Cybercriminals are quickly ramping up efforts to exploit the critical flaw found in the widely used Log4j open-source logging tool, targeting everything from cryptomining to data theft to botnets that target Linux systems.
The cybersecurity community is responding with tools for detecting exploitation of the vulnerability, a remote code execution (RCE) flaw dubbed Log4Shell and tracked as CVE-2021-44228 (Apache Log4j 2.15.0 requires its own fix). Efforts include a Log4j emergency patch from the Apache Software Foundation (ASF), a “vaccine” released by Cybereason, a mitigation from NCC Group to stop Log4j from loading classes remotely over LDAP, a Log4j exploit detection tool from CrowdSec, and more.
In addition, the U.S. Cybersecurity Infrastructure and Security Agency (CISA) is continuing to put its weight behind efforts to protect enterprise systems. CISA Director Jen Easterly said in a statement over the weekend that the agency has created a Joint Cyber Defense Collaboration senior leadership group to coordinate actions within the government – including the FBI and National Security Agency (NSA) – and private sector to manage the risk.
Easterly urged federal and other government agencies as well as private companies to patch the flaw – which carries the highest severity rating – as quickly as possible. “This vulnerability, which is being widely exploited by a growing set of threat actors, presents an urgent challenge to network defenders given its broad use,” she said.
CISA has offered guidance for dealing with Log4j vulnerabilities and added Log4Shell to its list of known exploited vulnerabilities. CISA is also compiling a list of vulnerable products, but others have stepped up in the meantime, among them the Dutch National Cyber Security Center and researcher Royce Williams.
There has been speculation that the vulnerability was behind a massive ransomware attack that could knock Kronos Private Cloud services offline for weeks, although the company hasn’t said that the vulnerability was a factor in the attack.
Read the latest on the Apache Log4Shell vulnerability
A Major Threat
The Log4Shell flaw – which Impacts Log4j versions 2.0 through 2.14.1 and has a CVSS severity score of 10.0 – carries with it a significant threat given the broad enterprise use of Log4j and the countless number of servers and cloud-based services that could be exposed to the zero-day vulnerability. Open-source projects like ElasticSearch and Elastic Logstash also use Log4j, and the vulnerability also could affect default configurations of such Apache frameworks as Apache Struts2, Apache Druid and Apache Flink.
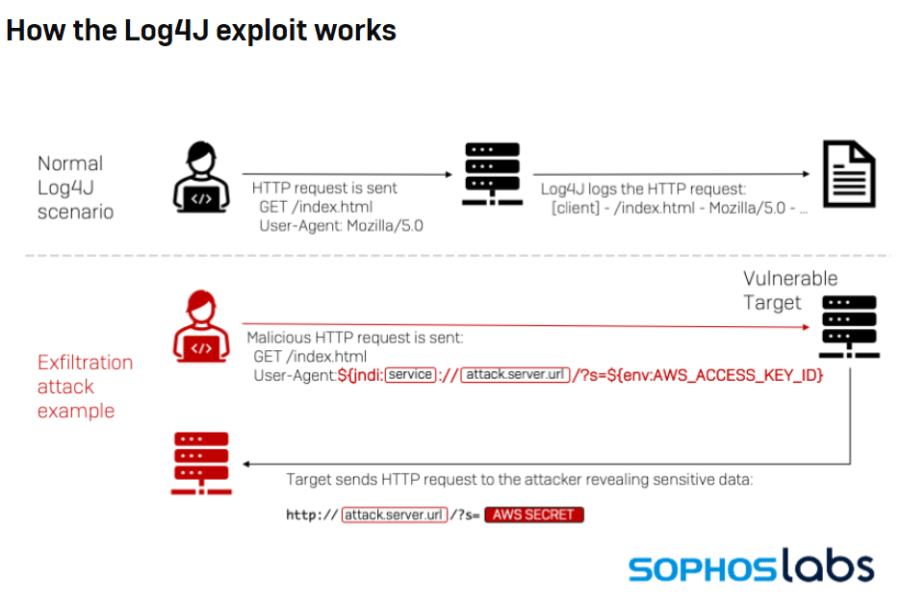
Adding to the dangerousness of the flaw is the ease with which it can be exploited. Bad actors need only send a string that includes the malicious code, which then gets parsed and logged by Log4j and loaded into a server. From there, hackers can gain control of the system that is running the software, giving them a platform for launching a variety of attacks.
“Because of its large attack surface and the innate severity of remote code execution, security researchers are notably calling this a ‘shellshock’ vulnerability,” John Hammond, senior security researcher at Huntress Labs, wrote in a blog post. “All threat actors need to trigger an attack is one line of text. There’s no obvious target for this vulnerability – hackers are taking a spray-and-pray approach to wreak havoc.”
Huntress created a tool to help organizations test whether applications are vulnerable to Log4Shell.
Also read: Top Vulnerability Management Tools
Attacks Include Cryptomining, Data Theft
According to a blog post by Microsoft threat researchers, most of the attacks seen were related to mass scanning by bad actors searching for vulnerable servers as well as by security companies and researchers.
“At the time of publication [Dec. 11], the vast majority of observed activity has been scanning, but exploitation and post-exploitation activities have also been observed,” they wrote. “Based on the nature of the vulnerability, once the attacker has full access and control of an application, they can perform a myriad of objectives. Microsoft has observed activities including installing coin miners, Cobalt Strike to enable credential theft and lateral movement, and exfiltrating data from compromised systems.”
The Microsoft researchers also have seen efforts by cybercriminals to evade detection. When an attacker performs an HTTP request against a targeted system, it generates a log using Log4j that uses JNDI (Java Naming and Directory Interface) to send a request to an attacker-controlled site that launches the payload. Attackers are running obfuscation efforts around the requests to bypass string-matching detections.
Botnets Strike
Researchers with Netlab, a security unit of Chinese tech giant Qihoo 360, wrote over the weekend that their Anglerfish and Apacket honeypots detected two efforts to leverage Log4Shell to create Muhstik and Mirai botnets to attack Linux devices. They also wrote that, given the broad impact of the Log4j vulnerability, they expect more bad actors to try to use it to create botnets.
Sophos researchers wrote that they have detected cryptomining efforts and “hundreds of thousands of attempts since December 9 to remotely execute code” using the vulnerability. Other vendors, including Cisco and VMware, also have seen Log4Shell being exploited in the wild.
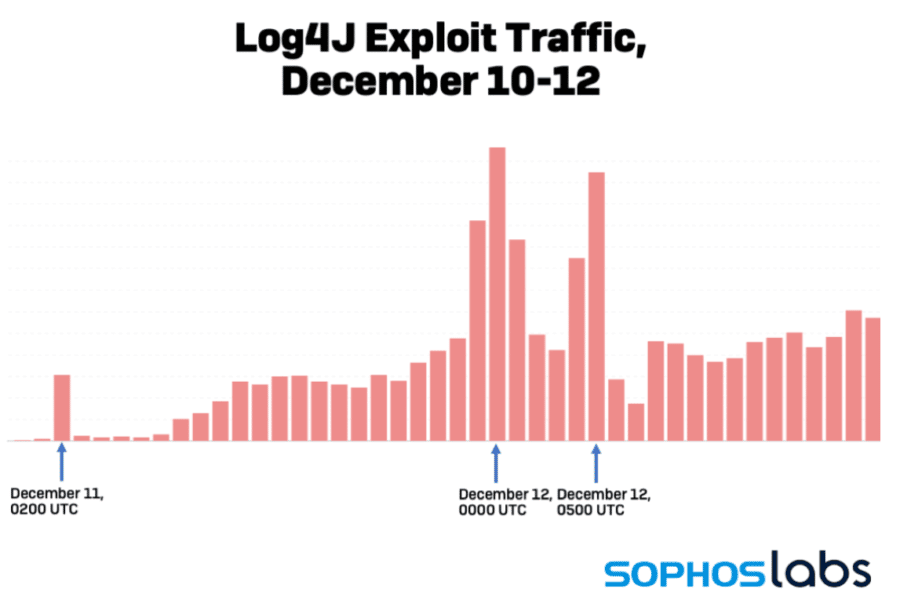
Researchers at Talus, Cisco’s threat intelligence business, wrote in a blog post that they detected a lead time between mass scans from bad actors and the callbacks from vulnerable systems.
“This may indicate that the exploit is being triggered as it makes its way through an [a]ffected enterprise’s infrastructure and its processed by internal systems … that may completely separate from the intended target system.”
They added that vulnerable inspection, event collection or logging systems on the communications path also could trigger the exploit.
Also read: Best Patch Management Software
A Vaccine for Log4Shell
Cybersecurity firms are trying to stem the rapidly rising tide of attempted exploits of the Log4j vulnerability. Beyond the ASF patch, cybersecurity firm Cybereason on Dec. 10 created a vaccine designed to disable Log4Shell and made freely available on GitHub.
“In short, the fix uses the vulnerability itself to set the flag that turns it off,” Yonatan Striem-Amit, co-founder and CTO of Cybereason, wrote in a blog post. “Because the vulnerability is so easy to exploit and so ubiquitous – it’s one of the very few ways to close it in certain scenarios. You can permanently close the vulnerability by causing the server to save a configuration file, but that is a more difficult proposition. The simplest solution is to set up a server that will download and then run a class that changes the server’s configuration to not load things anymore.”
The vendor’s fix “will disable the vulnerability and allow you to remain protected while you assess and update your servers,” Striem-Amit wrote.
Casey Ellis, founder and CTO of crowdsourcing security company Bugcrowd, told eSecurity Planet that as a first message, companies should be cautious about running Cybereason’s vaccine on someone else’s infrastructure, saying doing so could violate anti-hacking laws.
“Aside from that, I quite like the ‘chaotic good’ nature of this solution, especially given the chaos organizations are experiencing in finding all of the places that Log4j might exist within their environment,” Ellis said. “The script basically takes the workaround first flagged by Marcus Hutchins, which disables indexing and then uses the vulnerability itself to apply it. The fact that solutions like this are coming out so quickly is telling regarding the ubiquity of this vulnerability, the complexities of applying a proper patch and the sheer number of ways that it can be exploited.”
Vulnerability Surfaced in Late November
According to the emerging timeline, the security team at Alibaba Cloud in late November first detected the vulnerability on servers running Minecraft and reported it to the ASF. Apache on Dec. 5 identified the vulnerability in a JIRA issue and the next day released the patch. On Dec. 9, weaponized proof-of-concept (POC) exploits began to appear, fueling a rapid increase of scanning and public exploitation the next day, according to GreyNoise researchers.
Between noon and 2 p.m. ET on Dec. 10, they saw a five-fold increase in the number of hits per sensor related to Log4Shell.
However, a number of vendors, including Talus and Cloudflare, are reporting that the vulnerability may have been openly exploited more than a week before the first weaponized PoCs were pushed out to the public on Twitter Dec. 9, sparking the scramble of activity.
The problem likely will only get worse, according to Andrii Bezverkhyi, founder and CEO of threat detection and intelligence company SOC Prime.
“The problem with Log4j is that every major tech on our planet that has Java uses it and the exploit has been around since March,” Bezverkhyi told eSecurity Planet. “This is worse than Zerologon; it could get as bad as Wannacry.”
Enterprise security teams need to work on mitigation, hunt to understand if they were breached since March, and report the status to their boards of directors for tactical and strategic support, he said.
Further reading: Best Risk Management Software








