A SaaS security company says a spike in cyber attacks from Russia and China in recent weeks suggests the two countries may be coordinating their cyber efforts.
SaaS Alerts, which helps managed service providers (MSPs) manage and protect customers’ SaaS apps, mentioned the finding in conjunction with the release of its annual SaaS Application Security Insights (SASI) report.
“Over the last several weeks, SaaS Alerts has seen a sharp rise in activity from countries with consistently high levels of both attempted and successful attacks originating within their borders — Russia and China,” the company said in a statement. “The vast volumes of data analyzed suggests these countries may even be coordinating attack efforts. Per analysis available from SaaS Alerts, attack trend lines that compare Russia and China show almost the exact same pattern.”
eSecurity Planet checked with some well-known threat intelligence services, and while they didn’t conclude that the attacks are coordinated, they confirm that China has increased cyber activities in Ukraine and Europe.
Ben Read, Mandiant’s Director of Intelligence Analysis, told eSecurity Planet that “we’ve seen similar activity to Google with China targeting Europe/Ukraine, but no indication it’s coordinated with Russia.”
The Google threat landscape update issued yesterday notes that Mustang Panda or Temp.Hex, a China-based threat actor, targeted European entities with lures related to the Ukrainian invasion, such as malicious attachments with file names like ‘Situation at the EU borders with Ukraine.zip’. Contained within the zip file is an executable of the same name that is a basic downloader that when executed, downloads several additional files that load the final payload, Google said.
“Targeting of European organizations has represented a shift from Mustang Panda’s regularly observed Southeast Asian targets,” Google said.
The surge in cyber activity reported by SaaS Alerts and others coincides with the build-up to Russia’s unprovoked attack against Ukraine, and yesterday Resecurity Inc. reported that hackers – some linked to Russian GRU military intelligence – breached computers at nearly two dozen U.S. liquified natural gas (LNG) companies and the FBI reported that Russia-connected Ragnar Locker ransomware had hit at least 52 critical infrastructure companies as of January.
U.S. security agencies have issued a number of alerts on critical security infrastructure protection in recent months, including a network security framework released just last week (see U.S. Security Agencies Release Network Security, Vulnerability Guidance).
SaaS Apps Under Attack
With the average number of SaaS apps at 89 per organization, according to Okta, those apps have become one of the most critical cybersecurity challenges – and the SaaS Alerts report underscores how vulnerable they are.
In its report, SaaS Alerts said it analyzed 136 million SaaS security events in 2021 and found that the most successful unauthorized logins originated from Russia, with China, Vietnam, Korea and Brazil the next biggest sources (see chart below). These attacks – using valid credentials – are hard to detect without behavioral monitoring and geographical whitelisting, the report said.
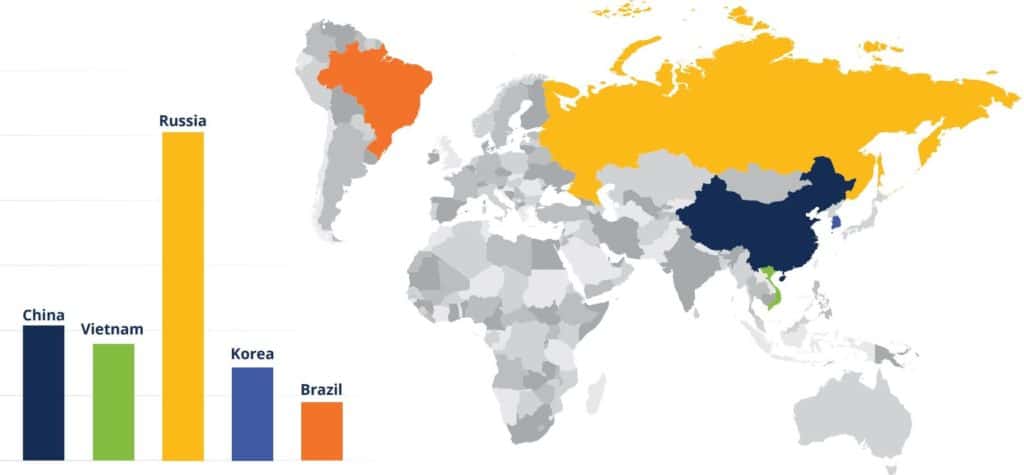
While some of those attacks may be state-sponsored, many are less sophisticated hackers who are finding it easier to acquire skills. And some governments – most notably Russia – have allowed cyber criminal groups to operate within their country in exchange for cooperation and promises not to attack the host country. Ragnar Locker, for example, terminates when it encounters a machine in former USSR countries.
There were about 10,000 brute force attacks against nearly 130,000 MSP user accounts monitored by SaaS Alerts, so determined cybercriminals have multiple ways to compromise target accounts. Account credentials have also been used to connect to third-party applications, which can result in data and account information being shared between SaaS apps.
“Users often establish these connections for convenience without consideration to potential security violations,” the report noted.
SaaS Alerts looked at more than 2,000 SMBs, and because the company’s platform is only available through the MSP channel, the data is specifically focused on SMBs who are served by MSPs.
Also read: Best Network Monitoring Tools
Most Common Critical Alerts
The report found that the three most common critical SaaS alerts are geographical violations, third-party app connections, and multiple account lockouts (image below).
The most common critical alert, “User Location: outside approved location,” is when there’s a successful login to a user account from outside an approved location or IP address range. While sometimes a false flag due to misconfiguration of approved locations or unexpected user travel, it nonetheless indicates a significant probability that a malicious actor has succeeded in compromising an account, the report said.
The “SaaS Integration Alert” indicates that the account credentials have been used to connect to a third-party application, which may lead to data and other account information sharing between SaaS apps.
“Multiple Account Lockouts” refers to accounts that are locked out four or more times in a 12-hour period. For an account to be locked means that “malicious actors have succeeded in validating a correct account name, and are actively (typically programmatically) trying password combinations to gain access to the account,” the report said.

Also read: Best Third-Party Risk Management (TPRM) Tools
Guest Accounts, File Sharing Are Risks
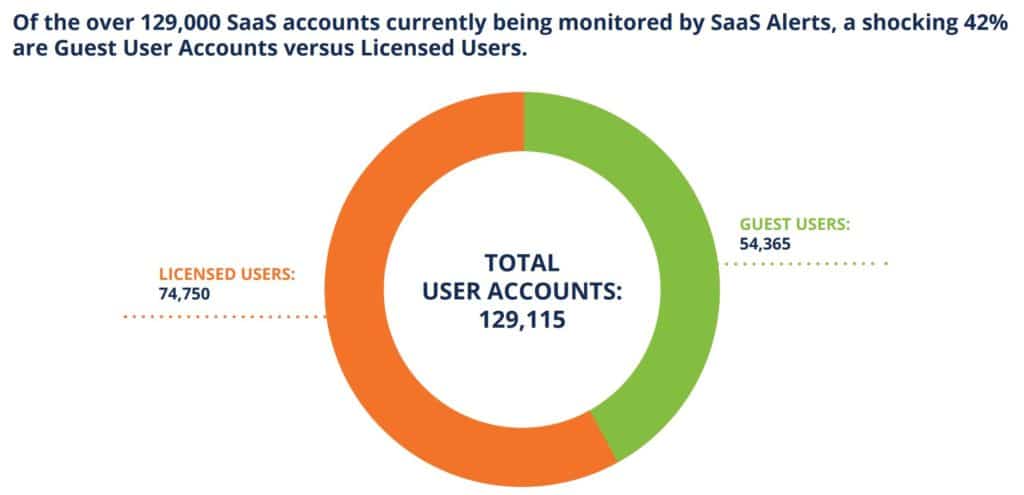
Other common vulnerabilities include guest user accounts – the report found that 42% of monitored accounts were guest accounts – and file-sharing activity.
Organizations must set up guest accounts with the minimum required access and permissions and to continuously monitor the activity of these accounts and disable unused guest accounts once they have finished their intended use, SaaS Alerts said.
Companies should also monitor SaaS file-sharing activity “to determine whether or not users are effectively and safely using document creation and file-sharing,” the report said. “End users should be trained to ensure they terminate ‘old’ share links in order to maintain proper security hygiene and mitigate risk.”
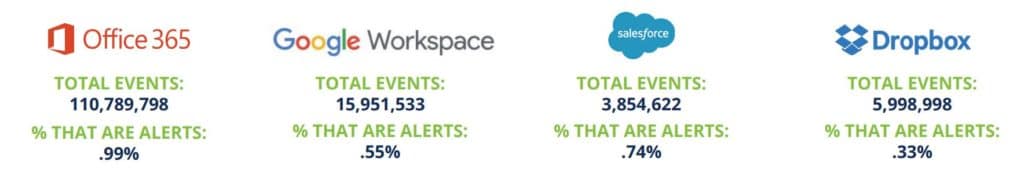
Office 365 the Most Attacked App
Not surprising given its size, Office 365 kept security pros busy, with more than 110 million events, about 1% of which triggered alerts. Google Workspace, Salesforce and Dropbox were next in terms of security activity (image below).
Read next: Top Vulnerability Management Tools








