Nation-state cyber threat groups and ransomware attackers are moving in to exploit a critical flaw found in the seemingly ubiquitous Apache Log4j open-source logging tool, as attacks spread just days after the vulnerability that could affect hundreds of millions of devices was made public late last week.
Microsoft researchers reported that the remote code execution (RCE) vulnerability is being exploited by nation-state groups associated with China, North Korea, Iran and Turkey, with the activity that includes “experimentation during development, integration of the vulnerability to in-the-wild payload deployment, and exploitation against targets to achieve the actor’s objectives.”
The vulnerability can be abused to enable an attacker to gain control of a targeted system.
Two of the known groups include Phosphorous from Iran and Hafnium from China. According to Microsoft, Phosphorous has been deploying ransomware and acquiring and making modifications to the Log4j exploit. In addition, Hafnium “has been observed utilizing the vulnerability to attack virtualization infrastructure to extend their typical targeting,” the researchers wrote in the blog post. “In these attacks, HAFNIUM-associated systems were observed using a DNS service typically associated with testing activity to fingerprint systems.”
Log4j Patching, Scanning Success Reported
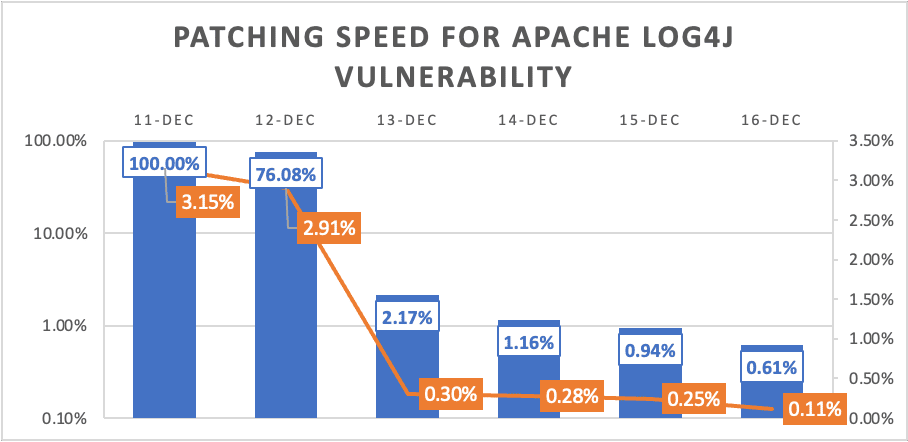
Update: In one positive and unexpected development, external attack surface management company Cyberpion reported that enterprises are patching the Log4j vulnerabilities unusually fast, if imperfectly.
Meanwhile, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released a scanning tool to “help organizations identify potentially vulnerable web services affected by the log4j vulnerabilities.”
Cyberpion scanned more than 500 enterprises to assess their exposure to the flaw in relation to their connected, third-party online assets and infrastructures. The vast majority (95%) of organizations were connected to external vulnerable infrastructure, yet while 3% of their third-party assets were exposed as of Dec 11th, this had fallen to just 0.11% as of Dec. 16.
To quickly block the attack, firewall rules were added by many security teams, though some could easily be bypassed with slightly more sophisticated payloads, indicating that many vulnerabilities still exist and can still be exploited, the company said.
Also read: Best Patch Management Software
Expanding Log4j Attacks
At the same time, cybersecurity professionals are reporting that bad actors are expanding the range of attacks they’re launching against the zero-day Log4j exploit, which is being tracked as CVE-2021-44228 and has been dubbed Log4Shell. Apache is tracking vulnerabilities as they emerge, and VMware has issued its own advisory.
Bitdefender researchers wrote in a blog post that early exploit attempts have involved cryptojacking and botnets, such as the Muhstik botnet.
However, while most of the attacks seen are targeting Linux servers, there are emerging attacks aimed at Windows systems, including a new ransomware family called Khonsari, which was first observed Dec. 11 as a malicious .NET binary file.
Microsoft researchers also wrote that multiple groups acting as access brokers are using Log4Shell to gain initial access to target networks and then “sell access to these networks to ransomware-as-a-service affiliates. We have observed these groups attempting exploitation on both Linux and Windows systems, which may lead to an increase in human-operated ransomware impact on both of these operating system platforms.”
Like Bitdefender, Microsoft also has seen the flaw absorbed into existing botnets, such as Mirai.
Greg Linares, principal software architect at Cylance, said in a tweet that he expects a worm to be developed within the next day or so that leverages the Log4j flaw.
Also read: Top Vulnerability Management Tools
Escalation of Exploit Attempts
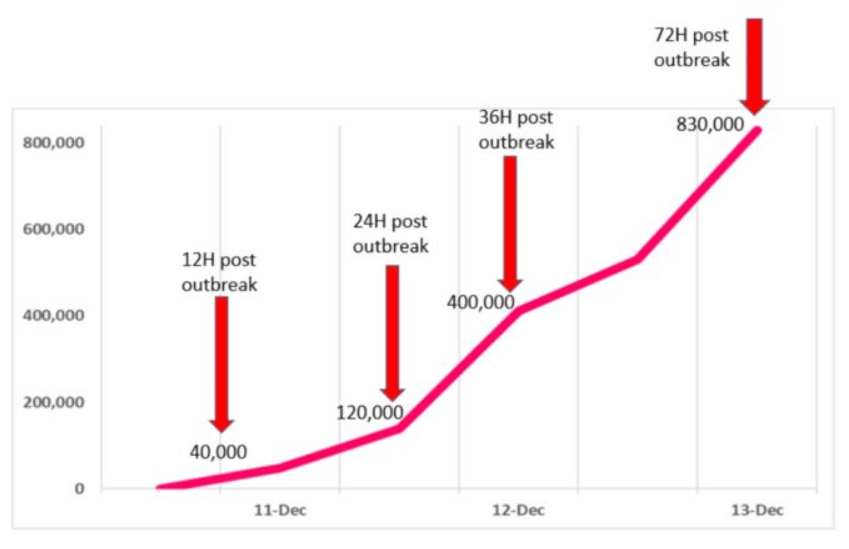
Overall, the pace and range of attacks are growing rapidly. Security researchers at Check Point Software in a blog post said that after the first weaponized proof-of-concepts (POCs) illustrating the vulnerability hit the internet on Dec. 9, there were reports of thousands of attacks the next day, expanding to more than 800,000 attacks after 72 hours.
Since Check Point began implementing its protection, the company in three days had prevented more than 1.8 million attempts to “allocate the vulnerability,” with more than 46 percent of the attempts being made by known malicious groups, they wrote.
There have been attempted exploits of the Log4j vulnerability on more than 44 percent of all corporate networks worldwide, according to Check Point.
“Three days after the outbreak, we are summing up what we see until now, which is clearly a cyber pandemic that hasn’t seen its peak yet,” they wrote.
In a tweet the same day, Cloudflare CEO Matthew Prince said the situation may be even more dire. Prince said his company is seeing more than 400 attempted exploits per second and that “payloads getting scarier. Ransomware payloads started in force in last 24 hours.”
Second Vulnerability Detected
Complicating the matter even more is a second Log4j vulnerability, which is being tracked as CVE-2021-45046 and is a less severe flaw (with a CVSS rating of 3.7 out of 10) than the first (the highest severity, a 10 out of 10 rating). It affects versions of Log4j from 2.0-beta9 through 2.12.1 and 2.13.0 through 2.15.0, an emergency fix the Apache Software Foundation (ASF) issued late last week to address the initial vulnerability. The ASF said the emergency patch for Log4Shell was “incomplete in certain non-default configurations.”
The group, which is the project maintainer for Log4j, wrote in advisory that the new vulnerability could be leveraged to “craft malicious input data using a JNDI [Java Naming and Directory Interface] Lookup pattern resulting in a denial-of-service (DoS) attack.”
Casey Ellis, founder and CTO of Bugcrowd, told eSecurity Planet that it isn’t surprising that other vulnerabilities were found in Log4j or that fixes for the software could trigger more research and discovery in the wake of a vulnerability as noisy as Log4Shell.
“In this case, the initial fix provided was developed in a way that mitigated the exploitable symptom, but didn’t properly address the root cause,” Ellis said while giving plaudits to the Log4j maintainers. “This also highlights the dangerous dependency open-source users have on libraries which power large portions of the internet but are ultimately written and maintained by unfunded volunteers with limited available time. A huge shoutout to the Log4j maintainers, who I’m sure have had an even busier and more stressful week than those in cybersecurity.”
More Flaws on the Way?
Davis McCarthy, principal security researcher at Valtix, told eSecurity Planet that the “technique of abusing JNDI lookups with user-generated data has been around for years. With the attention CVE-2021-44228 has received, I wouldn’t be surprised if we saw a third CVE related to Log4j2.”
Amid all this, cybersecurity professionals and tech firms are trying to stem the tide of the attacks. Beyond the emergency patch issued by the ASF, Cybereason this week issued a “vaccine” for the vulnerability while the NCC Group rolled out a mitigation to keep Log4j from loading classes remotely over LDAP and CrowdSec unveiled an exploit detection tool.
The latest to offer a Log4j defense tool is WhiteSource, which is offering a free developer tool, WhiteSource Log4j Detect, a CLI tool to help organizations detect and remediate Log4j vulnerabilities CVE-2021-44228 and CVE-2021-445046.
CISA Steps In
In addition, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) is ramping up its messaging about Log4Shell. In an updated advisory, the agency ordered that all civilian federal agencies patch the Log4j and three other vulnerabilities by Dec. 24 and placed Log4Shell on its Known Exploited Vulnerabilities list.
CISA also is urging vendors to identify, mitigate and update impacted products by using the latest patch, which protects against both Log4Shell and the subsequent flaw and to inform customers of their products to the vulnerability and to encourage them to prioritize software updates.
‘this vulnerability is one of the most serious that I’ve seen in my entire career, if not the most serious’
This comes as CISA met with industry leaders Dec. 13 in a phone briefing, urging them to take immediate action. According to CNN, CISA Director Jen Easterly reportedly told the executives that “this vulnerability is one of the most serious that I’ve seen in my entire career, if not the most serious. We expect the vulnerability to be widely exploited by sophisticated actors and we have limited time to take necessary steps in order to reduce the likelihood of damaging incidents.”
Taking the steps outlined by CISA won’t be easy, Bugcrowd’s Ellis said.
“That’s going to be nearly impossible for most organizations,” he said. “They need to find Log4j before they can patch it, and many are still stuck on that step. If Log4j is found, it’s likely that it is deeply embedded in existing applications and will require regression testing to ensure that a patch doesn’t break anything else. In short, the time pressure is a good thing for activating those who aren’t taking this seriously, but this will be a difficult timeframe for many to meet.”
A Cyber Pandemic
Still, the Check Point researchers warned that unless companies and service providers take immediate action to prevent attacks on their products, the Log4Shell vulnerability “seems that it will stay with us for years to come.”
“Since the outbreak of the COVID-19 pandemic, society has already gotten used to learning about variants, spread and other terminology that is taken from epidemiology theories,” they wrote. “The phenomena the world is witnessing with the exploitation of this vulnerability is very much identical. Given the upcoming holiday seasons, when security teams may be slower to implement protective measures, the threat is imminent. This acts precisely like a cyber pandemic – highly contagious, spreads rapidly and has multiple variants, which force more ways to attack.”
Further reading: Best Third-Party Risk Management (TPRM) Tools of 2021








