall zero-day vulnerability, etc.) to eliminate time consuming decisions such as which executives to contact, when to contact cybersecurity insurance companies, and when to bring in an external incident response team. Plans can’t cover all possibilities, but most events can build off of existing plans and faster responses limit potential damages.
6. Communicate & Report Results
The communication and reporting stage outlines the different types of communication required for regular communication and for specific events. This management phase builds off of status monitoring and event response. Monitoring will generate status reports and penetration test reports that validate existing controls. Each event response generates incident response reports that detail the incident response handling from detection through remediation.
Clearly defined metrics should be used for regular reports used in decision making, compliance reports, and reporting to the board of directors. Stakeholders need to receive communication that summarizes these reports at a suitable technical level and appropriate detail level. An effective IRM provides organization-wide reports to inform employee training and to help foster a risk-aware culture.
Top 5 Best Practices for IRM Implementation
Running through a framework doesn’t improve risk management by itself. Best practices ensure effective IRM by ensuring the proper ingredients for success, specifically to tie IRM to business practices, classify assets, centralize operations, standardize processes, connect systems in detail, use information effectively, involve all related parties, and make IRM an important focus for the organization.
Categorize Resources
Assign all assets and data types to general categories specific to the organization. These categories create a taxonomy that allows different parts of the organization to adopt a common understanding of their systems and to identify potential redundancies for elimination. The common terminology also reduces confusion and makes it easier to communicate consistently internally and to the board of directors.
Centralize Management
Consolidate authority, data flows, repositories, and systems management. This process eliminates redundancies that exist across silos, prevents inconsistent management for security or compliance, and lowers the attack surface for valuable resources. In many cases, consolidation can save money by reducing redundant storage, tests, or reports.
Embrace Standardization
Standardize event response processes, monitoring criteria, testing, and reporting to enable automation, accelerate decisions, and reduce response times for the majority of issues. Standardization makes data objective, quantifiable, and comparable across the organization to improve analysis and enable uniform decisions. Time saved for mundane and repeatable tasks frees up time for strategic thinking and to handle the exceptions.
Formalize Connections
Formally identify dependencies, connections, and data flows between resources. Formally connecting relationships identifies redundancies, security gaps, and potential stakeholders (including vendors or customers). Tie risks to goals, key risk indicators, and business activities to improve understanding of the business for everyone.
Involve Stakeholders
Create a risk-aware culture and enterprise-wide accountability by involving all stakeholders, internal and external, in the development and ongoing revisions of the IRM. Use cross-functional teams to extract each person’s knowledge to create accurate system maps and comprehensive risk assessments. Without wide participation, the skewed results will be inaccurate, ineffective, and likely face resistance.
Certifications, Classes & Tools for Integrated Risk Management
Integrated risk management combines concepts of network security, governance, compliance, and enterprise risk management. To learn more, consider taking individual courses from online providers to understand basics and pursue more formal certification to master concepts or validate experience.
Online course providers include:
- Coursera: Offers over 100 classes related to risk management, frameworks, and compliance priced per course (price varies) or included in Coursera Plus ($59/month).
- edX: Provides courses on risk management; many offered for free, with certificates available for extra fees that range from $5 to $249 depending on the course.
- ServiceNow: Offers a vendor-specific credential course for ServiceNow customers in GRC IRM Fundamentals that trains on the Service Now suite of GRC applications.
- Udemy: Promotes over 10,000 free and paid courses ranging from $45 to $85 on risk management, ERM, risk management professional (RMP) certification, and more.
Certification opportunities include:
- Certified in Risk and Information Systems Control (CRISC): Validates governance, IT security, and risk assessment for pros with three years of experience (starts at $575).
- Governance, Risk, and Compliance Certification (CGRC): Requires two years of experience to be certified in various GRC and risk management domains (costs $599).
- Integrated Risk and Decision Professional (IRDP): Promises certification in topics such as quantitative and qualitative risk management; the certification is in Beta (costs $499 per year).
- Project Management Institute Risk Management Professional (PMI-RMP): Provides certification for project managers with two years of experience (starts at $520).
Bottom Line: Integrated Risk Management Drives Business Safely
All companies accept risk simply by doing business. However, IRM exposes hidden technical, operational, or enterprise risks, which can undermine success or wipe out an organization entirely if ignored. Embracing and deploying effective risk management formally recognizes risk and develops controls against downside risk to enable responsible growth. Adopt IRM to embed risk awareness throughout the organization and create a more secure and aligned culture.
For more of a focus on IT security, consider reading about network security architecture.








