Are your systems running slower than they should? Perhaps a certain web page is more sluggish than usual and your system seems to lag. Be concerned – you could potentially be a victim of a cryptojacking campaign.
Cryptojacking is a relatively new term and is a class of attack that gained significant momentum in the latter half of 2017, as the value of cryptocurrencies, including Bitcoin and Ethereum, rose to unprecedented levels.
In this first article of an eSecurity Planet series on cryptojacking, we’ll discuss this new attack and how it is already disrupting IT users.
What is cryptojacking and how does it work?
So what is cryptojacking? Simply put, cryptojacking is an unauthorized cryptocurrency mining operation.
Cryptocurrencies are generally linked to some form of blockchain, which is basically a ledger of transactions and values. Many cryptocurrencies rely on a method of creation known as “mining,” in which computations are performed on a block to ensure its authenticity.
Individual systems generally do not have enough computing capacity to effectively mine cryptocurrencies directly. Rather, the general practice is for miners to be part of a mining pool, where the mining pool distributes and validates code blocks for miners to process.
The fundamental processing unit for a mining operation is the hash rate, or the rate at which cryptographic hashes are computed on a block in an effort to mine a given cryptocoin. The higher the hash rate, the greater chance of mining a coin. And as successful miners receive a small payment for their efforts, miners have good reason to compete to crack the code.
Bitcoin (BTC), perhaps the most widely known cryptocurrency, has a complex blockchain and generally requires purpose-built hardware (known as ASICs) or clusters of powerful Graphics Processing Units (GPUs) in order to mine Bitcoins. The same is generally true for Ethereum (ETH), another popular cryptocurrency.
The Monero cryptocurrency (XMR) is different, though, and can be mined with CPU power alone, though it does also benefit from systems that have a GPU on them. While cryptojacking can refer to any form of unauthorized cryptocurrency mining operation, in large part, most of the activity is directed at XMR mining.
Different cryptojacking attack vectors
One way that cryptojacking attacks occur is via JavaScript code that runs in a browser. In that type of attack, the user visits a page, watches a video or clicks a link, where the embedded JavaScript cryptocurrency code is deployed.
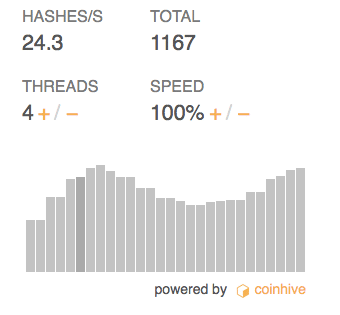
The embedded cryptocurrency JavaScript executes as a background process on the end-user system and can consume up to 100 percent of CPU resources in a short period of time. In-browser cryptojacking is not stealing user information, rather it is more of a nuisance attack that can degrade system performance. It’s basically stealing CPU power to increase cryptomining speed.
The most common form of in-browser mining cryptojacking attack uses code from the Coinhive site. It’s important to note that Coinhive itself is not malware and the code and service the site provides are intended to help site authors monetize content. There are sites that aim to legitimately use Coinhive in order to generate revenue and are supposed to alert users that Coinhive is being used. Cryptojacking attacks using Coinhive do not generally identify themselves and in many cases are deployed on sites as part of a malware payload.
The challenge for in-browser mining is the relatively low hash rate. In a test conducted by eSecurityPlanet, the Coinhive hash rate hovered at approximately 24.3 H/s. The low hash rate for in-browser mining has led attackers to attempt broad distribution on popular sites. That way attackers make money is from a lot of users over a period of time.
The other approach to cryptojacking can yield significantly higher hash rates — and revenues for attackers. In a server-based deployment, an attacker makes use of an existing vulnerability in order to deploy a full-scale cryptocurrency miner on a system.
Reported attacks that have used the server-based deliver method have abused SSH, SMB, Reddis database and Oracle WebLogic vulnerabilities. The reality is that that the miner code is just the payload for an intrusion. All an attacker needs to do is get enough access to a server to install the miner in order to cryptojack the server.
Typically, given that Monero is the most popular cryptocurrency for attackers, the deployment uses a variant of the open-source XMRig Monero mining code.
Stopping cryptojacking
So now you know what cryptojacking is all about, but how do you stop it? The next article in this series provides an overview and review of the technologies for blocking cryptojacking attacks.
Sean Michael Kerner is a senior editor at eSecurityPlanet and InternetNews.com. Follow him on Twitter @TechJournalist.