Open source security has been a big focus of this week’s Black Hat conference, but no open source security initiative is bolder than the one proffered by the Open Source Security Foundation (OpenSSF).
Amid discussions on the security of open source technologies like eBPF and Hadoop, OpenSSF speakers Jennifer Fernick, SVP and head of global research at NCC Group, and Christopher Robinson, Intel’s director of security communications, outlined the group’s vision to secure open source software “end to end, at massive scale.”
OpenSSF was formed a year ago by the merger of Linux Foundation, GitHub and industry security groups. It has more than 50 members so far, from tech giants like IBM, HPE, Intel, Facebook, Google, Cisco, Microsoft, Huawei, Samsung and VMware, to small companies, open source-based companies like Red Hat, Suse and Canonical, and open source users like JP Morgan Chase, Comcast and Uber.
Open Source Software is at the Heart of Everything
Fernick and Robinson cited Sonatype research that FOSS (free and open source software) constitutes 80-90% of any piece of modern software (see chart below).
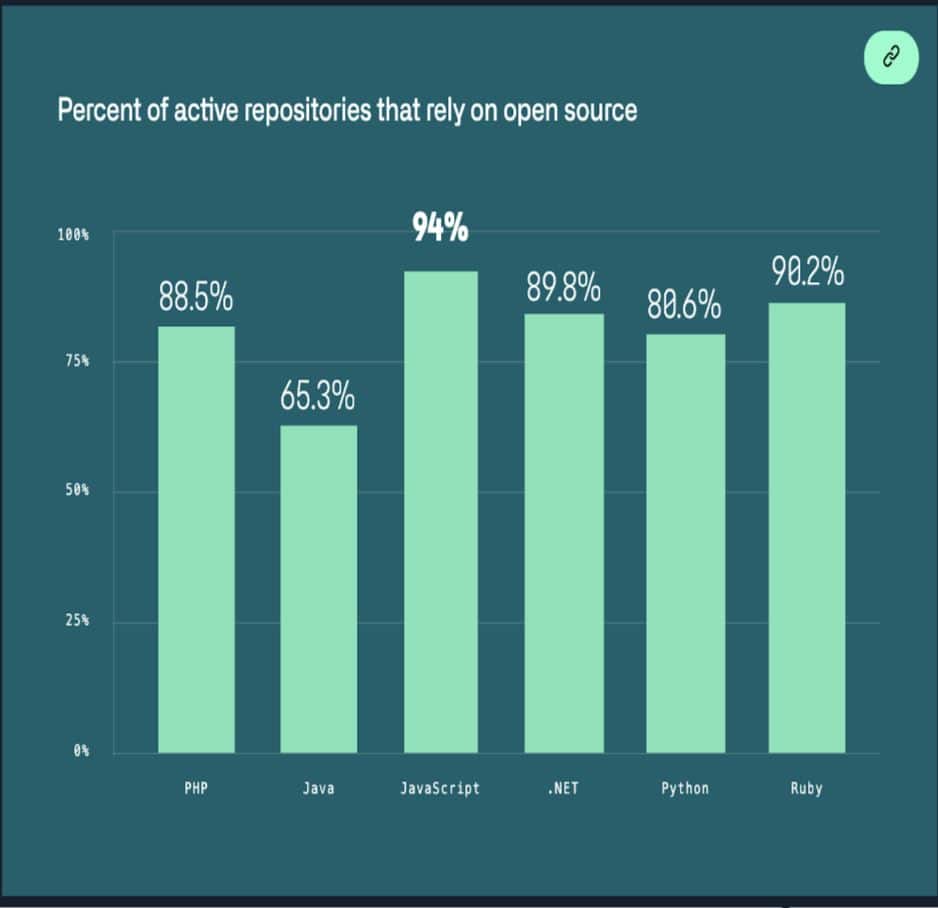
A Synopsis report found that 84% of these codebases had at least one vulnerability, with the average having 158 per codebase. Most OSS vulnerabilities are discovered in indirect dependencies (Snyk). A typical vulnerability can go undetected for 218 weeks, and on average takes 4 weeks to get resolved once the project is alerted to it (Octoverse).
At a time when the time between vulnerability disclosure and exploit creation has gone from 45 days to 3, “the number of vulnerabilities in the wild outpaces the speed at which the security community can patch or even identify them,” and automated attacks are quickly weaponizing even little-publicized flaws, Fernick said.
The distributed, public-facing nature of open source projects is one issue contributing to the security challenge, as can be limited project staffing. They noted that the Heartbleed OpenSSL vulnerability persisted for years in part because the project had just two full-time developers to develop and maintain 500,000 lines of code. Nearly 100,000 public web servers remained vulnerable five years later.
Robinson encouraged those who use open source software to help improve security by giving back.
“We all use the software,” he said. “Let’s all find ways to help improve it.”
Big Ambitions
OpenSSF plans to tackle the OSS security problem in a big way, with stated objectives like “prevent classes of bugs from being possible at all.”
The group wants to concentrate resources on securing the most critical libraries, components, and projects, a wise approach that should benefit everything using the same codebase, and a number of training, design, testing and vulnerability disclosure and patching projects are in the works. Robinsons also discussed OpenSSF’s reference architecture – see graphic below.
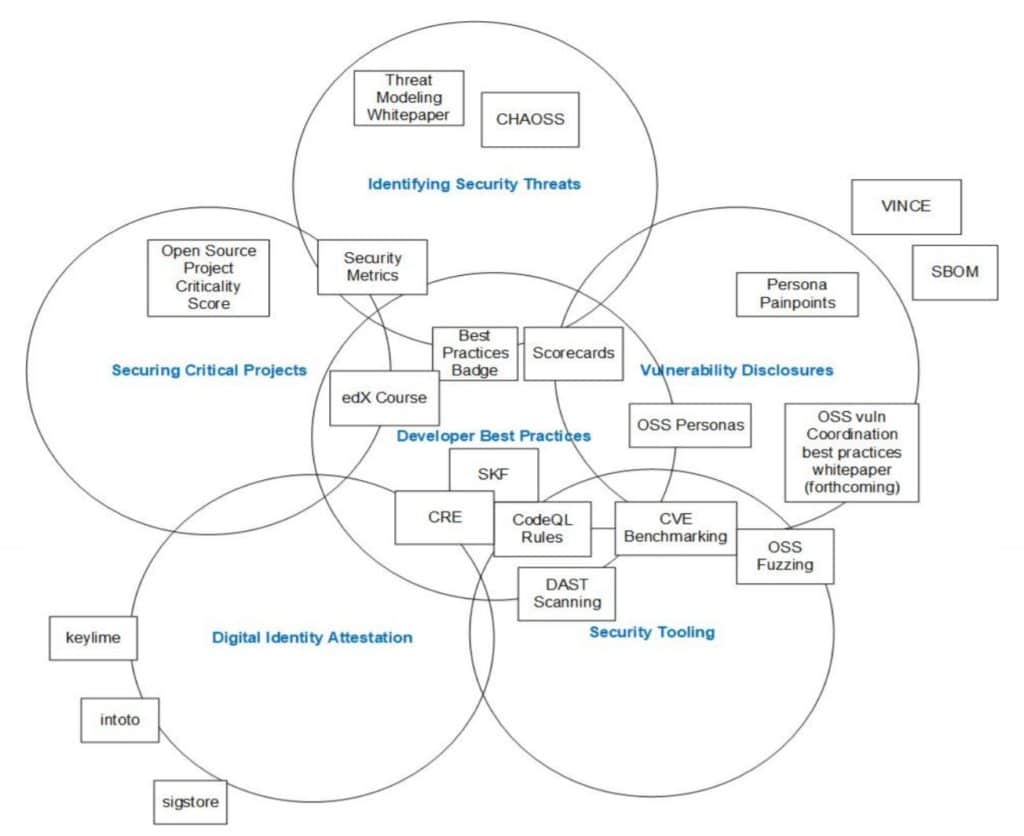
A number of successes so far include:
- Secure Software Development Fundamentals courses
- Security Scorecards
- Criticality Score
- Security metrics dashboard
- Security Reviews Initiative
- Security Metrics Initiative
- OWASP ZAP Baseline and Full scanning tools
- OpenSSF CVE Benchmark
- OWASP Security Knowledge Framework (SKF)
Big Data, eBPF Face Scrutiny
Weaknesses in Big Data tools and the eBPF kernel program and monitoring interface were among the open source tools in the spotlight at the conference.
In a presentation titled “The unbelievable insecurity of the big data stack,” Sheila Berta of Dreamlab Technologies discussed weaknesses in Apache Hadoop tools like the Zookeeper management layer and Ambari cluster management.
Datadog researchers might have best summed up the attitude toward eBPF’s kernel access by asking, “With friends like eBPF, who needs enemies?”
The conference also included a number of open source security tools that can be used to shore up security.
Microsoft Gets Attention Too, Of Course
Linux hardly got all the attention at the conference, of course. Microsoft got plenty, including architecture-level vulnerabilities in Microsoft Exchange, along with significant flaws in Active Directory and Microsoft 365. AWS and DNS-as-a-Service providers got their time in the spotlight too.
Further reading: Top Vulnerability Management Tools








