Application programming interface (API) security is a combination of tools and best practices to secure the all-important connections between applications.
API security protects data and back-end systems while preserving fluid communication between software components through strict protocols and access controls. Apps are protected from unauthorized access, data breaches, and other unwanted actions thanks to proactive defenses that prevent and mitigate vulnerabilities, misconfigurations, and other security weaknesses.
Table of Contents
Fundamentals of API Security
API security includes a range of tactics such as strict authentication and authorization methods, data encryption technologies, and strong access controls. Effective input validation prevents possible intrusions, while secure API key management and token management procedures ensure secure access. Real-time monitoring is made possible via auditing and logging, which helps in incident response and threat identification.
Additionally, as fundamental parts of this complete architecture, adherence to safe API design standards and compliance with data protection laws reinforce APIs against a variety of cyber risks.
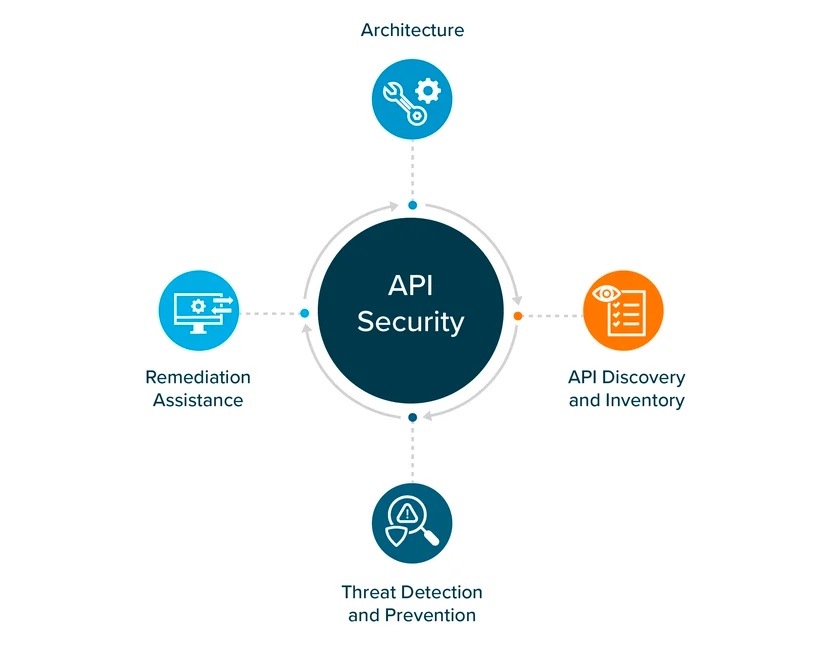
API Architecture
APIs act as virtual bridges, connecting different apps and systems for seamless communication and data sharing without exposing source code to partners — and hopefully keeping back-end systems secure too. A secure API architecture serves as a strong foundation for all that, designed with security in mind. So in addition to good development and coding practices like data partitioning and encryption, API security entails creating clear boundaries and permissions to ensure that only authorized users can access APIs. By constructing APIs thoughtfully, vulnerabilities are minimized, protecting against accidental data leaks.
API Discovery and Inventory
Imagine APIs as digital keys granting access to your virtual “doors,” and maintaining an API inventory is akin to having a record of your keys. It’s not just about knowing what you have; it’s about managing access. Tracking APIs helps manage potential security gaps and the risk of unauthorized entry, preventing potential points of attack.
Threat Detection and Prevention
Once your development and architecture practices are set, you still need to monitor API interactions for any suspicious or improper behavior. API security tools can quickly identify suspicious actions, patterns and vulnerabilities and take action before they worsen. And many API security tools can test for security issues while APIs are still in development, improving security both in development and production environments.
See our picks for the Top API Security Tools
Remediation Assistance
Despite safeguards, vulnerabilities can occur. Having a response plan for security incidents is essential. When a vulnerability is detected or an attack unfolds, remediation assistance offers guidance to swiftly address the issue. This ensures timely containment and restoration to a secure state. Integration with continuous development and integration (CI/CD) processes is also important to speed and track security fixes.
API Security Standards
Modern API security is built on best practices, monitoring, and industry standards like Open Authentication (OAuth) and OpenID Connect, both of which play specific roles in strengthening your digital space.
How OAuth Works
OAuth is primarily focused on authorization. It offers a framework for letting other programs access resources on behalf of a user without disclosing the user’s login information. It uses cryptographic signatures to guarantee safe communication between the parties involved.
OAuth 2.0 adds access delegation. With the use of tokens like access tokens and refresh tokens for secure resource access, it presents a more adaptable and versatile token-based method. In order to make the protocol more comprehensible and flexible, OAuth 2.0 also standardized the division of roles, such as resource owners, clients (applications), and authorization servers.
For example, a client (mobile app) registering with the Google Photos Authorization Server receives a client_id and a client_secret. The client initiates the OAuth process by redirecting the user to the Authorization Server’s authorization endpoint, which includes parameters like client_id, redirect_uri, response_type, scope, and state.
The user is then presented with a Google Photos login page and asked to grant or deny access. If the user grants access, the Authorization Server generates an authorization code. The code is then sent to the client provided. The client sends a POST request to the Authorization Server’s token endpoint, providing an access token and possibly a refresh token. The client can use the obtained access token to make authorized requests to the Resource Server (Google Photos), which verifies the token and responds with requested data if authorized. If the token expires, the client can use the refresh token to obtain a new access token without user interaction.
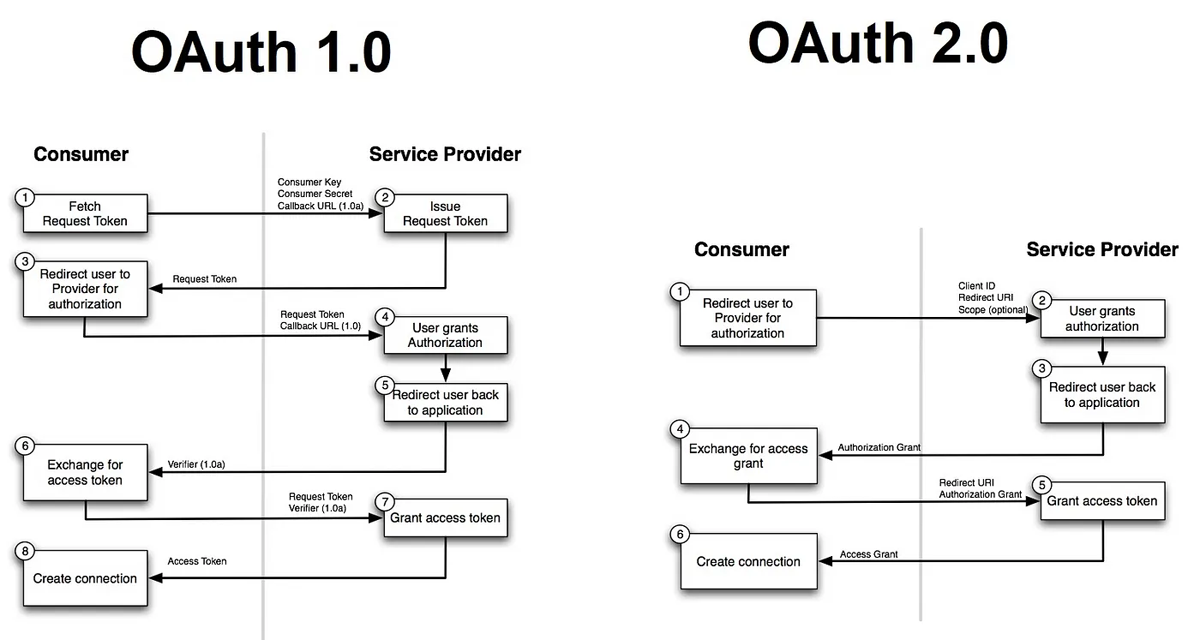
OpenID Connect
Precise user identity confirmation across a wide range of platforms and apps is orchestrated via OpenID Connect. A single set of credentials may be used by users to verify their identity across various online environments thanks to OpenID Connect, the orchestrator of the authentication symphony and master conductor of digital identity. The frictionless use of services like Spotify, where access is accelerated by a single login via Facebook or Gmail, serves as an example of this. With this function, OpenID Connect is elevated to additionally provide identity verification, departing from OAuth’s initial scope of access provisioning and igniting a faster, more secure authentication process.
10 Most Common API Security Risks
Here are 10 common API security risks and prevention steps, from OWASP and other application security organizations.
Unsafe Consumption of APIs
This risk involves utilizing APIs in a way that could result in security flaws, including problems like not properly managing login and authorization or not ensuring the accuracy of data received through APIs.
Prevention: Ensure that the data you receive from APIs is thoroughly vetted and cleaned. Control access to critical resources by utilizing secure communication protocols (HTTPS), establishing suitable authentication procedures, and running authorization checks.
Improper Inventory Management
This risk could lead to APIs that accidentally expose sensitive information about the architecture, parts, or underlying technology of the application.
Prevention: Implement appropriate API access restrictions and authentication. Make sure that only intended APIs are exposed and accessible by doing regular audits and reviews of your API inventory.
Security Misconfigurations
Improperly configured APIs are a major source of security vulnerabilities. This involves enabling superfluous features, using default settings, and resolving errors ineffectively.
Prevention: To avoid leaking sensitive information, disable unnecessary functionality, utilize least privilege principles for access, and put solid error handling systems in place.
Server-side Request Forgery (SSRF)
By tricking a server into making unauthorized calls to internal resources, an attacker might expose sensitive information or inadvertently take unexpected action.
Prevention: To avoid fraudulent URLs, validate and sanitize user input. Utilize network-level safeguards to limit outgoing requests and implement whitelists of permitted domains or IP ranges that the server may send requests to.
Access to Business Flows Without Restriction
This risk arises when APIs give unauthorized users access to confidential corporate procedures or activities.
Prevention: Implement suitable procedures for authentication and authorization as a preventive measure. To guarantee that only authorized users may access critical APIs, employ role-based access control (RBAC).
Broken Function-Level Authorization
Attackers do this by taking advantage of flaws in authorization processes to access features or perform actions they shouldn’t be able to.
Prevention: Implement fine-grained permission checks for each function or activity within the API as a mitigation. Verify user rights and roles before granting access to a particular feature.
Unrestricted Resource Consumption
Denial-of-service (DoS) attacks can be launched by attackers who use APIs to use large amounts of server resources and disrupt function and access.
Prevention: To mitigate resource misuse, implement rate limitation, request throttling, and input validation. Check API use for questionable patterns.
Broken Object Property Level Authorization
This is when attackers trick API requests to gain unauthorized access to or alter the characteristics or attributes of an object.
Prevention: Implement appropriate access restrictions and validation to make sure users can only see or change the attributes for which they have been given permission.
Broken Authentication
Attackers obtain unauthorized access to APIs and sensitive data by taking advantage of flaws in authentication processes. Broken authentication happens because of poor password creation, compromised password storage systems, and vulnerabilities in the encrypted authentication framework.
Prevention: Protection against typical attacks like brute force and credential stuffing may be achieved by implementing strong authentication methods like multi-factor authentication (MFA), enforcing safe password rules, and properly implementing encryption.
Broken Object-Level Authorization (BOLA)
BOLA vulnerabilities can let attackers tamper with input to gain access to restricted areas or carry out forbidden activities. This happens because of insecure coding practices that fail to validate a user input.
Prevention: To prevent access to resources and actions by unauthorized users, implement appropriate input validation and permission checks. You can employ universal unique identifiers and adopt the zero-trust security framework.
A combination of secure coding techniques, comprehensive testing, appropriate setup, and ongoing monitoring are required to defend against API vulnerabilities. It is crucial to keep up with the most recent security issues and incorporate any fixes into your development process.
Tips on How to Avoid API Attacks
API attacks are among the most common and damaging cybersecurity issues. To reduce these risks, organizations should proactively address the vulnerability of their API systems. Building robust APIs that can withstand various attacks ensures data protection, accuracy, and unrestricted access to essential services.
Utilize Strong Authentication and Authorization
Opt for robust authentication mechanisms that suit your application’s requirements. Employ OAuth for secure third-party access and token-based authentication for user sessions. Enforce role-based access control (RBAC) to meticulously manage authorization, ensuring that users can only access authorized resources and actions.
Incorporate Rate Limiting and Throttling
Set up rate limiting tailored to your API’s nature and user roles. Define thresholds for requests per user, IP, or specific API endpoints. Throttling works as a safeguard against misuse and depletion of resources by governing the pace at which requests can be initiated.
Validate Inputs and Sanitize Data
Undertake comprehensive input validation to ascertain that user inputs adhere to anticipated formats and values. Employ established input validation techniques and libraries to thwart threats like SQL injection and cross-site scripting (XSS). Implement output encoding to neutralize the potential interpretation of data as code.
Prioritize HTTPS and Secure Communication
Employ HTTPS exclusively to encrypt data exchange between clients and servers. This measure assures data confidentiality, rendering eavesdropping, man-in-the-middle attacks, and data tampering ineffective.
Implement Sound Error Handling
Adopt generic error messages free of sensitive information about your system’s internal mechanisms. Develop a robust error handling mechanism that logs errors without revealing confidential data and responses.
Champion Security Testing and Code Reviews
Regularly conduct security evaluations encompassing dynamic application security testing (DAST), static application security testing (SAST), and manual penetration testing. Consistent code reviews facilitate the early identification of vulnerabilities.
Maintain Timely Updates and Patches
Stay abreast of security vulnerabilities associated with your API’s dependencies. Keep all software elements up to date, including libraries, frameworks, and the underlying OS. Swiftly apply patches to mitigate the risk posed by known vulnerabilities.
Monitor API Traffic
Integrate monitoring and logging mechanisms for your APIs. Analyze inbound and outbound traffic for abnormal patterns, spikes, or trends suggestive of malicious activity. Employ intrusion detection and prevention systems (IDPS) for automated detection and response to suspicious behavior.
Employ Web Application Firewalls (WAF)
Consider deploying a WAF for an additional layer of defense. A WAF screens out malevolent traffic, obstructs recognized attack patterns, and provides protection against emerging threats.
See the top Web Application Firewalls
Sanction Whitelisted Domains and IPs
When feasible, configure your API to exclusively accept requests from trusted domains or specific IP ranges. This measure minimizes exposure to potential attackers.
Educate Developers and Users
Provide secure coding training to your development team and consistently deliver security awareness training to API users. Foster a security-centric mindset throughout the development and usage life cycle.
Integrate Content Validation
Validate that incoming API requests adhere to the projected schema in terms of structure, format, and content. This guards against attackers exploiting vulnerabilities in data processing.
Implement OAuth for Third-Party Access
For APIs interfacing with third-party applications, implement OAuth for secure authorization and constrained access. OAuth permits users to grant specific permissions to third-party apps without exposing their credentials.
Implement API Version Control
Employ versioning to guarantee backward compatibility and provide a seamless transition for consumers when introducing modifications. This prevents disruptions to existing integrations.
Incorporate Security Headers
Leverage security headers in API responses to regulate browser behavior. Content security policies (CSP) help thwart cross-site scripting, while Cross-Origin Resource Sharing (CORS) policies constrain access to your API from specific origins.
Ensure Secure API Documentation
Validate that your API documentation refrains from divulging sensitive information about your application’s architecture, technology stack, or security mechanisms. Disclose only essential details to enable secure API interaction comprehension.
Adhere to OWASP Guidelines
Stay current with OWASP’s resources, particularly the OWASP API Security Top Ten. Regularly review and implement their recommendations to align with the latest API security best practices.
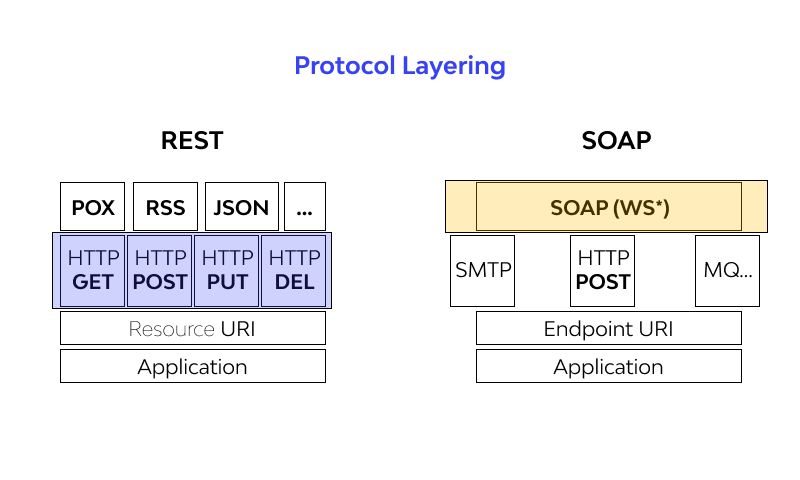
REST vs SOAP API Security
REST and SOAP are commonly used approaches for building APIs, and using them securely is critical for API security.
Simple Object Access Protocol (SOAP) is a collection of tools and strategies that make use of Web Service Description Language (WSDL). These requirements serve as locks and keys for data, guaranteeing that the data supplied and received is kept private and cannot be altered without the consent of the intended recipient.
The standardization and organization of SOAP API Security results in a concise set of guidelines that lessen the likelihood of errors or security flaws. This standardized and exacting technique, however, could take more work to set up and comprehend than straightforward approaches.
Representational State Transfer (REST) is for simpler operations where create, read, update, and delete (CRUD) are being performed. REST excels at being straightforward and adaptable, which makes it useful for a variety of applications. To protect the integrity and confidentiality of the shared data, REST implementation will frequently utilize tokens for authentication and authorization in addition to the protection offered by HTTPS.
HTTPS encrypts communication between the client and server and guarantees data integrity and confidentiality, which is the foundation for security in REST APIs. The padlock icon in the browser’s address bar denotes a secure connection. For safeguarding access and authorization, tokens like JSON Web Tokens (JWT), OAuth tokens, or other authentication tokens are frequently used. A user’s role, permissions, and access privileges are represented via tokens.
REST vs SOAP Comparison Table
| REST | SOAP | |
|---|---|---|
| Server-side sessions? | Yes (for default configuration), it is stateless. It can be changed to stateful. | No, because it is stateful. |
| How does it operate? | It is driven by functionalities (services) for data fetching. Commands like getUser are used. | Data is considered a resource. |
| Transfer Protocol | HTTP, UDP, SMP, etc. | HTTPS |
| Design | It is well-standardized and has a strict set of pre-specified rules. | The architecture follows a not-so-strict guideline. |
| Cashes | Not used | Used |
| Security | Adheres to ACID properties and ensures enterprise-grade security that makes it ideal for sensitive data exchange and even financial transactions. | HTTPS + SSL |
| Format accepted for messaging | XML | JSON, XML, HTML |
| Resource consumption | It is resource-intensive and requires higher bandwidth and computing power. | Requires much fewer resources. |
| Java API | JAX-WS | JAX-RS |
| Do they work together? | It does not utilize SOAP due to its high architectural standards. | This web service can utilize SOAP due to its standard for diverse usage. |
| Exposing Technique | Technicalities and methods can be viewed using WSDL. | Its methods can be exposed using URIs. |
What Are the Top Tools for API Testing?
Different requirements and preferences are addressed by these tools. Beagle Security offers a user-friendly interface for API security testing, StackHawk is developer-focused, and Wallarm specializes in automated threat detection. Your decision should be based on your unique demands and the nature of your organization’s API security requirements. See our list of the Top API Security Tools for additional ideas.
Wallarm API Security Platform: Best for Automated Threat Detection
Wallarm is a thorough security platform created to safeguard apps and APIs from online dangers. It excels in automated threat detection, which enables it to swiftly recognize and address any security vulnerabilities without the need for user intervention. For businesses wishing to automate their monitoring and response procedures for API security, this makes it ideal.
StackHawk: Best for Developer Teams
A tool that effortlessly fits into the process of development is StackHawk. It is an API security testing tool that is user-friendly for developers, so it can be used while they create and distribute apps. It is a great asset for teams focusing on continuous integration and delivery (CI/CD) since it aids developers in identifying and fixing security problems early in the development process.
Beagle Security: Best for User Interface API Security Testing
For assessing API security, Beagle Security provides a simple user interface. It makes it easier to scan and evaluate the security of your APIs. Its user-friendly interface makes it simpler for developers and security experts to communicate and comprehend the findings of security testing. Beagle Security may be a wise choice if you place a high priority on a user-friendly experience when performing API security testing.
Also read:
API Breach Examples
Unfortunately, major API security breaches happen all the time. Here are three major API breaches that happened this year, the most recent just a few weeks ago.
Duolingo
In August 2023, news broke that the personal information of 2.6 million users of the well-known language learning website Duolingo — including email addresses, usernames, language preferences, and learning progress — had been leaked. An unprotected API that let anybody check if an email address was linked to a Duolingo account caused the compromise.
Discord
In March 2023, over 760,000 users were impacted by a data breach at Discord.io, a customized invite service for Discord. The hacker ‘Akhirah’ posted a database of user data for sale on the dark web. Both non-sensitive information and possibly sensitive information were included in the data. Discord.io suspended operations and began an inquiry. To prevent a breach from happening again, Discord.io wants to update the website’s programming and security features. Users weren’t compelled to change their passwords, but those who registered prior to 2018 should think about doing so on other websites as well. Users are urged to implement two-factor authentication for increased security because Discord.io and Discord are independent companies.
MOVEit
Also this year, the MOVEit file transfer software breach impacted over 1,000 organizations and 60 million people worldwide, with most victims in the U.S., Germany, Canada, and the UK. Notably, a U.S. government contractor, Maximus, had the data of up to 11 million individuals compromised. Financial institutions were hit the hardest.
The breach’s estimated cost is around $10 billion, but it could be even higher if more victims report their losses. The ransomware group Clop might have been planning this since 2021, and stands to gain a significant $100 million from this campaign.
Bottom Line: Getting API Security Right
API security is critically important in today’s digital landscape, ensuring the confidentiality, integrity, and availability of sensitive data and services. Whether dealing with simple REST APIs or complex SOAP-based systems, robust security measures are not optional. Basic API security measures like development best practices, tracking and assessing vulnerabilities, and implementing authentication and authorization controls offer a big payoff for low-cost efforts. Investing in API security solutions will also help safeguard your organization’s reputation and financial well-being in our deeply connected world.
Next: See the Top Vulnerability Management Tools








