The U.S. National Security Agency (NSA) released comprehensive network security guidance on March 3, on the same day that the Cybersecurity and Infrastructure Security Agency (CISA) released its longest-ever list of exploited vulnerabilities.
With organizations around the world on heightened alert in the wake of Russia’s unprovoked war against Ukraine, government agencies have stepped up efforts too. The U.S. Senate has also been active, passing the “Strengthening America Cybersecurity Act,” which requires critical infrastructure owners to report cyber attacks within 72 hours and ransomware payments within 24. The legislation must still be approved by the House.
The 95 vulnerabilities added to CISA’s Known Exploited Vulnerabilities Catalog (sort by date) are by far the most yet, growing the list to 478.
Among the latest additions are:
- Cisco Small Business RV routers and IOS software (38 new Cisco vulnerabilities in all)
- Privilege and other vulnerabilities in Microsoft Windows, Exchange Server, Excel, Office, PowerPoint, Malware Protection Engine, Internet Explorer and more (27 in all)
- The Linux Kernel and Apache Tomcat
- Oracle Java SE and VirtualBox
CISA urges organizations to prioritize fixes identified in the Catalog, a priority also included in the recent Shields Up guidance outlining steps to take to prepare for any Russian cyberattacks that might occur as a fallout from the war.
Also read: Top Vulnerability Management Tools
Segmentation Figures Prominently in NSA Guidance
SANS Institute officials have been active lately with network security advice in response to the war in Ukraine, and some of that advice has sparked considerable interest among cybersecurity pros.
The NSA’s 58-page Network Infrastructure Security Guidance (PDF) is more of a catalog of network security best practices, based on principles of zero trust and segmentation, following up on brief January guidance (PDF) on segmentation that discussed the Purdue Enterprise Reference Architecture (image below).
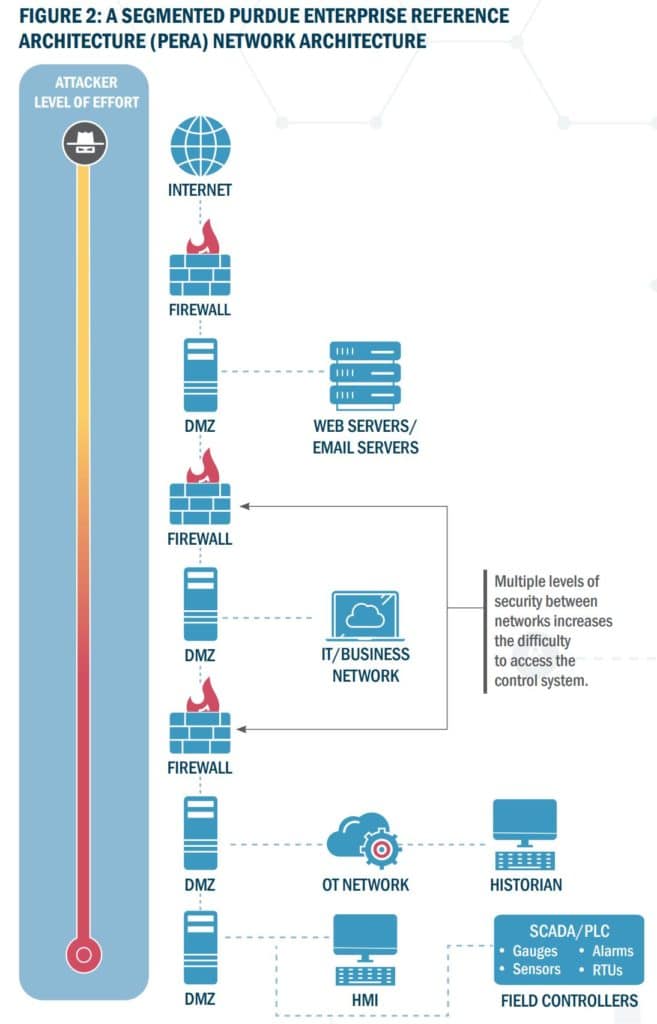
The new guidance is significantly more comprehensive and in-depth, addressing network architecture, maintenance, authentication, routing, ports, remote logging, monitoring and administration. Here’s some of the advice detailed in the document.
Network Architecture and Design
The network architecture outlined in the document is based on zero trust principles, but the NSA noted that it’s intended not so much for building new networks as it is for mitigating “common vulnerabilities and weaknesses on existing networks. As system owners introduce new network designs intended to achieve more mature Zero Trust principles, this guidance may need to be modified.” Architecture recommendations include:
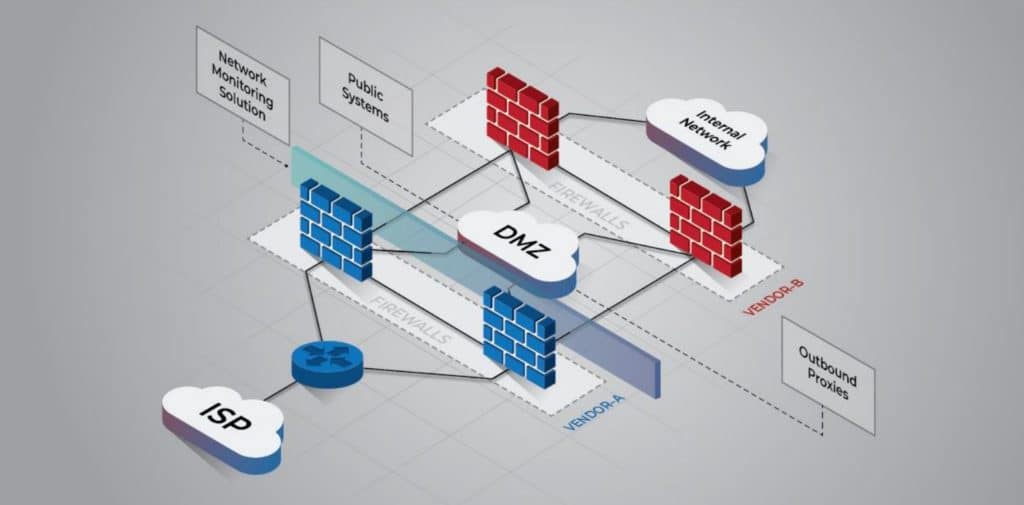
- Install a border router to facilitate a connection to the external network, such as an Internet service provider (ISP)
- Implement multiple layers of next-generation firewalls throughout the network to restrict inbound traffic, restrict outbound traffic, and examine all internal activity between disparate network regions
- Each layer should utilize different vendors to protect against an adversary exploiting the same unpatched vulnerability in an attempt to access the internal network
- Place publicly accessible systems and outbound proxies in between the firewall layers in one or more demilitarized zone (DMZ) subnets, where access can be appropriately controlled between external devices, DMZ devices, and internal systems
- Implement a network monitoring solution to log and track inbound and outbound traffic, such as a network intrusion detection system (NIDS), a traffic inspector, or a full-packet capture device
- Deploy multiple dedicated remote log servers to enable activity correlation among devices and detection of lateral movement
- Implement redundant devices in core areas to ensure availability, which can be load-balanced to increase network throughput and decrease latency
- Group similar network systems
- Remove backdoor connections
- Implement strict perimeter access control and NAC
- Limit and encrypt VPNs
Also read: Top Microsegmentation Tools
Network Operation and Management
Network operations and management make up the bulk of the report. Recommendations include:
- Verify the integrity of operating system files
- Implement patching and vulnerability management
- Use proper file system and boot management
- Use centralized authentication, authorization, and accounting (AAA) servers to manage administrative access to devices
- Apply least privilege principles
- Limit authentication attempts
- Change default passwords and remove unnecessary accounts
- Store passwords with secure algorithms
- Implement remote logging and monitoring
- For remote admin and network services, disable clear text administration services, use adequate encryption and secure protocols (TLS 1.2 or higher), use timeouts and TCP keep-alive, and disable outbound connections, unnecessary services and discovery protocols
- Disable IP source routing and enable unicast reverse-path forwarding (uRPF) and routing authentication
- Disable dynamic trunking and default VLAN, unused ports, port monitoring and proxy address resolution protocol (ARP), and enable port security
Read next: Best Network Monitoring Tools








