Cloudflare last month fought off a massive distributed denial-of-service (DDoS) attack by a botnet that was bombarding 17.2 million requests per second (rps) at one of the internet infrastructure company’s customers in the financial services space.
The attack was almost three times larger than any previous attack that Cloudflare is aware of, according to Omar Yoachimik, product manager for DDoS protection at Cloudflare. For comparison, Cloudflare manages an average of more than 25 million HTTP rps, so at its peak, this botnet-driven DDoS attack was sending the equivalent of 68% of Cloudflare’s daily average RPS rate of legitimate traffic.
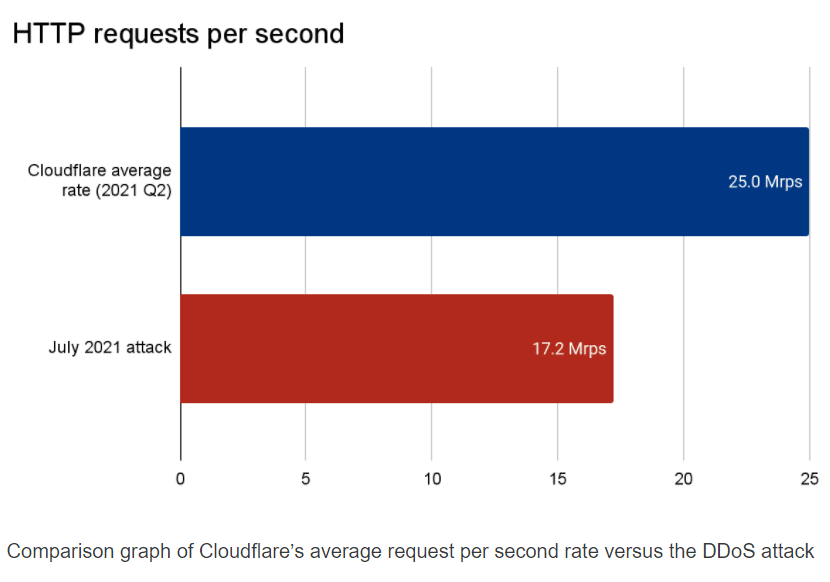
“Within seconds [of the onset of the attack], the botnet bombarded the Cloudflare edge with over 330 million attack requests,” Yoachimik wrote in a blog post this week.
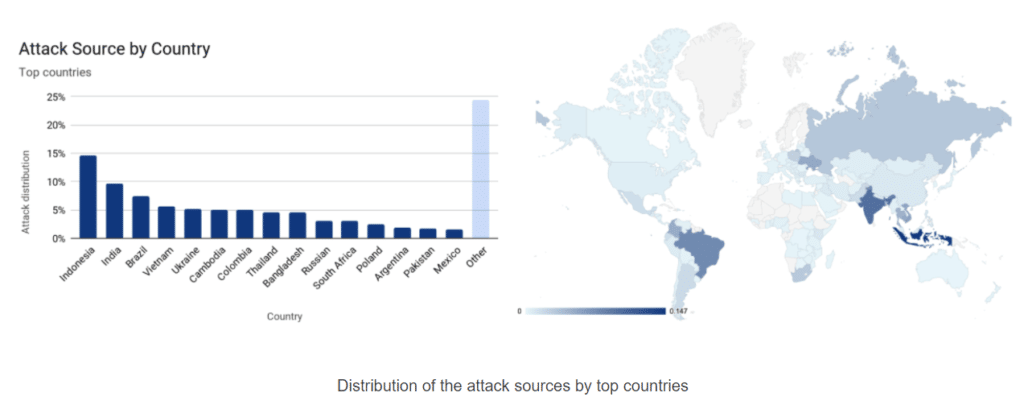
He added that the botnet comprised more than 20,000 bots in 125 countries, with almost 15 percent of the attacks coming from Indonesia and another 17 percent from India and Brazil combined, an indication that there could be many malware-infected devices in those countries.
A Significant Attack
The size of the botnet and the attack is significant, according to Tyler Shields, chief marketing officer at cyber asset management platform provider JupiterOne.
“The ability for a DDoS attack to reach that level of bandwidth exhaustion means that there is a significant backend infrastructure of either compromising hosts or hosts that have been scaled up with the sole purpose of sending malicious traffic,” Shields told eSecurity Planet. “The only other way to achieve these levels of bandwidth is to couple an enormous infrastructure with some kind of packet amplification technique. Either way, this is a meaningful attack that was not generated by a random attacker. This group is likely large, well-funded and dedicated.”
Yoachimik wrote that Cloudflare was able to mitigate the attack through its autonomous edge DDoS protection systems, which leverages a Cloudflare-developed denial of service daemon (dosd). A unique dosd instance runs in each of Cloudflare’s servers in all of its data centers worldwide, and is designed to analyze traffic samples, scanning for DDoS attacks and putting mitigation processes in motion.
DDoS Attacks on the Rise
According to a report from Netscout, there was a record number of DDoS attacks in 2020 during the COVID-19 pandemic and researchers expected that the trend would follow into 2021. That prediction proved correct. Netscout’s Atlas Security Engineering and Response Team (ASERT) found that about 2.9 million DDoS attacks occurred in the first quarter, a 31 percent increase year-over-year.
If the current pace persists through the end of 2021, it will rush past last year’s record of about 10 million attacks. The researchers also noted that January and February usually are the slowest months for DDoS attacks, and while the size of the attacks in Q1 were relatively flat over last year, the maximum throughput recorded for attacks in the quarter jumped 71 percent – an indication that “attackers continue to find value in pouring on faster, more difficult-to-mitigate attacks”.
Netscout also saw increases in DDoS attacks in the healthcare industry and the education realm, both of which saw increased attention from attackers due to their roles during the pandemic. There was a 53% increase in first-quarter attacks among healthcare organizations. Meanwhile, there were 32,000 attacks on educational services in the third quarter 2020, compared with 45,000 in the first quarter this year.
“As we know, adversaries thrive on constant innovation,” ASERT researchers wrote. “Attacks will only grow more complex, and threat actors will continue to discover and weaponize new attack vectors designed to exploit the vulnerabilities exposed by this enormous digital shift.”
Mirai Still on the Loose
Cloudflare’s Yoachimik said the botnet used to attack the financial services customer appears to have leveraged a new version of the durable Mirai malware, which tends to be aimed at Internet of Things (IoT) devices. The same botnet also apparently carried out two other large-scale DDoS attacks in the weeks leading up to the latest one, including one aimed at a web hosting provider that peaked at 8 million rps. The other victim was a gaming company.
Yoachimik wrote the Mirai botnet initially started off with about 30,000 bots, though it shrunk to about 28,000. Still, the volumes of attack traffic over short periods – in some cases lasting only a few seconds – was impressive, he said.
Cloudflare researchers have seen a sharp increase in the number of Mirai-based DDoS attacks over the past several weeks. In July, the number of L3/4 Mirai attacks jumped 88 percent and L7 attacks increased 9 percent. In addition, based on what they have seen in the per-day average in August, the number of L7 Mirai and similar botnet attacks should increase by 185 percent and L3/4 attacks by 71 percent by the time August is over.
Growing IoT Will Fuel More Attacks
Howard Ting, CEO of data detection and response specialist Cyberhaven, told eSecurity Planet that such DDoS attacks are “a growing problem and one that we should expect to see more of. Botnets, such as Mirai that launched the attack, heavily rely on compromised IoT devices and other unmanaged devices. As the number of these devices grows, so too does the potential army for DDoS attacks.”
Mirai was first discovered in 2016 and the malware spreads by infecting Linux-based devices like security cameras and routers, according to Yoachimik. One a device is infected, the malware “self-propagates by searching for open Telnet ports 23 and 2323. Once found, it then attempts to gain access to vulnerable devices by brute forcing known credentials such as factory default usernames and passwords,” he wrote.
Some variants since then have taken advantage of zero-day exploits in devices like routers and, once infected, the devices will monitor a Command and Control (C2) server for instructions on targets to attack.
The Mirai attack on the financial services firm was a volumetric DDoS attack, which is designed to overwhelm the capacity of networks by shoving significantly high volumes of malicious traffic at them, consuming huge amounts of bandwidth.
Yoachimik wrote that while most of the attacks Cloudflare sees are small and short, these types of volumetric attacks are becoming more common.
“It’s important to note that these volumetric short burst attacks can be especially dangerous for legacy DDoS protection systems or organizations without active, always-on cloud-based protection,” he wrote. “Furthermore, while the short duration may say something about the botnet’s capability to deliver sustained levels of traffic over time, it can be challenging or impossible for humans to react to it in time. In such cases, the attack is over before a security engineer even has time to analyze the traffic or activate their stand-by DDoS protection system. These types of attacks highlight the need for automated, always-on protection.”
Further reading:
How to Stop DDoS Attacks: 6 Tips for Fighting DDoS Attacks
How to Prevent DDoS Attacks: 6 Tips to Keep Your Website Safe
Top 10 Distributed Denial of Service (DDoS) Protection Vendors








