Cybercriminals are targeting Linux-based servers running Microsoft’s Azure public cloud environment that are vulnerable to flaws after Microsoft didn’t automatically apply a patch on affected clients in its infrastructure.
According to cybersecurity firm Recorded Future, the attacks began the night of Sept. 16 after a proof-of-concept exploit was published earlier in the day on GitHub. About 10 malicious servers have been searching the internet for vulnerable systems, and while the search began slowing, it has now ramped up to more than 100 sites by morning, Recorded Future noted, citing information from threat intelligence vendor GreyNoise.
In addition, Cado Security researchers in a blog post also noted a tweet from cybersecurity researcher German Fernandez, who found that the infamous DDoS Mirai botnet – known for taking advantage of insecure Internet of Things (IoT) devices – also is exploiting OMIGOD. Mirai is putting a version of the botnet into a system and then closing the 5896 OMI SSL port, essentially stopping others from exploiting the same box.
According to Cado researchers, the Mirai worm tries to spread to other systems via various vulnerabilities, including OMIGOD.
“The race is on,” Stuart Winter-Tear, director of strategy at threat model solutions maker ThreatModeler, told eSecurity Planet. “As this is now confirmed as being actively scanned and exploited in an automated fashion via botnets, and we know there is the potential for root privilege remote code execution, any open OMI ports must be closed as soon as possible and Azure mitigation guidelines need to be implemented.”
Large Number of Linux Servers Vulnerable
Security researchers from cybersecurity startup Wiz detected the zero-day vulnerabilities – which they called OMIGOD “because that was our reaction when we discovered them,” Wiz Senior Security Researcher Nir Ohfeld wrote in a blog post – and published their findings Sept. 14.
thousands of Azure customers and millions of endpoints are impacted by the flaws
The flaws include CVE-2021-38647, which is a remote code execution bug, and three privileged escalation vulnerabilities: CVE-2021-8648, CVE-2021-38645 and CVE-2021-38649. Ohfeld wrote that the researchers offered a conservative estimate that thousands of Azure customers and millions of endpoints are impacted by the flaws.
Wiz, which came out of stealth in December 2020 with $100 million in funding, analyzed a small number of Azure tenants and found that more than 65 percent were unknowingly at risk.
“Supply chain cyber attacks have disrupted everyday life and dominated headlines this year,” he wrote. “One of the biggest challenges in preventing them is that our digital supply chain is not transparent. If you don’t know what’s hidden in the services and products you use every day, how can you manage the risk?”
Microsoft was quick to issue fixes to the four vulnerabilities in its September release of security updates.
The vulnerabilities put a spotlight on the risk to supply chains that open-source code represents, particularly for organizations using cloud computing services, Ohfeld wrote.
Further reading: Open Source Security: A Big Problem
OMI Agent at the Center of OMIGOD
With OMIGOD, the issue is a relatively unknown app called Open Management Infrastructure (OMI), which is embedded in many Azure services. Microsoft sponsors the open-source OMI project in collaboration with The Open Group. Ohfeld described OMI as Windows Management Infrastructure (WMI) for Unix and Linux systems and Linux is the dominant OS running in Azure.
Through OMI, organizations can collect statistics and sync configurations across their Azure environment and it’s used by such Azure services as Open Management Suite, Azure Insights and Azure Automation.
“When users enable any of these popular services, OMI is silently installed on their Virtual Machine, running at the highest privileges possible,” he wrote. “This happens without customers’ explicit consent or knowledge. Users simply click agree to log collection during setup and they have unknowingly opted in. Because Azure provides virtually no public documentation about OMI, most customers have never heard of it and are unaware that this attack surface exists in their environment.”
Remote Code Execution is Most Serious Flaw
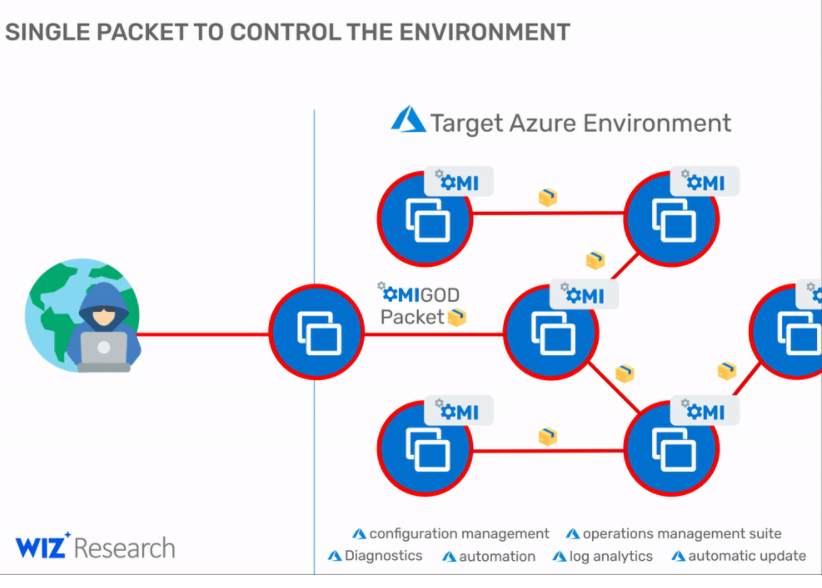
The OMI agent operates as a root with the highest privileges and any users can communicate with it using a Unix socket or through an HTTP API, when it’s configured to allow external access. The three vulnerabilities with privilege escalation capabilities would allow bad actors to gain control of the servers. However, the vulnerability with remote code execution is the most serious flaw where OMI ports are accessible to the internet.
“This vulnerability can be also used by attackers to obtain initial access to a target Azure environment and then move laterally within it,” Ohfeld wrote in another technical blog. “Thus, an exposed HTTPS port is a holy grail for malicious attackers. With one simple exploit they can get access to new targets, execute commands at the highest privileges and possibly spread to new target machines.”
Recorded Future noted that Microsoft addressed the bug by developing version 1.6.8.1 of the OMI client and releasing it on GitHub, but didn’t automatically install the update on OMI clients in its infrastructure, essentially leaving tens of thousands of servers vulnerable. The company also took three days to replace the OMI client version inside its Azure Linux VM images.
The cybersecurity firm said a query on the Shodan search engine found more than 15,600 Azure Linux servers connected to the internet.
Open Source Software is Safe if Not Misused
Wiz’s Ohfeld wrote that despite these vulnerabilities, open source software used by the community is vetted by thousands of experts and tends to be much more secure than proprietary software, though it can become a risk when misused.
“One of the benefits of open source is that it’s easy for developers to grab code from different projects and mix it with other open source and proprietary software,” he wrote. “As a result, bad open-source code can wind up in an enormous range of products and services – inadvertently becoming a ‘single point of failure.’ Because customers don’t know what franken-code is running in the background of the services they use, they remain at risk and unaware. “
Tyler Shields, chief marketing officer at security vendor JupiterOne, said finding such an underlying vulnerability in a management function of a cloud service provider is significant.
“To understand their exposure to this vulnerability, enterprises need to know which assets have the OMI management function enabled and ensure that nothing is directly exposed to the internet,” Shields told eSecurity Planet. “You may assume that two or three layers of firewalls protect these assets, but unfortunately, transitive trust relationships among assets can accidentally create a path that an attacker can exploit. A cloud-native attack-surface measurement tool that connects assets together in a relationship graph will tell you pretty quickly if any of those instances are actually exposed.”
Risk-Reward in Cloud Security
The OMIGOD scenario highlights the risk-reward tradeoff of cloud services, according to Yaniv Bar-Dayan, co-founder and CEO of cybersecurity firm Vulcan Cyber.
“IT security teams trust cloud providers like Azure to provide a secure service, and in the event of a bug or vulnerability, to take immediate steps to mitigate the risk,” Bar-Dayan told eSecurity Planet. “In almost all cases, the cloud providers we use remediate the vulnerabilities found in their services before they are exploited at scale. It typically takes a series of vulnerabilities to be left unaddressed by vendors and users for an advanced persistent threat to be successful.”
About 99 percent of cybersecurity breaches exploit a known and unmitigated vulnerability, he said. However, that doesn’t apply to cloud services because providers like Microsoft and Amazon Web Services (AWS) are highly proactive about ensuring their products are clear of cybersecurity issues.
“The real risk in cloud security stems from the fact that 95 percent of all cloud security breaches are due to user error and cloud service user misconfigurations,” he said. “We plead with enterprise consumers of cloud services to make the security of the services they consume a top priority and be as proactive as the cloud service providers in their never-ending mitigation efforts.”
Wiz’s Ohfeld noted that OMI is only one example of a relatively unknown software agent pre-installed and silently deployed in cloud environments and that these agents are in AWS and Google Cloud Platform as well as Azure.
“We hope to raise awareness of the risks that come with unknown agents running with high privileges in cloud environments, particularly among Azure customers who are currently at risk until they update to the latest version of OMI,” he wrote. “We urge the research community to continue to audit OMI and report issues they may find with similar agents.”
Further reading:








