Multi-cloud is a cloud computing strategy that enables businesses to run their applications and services across multiple private and public cloud platforms, so securing multi-cloud environments is a complicated task.
As flexibility and resilience are key goals of a multi-cloud strategy, multi-cloud security must also be adaptable, protecting data and applications across multiple cloud providers, accounts, different geographic availability zones, and even on-premises data centers. We’ll look at multi-cloud security and the best practices required for addressing the wide range of threats these environments can face.
Also see our guides to public, private and hybrid cloud security
Table of Contents
How Multi-Cloud Security Works
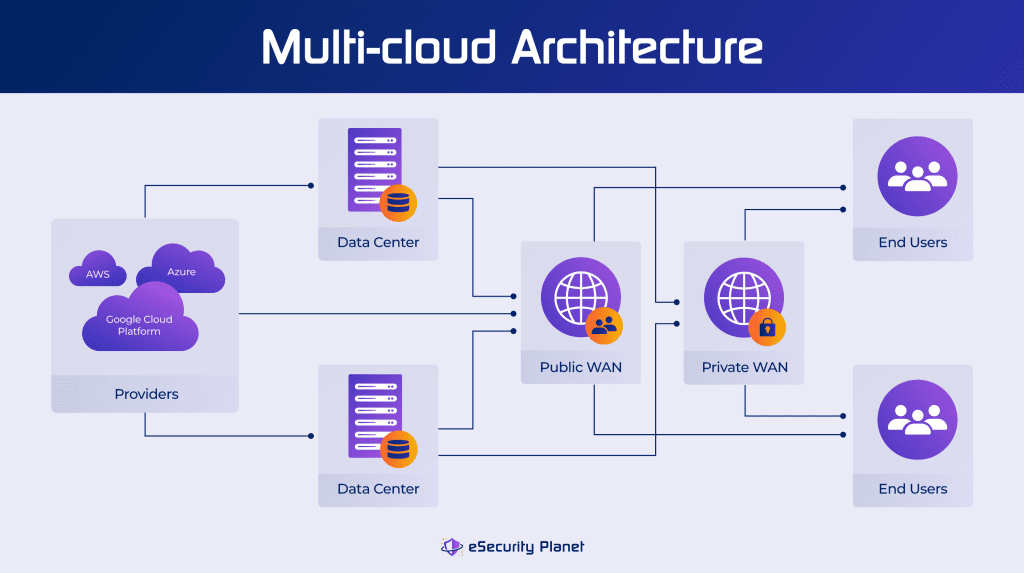
To facilitate an easier transition and ongoing management of a range of cloud resources, navigating the multi-cloud journey needs careful preparation and a well-defined stack. Consider establishing a Center of Excellence (CoE) within your business to take on tasks relating to multi-cloud management, ensuring alignment with the firm’s goals, and taking a customer-focused approach while prioritizing security.
Multi-cloud security is critical for protecting data across multiple public and private clouds, but how does it work? Here is a step-by-step approach for making multi-cloud security work.
Step 1: Defining Responsibilities
It is critical to understand who is accountable for what parts of security in a multi-cloud environment. Organizations are completely responsible for security while using a private cloud, including responsibilities like patching, IAM (Identity and Access Management) configuration, and network security. In contrast, public cloud services have a shared responsibility model, with cloud service providers generally responsible for securing the cloud infrastructure and customers responsible for securing data, applications and access. A clear understanding of responsibilities is essential for effective and efficient multi-cloud security.
Step 2: Integrating Security Early
Regardless of whether you are working in a private or public cloud environment, security should be an intrinsic element of the software development life cycle (SDLC) workflow. The “Shift Left Security” strategy promotes early security integration into your Continuous Integration/Continuous Deployment (CI/CD) process. You may examine container images for misconfigurations, malware, IAM risks, lateral movement concerns, and sensitive data exposure.
Step 3: Embracing Infrastructure as Code (IaC)
Cloud infrastructure configuration can be complicated, and human interventions may not be practical in the long term. Changes to infrastructure, such as application code, access management and network rules, should be logged in your code repository. This is referred to as Infrastructure as Code (IaC). IaC promotes consistency, repeatability, and speed of change, while also allowing version control. This method is especially critical for maintaining security in multi-cloud situations.
Step 4: Automation
Cloud technology is ever-evolving, with changes to regulations, applications, patches, and access control occurring on a regular basis. Automation simplifies processes like changing network policies, reacting to Common Vulnerabilities and Exposures (CVEs), and maintaining employee access permissions. It ensures that security measures are applied consistently and that they are quickly adjusted to meet changing requirements.
Step 5: Prioritizing Visibility and Monitoring
Monitoring keeps you up to date on the status of your security policies and infrastructure. It allows you to determine if your security policy is current and matched with growing risks. Monitoring also provides insight into access control, revealing which data is available from which cloud environments and which ports are open. This guarantees that your security solutions continue to be effective and responsive to emerging security issues.
CNAP platforms (CNAPP) have emerged as a comprehensive cloud security solution, combining cloud workload protection, cloud security posture management, Infrastructure as Code, entitlement management, and more. SIEM systems are another good comprehensive security tool for multi-cloud environments, combining on-premises security management with the ability to monitor cloud logs too.
Top Multi-Cloud Security Threats
Given the breadth of multi-cloud environments, enterprises face a number of issues, not the least of which is a much broader potential attack surface. Among the top multi-cloud security threats are:
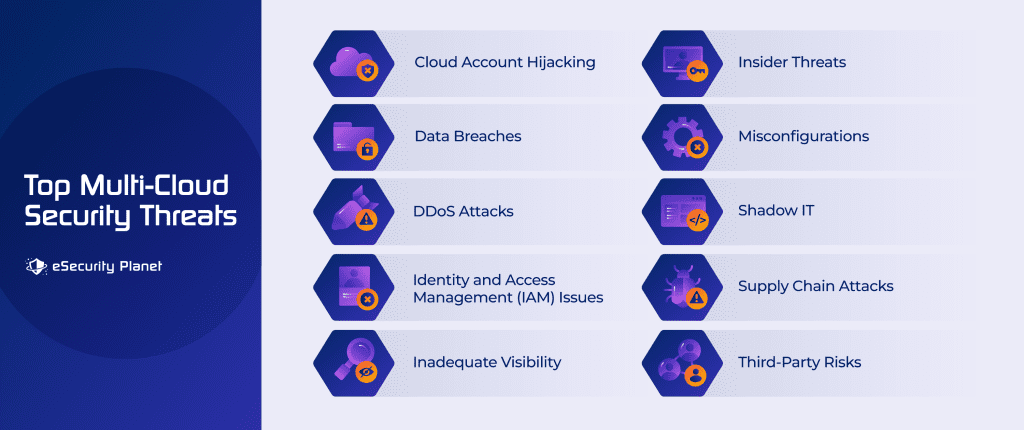
Cloud Account Hijacking
Cloud account hijacking happens when attackers obtain unauthorized access to cloud accounts. They can gain control by using stolen credentials or exploiting flaws. Once inside, they have the ability to steal data, modify resources, and engage in other nefarious operations.
Data Breaches
With data dispersed across multiple cloud environments, the risk of illegal access, data leaks, and breaches increases. Data exposure might occur due to insufficient access restrictions, misconfigurations, or inadequate authentication.
DDoS Attacks
DDoS attacks have the potential to interrupt and render cloud services inaccessible. Attackers overburden cloud resources with traffic, creating service failures. DDoS prevention and mitigation is critical for maintaining service availability.
Identity and Access Management (IAM) Issues
Mismanagement of IAM can lead to security breaches. Insecure and exposed accounts and excessive permissions granted to users or applications can result in unwanted access, data disclosure, and resource misuse. It is important to configure IAM policies correctly.
Inadequate Visibility
It takes effort to maintain complete awareness across many cloud platforms. Security teams may struggle to identify and respond to attacks in a timely way if they lack effective monitoring and visibility technologies.
Insider Threats
While external threats are frequently highlighted, individuals with malicious intent or those who unwittingly cause security flaws can also pose hazards. Internal access must be monitored and controlled.
Misconfigurations
Misconfiguration in cloud settings is a common security problem. Cloud services provide lots of setup choices, and errors might result in vulnerabilities. Inadequate access restrictions, exposed storage buckets and APIs, or incorrect network settings can all provide possibilities for attackers.
Shadow IT
Shadow IT is the use of unapproved programs or services by employees without the knowledge of IT. Unvetted technologies can create security flaws and data disclosure issues. Gaining insight into and control over shadow IT can be tricky, but cloud access security brokers (CASB) are a good option for cloud application control.
Supply Chain Attacks
Attackers may hack the software supply chain to inject malware or vulnerabilities into your cloud system, often through open source components that are part of other applications. If not discovered and handled, this can lead to widespread security vulnerabilities. DevOps and application vulnerability scanning tools can help detect these issues.
Third-Party Risks
In a multi-cloud environment, using third-party vendors or services could pose extra risks. These providers may have security flaws, and breaches in their systems might compromise your security. Third-party risk management (TPRM) tools can help manage these risks.
6 Benefits to Multi-Cloud Security
Multi-cloud environments offer important benefits if you can properly manage their security and complexity.
1. Avoiding Vendor Lock-In
- Multi-cloud offers the capability to move between cloud providers on demand, decreasing reliance on a single source.
- Allows development teams to create apps that can run across several clouds for greater flexibility.
2. Cost Optimization
- Multi-cloud can reduce capital expenditures on data centers by using cloud resources.
- Gives the option to choose the least expensive cloud providers for certain business requirements.
3. Reliability and Security
- DDoS assaults may be mitigated by dispersing workloads over several cloud environments.
- Increases reliability through smooth failover alternatives when one cloud fails.
4. Flexibility
- Allows enterprises to select the best cloud provider for each application, and to access extra resources to meet peak demand.
- Optimizes performance by tailoring infrastructure to business goals.
5. Disaster Recovery and Business Continuity
- Distributes data and applications across different clouds, allowing for more sophisticated disaster recovery planning.
- Ensures business continuity in the event of outages or disasters at cloud providers in certain areas.
6. Regulatory Compliance
- The ability to geographically shift and control workloads is an important ability for meeting data privacy regulations like GDPR.
- The ability to apply different levels of security to different applications and data is another multi-cloud benefit.
5 Common Challenges to Multi-Cloud Security
Shifting to a multi-cloud strategy offers substantial benefits but it also comes with some major challenges.
1. Complex Infrastructure
- Diverse Technologies: Multi-cloud setups frequently include many cloud providers, each with their own set of technologies, offerings, and settings. Managing these distinctions may be difficult and time-consuming.
- Non-uniformity: Due to a lack of standardization across cloud suppliers, instance sizes, services, and methodology may vary dramatically. This non-uniformity might make resource allocation and management more difficult.
Addressing the challenge: Utilize cloud management tools to simplify infrastructure management, speed deployment procedures, and enforce uniform security rules.
2. Multiple Skill Sets and Vendors to Manage
- Skill Requirements: Running multi-cloud setups requires a wide variety of technological skills. Each cloud platform may need specialized knowledge for proper management and optimization.
- Vendor Management: It might be difficult to coordinate and manage relationships with different cloud suppliers. Contract negotiations, billing, and guaranteeing service quality/SLAs among providers are all part of this.
Addressing the challenge: Encourage cross-training for IT teams, adopt cloud management platforms that provide vendor-agnostic solutions, and explore utilizing managed services from cloud providers to minimize the strain on in-house expertise.
3. Migration Complexity
- Data Transfer and Integration: Moving apps and data between cloud environments can be challenging. Data transported across different data formats, storage systems, and programs may require significant changes to run effectively across platforms.
- Mismanagement Risk: If migration is not correctly done, it can result in cost overruns and data loss. It might be difficult to ensure that the transition matches budget and performance requirements.
Addressing the challenge: Create a well-defined migration strategy, prepare a comprehensive plan, and leverage migration tools and processes supplied by cloud providers or third-party suppliers.
4. Interoperability Issues
- Integration Difficulties: Due to variations in APIs, data formats, and compatibility, it can be challenging to integrate applications, services, and data across numerous cloud platforms. Creating and maintaining cross-platform solutions can be time-consuming.
- Dependency Management: Managing dependencies between applications and services hosted by multiple cloud providers demands careful planning. Changes or disruptions in the services of one provider might have an impact on linked services.
Addressing the challenge: Use open APIs and protocols, and cloud-native services that are cross-cloud compatible. To bridge gaps and ensure seamless data and process flow, use integration platforms.
5. Data Governance and Compliance
- Varying Regulatory Requirements: Different cloud service providers may operate in various areas and must comply with local data protection and privacy laws — and your own data may require geographical controls too.
- Data Security and Privacy: Maintaining data security and privacy in a multi-cloud environment requires the consistent application of rules and controls, which can be challenging to administer across several cloud platforms.
Addressing the challenge: To comply with legal standards, implement a uniform data governance architecture that covers all cloud providers, provide encryption and access restrictions, and frequently assess compliance adherence.
12 Best Practices for Securing Multi-Cloud Environments
Now that we’ve looked at some multi-cloud security issues and controls, here are some best practices to help you manage all those challenges.
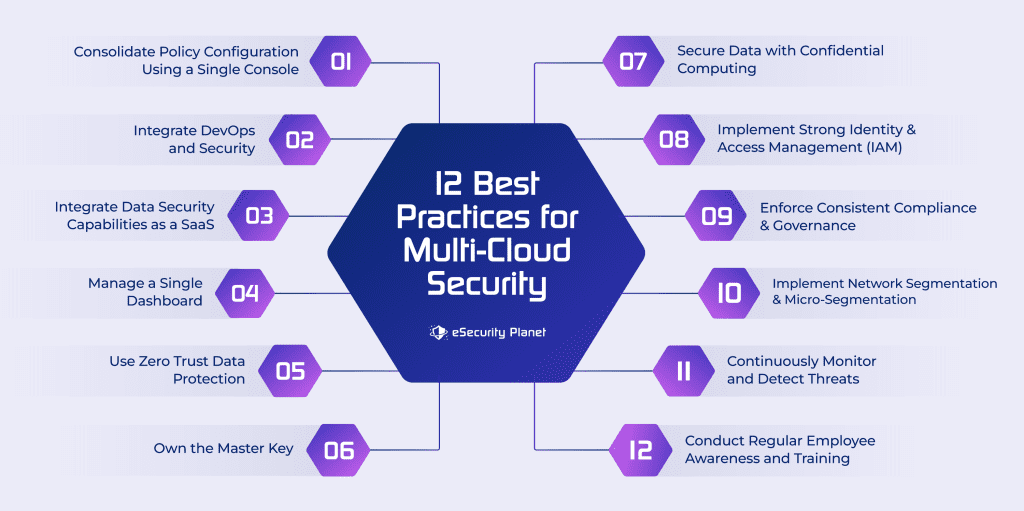
1. Consolidate Policy Configuration Using a Single Console
Centralizing policy configuration enables uniform security rules across many cloud platforms. Using a single interface reduces the risk of misconfigurations and security vulnerabilities by simplifying the management of access restrictions, firewall rules, and compliance settings.
2. Integrate DevOps and Security
Integrate security procedures into the DevOps pipeline to guarantee that security is a component of the software development life cycle (SDLC). As part of the continuous integration/continuous deployment (CI/CD) process, automate security testing, code scanning, and vulnerability assessment processes.
3. Integrate Data Security Capabilities with SaaS
To protect data across several cloud platforms, use Security as a Service (SaaS) solutions. SaaS services can provide consistent and accessible encryption, data loss prevention (DLP), and access restrictions. Firewalls-as-a-Service (FWaaS) are one possible option for applying security policies evenly from a single interface.
4. Manage a Single Dashboard
Employ a unified dashboard or security management platform that provides visibility and control over all of your multi-cloud setups. Monitoring, alerting, and administration are simplified, allowing for real-time security incident response. A cloud-based SIEM or SOAR solution could help.
5. Use Zero Trust Data Protection
To reduce excess privileges, use a zero trust security approach. Access to resources and data is controlled to authorized users and devices with this method. The danger of illegal access is reduced by enforcing continuous verification and stringent access controls.
6. Own the Master Key
Take command of encryption keys to safeguard your data. You may protect the confidentiality of your data even in a multi-cloud scenario by holding the master encryption keys. Avoiding vendor-controlled keys adds another degree of protection.
7. Secure Data with Confidential Computing
Implement secure computing technology to safeguard sensitive data while processing. This protects data from even the cloud provider or administrators. Confidential computing environments provide safe enclaves in which data is encrypted and kept private.
8. Implement Strong Identity and Access Management (IAM)
Set up strong IAM processes to manage access to resources, services, and data. To prevent unauthorized access, ensure that users have the right permissions and evaluate and audit user privileges on a regular basis.
9. Enforce Consistent Compliance and Governance
Create and implement standard compliance and governance policies across all cloud platforms. Monitor and audit settings, access restrictions, and data handling processes on a regular basis to ensure compliance with legal requirements and industry standards.
10. Implement Network Segmentation and Microsegmentation
To segregate workloads and applications, use network segmentation and microsegmentation solutions. This improves security by restricting lateral movement and creating a secure environment for your most important applications and data.
11. Continuously Monitor and Detect Threats
Monitor multi-cloud settings for unusual behavior and potential threats on a continuous basis. To discover and respond to security problems in real time, use threat detection technologies and machine learning algorithms.
12. Conduct Regular Employee Awareness and Training
Invest in cybersecurity training and awareness campaigns for your employees. Employees that are well-informed are better positioned to recognize and manage security issues in a multi-cloud environment.
Also read: Cloud Security Best Practices & Tips
Top 3 Multi-Cloud Security Solutions
These multi-cloud vendor solutions provide a variety of benefits, ranging from solid security measures to increased scalability and performance, while adapting to the different demands of enterprises in cloud computing.
Microsoft Defender for Cloud
Best for unified multi-cloud security management.
Microsoft Defender for Cloud offers comprehensive multi-cloud security solutions that assist companies in identifying and mitigating security risks while improving their security posture across Azure, Google Cloud, Amazon Web Services, and hybrid environments. It provides real-time access to security, risk prioritization, and consolidated information.
Key Features:
- AI and automation for threat detection and response
- Real-time security access and risk prioritization and classification
- Extended detection and response (XDR) integration across multi-cloud workloads
- Consolidated insights for multi-pipeline and multi-cloud DevOps
- Offers built-in policies and prioritized recommendations for multi-cloud compliance
Pros:
- Supports modernizing existing infrastructures.
- Provides visibility into multi-cloud environments.
- Offers DevOps insights for improved application security.
- Provides comprehensive workload security for virtual machines, containers, databases, storage, and other resources.
- Integrates seamlessly with other Microsoft services and products, making it advantageous to users of a Microsoft ecosystem.

Google Cloud Platform
Best for standard compliance and security automation.
Google Cloud Platform (GCP) is a cloud-based service that allows you to create, deploy, and manage applications across various clouds. It offers solutions such as the Security Foundation, Risk and Compliance as Code, Web App and API Protection, as well as a security and resilience architecture.
Key Features:
- Risk and compliance as code
- Threat identification with an advanced rules engine
- Security and resilience framework
- Web App and API Protection
- Autonomic Security Operations
Pros:
- Easily adapts to changing workloads.
- An analytic engine is included for viewing and analyzing security occurrences.
- Assists in the automation of security enforcement across the supply chain.
- The RCaC system is included for quick noncompliance issue identification.
- Provides cost-cutting tools and warnings.
- BigQuery is used for data analysis, while AI/ML technologies like TensorFlow are used to build and deploy machine learning models.
- Global network infrastructure enables low-latency, high-performance access to cloud resources worldwide.

Cloudflare
Best for integration-based multi-cloud security solutions.
Cloudflare offers various products for data protection across different platforms, providing unified control and seamless integration with other cloud service providers like IBM, GCP, AWS, and Azure.
Key Features:
- Unified control plane for consistent security policy enforcement
- Integration with major cloud providers
- Massive global network scale
- Distributed denial of service mitigation, web application firewalls, and content delivery networks
Pros:
- Speeds up online content and application delivery while protecting them from DDoS attacks.
- Protects against web application attacks and harmful bots by providing a Web Application Firewall (WAF) and bot mitigation capabilities.
- Uses its own edge computing technology, Workers, to enable enterprises to run serverless operations at the network edge.
- Offers a free version and various pricing plans.
- Provides 24/7 enterprise support.
Also consider Secure Access Service Edge solutions for their broad security capabilities.
Bottom Line: Get Started with Multi-Cloud Security
Businesses can adopt a multi-cloud security strategy to optimize resources, meet changing business demands, and assure long-term success in a dynamic environment while protecting critical assets. Integrating multi-cloud security can be difficult, posing a challenge to wider adoption. To overcome these challenges, enterprises should adopt a cloud-first strategy and carefully pick a multi-cloud security solution provider. You can maximize the benefits of this approach by making an informed decision that keeps your multi-cloud environment safe, protected, and compatible with regulations and standards for cloud security and governance.
Read next:









