The largest businesses, government agencies, non-profit corporations, universities, and other similar sized organizations qualify as enterprises. These complex multi-location entities often deploy local networks, virtual computing environments, cloud infrastructure, and a variety of devices that classify into the internet of things (IoT) and operational technology (OT) categories. Some even deploy applications, web servers, and containers.
To examine this broad spectrum of assets and connections, these organizations need multi-faceted tools, or a vendor that can supply integrated tools that support complex workflows and larger teams for vulnerability management, remediation, and related tasks. Security teams choosing between tool options will frequently decide based upon the need for optional integrations for specific security tools or particular automation capabilities.
| Vulnerability Scanning Tools for Specific Asset Types | |||||
|---|---|---|---|---|---|
| Network / Endpoint | Cloud | Container | Virtual Machines | Apps | |
| Fortra | Tripwire IP360 | Tripwire IP360 | Tripwire IP360 | Tripwire IP360 | Multiple tools |
| Intruder | Intruder Pro | Intruder Pro | Intruder Pro | Intruder Pro | Intruder Pro |
| Rapid7 | Insight VM | Insight VM | Insight VM | Insight VM | Insight AppSec |
| Qualys | Qualys VMDR | Qualys CloudView | Qualys Container Security | Qualys VMDR | Qualys Web Application Scanning |
| Tenable | Tenable.io | Tenable.io | Tenable.io | Tenable.io | Tenable.io |
Fortra
Fortra offers several vulnerability detection and management solutions that integrate with their security and automation solutions. Tripwire IP360 provides a focused vulnerability detection tool for both on-premises and cloud networks, including all devices and their associated operating systems and applications.
The other Fortra tools include beSECURE (available as a hosted service, an appliance, or a hybrid solution) and the Frontline Vulnerability Manager, which is part of the Frontline Cloud SaaS vulnerability management solution. Tripwire IP360 offers the most flexibility and focused capabilities of the three solutions, but organizations should select the option most appropriate for their needs.
For application scanning, Fortra offers three solutions. The BeSource SAST tool performs static application security testing (SAST), the BeSTORM DAST solution performs dynamic application security testing and black box fuzzing, and the Frontline Web Application Scanning focuses on a range of vulnerability scanning for applications within websites.
Key Features
- Uses both agent and agentless scans
- Scan online, offline and non-running cloud and local containers
- Scans IT, IoT, and OT
- Proprietary Tripwire VERT vulnerability ranking score that builds off of CVSS scores, but also considers active attacks, difficulty of exploitation, and other factors
- Integration with Fortra security and automation tools
Pros
- Asset discovery and profile
- Scans on-premises, cloud, and containers
- Scalable architecture & application-specific reporting
- Scan reports stored in a database
- Attempts to minimize false positives and offers a ‘bounty’ for confirmed false positives
Cons
- Customers note that some scans can slow down performance
- Reporting can be inflexible and limited
- Port scans can take significant time to complete
Pricing
Fortra does not publish prices but provides a form to obtain a price quote for their tool and a managed service.
Intruder
Intruder is a cloud-based vulnerability scanner that performs over 10,000 security checks. Intruder uses an enterprise-grade scanning engine to run emerging threat scans for newly discovered vulnerabilities. Results are then emailed to IT and available on the dashboard.
Intruder can perform perimeter scanning, internal scanning, cloud resource scanning, and web application vulnerability scanning. Internal scanning uses an endpoint agent.
Key Features
- Scans publicly and privately accessible servers, cloud systems, websites, and endpoint devices
- Finds vulnerabilities such as misconfigurations, missing patches, encryption weaknesses, and application bugs in unauthenticated areas
- Automatically scans systems for new threats
- Automatic IP and DNS tracking
- Integrates OpenVAS external scanning and Tennable’s scanning tools under one integrated tool and license
Pros
- Easiest to Use in Vulnerability Scanner software rankings on G2
- Provides alerts when exposed ports and services change
- Reduces the noise generated by constant log entries and warnings
- Prioritizes issues based on context and focuses on perimeter vulnerabilities
- Easy to set up, easy to maintain
Cons
- Can require manual work in tasks such as agent deployment
- Lacks a comprehensive GUI
- Does not use proprietary detection engine; uses OpenVAS and Nessus scanning engines
Pricing
Customers license Intruder at one of three levels and pricing is based upon the number of targets to scan. Annual discounts are available and for more than 250 targets, customers cannot use the calculator and must obtain a quote.
- Essential
- Powered by OpenVAS scanning engine
- 1 scheduled monthly scan, unlimited ad hoc scan, 2 users
- External vulnerability scanning only
- Pricing starts at $101 / month (1 target) and at 250 targets hits $689 / month
- Pro (free trial available)
- Uses Tenable’s Nessus scanning engine
- Unlimited scheduled and hoc scans, unlimited users
- External and Internal scanning
- Syn AWS, Google Cloud, Azure targets
- API & developer integrations
- SSL/TLS certificate monitoring
- Pricing starts at $163/month (1 target) and at 250 targets hits $983/month
- Vanguard
- Add triage from certified penetration testing
- Enhanced accuracy
- Extended vulnerability discovery
- Requires contacting Intruder for a quote
Rapid7 Insight Platform
The Rapid7 Insight platform provides a suite of security, vulnerability management, penetration testing, web and app scanning, orchestration and automation tools to enable organizations of all sizes to secure their sprawling IT environment. Insight VM provides the vulnerability management platform to automatically scan and assess physical, cloud and virtual infrastructures. The tool provides live and interactive dashboards, solution-based remediation and risk scoring and prioritization.
Insight VM builds on the local network vulnerability tool Nexpose, and automatically detects and scans all new devices connected to a network to provide real time vulnerability identification. It also offers a lightweight endpoint agent for processing information while consuming minimal bandwidth.
The InsightAppSec tool performs Dynamic Application Security Testing (DAST) on applications and integrates into development (dev) and security (sec) workflows. The tool crawls launched applications to check for nearly 100 different attack types including SQL Injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Key Features
- Unlimited user accounts
- 24/7 technical support
- Customizable dashboards
- Extensive vulnerabilities list scanned
- Policy assessment
- Attack surface monitoring
- Integrates with Splunk, ServiceNow, AWS and more
Pros
- Integrates with Rapid7 Detection & Response and Cloud security products as well as automation and orchestration products
- Includes remediation workflow
- Constant scanning and real-time data availability
- Uses a risk scale of 1,000 to help IT managers prioritize more effectively and efficiently
- Create custom asset groups to direct remediation to designated IT teams
- Can scan temporary assets such as containers and other virtual assets
Cons
- Requires an agent
- Limited PAM integration
- Requires SSH access to scan ESXi environments
- Challenging to scale
- Limited options for database instances
- Application scanning is not as comprehensive as dedicated app scanners
Pricing
Insight VM pricing depends on volume. Published prices start at $2.19/month/asset for 250 assets and decrease with volume discounts. For example, with 1,000 assets, the price drops to $1.71/month/asset. Annual payment pricing discounts and free trials are available, and Insight VM is also available within the AWS marketplace.
Packaged licensing options are also available, although Rapid7 does not necessarily publish pricing. For example, Cloud Risk Complete combines cloud infrastructure and application security scanning into one license.
Qualys Vulnerability Scanning
The Qualys Cloud Platform provides options for a wide variety of integrated security, vulnerability, compliance, asset management, and patch management tools. Organizations seeking vulnerability scanning can select from the modules related to vulnerability detection and management:
- Container Security
- Cloud Security Assessment
- Vulnerability Management Detection and Response (VMDR 2.0)
- Web Application Scanning
Although the features and capabilities will vary depending upon the modules selected, Qualys provides a one-stop shop for enterprise-scale security and vulnerability management for an entire IT environment.
Key Features
- Scans and detects IT devices, web applications, Operational Technology (OT), and Internet of Things (IoT)
- Scans all applications within the perimeter including cloud instances and APIs for mobile devices
- Qualys TruRisk provides proprietary risk ratings that combine CVSS scores, real-time threat indicators, exploit code maturity, assessments of active malware, threat actors, trending risk, and applied mitigation controls
- Can combine scans for vulnerabilities, compliance, and malware
- Consolidated user interface, reporting, and dashboards for all modules
- Deploys from a public or private cloud, fully managed by Qualys
- Options for one-click remediation of some vulnerabilities
Pros
- No code workflows
- Huge number of options
- Very effective when fully integrating asset management, vulnerability management, and security
- Rule-based integrations generates automatic tickets for remediation through tools such as ServiceNow and JIRA
Cons
- Requires an agent
- Steep learning curve for new users
- Many modules can often lead to excessive and repetitive menu options
- Not all options perform at equally high levels – especially without training
- Modules sometimes update separately resulting in inconsistent user interfaces
- Can be slow in scanning endpoints
Pricing
Customers license the Qualys Cloud Platform on an annual basis based upon the number of Cloud Platform Apps selected, the number of IP addresses, the number of web applications, and the number of user licenses. Customers describe three tiers of pricing: Express Lite (max 256 IP addresses, 25 web apps, 2 scanners, 3 users), Express (Max 3072 IP addresses, 100 web applications, 5 scanners), Enterprise (unlimited use).
Qualys does not publish prices, but customers have reported pricing packages from below $300 for small businesses and up to $2,000 for larger packages. Free trials subscriptions are available.
Tenable
Developed originally as an open source and free Unix vulnerability-scanning tool, Tenable later evolved Nessus into an agentless vulnerability assessment tool with coverage for more than 47,000 unique IT, IoT, OT, operating systems, and applications. Nessus and the free version, Nessus Essentials, still exist, but enterprise-scale customers need more sophisticated solutions.
For enterprise customers, Tenable integrates Nessus with the broader Tenable One platform, which includes tenable.io for vulnerability management and web app scanning as well as the tenable.sc security center. Tenable conducts regular research and discovers zero-day vulnerabilities that it adds to the Nessus tool for early detection.
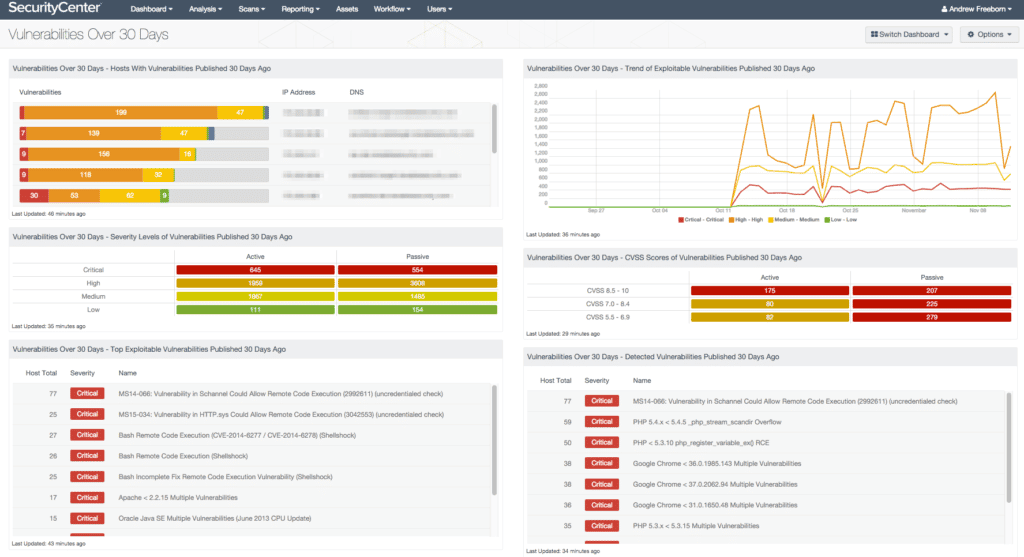
Key Features
- Preconfigured templates to enable quick starts
- Automatically performs full scans as soon as new vulnerability plugins are added
- Checks for vulnerabilities as well as compliance configurations
- Report templates provide quick snapshots
- Customizable templates enable branded reports for consultants and service providers
- Automated vulnerability and misconfiguration alerts for Security Incident and Event Management (SIEM) tools
Pros
- 3rd Easiest to Use in Vulnerability Scanner software rankings on G2
- Executive dashboards and powerful filtering to dig into findings
- Can assess modern infrastructure as code (IaC)
- Agentless Scanning
- False positive rate is lowest published rate with better than six-sigma accuracy (~0.32 defects per 1 million scans)
Cons
- Steep learning curve for new users
- Some users complain of false negatives
- Some users complain about limited API integration
Pricing
Tenable provides their products based on annual subscriptions with multi-year discounts. They offer two levels of pricing for Tenable.io:
- Tenable.io Vulnerability Management
- Pricing based per asset (minimum 65)
- $2,275 / year at 65 assets; discounts for multiple year contracts
- Tenable.io Web App Scanning
- Pricing per domain starting at 5 fully qualified domain names
- $3,578 / year for 5 domains
Free trial versions are available for the commercial products. Resellers may offer discounted or bundled pricing.
Best Enterprise Vulnerability Scanning Tool Criteria
To create this list, we surveyed a broad array of websites, vendor materials, and customer reviews to create a pool of qualified candidates based upon capabilities and reputation. We then filtered the list specifically for vendors that provide vulnerability scanning of the many different types of IT technologies and applications that an enterprise might deploy.
Similar capabilities can be achieved by combining very capable, but focused vulnerability scanners, but enterprises need tools that integrate with each other and that can be centrally managed by specialized security teams or service providers. Enterprise vendors also typically need enterprise-grade support for complex needs and issues.
Bottom Line: Buying Enterprise Vulnerability Scanning Tools
When purchasing integrated tools, it can be tempting to compare future features that could possibly be needed in 5-10 years., especially when it can be difficult to switch tools once the security team gains expertise after training and years of use on one tool.
Additionally, with enterprise-class vulnerability scanners, it doesn’t make sense to deploy multiple tools from different vendors and suffer with integration issues. Instead, open source tools should be used to provide low-cost second-opinion vulnerability scans — if the security team has the bandwidth to learn and run those tools.
Enterprise-grade vulnerability scanning tools can provide enormous return on investment by lowering the cost of IT and security teams to track, scan, and manage vulnerabilities. Still, organizations should avoid overpaying for unneeded features. Compare deployed assets against the scanning capabilities of the tools, and compare the integrations with the specific security tools already in place or options to replace existing tools.
If the tool doesn’t make sense now, future cost-savings initiatives may eliminate the tool in the future. Buy the tool needed to solve today’s problem at a price that makes sense now.
For more information on Vulnerability Scanning Options see:
- What is Vulnerability Scanning & How Does It Work?
- Best Vulnerability Scanner Tools
- 12 Top Vulnerability Management Tools for 2023
- 10 Best Open-Source Vulnerability Scanners for 2023
- Penetration Testing vs. Vulnerability Testing: An Important Difference








