Cloud workload security, or cloud workload protection (CWP), refers to the tools and policies used to protect apps, services, and resources that run on cloud infrastructure. It secures virtual machines, databases, containers, and applications against common threats. CWP platforms, now commonly included in cloud-native application protection platforms (CNAPPs), safeguard workloads in public, hybrid, and multi-cloud environments.
Table of Contents
How Cloud Workload Security Works
Your organization can manage cloud workload security through coordination across multiple specialist teams. IT admins protect your consoles. Cloud security teams oversee virtual infrastructure and perform automated discovery. DevOps teams remove hard-coded secrets and manage consoles. Network security specialists monitor traffic insights, while the incident response teams monitor security events.
The following security processes performed by these teams should fully work together to ensure comprehensive protection:
- Securing cloud management consoles: IT administrators manage your consoles continuously and support all other security measures by managing permissions and configurations centrally.
- Protecting virtual infrastructure: Cloud security teams monitor virtual servers and combine this process with management panels and automated discovery to assure secure environments.
- Removing hard-coded secrets: DevOps teams prevent unauthorized access, eliminate hard-coded secrets, secure DevOps methods and integrate them into deployment frameworks.
- Overseeing and securing DevOps consoles: DevOps team track and defend DevOps consoles while enabling automatic discovery and integration into deployment frameworks.
- Conducting automated discovery: Security operations team evaluate and track workloads regularly to improve virtual infrastructure control and protection and security event management.
- Gaining insights into network traffic: Network security specialists manage and enhance the network data to assist in real-time threat identification and automated remediation.
- Integrating processes into deployment frameworks: Security and DevOps team automate security procedures during deployments to ensure coverage across all workloads and environments.
- Consolidating events: Security and incident response teams control and centralize security events to improve threat visibility and response while supporting all other security activities.
Incorporating these operations within your organization creates a strong, multilayered security structure for effective cloud workload protection. Examine the types, tools, and platform requirements for successful implementation. Then, through adhering to best practices, you can optimize the benefits of cloud workload security. This results in resilience against the common threats while protecting the reliability and integrity of your cloud environments.
Common Cloud Workload Protection Classifications
The different types of cloud workload protection can be grouped into three categories: cloud deployment models, cloud native technologies, and resource demands. These help you select proper security measures and deployment methodologies for your specific cloud workload requirements.
Deployment Model
There are three kinds of deployment models: infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS). Each cloud deployment model provides distinct benefits geared to specific organizational objectives and operational effectiveness in the cloud environment.
- Infrastructure as a service (IaaS): Controls virtualized resources such as virtual machines (VMs), storage, and networking.
- Platform as a service (PaaS): Enables application creation and management without requiring infrastructure.
- Software as a service (SaaS): Provides entire software solutions through the internet via a subscription model.
Cloud Native Technology
Classifying cloud workloads via native technology allows you to optimize deployment methods and safety protocols. Understanding whether applications are better suited to containers, serverless environments, or virtual machines supports more efficient resource allocation, scalability planning, and security setting. Each provides distinct advantages in terms of flexibility, efficiency, and scalability.
- Containers: Are lightweight, portable components designed for application deployment in isolated settings.
- Container as a service (CaaS): Offers fully managed container environments that isolate infrastructure complexities.
- Serverless: Automatically scales computational resources for code execution without the need to manage infrastructure.
- Virtual machines (VMs): Simulate physical servers, and are often provided via cloud-based services.
Resource Demands
Categorizing cloud workloads types based on resource requirements helps optimize task resource allocation. It guarantees that computational resources such as CPU, GPU, memory, and storage are tailored for task demands to improve efficiency and performance in cloud settings. This classification enables enterprises to achieve affordability and scalability while meeting specific operational requirements.
- High central processing unit (CPU): Employ powerful central processing units to execute complex computations such as data analytics and scientific simulations.
- High graphics processing unit (GPU): Includes specialized graphics processing units to handle graphics-intensive applications like CAD and video rendering.
- High performance computing (HPC): Uses parallel computing to effectively execute complicated computations in large-scale contexts.
- Memory-intensive: Requires a large amount of memory to function properly and handle databases, analytics, and caching applications.
- Standard compute: Manages broad responsibilities like site hosting and software development effectively in cloud settings.
- Storage-optimized: Needs high input/output performance to conduct large data analytics and content management.
8 Benefits of Cloud Workload Security
Cloud workload security advantages, from protecting sensitive information to managing cloud complexity, maintaining data integrity, and guaranteeing operational continuity. They also help you in meeting regulatory standards and increasing efficiency across cloud settings. Each advantage contributes specifically to the organization’s overall resilience and security posture.
- Handles sensitive information: Minimizes illegal access and data breaches while maintaining trust and compliance.
- Maintains business continuity: Reduces disruptions and ensures continuous operations to improve organizational resilience and customer satisfaction.
- Supports compliance efforts: Adheres to regulatory rules and industry norms, avoiding legal concerns and reputational damage.
- Strengthens security posture: Improves overall cloud security posture by reducing risks and vulnerabilities to ensure long-term protection.
- Incorporates security measures: Enforces IAM and RBAC, which regulate access and reduce the risk of unauthorized exposure.
- Automates security processes: Increases efficiency in identifying and responding to threats, hence improving overall security effectiveness.
- Provides comprehensive asset visibility: Enables a unified picture of assets, allowing for proactive monitoring and speedier issue response.
- Centralizes workload management: Streamlines your workload control, reduces complexity, and improves operational efficiency.
8 Common Cloud Workload Risks & Threats
Cloud workloads are vulnerable to data breaches, malware, misconfiguration, and more. Regardless of cloud providers’ security measures, compromised credentials may harm entire systems, disclosing sensitive data to attackers. Hard-coded API keys, privileged access, and unpatched apps make them vulnerable to attacks, but you can reduce these risks by employing tools and secure practices. Here are the common threats and risks of cloud workload security:
- API vulnerabilities: Arise when insecure APIs in cloud apps allow unwanted access or compromise, usually due to poor design, weak authentication, or insufficient encryption mechanisms.
- Data breaches: Occur as a result of weak passwords, unpatched software, or weak access restrictions, which allow unauthorized parties to steal or change sensitive data housed in cloud environments.
- Distributed denial-of-service attacks: Flood cloud workloads with excessive traffic, disrupting services and causing downtime, frequently exploiting vulnerabilities in network infrastructure or application layers.
- Insider threats: Happen when internal users abuse privileges or credentials to access and exploit sensitive data or resources housed in cloud environments for personal gain or malevolent purpose.
- Malware and ransomware: Infect cloud workloads by exploiting vulnerabilities or misconfigurations, encrypting data or disrupting processes, and demanding ransom payments to restore access.
- Misconfiguration of security controls: Occur when credentials, firewalls, or access policies are incorrectly configured, resulting in vulnerabilities that attackers can exploit to obtain unauthorized access or compromise cloud resources.
- Multi-tenancy risks: Result from sharing cloud infrastructure with multiple tenants, raising the risk of data breaches or unauthorized access if security measures are not properly segregated or monitored.
- Unauthorized access to workloads: Takes place after attackers use stolen or compromised credentials to circumvent inadequate access controls and get unauthorized access to cloud-hosted apps or data.
10 Cloud Workload Security Best Practices
The best practices for cloud workload security include established methods for risk mitigation and data protection. They ensure uniformity in the implementation of security measures across several cloud environments, hence reducing vulnerabilities. Evaluate your cloud infrastructure, workloads, and existing security measures first. Then, apply other best practices once you’ve identified which of the methods below best fit your business operations.
Examine Your Cloud Infrastructure
Begin by recording and analyzing the different types of cloud services (public, private, and hybrid) that your company employs. Identify the cloud providers you collaborate with and describe the types of workloads managed in each environment. This mapping aids in visualizing the complete cloud landscape and detecting potential security concerns linked with different types of services and providers.
Identify the Criticality of Your Cloud Workloads
This includes categorizing the data, applications, and infrastructure components that make up each workload in your cloud environment. It allows you to get insight into each workload’s sensitivity and criticality. Understanding these elements helps you prioritize security solutions, ensuring that the most critical workloads are adequately protected.
Evaluate Your Existing Security Measures
Assess the performance of your current security measures and practices throughout your cloud system. Conduct audits and assessments to discover any holes or flaws in your security posture. The assessment acts as a baseline for determining where improvements are needed, and it assists in developing your security goals and strategies.
Secure Individual Workloads
Apply appropriate security measures to each workload based on its classification and criticality. For example, sensitive data might need encryption at rest and in transit, whereas important applications may have stringent access controls and continual monitoring. To prevent potential hazards, address any vulnerabilities found during evaluations as soon as possible.
Automate Cloud Workload Management
Use automation tools and techniques, such as infrastructure-as-code (IaC), to handle and deliver workloads in hybrid or multi-cloud systems. Automation minimizes human errors associated with manual setups, assures consistency in security policy enforcement, and speeds up operations such as provisioning, monitoring, and patch management.
Restrict Access to Sensitive Workloads
To limit access to sensitive data and apps, use strong identity and access management (IAM) solutions such as role-based access control (RBAC) and zero-trust principles. By prohibiting over-privileged access and applying least privilege principles, you can reduce the attack surface and lower the risk of unauthorized access and data breaches.
Deploy Monitoring & Logging Tools
Leverage cloud monitoring and logging tools to continuously manage the performance and health of your cloud applications and infrastructure. Monitoring aids in discovering odd activity or abnormalities that may signal a security breach. Logging provides audit trails for forensic investigation, as well as the ability to respond to and mitigate incidents quickly.
Apply Policy as Code
By incorporating security configurations directly into your code and deploying applications via containers, you ensure that security protections are reliably applied across several environments. The strategy improves security posture while reducing configuration drift and vulnerabilities.
Perform Security Analysis
Conduct regular security assessments, such as vulnerability scanning and penetration testing, to proactively discover and mitigate security flaws. Regular evaluations assist in understanding evolving risks, evaluating security procedures, and following regulatory compliance. Create and implement remediation plans based on the assessment results to improve your overall security posture.
Centralize Tracking for Visibility
Create consolidated monitoring and tracking capabilities across your cloud environments to acquire a comprehensive view of security events and activities. Integrate monitoring technologies that collect logs and metrics from many cloud providers and environments. This centralized method allows for proactive threat detection, rapid incident response, and effective security issue management.
Combine your workload-specific measures with general cloud security best practices and tips for deeper protection of your cloud systems.
Cloud Workload Protection Platform Requirements
Before choosing a CWPP solution, evaluate the support for hybrid and multi-cloud setups, ease of deployment, continuous monitoring, and runtime protection while maintaining performance. It should also provide visibility across all cloud types, security against misconfigurations, malware, and breaches, and automated risk management and compliance, among other things.
Consider the following factors:
- Deployment flexibility: Make sure the CWPP works flawlessly with your hybrid and multi-cloud settings.
- Ease of deployment: Select a system that integrates seamlessly without increasing operational overhead.
- Comprehensive security features: Verify that it has features like endpoint detection and response (EDR), vulnerability scanning, and compliance monitoring.
- Continuous monitoring: Consider a CWPP that provides real-time monitoring features to quickly discover threats and anomalies.
- Automation capabilities: Look for features that simplify risk management, compliance, and vulnerability prioritization.
- Runtime protection: Determine whether the platform offers full security for containers and cloud workloads during runtime, rather than merely at launch.
- Visibility: Ensure that the CWPP provides complete insight into workload events, including container activity, to enable effective threat detection and response.
- Performance: Assess the solution’s performance impact to ensure that it meets operational requirements without causing major delays.
- Integration with DevOps: Evaluate whether the CWPP works well with DevOps methods to facilitate agile development.
- Scalability: Check if the solution scales as your workload grows and if it adapts to your dynamic cloud environment.
Top CWPPs to Consider
CWPP solutions like Illumio Core, SentinelOne Singularity Cloud, and Sophos Cloud Workload Protection automate monitoring across servers. They provide unified visibility and administration for physical machines, VMs, containers, and serverless programs to boost cloud security. These solutions improve your overall cloud management, lower the likelihood of data breaches, and help strengthen your security posture.

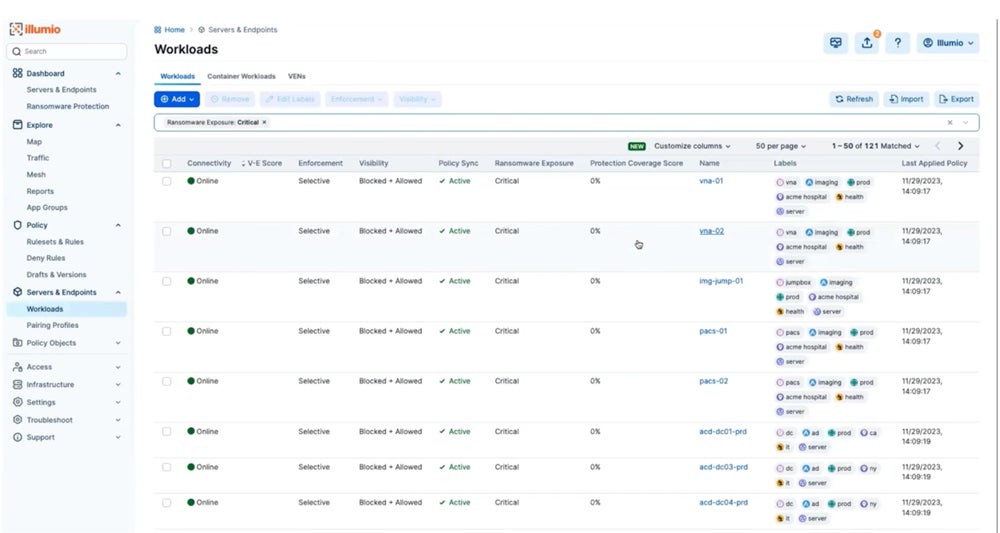
Illumio Core
Illumio Core is a CWPP solution offering micro-segmentation capabilities, workload visibility, and real-time threat detection. It offers granular security control over network traffic and dynamically modifies security settings based on workload behavior. Illumio Core provides consistent protection through easy scaling in cloud environments. Pricing starts at $7,000 per year for 50 protected workloads and 25 ports.

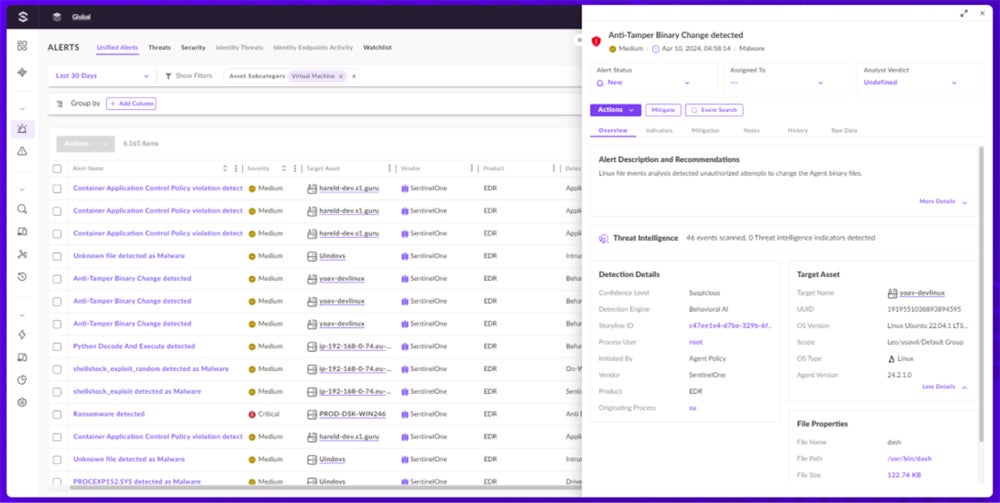
SentinelOne Singularity Cloud
SentinelOne’s Singularity Cloud specializes in advanced automation, with a focus on runtime detection and response for cloud virtual machines, containers, and Kubernetes clusters. It employs AI-powered algorithms and behavioral analytics to respond to advanced threats in real time. Singularity Cloud expands across many cloud environments and starts at $36 per VM or Kubernetes worker node, per month.

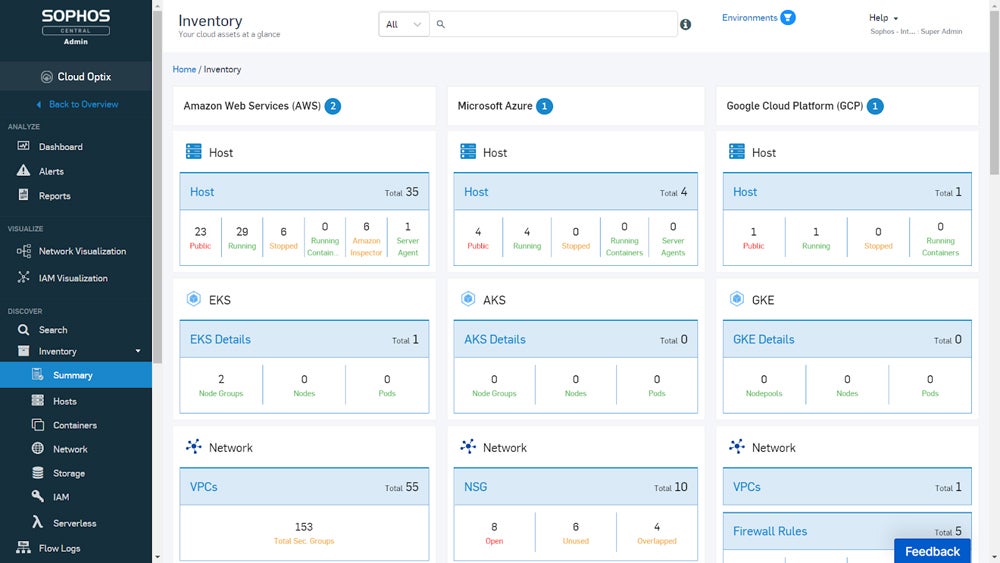
Sophos Cloud Workload Protection
Sophos Cloud Workload Protection provides effective cloud workload protection through a user-friendly interface, strong security features, and seamless integration possibilities. It offers extensive visibility and detects threats, including container escapes and kernel exploits. Sophos’ Integrated Live Response enables rapid incident response, hence improving total cloud workload protection. Custom quotations are available by contacting their sales team.
Discover more solutions in our full review of the top CWPP solutions covering their use cases, features, pros, cons, and more.
Bottom Line: Boost Your Cloud Workload Security Now
Implementing cloud workload security best practices and utilizing CWPP tools improve security, guarantee regulatory compliance, and sustain business continuity. Combining CWPPs with supplementary cloud solutions enhances your overall protection through the integration of multiple security layers specific to different aspects of cloud security. Utilize CWPPs’ integrative capabilities to strengthen the security and resilience of your cloud workloads.
To further enhance your cloud security posture, explore other solutions by reading our comprehensive guide covering CSPM, CWPP, CIEM, CNAPP, and CASB, plus their distinct features and practical applications.








