Confidential computing is a technology and technique that encrypts and stores an organization’s most sensitive data in a secure portion of a computer’s processor — known as the Trusted Execution Environment (TEE) — while it’s processed and in use.
It’s a fast-growing cloud computing technique that has gotten buy-in and support from a variety of hardware, software, and cloud vendors. Read on to learn more about confidential computing, how it works, and how it benefits enterprise data security efforts.
Table of Contents
How Does Confidential Computing Work?
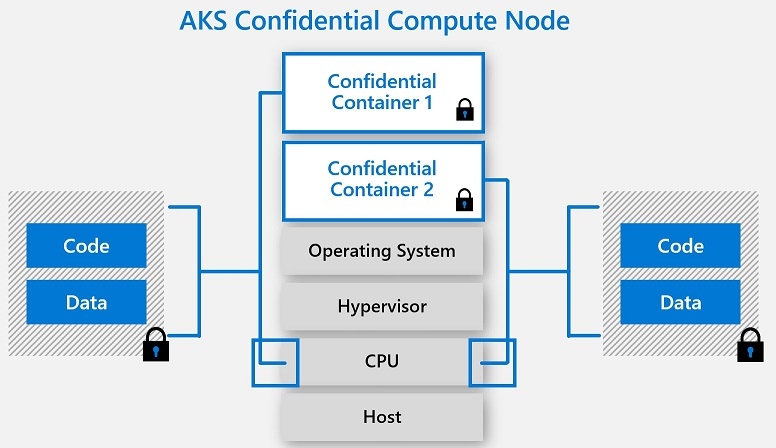
Confidential computing is all about using technology to create an isolated safe space, otherwise known as a Trusted Execution Environment (TEE), for the most sensitive data and data processing instructions. During confidential computing, the TEE and a preselected dataset are separated from the rest of the computing environment, including the operating system, the hypervisor, uninvolved applications, and even cloud service providers.
Unlike other types of data processing, in confidential computing data does not need to be decrypted in memory and exposed to external security vulnerabilities in order to be processed. Instead, it is only decrypted in the Trusted Execution Environment, which relies on hardware-based coprocessor security, embedded encryption keys, and embedded attestation mechanisms to ensure that only authorized applications, users, and programming code can access the TEE and the data it houses. Data processed inside a Trusted Execution Environment is completely invisible to all computing elements that aren’t part of the designated TEE, and data always stays encrypted while in transit or stored outside the TEE.
Also read: Encryption: How It Works, Types, and the Quantum Future
7 Benefits of Using Confidential Computing
Confidential computing offers a number of benefits for safer handling of sensitive data while in use.
1. Added security in shared, untrusted, or unfamiliar environments
The modern computing landscape, especially when the cloud’s involved, means your data is often stored in environments that are exposed to third parties, different departments, and public users. There’s limited native protection built into cloud environments, especially for your most sensitive data when it’s in use. Confidential computing techniques and technologies give your sensitive data more safeguards, regardless of the computing environment.
2. Secure data input and output
The only time data is decrypted during the confidential computing process is when the TEE has taken multiple steps to ensure that only authorized programming code is entering the environment. At all other times, sensitive data remains encrypted, adding more privacy and security while data is in transit or stored in another part of the computing environment.
3. Equal focus on security and cloud computing capabilities
Traditionally, businesses have either had to process sensitive data in memory with major security risks or limit their sensitive data processing in order to protect it; neither approach is ideal for optimal data usability and outcomes. Confidential computing makes it so users can take advantage of the power and complexity of a cloud computing environment while still protecting their sensitive data to the utmost degree.
4. Remote quality assurance capabilities
Confidential computing architecture is designed for remote quality assurance and security management. Remote verification and attestation make it easier for security admins to manage a distributed network while still protecting and monitoring the Trusted Execution Environment.
5. Easier detection and prevention of unauthorized access
Built-in attestation enables the confidential computing architecture to verify programming codes before they can enter the TEE; confidential computing technology can also completely shut down the computing process if an unauthorized set of code attempts to tamper with or gain access to the TEE. This type of computing provides an ideal combination of hands-off security protocols and visibility into unauthorized network traffic.
6. Compatibility with data privacy and compliance requirements
Compliance laws like GDPR and HIPAA require companies to store and use data in specific ways to maintain compliance. It’s not always easy to adhere to these standards in a public cloud environment, but with the additional security features confidential computing provides for sensitive data, businesses can more easily comply with a variety of data privacy and security regulations while still making the most of their data.
7. Protection for data in use
Although other techniques are emerging and being used today, confidential computing is one of the few encryption strategies that effectively protects data in use. Most other encryption approaches protect data at rest and data in transit only.
Also read: Exfiltration Can Be Stopped With Data-in-Use Encryption
Confidential Computing Use Cases
Confidential computing’s protections make it ideal for a number of sensitive data use cases.
Secure third-party outsourcing
Outsourcing certain business functions to third parties is common these days, but it can be a risky move if your data isn’t entirely secure. The enclaved approach taken with TEEs makes it so your internal team can protect and essentially hide sensitive data from unauthorized third-party users, allowing them to focus solely on the parts of your computing process they need to access while trusted members of your team manage sensitive data processes.
Encryption to mitigate insider threats
Because confidential computing means sensitive data is encrypted at all times (until it is processed in the TEE), even members of your internal team cannot access and interpret this protected data without authorization. This feature of confidential computing protects against rogue users within the network as well as users who fall victim to credential phishing attacks.
Protected public cloud use
Businesses are moving many of their workflows and operations to the cloud, but some of the largest enterprises are still hesitant to move their most sensitive workloads to a public cloud environment. With confidential computing in the mix, enterprises can feel more confident and maintain more control over their sensitive data at rest, in transit, and in use, even in a public cloud environment with third-party vendors and users that follow varying security protocols.
See the Best Third-Party Risk Management Software & Tools
IoT data processing
Internet of Things (IoT) devices generate massive amounts of data that are rarely stored in a secure fashion. Confidential computing is increasingly being used to create enclaves where IoT data can be processed in a confidential way that ensures the data isn’t tampered with.
Collaborative data analytics and data usage
Analyzing broader patterns across an organization or an entire industry often requires users to access sensitive data outside of their normal scope of work. Offering an alternative and more secure approach, confidential computing supports secure and collaborative data analytics, allowing users to manage and view their own inputs and gain insights into a sprawling dataset without seeing other users’ inputs or outputs. This approach to analytics is especially helpful in industries like insurance and healthcare where analyzing and interpreting broad patterns can inform insurance rates and diagnostics, respectively.
Blockchain and crypto security
The encryption involved in confidential computing is especially useful in a blockchain environment. Common confidential computing use cases include smart contract, private key, and cryptographic operations management.
Machine learning training
For organizations that want to work with or train a machine learning model without exposing their training dataset, confidential computing is a viable solution for privacy. The machine learning model can be placed in a TEE enclave, allowing data owners and users to share their data with the model and train it in an invisible, isolated environment.
Confidential Computing Consortium (CCC)
The Confidential Computing Consortium (CCC) is a Linux Foundation project community that is made up of various tech leaders. The CCC works to advance confidential computing capabilities and adoption through collaboration on high-profile and open-source confidential computing projects. Its current projects include Enarx, Gramine, Keystone, Occlum, Open Enclave SDK, Veracruz, and Veraison.
The organization is led by two governing officers, a board of directors, committee chairs, and various staff. Members of the Confidential Computing Consortium include Intel, Meta, Microsoft, Google, Accenture, Huawei, Red Hat, Accenture, Anjuna, AMD, Canonical, Cisco, Fortanix, Nvidia, Ruby, and VMware.
Confidential Computing vs. Homomorphic & Data-in-Use Encryption
Confidential computing, fully homomorphic encryption (FHE), and data-in-use encryption share many similarities, especially since they all focus on securing data in use, but each creates a slightly different encryption and usage scenario.
Data-in-use encryption could be looked at as one component of confidential computing; it is used to keep data encrypted until it is in an isolated TEE, where it can then be decrypted by authorized keys and code. Confidential computing also takes this approach to encryption and isolated data processing, but it’s a much broader concept that includes other technologies and strategies, like other types of encryption, secure execution environments and storage, secure communication protocols, and secure key management features.
Fully homomorphic encryption is an old idea that has only recently advanced enough to realize its promise. This approach to data security encrypts data throughout its entire lifecycle, even when it’s being used in computations. Data inputs are encrypted during processing and computing, and results come out encrypted as well. In contrast, both confidential computing and data-in-use encryption allow data to be decrypted and viewed when it’s in the Trusted Execution Environment.
In theory, FHE has some major security benefits since data is encrypted throughout the computing process. However, this type of encryption requires large amounts of overhead, is complex to manage, and has potential for users to make changes to encrypted data without other users ever knowing, thus damaging data integrity. FHE is still early in its development and may overcome some of these shortcomings over time.
Also read: Homomorphic Encryption Makes Real-World Gains, Pushed by Google, IBM, Microsoft
Top 3 Confidential Computing Companies
Confidential computing is a complex process that requires advanced software, hardware, and cloud computing technologies. As such, there are many confidential computing companies and leaders that focus on different parts of the confidential computing architecture. We’ve taken a closer look at three of these leaders below. Other leading confidential computing companies include IBM, Google (Alphabet), AWS, and Fortanix, and promising startups like Anjuna Security, Opaque Systems, Inpher, Gradient Flow, HUB Security, Edgeless Systems, Profian, Secretarium, and Decentriq.

Intel
Intel is one of the first and foremost players in the confidential computing space. Intel Software Guard Extensions (SGX) is the most commonly used hardware-based enclave solution for confidential computing. The company also manages Project Amber, a zero-trust confidential computing project, and Intel Trust Domain Extensions (TDX), a VM-focused approach for added privacy and control. Ron Perez, an Intel fellow and chief security architect at Intel, is the Confidential Computing Consortium’s governing board vice-chair.

Fortanix
Fortanix is considered one of the earliest pioneers in confidential computing. Fortanix’s Confidential Computing Manager (CCM) is a SaaS solution that helps users manage TEEs and protect data in use across various cloud environments. Fortanix is also a founding member of the Confidential Computing Consortium.
Microsoft
Microsoft offers a range of confidential computing solutions primarily through the Azure cloud environment. The Azure confidential computing initiative includes various products and services, such as confidential VMs and confidential VMs with application enclaves, confidential containers, trusted launch, a confidential ledger, SQL Azure Always Encrypted, Microsoft Azure Attestation, and Azure Key Vault M-HSM. Stephen Walli, a principal program manager for Microsoft Azure, is the governing board chair for the Confidential Computing Consortium.
See the Top Enterprise Encryption Products
Bottom Line: Confidential Computing
The modern enterprise network isn’t just an on-premises environment or simple data center. It consists of third-party partners and applications, public and hybrid clouds, and other external factors that feel somewhat beyond the control of traditional network security solutions. Processing data in those environments is more perilous than ever. For companies that want to increase their security and control at the data level, regardless of what their network looks like or who is using it, confidential computing offers a solution to maintain data security while upholding data integrity and enabling high-performance data tasks.
Read next: Security Considerations for Data Lakes








