Underground services are cropping up that are designed to enable bad actors to intercept one-time passwords (OTPs), which are widely used in two-factor authentication programs whose purpose is to better protect customers’ online accounts.
By using the services, cybercriminals can gain access to victims’ accounts to steal money. Security expert Chris Krebs wrote in a blog post this week that he discovered such a service – called OPT Agency – earlier this year, noting that the service was shut down soon after his report was published.
However, researchers at threat intelligence firm Intel 471 in a report this week said they have seen a rise in these services, enabling attackers to target everything from bank accounts to social media platforms. The services have been operational since June and either operate through a bot on the cloud-based instant messaging system Telegram or by providing support to bad actors via a Telegram channel.
“Over the past few months, we’ve seen actors provide access to services that call victims, appear as a legitimate call from a specific bank and deceive victims into typing an OTP or other verification code into a mobile phone in order to capture and deliver the codes to the operator,” the Intel 471 researchers wrote. “Some services also target other popular social media platforms or financial services, providing email phishing and SIM swapping capabilities.”
OTP Interception Services Emerge
They added that in the Telegram support channels, bad actors using the services “often share their success while using the bot, often walking away with thousands of dollars from victim accounts.”
A wide range of websites are requiring users to not only type in a password to get onto the site, but also to type in a numeric code or OTP token that is sent via a text message. In addition, Google (with Google Authenticator) and Authy offer mobile apps that generate such numbers and are used by the website and user.
The goal is to strengthen the security of the websites and their customer accounts by adding another layer of protection by requiring the code or OTP token.
However, Intel 471 researchers found that a number of new OTP interception services have emerged over the last few months, with slight differences in the way they work but all with a common endgame. They’re also part of a larger trend toward offering services – such as ransomware-as-a-service (RaaS) – that make it easier for even low-skilled cybercriminals to launch attacks.
“The ease by which attackers can use these bots cannot be understated,” they wrote. “While there’s some programming ability needed to create the bots, a bot user only needs to spend money to access the bot, obtain a phone number for a target, and then click a few buttons.”
Stealing Credentials
Despite the relative newness of the services, the news of their rise didn’t surprise Brian Uffelman, vice president and security evangelist at cybersecurity firm PerimeterX.
“Cybercriminals are finding every means possible to leverage weaknesses in human behavior for financial gain,” Uffelman told eSecurity Planet. “Stolen credentials, like OTPs, can be used for credential stuffing and ATO [account takeover] attacks, which can steal value, whether that is in the form of gift cards, credit card numbers, loyalty points or false purchases. ATO attacks are a major threat to any business and all of this just creates more fuel to feed the ATO attack fire. It is much simpler and lucrative to walk in through the front door of a digital business with valid, stolen credentials than to look for holes in an organization’s cybersecurity defenses.”
How OTP Bots Work
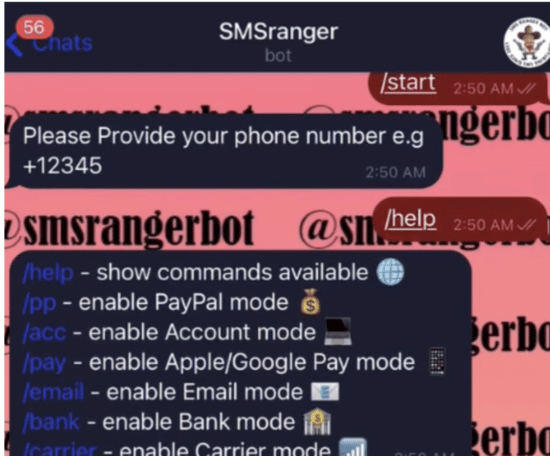
Intel 471 researchers said one bot, called SMSRanger, is easy for bad actors to use. They pay for access to the bot and can use it by entering commands similar to those used on Slack’s workforce collaboration tool. Users can enter a simple slash command to enable different scripts aimed at services – called “modes” – that can target specific bands, a wireless carrier and payment apps like PayPal, Apple Pay and Google Pay.
“Once a target’s phone number has been entered, the bot does the rest of the work, ultimately granting access to whatever account has been targeted,” the researchers wrote. “Users claim that SMSRanger has an efficacy rate of about 80% if the victim answered the call and the full information (fullz) the user provided was accurate and updated.”
BloodOTPbot, another bot, includes the ability to send victims a fake OTP code through SMS. To do this, an attacker needs to spoof the victim’s phone number and impersonate a bank or company representative and then the bot would try to call the victim, using social engineering techniques to get ahold of a verification code.
“The [bot’s] operator would receive a notification from the bot during the call specifying when to request the OTP during the authentication process,” they wrote. “The bot would text the code to the operator once the victim received the OTP and entered it on the phone’s keyboard.”
Attackers using the bot need to pay a $300 monthly fee to obtain the authentication code required to operate the bot. At the same time, they also could pay another $20 to $100 for live phishing panels that target accounts on social media networks like Facebook, Instagram and Snapchat, as well as financial services like PayPal and Venmo, investment app Robinhood and the Coinbase cryptocurrency marketplace.
A third bot, dubbed SMS Buster, is more difficult for bad actors to use. Users are given options for disguising a call so it appears to be a real contact from a specific bank even as attackers dial from any phone number. The caller then follows a script to get the victim to provide sensitive information, like an ATM PIN, OTP and a card verification value (CVV). That can then be sent to a person’s Telegram account.
SMS Buster has been used against Canadian victims, giving bad actors the ability to launch an attack in English or French. So far, Intel 471 researchers found accounts illegally accessed at eight Canadian-based banks.
Phishing, Social Engineering are Still Problems
The methods of attack may be relatively new, but they rely on the time-tested practice of social engineering, according to Nicolas Malbranche, senior product manager at ID management company Axiad.
“At the core of this issue is phishing, showing yet again how phishing threats are on the rise,” Malbranche told eSecurity Planet. “Even if your organization is up to date with the latest anti-malware software, it’s impossible to protect your employees from every potential business email compromise like this. That’s why it’s important to prioritize security training for all your employees and teach them best practices on how to spot and report phishing. Without employee education, issues like this will continue to impact businesses.”
The bot services also illustrate how some forms of two-factor authentication can still carry risks, the Intel 471 researchers wrote.
“While SMS- and phone-call-based OTP services are better than nothing, criminals have found ways to socially engineer their way around the safeguards,” they wrote. “More robust forms of 2FA — including Time-Based One Time Password (TOTP) codes from authentication apps, push-notification-based codes or a FIDO security key — provide a greater degree of security than SMS or phone-call-based options.”
Further reading:








