Vulnerability management is the process of identifying, classifying, remediating, and mitigating vulnerabilities. It is a critical part of an organization’s cybersecurity program.
There are many different vulnerability management frameworks, but the vulnerability management lifecycle of most organizations today typically includes five phases. We’ll examine those and then look at vulnerability management lifecycle best practices.
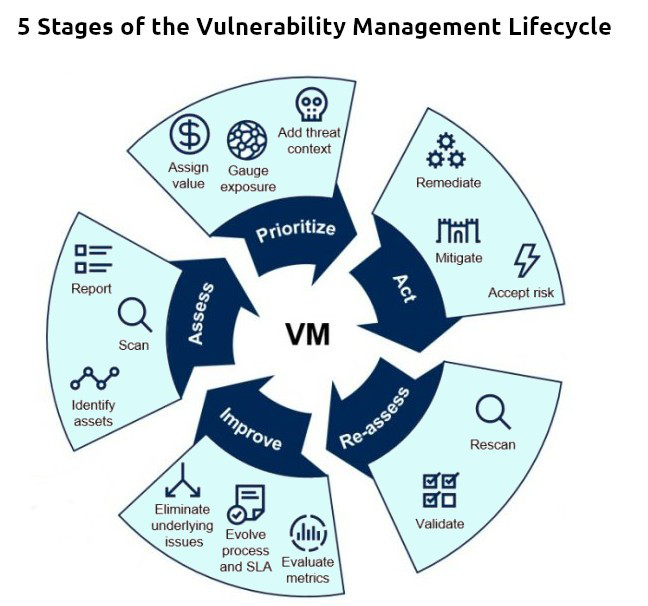
However, before we take a closer look at what each of the five stages entails, let’s discuss the prework stage, which lays the groundwork for a successful vulnerability management program. This planning stage includes:
- Define the scope of the program: The first step in the process is to define the scope of your vulnerability program. This includes establishing explicit goals for your organization, such as improving security posture or reducing risk.
- Define roles and responsibilities: Once you have defined the program goals, assign roles and responsibilities for each step in the vulnerability management lifecycle. This action ensures that all stakeholders are aware of their respective positions, as well as what they need to do to complete their tasks successfully.
- Select vulnerability assessment tools: Once you know who is responsible for which aspects of your vulnerability management program, it is crucial to select the right tools to help you optimize and streamline your efforts. This could include vulnerability scanners, configuration assessment tools, or security intelligence platforms.
- Create and refine policy and SLAs: A vital part of any vulnerability management program is the creation and refinement of policies, processes, procedures, and service level agreements (SLAs). These documents will help you determine how to address potential vulnerabilities, and they set expectations with stakeholders for what your program will achieve.
- Identify asset context sources: The vulnerability management lifecycle is about identifying and prioritizing assets based on their security context. Therefore, it is critical to understand the context surrounding your assets, such as their network and service dependencies and their business value to your organization.
Once you have completed the pre-work stages, you can move on to the actual vulnerability management lifecycle.
See the Top Vulnerability Management Tools
Assessment
There are three key phases in the initial vulnerability assessment stage.
Identify Assets
In this phase, you identify and inventory all of your organization’s digital assets, such as servers, workstations, and other devices. This involves gathering as much information about each asset as possible, including IP addresses, service account credentials, patch status, and more.
Scan for vulnerabilities
Once you have identified your assets, the next step is to scan them for vulnerabilities. Depending on your organization and its security needs, this could involve running vulnerability scans on all your assets or prioritizing certain assets based on their potential exposure and importance. In general, vulnerabilities will typically include:
- Broken authentication
- Human error
- Injection vulnerabilities
- Misconfigurations
- Missing encryption
- Missing software updates or patches
- Zero-day exposures
Report
Once the asset scans have been completed, you will prepare an asset inventory that identifies all business-critical assets. This will include asset details, any vulnerabilities detected during the scan, and their severity.
See the top IT Asset Management (ITAM) Tools
Prioritization
Once you know your vulnerabilities, you need to prioritize your fixes. There are three steps to this phase of the process.
Assign value
In this phase, you assign a value to each asset based on its business importance and potential exposure to cyber threats. This will help you prioritize your remediation efforts, as well as determine which assets should receive regular vulnerability scans. For example, you may choose to scan critical assets weekly, while less important assets can be scanned monthly.
Gauge exposure
The next step in the prioritization stage is to gauge the exposure of each asset. This involves assessing how likely it is that a vulnerability could be exploited by a cyber threat, as well as the potential impact of an exploit on your organization. For example, you may identify a potentially serious vulnerability that could turn into a DDoS attack if exploited, so it will be prioritized over a less severe vulnerability. The same can be said of a zero-day vulnerability that is actively being exploited, versus a well known vulnerability that is of lower threat risk.
Add threat context
Finally, you need to add threat context to each asset by integrating data from threat intelligence platforms and other external sources into your vulnerability management program. Examples of external sources you can leverage include threat feeds such as STIX, OpenloC, and MAEC. There is also a lot of information online about current threats, threat actors, tactics and techniques, and more.
Action
Once you have completed the vulnerability assessment, it is time to take action and address any detected vulnerabilities. There are several steps in this phase depending on the level of potential threat.
Remediate
One option is to remediate the vulnerability by patching or eliminating it. This involves evaluating and addressing the root cause of the vulnerability, as well as applying any necessary patches or updates to your systems. Patch management systems can make this phase of the job a lot easier.
Mitigate
Alternatively, you may choose to mitigate a vulnerability by adding additional security controls around assets that are at risk. For example, you may place a static firewall around any servers that are not adequately patched to prevent attackers from exploiting them. This process is sometimes called virtual patching.
Accept risk
In some cases, you may choose to accept the risk of a vulnerability and take no action. This could be due to a lack of resources or other factors such as low priority. This is generally not recommended, as it leaves your organization vulnerable to potential cyber threats and breaches, and hackers can string together vulnerabilities in surprising ways in a successful cyber attack.
It is important to evaluate all options before deciding which action is best for your organization.
Reassessment
Once you have completed the remediation or mitigation steps, it is important to continually reassess your vulnerability management process. This stage involves two phases.
Rescan
First, you need to rescan all assets to determine if they are still vulnerable. This may involve repeating the initial scans or using automated vulnerability assessment tools that can scan and identify new vulnerabilities.
Validate
Next, you will validate your remediation efforts by confirming that each vulnerability has been addressed or mitigated accordingly. You may need to conduct penetration tests and other assessments to ensure that your systems are secure from threats.
Improvement
Vulnerability management is a cycle. It is therefore good practice to get continuous feedback to improve effectiveness. This stage incorporates three critical phases.
Evaluate metrics
One important step in improving your vulnerability management process is to evaluate and analyze the metrics gathered throughout each stage. This can help you track progress, identify trends and patterns, and make improvements to optimize performance.
Evolve process and SLAs
In addition to evaluating metrics, it is also important to evolve your vulnerability management process over time. This may involve making changes to your SLAs and evaluating new technologies, platforms, or services that can enhance your cybersecurity posture.
Eliminate underlying issues
Finally, you may need to eliminate underlying issues to truly improve your vulnerability management process. For example, this could mean improving patching times, strengthening access control measures, or addressing any other weaknesses in your systems that could leave you vulnerable to threats.
Also read: Vulnerability Management Policy: Steps, Benefits, and a Free Template
Vulnerability Management Lifecycle Best Practices
Unfortunately, implementing the vulnerability management lifecycle into your workflow is often easier said than done. Organizations have to grapple with a host of issues such as a lack of resources, insufficient training, outdated technologies, forgotten assets, and organizational silos that impede effective vulnerability management. Here are some best practices to help you implement the vulnerability management lifecycle into your workflow.
- Do your prework: Problems usually occur when organizations fail to do their prework, which includes critical steps like assessing which assets and systems need to be scanned.
- Create a vulnerability management plan: Another critically important step is to create a formal plan that outlines your approach and identifies key stakeholders and responsibilities.
- Streamline handovers and communication: One of the reasons organizations fail to effectively incorporate the vulnerability management lifecycle is that teams at various stages of the cycle are often working independently. For example, it isn’t uncommon for the scanning team to transmit a report containing thousands of vulnerabilities to the operations team to fix. To streamline handovers and ensure that each team is working in sync, it is helpful to establish clear lines of communication and workflows that ensure all teams are aligned.
- Implement targeted training and education: To ensure the success of your vulnerability management efforts, it’s important to invest in targeted training and education programs that help team members understand their roles and how they fit into the larger vulnerability management process.
- Invest in the right tools, technologies, and platforms: Finally, organizations must also take an iterative approach when it comes to investing in tools, technologies, and platforms that can support effective vulnerability management. This may involve evaluating new scanning tools, implementing continuous monitoring capabilities, or incorporating automation into your workflow. Breach and attack simulation (BAS) tools are one way to help automate the process.
Bottom Line: Vulnerability Management Lifecycle
By following these best practices and implementing the vulnerability management lifecycle into your workflow, you can ensure that your organization is better equipped to deal with cybersecurity threats and vulnerabilities. With thoughtful planning, coordination and execution, you can maximize efficiency and performance while greatly reducing cybersecurity risks.
Read next: Vulnerability Management as a Service: Top VMaaS Providers








