Security service edge (SSE) is a security technology that secures access to assets outside of the corporate network. SSE works by extending security to cover the dispersed threat landscape where websites, cloud assets, and many employees operate outside of the traditional firewall protection. To fully explain SSE, I’ll cover its key features, benefits, challenges, use cases, vendors, and trends as well as contrast SSE against alternative solutions.
Table of Contents
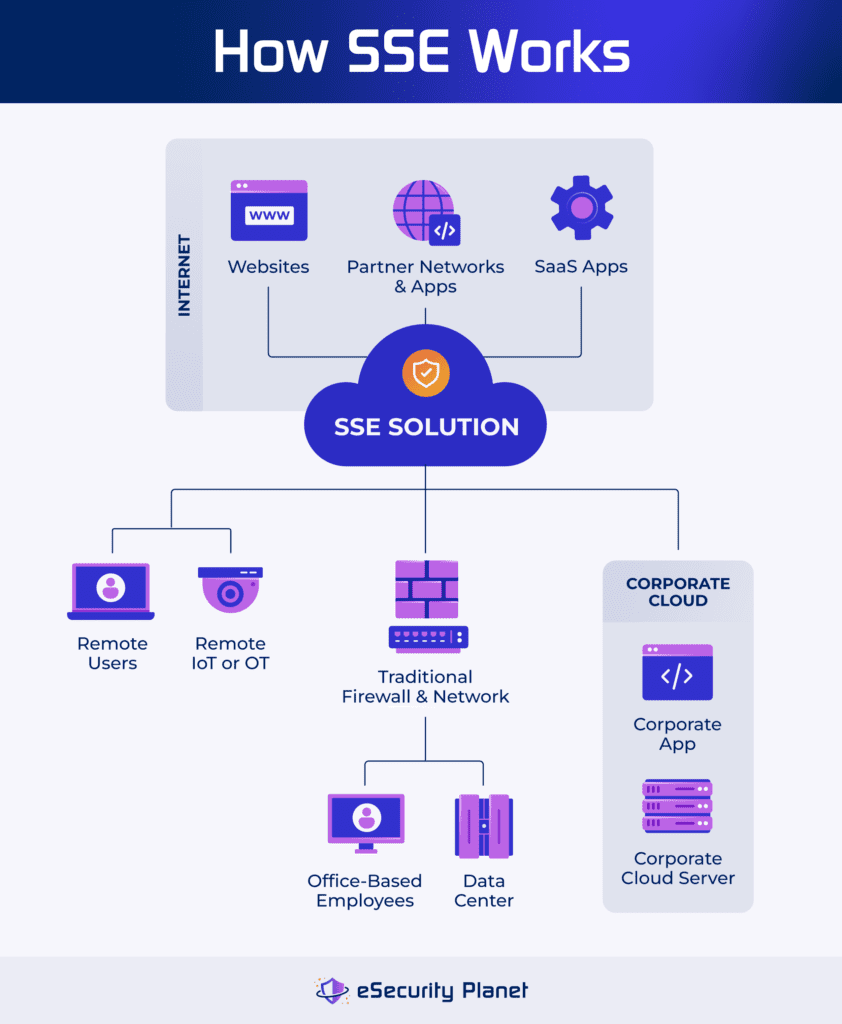
How Does SSE Work?
Security service edge introduces a control that connects to remote users and assets before they connect to each other. It solves the problem organizations experience in a modern IT environment where many users and assets reside outside of the protected corporate network.
Some organizations use virtual private networks (VPNs) to pull remote user access within the network, but these solutions cause huge bottlenecks and some users will bypass the VPN to access software-as-a-service (SaaS) and third-party websites. All SSE tools borrow from network security concepts to isolate communication within an envelope of protection and many introduce the granular security controls of zero trust as well.
5 Key Components & Capabilities of SSE
An integrated SSE tool needs to include capabilities for access control, acceptable use, data security, security monitoring, and threat protection. Additionally, SSE should integrate with other operations and security controls to enable connections to data centers, cloud resources, local networks, websites, and both in-house and third-party apps.
Access Control
Access controls validate user credentials, authorize access to specific assets, and block unauthorized devices, users, and access requests. The solution must also control access to external SaaS apps and third-party website access. Typical identity access management (IAM) tools won’t provide enough protection for cloud resources.
More robust solutions, such as a cloud access security broker (CASB), enterprise VPNs, or zero-trust network access (ZTNA), need to be used to ensure that remote users use the tool to access remote assets. Some SSEs will even check device posture and check for missing patches as part of additional network access control (NAC) features.
Acceptable Use
Within a local network, acceptable use of IT security policies needs to be enforced to prevent users from visiting unacceptable websites or misusing data. As with access control, traditional solutions generally can’t sufficiently protect SaaS app data, cloud resources, and direct website access for remote users.
SSEs combine CASB, secure web gateway (SWG), and user and entity behavior analytics (UEBA) capabilities. Combined, these controls monitor and block unacceptable access or use for all assets, applications, and websites.
Data Security & Threat Protection
Data security must protect incoming and outcoming data flows against leak or attack with equivalent protection to internal network firewall and network monitoring. SSE tools will often deploy a cloud-hosted firewall-as-a-service (FWaaS) as the fundamental tool to decrypt and examine traffic flows to block threats. SWG capabilities can also screen IP addresses and websites to protect against known-malicious sites.
Some SSEs add further protection to the endpoint through remote browser isolation (RBI) that maintains all work within the browser application to prevent data exfiltration and minimize malware access to the endpoint. Even more information security can also be applied through data loss protection (DLP) capabilities that track sensitive or secret data use.
Security Monitoring
The internal network intrusion detection and prevention systems (IDPS) don’t extend beyond the firewall, but traffic still needs monitoring to capture signs of attack on remote assets. Secure service edge tools use the FWaaS scanning to capture many signs of attack and can use CASB capabilities to scan SaaS data used to complement the firewall scanning. Some tools even use cloud security posture management (CSPM) capabilities to monitor cloud infrastructure.
Security Stack Integration
SSE tools provide strong security but must integrate with other systems to provide more comprehensive network security and protection for the organization overall. Common integrations needed include:
- Identity and access management (IAM): Connects identities and permissions to the SSE tool for appropriate access level grants and group authorizations.
- Managed detection and response (MDR): Provides security monitoring for the organization as a whole including local networks and the SSE environment.
- Software-defined wide area network (SD-WAN): Creates the interlink connections and microsegmentation to segregate assets or connect internal assets to the SSE.
- Security information and event management (SIEM): Captures activity logs for security review and potential event investigation.
- Security orchestration, automation, and response (SOAR): Automates some incident response and prioritizes alerts and threat intelligence for security analysts.
- Threat intelligence platforms: Consolidates vulnerability news, malware changes, and attack trends to inform security teams and security tools for improved response.
Connectors can be explicit and tailored for common solutions, but others will require using standardized application programming interfaces (APIs).
Primary Benefits of SSE
Secure service edge tools directly address the security and operations problems created by attempting to secure remote users and assets. Adopting SSE will reduce complexity, secure remote assets, and improve remote security, network traffic, and visibility into user behavior.
Improved Remote Security
Remote users often bypass VPN security to directly access cloud apps such as Office 365 and Salesforce or to browse the web. These direct connections lack security controls to adequately defend against viruses and prevent endpoint infections. SSE introduces additional cloud-based and scalable security controls to improve remote user security with minimal disruption.
Improved Network Traffic Performance
Traditional solutions use VPNs to route traffic within the corporate network only to send many connections right back out to the internet. Additionally, the traffic will be subject to network firewall and other security inspections for each traversal. SSE eliminates these bandwidth-wasting practices to improve performance and user experience.
Reduced Security Tool Complexity
A number of tools can replicate SSE capabilities for teams with the expertise and capability to perform the complex integration and installation. However, most will choose to benefit from an integrated SSE that consolidates the capabilities under a single management pane with dramatically less complicated integration and installation requirements.
Secure Access to All Assets
Traditional network security can only secure traffic rerouted into the local network using VPNs, so many users directly connect to SaaS apps and websites without sufficient protection. SSE extends security to all users, Internet of Things (IoT), operations technology (OT), cloud assets, and applications that reside outside of the internal network.
Visibility & Control of User Activities
Traditional security can’t track or monitor remote users that bypass VPN controls, which allows malicious insiders or users with stolen credentials to access or potentially exfiltrate sensitive data from remote assets (SaaS applications, cloud databases, etc.). SSE introduces full visibility into user behavior to detect and control unauthorized behavior.
Common Challenges of SSE
SSE provides distinct benefits to protect remote users. Yet the technology still introduces challenges that affect adoption or successful implementation.
- Integration difficulties: Some existing communications and security tools may lack support from specific SSE tools and require additional integration efforts or workarounds.
- Legacy architecture issues: SSE performs security in a dramatically different fashion for improved efficiency, but forcing SSE processes into legacy network architecture or security processes will introduce delays and performance issues.
- SSE adaptation struggles: New technology requires review and heavy modification of policies and procedures developed for traditional security tools to cover SSE capabilities; may potentially need entirely new incident response plans and processes.
- Third-party packet inspection: Cloud-based SSE providers perform data inspection to protect against malware and malicious insider data use, which technically can expose secrets to third parties; this might be unacceptable and require modification.
- User resistance: SSE introduces new security controls where none previously existed, which may cause user complaints and other issues during implementation and training.
5 SSE Use Cases & Applications
The primary use case for SSE is to protect the remote users and assets outside of the network. However, what this means exactly will vary dramatically from organization to organization. To make this concept more tangible, consider the following five specific use cases incorporating video editing, international shipping, medical, human resources, and sales reps.
Break VPN Logjams
A large number of remote users at a video editing company still use VPN connections to access video editing suites that have moved to the cloud. The high-bandwidth video streaming requirements now pass through security and through the company’s VPN structure multiple times crushing bandwidth and performance. SSE adoption eliminates the VPN logjam to make direct connections that require less inspection to dramatically improve performance.
Global OT Monitoring
A fleet of transport ships will deploy a large number of sensors to monitor engines and other systems but lack the IT talent to maintain local networks. Deploying SSE enables secure connections between world-wide OT deployments, the cloud-based monitoring applications, and data lakes for sensor data storage.
Improved Medical Professional Experience
Doctors and nurses rush to address patients’ needs in a medical center, which makes them prone to forgetting login credentials or phishing attacks. Implementing SSE can enable single-sign-on experiences that eliminate login requirements and add security protection to block additional malware exposure. This improves the experience and security when checking Office 365 emails or accessing remote resources for medical imaging, billing, or messages.
Safer Resume Screening
Telling employees not to click on attachments to avoid malware doesn’t work for human resources professionals who must open and evaluate resume attachments as part of their job. An SSE deployment with remote browser isolation protects remote-work HR professionals with a sandboxed environment in their browser to open and evaluate PDF files and other attachments safely and securely.
Secure Remote SaaS Users
Sales reps need access to Salesforce, Box, and other SaaS tools to manage leads and distribute sales materials securely. To protect against unauthorized access using stolen credentials or unauthorized download of leads by quitting sales reps, SSE can be implemented to protect the reps, secure the SaaS resources, and block unauthorized use.
Top SSE Solution Options
For those considering an SSE tool, start with the top-ranked vendors in Gartner’s Magic Quadrant for Security Service Edge:
- Fortinet: The only vendor in the Challenger quadrant, FortiSASE also includes SD-WAN and builds off of their next-generation firewalls for strong packet filtering.
- Lookout: This cloud security provider in the Visionary quadrant focuses on data protection and claims a 60 minute or less deployment.
- Netskope: Using a private cloud network in 70+ regions, Netskope claims a spot in the Leader quadrant with strong operations capabilities for ZTNA.
- Palo Alto Networks: Strong security performance for ZTNA and firewall capabilities earn Prisma SASE (includes SD-WAN) a Leader quadrant position for SSE.
- Skyhigh Security: Remote browser isolation and data loss protection included in their SSE secure data effectively and earn Skyhigh a spot in the SSE Visionary quadrant.
- Zscaler: Their cloud-first architecture and built-in zero-trust capabilities for a wide variety of assets earn ZScaler a position in the Leaders quadrant for SSE.
While there is some overlap between secure access service edge (SASE) and SSE tools, many quality SSE tools will not qualify under SASE because they lack full SD-WAN integration.
Difference Between SSE, SASE & VPNs
SSE, SASE, and VPNs all manage remote access using different techniques and network security architectures. SASE essentially integrates SD-WAN capabilities into SSE to add additional network segmentation and operations capabilities such as quality of services (QoS). SASE vendors offer more capabilities but will also require more setup, network equipment, and possibly migration time to reproduce network connections.
Traditional VPNs route all traffic through the local network to use traditional network security controls to protect remote users and assets, but often suffer scalability problems and both network and internet connection bandwidth issues. Enterprise VPN addresses scalability and bandwidth problems through cloud-based gateways and access points but lacks the full SSE or SASE capabilities to secure remote applications and cloud infrastructure.
Key SSE Future Trends
Buyers can expect their own needs for service secure edge to change as the security standards, industry regulations, and the SSE tools themselves evolve. Look for changes to the market to center around tool adoption, expanding requirements, and improved support in addition to increased SSE capabilities.
Adoption Motivated by Security & Operations Advantages
SSE introduces additional agility, scalability, and operations improvements for organizations even as the need to secure remote users and assets continues to increase and add pressure to security and operations teams. These advantages and trends will drive increased deployments for organizations of all sizes.
Blurred Product Definitions
SSEs and VPNs once represented very distinct and different solutions. However, as enterprise VPNs and firewall providers continue to add additional SWG, CASB, and UEBA features to their products, the distinctions will blur as capabilities become similar. In the future, buyers will focus on implementation, integration, and price models as top distinguishing aspects.
Expanded Service Provider Support
Managed service providers (MSPs) will reflect the needs of their customers and continue to expand support for SSE integration and ongoing management. The current cloud-based providers already provide multi-tenant capabilities and service providers will discover opportunities to support customers as they add more and more users and assets to the SSE umbrella of protection.
Increased Connectivity Requirements
As more IoT and OT become connected through traditional and mobile (5G, etc.) networks, SSE tools will need to expand capabilities to integrate protection for an increasingly diverse array of endpoints. Future endpoints should include sensors, security cameras, radio frequency identification (RFID) sensors, and much more.
Advanced Zero Trust Features
Currently, vendors with zero trust network access (ZTNA) promote it as a basic component of SSE. As Zero Trust becomes more defined by regulation and adoption of zero trust improves, vendors will apply zero trust principles to other aspects of the SSE tool, such as identity and website access, to further enhance security.
Bottom Line: SSE Locks Down the Modern Network
Secure service edge more than replaces traditional VPN security for remote users. SSE encompasses the remote IoT devices, cloud infrastructure, and SaaS apps that operate beyond normal VPN protection in our modern IT infrastructure. If it’s time to secure your remote assets, schedule a demo with a couple of top SSE candidates to learn how this solution can secure your architecture.
For those that only need to secure remote users, consider a more basic approach and read about VDI vs VPN vs RDP.








