Website and application developers need vulnerability scanning tools to test compiled and uncompiled code for known vulnerabilities.
Most vulnerability scanning tools will detect common vulnerabilities, but may be limited in the types of scans performed, the programming languages they support, and integrations with other developer and operations (DevOps) tools.
Most DevOps teams will make purchasing decisions for vulnerability scanners based upon deployment flexibility, scanning speed, scanning accuracy, connections to other tools, and, of course, price. The recommendations in this article focus primarily on specialty web application scanning tools and does not list the web application scanning modules of integrated enterprise vulnerability scanners developed by Rapid7, Qualys, etc.
After reviewing the specific tools, this article will also define characteristics and list Best Application Vulnerability Scanning Tool Criteria used to select the recommended tools.
- Acunetix Vulnerability Scanner (Invicti): Recommended for WordPress Sites
- AppScan (HCLTech): Best for Many Programming Languages
- Burp Suite Enterprise Edition (Portswigger) – Best for Out-of-Band Application Security Testing
- Detectify – Best for Crowd-Sourced External Attack Surface Management
- Invicti (Formerly Netsparker): Best Overall Application Vulnerability Scanner
- StackHawk: Best SMB Option
- ZAP (OWASP Zed Attack Proxy): Best for Budget-Minded Experts
- Best Application Vulnerability Scanning Tool Criteria
- Bottom Line: Application Scanning Tools
| DAST – Dynamic Application Security Testing | IAST – Interactive Application Security Testing | Fuzzing | SAST – Static Application Security Testing | SCA – Software Composition Analysis | |
|---|---|---|---|---|---|
| Acunetix | Yes | Option | |||
| AppScan | Yes* | Yes* | Yes* | Yes* | |
| Burp Suite | Yes | ||||
| Detectify | Yes | Yes | |||
| Invicti | Yes | Yes | Yes | ||
| StackHawk | Yes | ||||
| ZAP | Yes |
Acunetix Vulnerability Scanner (Invicti): Recommended for WordPress Sites
Invicti’s Acunetix tool provides enhanced DAST vulnerability detection with options for IAST and network security scanning. Acunetix focuses on speed and accuracy, but is not designed to scale in the same manner as the enterprise-designed Invicti tool (see below). Heavy WordPress developers with many pages often select Acunetix because of the concurrent crawling and scanning features that work well with large WordPress sites.
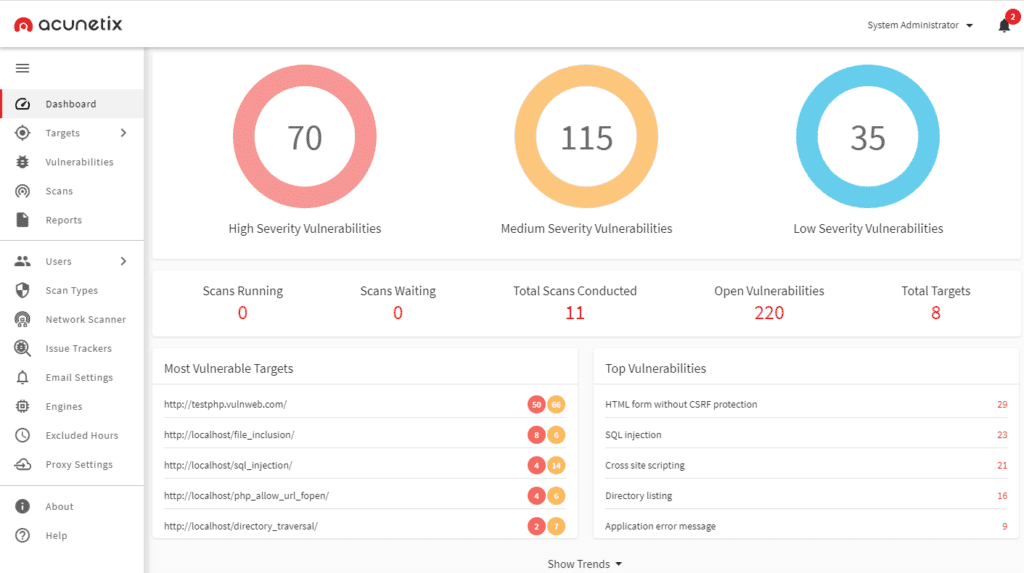
Key Features
- Deploys locally on Linux, macOS, and Microsoft Windows or on the cloud
- Optional IAST scanning for PHP, Java, or .NET code
- Integrated OpenVAS to perform network security scanning of IP address ranges to detect open ports and other network-specific vulnerabilities
- Ranks vulnerabilities as high confidence (100% verified), medium confidence (likely there, cannot be verified automatically), and low confidence (suspected possibility, requires penetration testing or source code examination)
- Scans complex paths and multi-level forms, password-protected areas, script-heavy sites (JavaScript or HTML5), single page applications (SPAs), unlinked pages
Pros
- Built for speed and efficiency
- Written in C++ for speed
- Coded to test code with reduced number of requests to reduce bandwidth and server load
- Concurrent crawling and scanning to deliver results quickly and efficiently
- Dynamically prioritizes scans to return up to 80% of the vulnerabilities in the first 20% of the scan
- Can detect changes to web applications and perform incremental scanning only on the changes to the code
- Actively reduces false positives and can verify vulnerabilities and provide proof of exploit
- Integrates with pipeline tools and issue trackers such as Jenkins, Jira, and GitHub for developer workflow integration
Cons
- Not as accurate as Invicti’s flagship scanning tool in testing (see below)
- Vulnerability proof of concept is sometimes complex and hard to follow
- Customers complain about the target app licensing model
Pricing
Invicti does not publish prices for Acunetix on their website and encourages interested parties to fill in a form to request a quote or a demo. Acunetix is offered as an annual subscription based upon the number of websites or web applications scanned and length of the contract. Invicti offers three versions:
- Standard: single user, on-premises
- Premium: standard version + continuous scanning, role-based access controls, compliance reports, network vulnerability scanning, issue tracker integration, multiple users, multiple scan engines, hosted or on-premises
- Acunetix 360: Premium without network vulnerability scanning, but with customizable workflows, single-sign-on, and hybrid environment installation options
AppScan (HCLTech): Best for Many Programming Languages
In 2018, IBM sold iconic software brands, including AppScan, to HCLTech of India. HCLTech continues to develop the AppScan software, which now offers five different versions: AppScan CodeSweep (free), AppScan Standard (DAST), AppScan Source (SAST), AppScan Enterprise (SAST, DAST, IAST, and risk management), and AppScan on Cloud (SAST, DAST, IAST, and SCA).
Key Features
- Supports a huge range of programming languages from standard JavaScript and Python, to more niche languages such as Dart and Cobol
- Highlights vulnerabilities and can educate programmers on mitigation strategies
- Can review uncompiled code, GitHub pulls, web apps, web services, and mobile back-ends
- Can track and identify vulnerabilities in open source supply chain code
- Can compare against compliance benchmarks from PCI DSS, OWASP top 10 and more
- Scalable and automatable security testing
- Scans and analyzes API
- Monitors active code for runtime issues without scan requests
Pros
- Offers a variety of tools to suit developing needs
- Can handle complex use cases and application flows
- Can integrate with DevOps Continuous Integration/Continuous Delivery (CI/CD) pipelines
Cons
- Some default DAST scans can take too long or error out
- Can suffer false positives from strict definitions
- Plugins can affect score results
- Customers note that some licenses can be quite expensive
Pricing
HCLTech does not list prices for the AppScan products on their website, but does disclose that customers can obtain node-locked licenses (single license, single machine) or floating licenses. Customers can contact HCLTech for a quote or go through partners. Licenses are for 12 months of subscription and support.
Burp Suite Enterprise Edition (Portswigger) – Best for Out-of-Band Application Security Testing
Portswigger’s popular Burp Suite can be licensed in four ways. The Burp Suite Community Edition and Dastardly web application scanners provide free, but feature-limited tools to help developers get started. Burp Suite Professional provides manual penetration testing capabilities and the Burp Suite Enterprise Edition provides automated dynamic web vulnerability scanning.
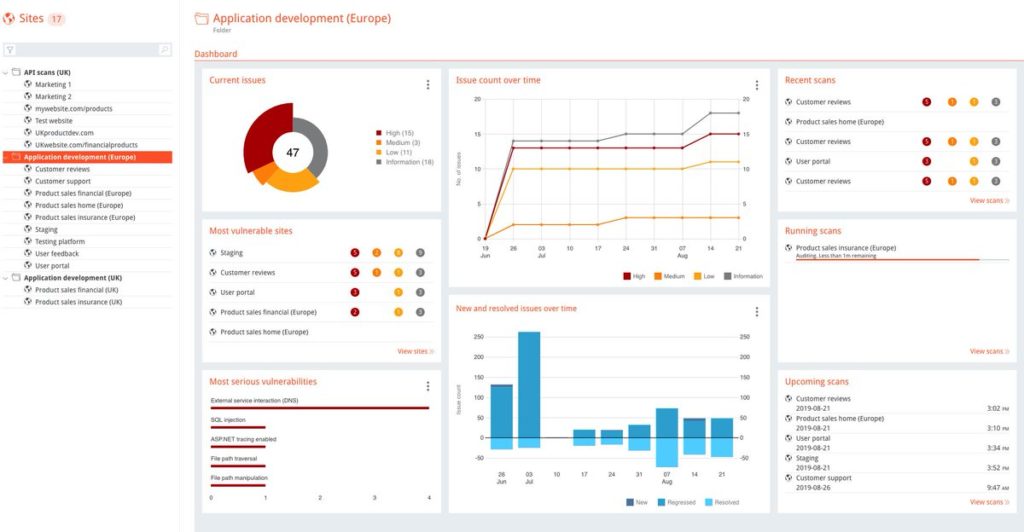
Key Features
- Pioneered Out-of-band application security testing (OAST) to use external servers to find bugs difficult to detect with DAST such as blind and asynchronous bugs. OAST also reduces the false positives of SAST
- API security testing
- Easy setup and scanning
- Integrates with all major CI/CD platforms and bug tracking systems
- Role-based, multi-user access control
- Multiple deployment options
- Aggregated issue reporting, intuitive dashboards, graphs, and reports
- Compliance-specific reports available
- Uses embedded chromium browser for scanning
Pros
- Easy scheduling for recurring scanning
- Scalable scanning
- Custom and out-of-box configurations
- Deploys as a standard software or in Kubernetes using a Helm chart
Cons
- Some customers complain of complex and time consuming configurations
- Some false positives and false negative results have been reported
Pricing
For the Enterprise edition of Burp, Portswigger does not have any limit to the number of users or distinct applications that can be scanned. The solution is licensed based on the number of concurrent scans to be performed:
- Starter plan: 5 concurrent scans = $8,395/year
- Grow plan: 20 concurrent scans = $17,380/year
- Accelerate plan: for 50+ concurrent scans, starts at $35,350/year
For more on the Burp Suite, see Getting Started with the Burp Suite: A Pentesting Tutorial
Detectify – Best for Crowd-Sourced External Attack Surface Management
Detectify seeks to use crowd-sourced vulnerability research to power External Attack Surface Management (EASM) tools for asset discovery and vulnerability assessments. Currently, Detectify offers two solutions, Surface Monitoring and Web Application Scanning.
Surface Monitoring examines the internet-facing subdomains of an application to detect exposed files, vulnerabilities, and other non-coding misconfigurations. The Webapp scanning tests the code of custom-built apps for security vulnerabilities.
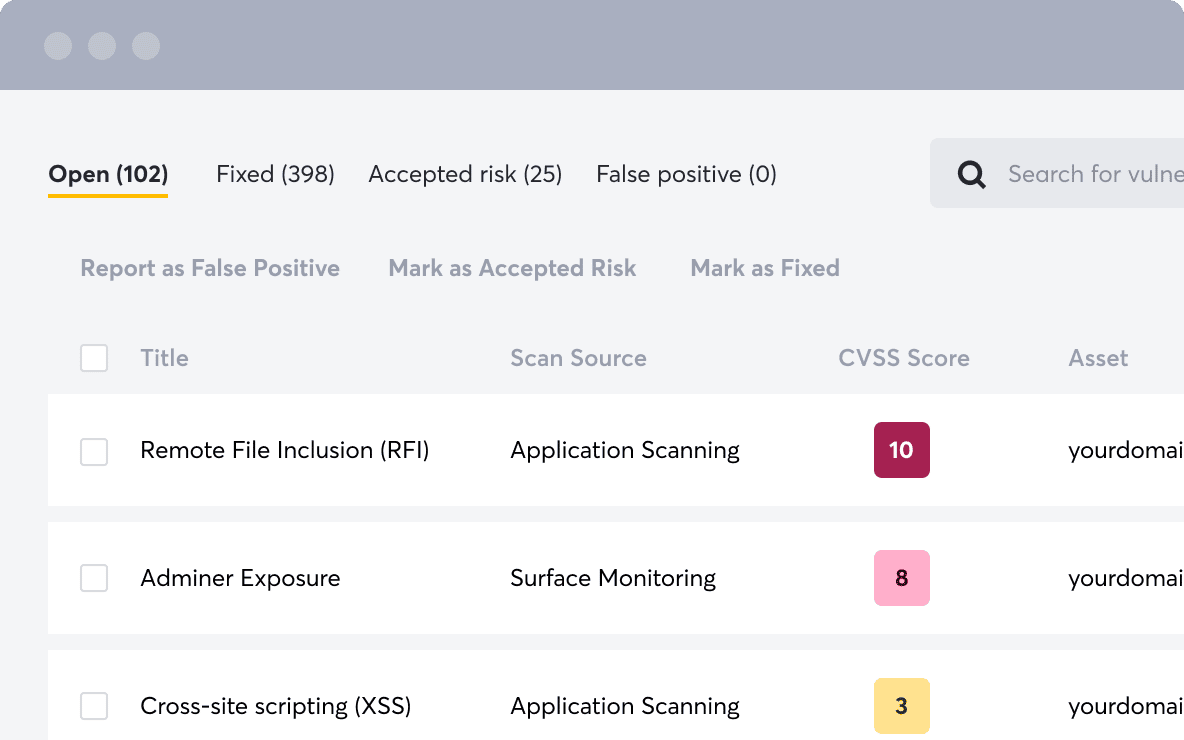
Key Features
- Continuous and automated discovery, inventory and monitoring of internet-facing assets
- Unique and optimized engine to crawl code
- Performs fuzzing testing
- Vulnerabilities can be filtered and tagged for remediation prioritization
- Flexible API to integrate with Slack, Jira, Splunk and other tools
Pros
- Will detect open ports, DNS record types, and hosted technologies on each asset
- Options to set custom policies
- Can protect against subdomain takeovers
- Will detect unintentional information disclosures
Cons
- System tracks vulnerabilities in history, but does not recognize or include recently fixed vulnerabilities in reports
- Marked false positives can continue to appear in subsequent reports
- Does not always note the likelihood a vulnerability is exploitable
Pricing
Detectify provides a 2-week free trial and licenses their software based upon the number of web applications, domains, and subdomains scanned. For smaller organizations, Detectify offers package deals that start at:
- $289/month surface monitoring for up to 25 subdomains, billed annually
- $89/month per scan profile, billed annually
Invicti (Formerly Netsparker): Best Overall Application Vulnerability Scanner
Invicti, formerly known as Netsparker, is an application vulnerability scanner designed for enterprise-scale and automation. Invicti intends this product to be the tool a company grows into after using the Acunetix product aimed at small businesses.
Key Features
- Automatic and continuous scans to update website, application and API inventories
- Avoids scanning queues by allowing multiple concurrent scans and scanners that feed into a centralized repository for reporting
- Deploys on-premise, in the cloud, within Docker images, or as a hybrid solution. Cloud agents launch for scans then self-delete when the scan is completed.
- Dynamic and automatable DAST, IAST, and SCA scanning
- Out-of-band testing and asynchronous vulnerability testing
- IAST sensors can often provide file name and programming line number for vulnerabilities
- Crawls pages authenticated by form submission, OAuth2, NTLM/Kerberos and more
- Scans complex paths and multi-level forms, password-protected areas, script-heavy sites (JavaScript or HTML5), single page applications (SPAs), unlinked pages
Pros
- Scans hidden files
- Detects misconfigured configuration files
- Industry leading detection and false positive rates from independent tests
- Will track security posture for applications over time and identify vulnerability trends
- Actively reduces false positives and can verify vulnerabilities and provide proof of exploit
- Integrates with pipeline tools and issue trackers such as Jenkins, Jira, and GitHub for developer workflow integration
Cons
- Can have a steep learning curve
- Customers complain about ineffective multi-factor authentication testing
- Users notice slowness in the scans on larger web applications
- Only available with a Windows software installation
Pricing
Invicti publishes neither pricing information nor licensing levels on their website. Invicti offers three plans:
- Standard on-premises desktop scanner
- Team scanner (hosted) adds additional features over desktop scanner:
- Multi-user platform
- Built-in workflow tool
- PCI Compliance scanner
- Asset Discovery
- Enterprise (hosted or on-premises) adds custom workflow and dedicated tech support
StackHawk: Best SMB Option
Founded by DevOps engineers for DevOps engineers who write and push out code every day, StackHawk seeks to simplify the process of building secure software. Their DAST scanner integrates with CI/CD Automation and Slack to help triage findings and enable rapid correction. With a free tier that allows scanning for one application, even resource constrained small- and medium-sized businesses (SMBs) can afford to implement security into their development.
Key Features
- CI/CD and Slack Integration
- REST, GraphQL and SOAP support
- Custom scan discovery and historical scan data
- cURL-based reproduction criteria
Pros
- Unlimited scans for one application
- Unlimited scans and environments
- Docker-based application security scanner
- Continues to add features to the free tool (gRPC support in development)
Cons
- Requires use and knowledge of Docker infrastructure
- Only provides email based support for the free version
- Requires a paid license for more than one application
Pricing
Stack Hawk offers three levels of licensing. Paid versions are based on a price of per developer per month and can be billed monthly. Annual billing results in a discount for the paid tiers.
- Free Tier: Only one application
- $49/developer per month Pro Tier
- Minimum 5 developers, volume discounts available
- Unlimited application scanning
- Free Tier features plus: Applications dashboard, Snyk integration, GitHub CodeQl and Repo integration, Custom Test Data for REST, HawkScan ReScan, and custom Test Data for GraphQL
- Support via email and Slack
- $69/developer per month Enterprise Tier
- Volume discounting available
- Pro Tier features plus many other features including: Single Sign-on, MS Teams, Webhooks integration, role-based permissions, executive summary reports, API access for scan results, policy management
- Support via email, slack (dedicated support), and an option for Premier Zoom support
ZAP (OWASP Zed Attack Proxy): Best for Budget-Minded Experts
The Open Web Application Security Project (OWASP) foundation and an open-source community created the Zed Attack Proxy, or ZAP as a free web app scan tool. ZAP is supported by dedicated open source volunteer programmers and additional capabilities can be obtained through the ZAP marketplace.
Key Features
- Available for major operating systems and Docker
- Docker packaged scans available for quick starts
- Automation framework available
- Comprehensive API available
- Manual and automated exploration available
Pros
- Free tool
- Huge support community
- ZAP is commonly used by penetration testers, so using ZAP provides an excellent idea of what vulnerabilities casual attackers might locate
Cons
- Open source community support is not as responsive or directly helpful as paid support
- Requires more expertise to use
Pricing
ZAP is a free, open source tool.
Best Application Vulnerability Scanning Tool Criteria
There are many website and application vulnerability scanning tools and most will detect common critical vulnerabilities listed in the OWASP top 10 such as SQL Injections (SQLi) or Cross-site Scripting (XSS). There will also be heavy overlap of capabilities with Top Application Security Vendors as both types of tools examine the code using similar techniques:
- Dynamic Application Security Testing (DAST) that scans running code
- Static Application Security Testing (SAST) that scans code at rest
- Interactive Application Security Testing (IAST) that operates inside of running code and monitors for performance and issues
- Software Composition Analysis (SCA) tools analyze open source components
- Fuzzing tools intentionally use unexpected characters, special characters, incorrect formats and other data input variations to test the resilience of the software to bad inputs
To create this list, we surveyed a broad array of websites, vendor materials, and customer reviews to create a pool of qualified candidates based upon capabilities and reputation. We then filtered the list specifically for vendors that specialized in website and application security.
We intentionally excluded most Open Source tools (other than ZAP) because of their limited features, integrations, and support. We also excluded the application-scanning modules or features of enterprise-grade tools such as those from Qualys or Tenable.
Bottom Line: Application Scanning Tools
The rise in importance and functionality of websites and applications draws the attention of attackers seeking to exploit any opportunity. Organizations of all sizes need to incorporate vulnerability scanning tools to locate the most common vulnerabilities before anyone else can.
To ensure efficient elimination of vulnerabilities, organizations should seek a tool that enables ticketing or tracking for detected vulnerabilities. Some tools will send alerts (email, Slack, etc.) and others will integrate directly with DevOps tools. For best adoption, the security and development teams need to work together to select an appropriate and effective tool.
For more information on Vulnerability Scanning Options see:
- What is Vulnerability Scanning & How Does It Work?
- Best Vulnerability Scanner Tools
- 12 Top Vulnerability Management Tools for 2023
- 10 Best Open-Source Vulnerability Scanners for 2023
- Penetration Testing vs. Vulnerability Testing: An Important Difference
- Application Security: Complete Definition, Types & Solutions








