Cybercriminals are using Salesforce’s mass email service to dupe people into handing over credit card numbers, credentials and other personal information in a novel phishing campaign that highlights the threats to corporate networks that can come from whitelisted email addresses.
According to a recent blog post from email security service provider Perception Point, the bad actors are sending phishing emails via the Salesforce email service by impersonating the Israel Postal Service in a campaign that has targeted multiple Israeli organizations.
In the blog post, Perception Point cybersecurity analysts Miri Slavoutsky and Shai Golderman wrote that this is the first time they had seen attackers abuse Salesforce services for malicious purposes.
“Mass Email gives users the option to send an individual, personalized email to each recipient, thus creating the perception of receiving a unique email, created especially for you,” Slavoutsky and Golderman wrote. “Spoofing attempts of Salesforce are nothing new to us. Attackers spoof emails from Salesforce for credential theft, is a typical example. In this case, the attackers actually purchased and abused the service; knowing that most companies use this service as part of their business, and therefore have it whitelisted and even allowed in their SPF records.”
Whitelisting Increases Vulnerability
Therein lies a key issue raised by the phishing campaign. Most email security services are unable to detect attacks using Salesforce’s legitimate platform because they “blindly trust that Salesforce is a safe source,” even to the point of whitelisting the service’s IP addresses to streamline the email process, they wrote.
“While Salesforce’s recommendation is to whitelist their entire IP range, this creates a vulnerability in your company’s network,” the Perception Point analysts wrote. “Creating this type of whitelist is essentially ignoring the fact that the platform might be used for malicious purposes. By creating such a whitelist, one is basically creating a hole in one’s organizational security that such emails can sail straight through. When users receive such emails, they are unable to distinguish that the email was sent via a Mass Email platform.”
Shlomi Levin, Perception Point’s co-founder and CTO, told eSecurity Planet that given how whitelisting a trusted source can result in security breaches, “it is essential to employ a zero-trust attitude combined with a strong filtering mechanism to any content that enters the organization no matter the source: email, collaboration tools or Instant Messaging.”
Spoofing Salesforce
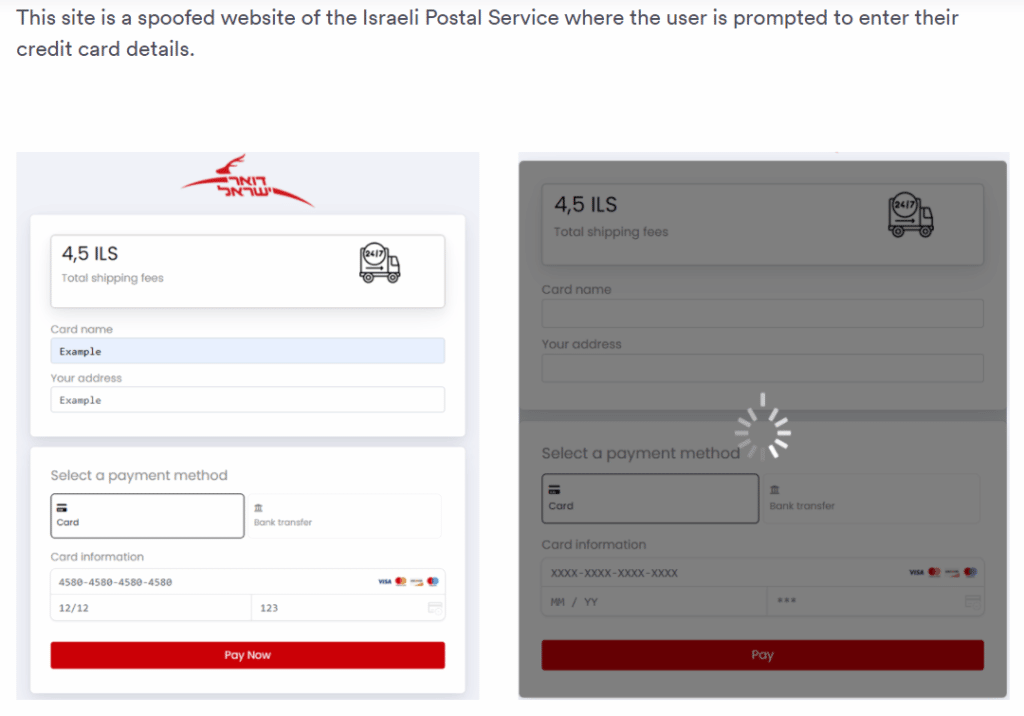
In this case, bad actors sent the victims email via the Salesforce email service purportedly from the Israeli Postal Service, telling the recipient that a package had been held up because the shipping fees hadn’t been paid. The email was sent from what Perception Point said is the standard sender of all salesforce.com emails.
The phishing email contains a link automatically redirecting the victim to a spoofed website of the Israeli Postal Service that prompts the user to enter credit card details. The user is then redirected to another page, which requires verification through an SMS code.
The Perception Point analysts said the attackers made an effort to prove the legitimacy of the emails, an indication of how far they will go to convince victims to give up their information and how easy it is to do just that. Researchers found that the malicious server running the website was accessible without any authentication and was developed and hosted by LiteSpeed Web Server. In addition, the site has a certificate issued to it.
Use of Legitimate Email Services
The use of Salesforce’s email service is akin to a phishing campaign run by Nobelium, the Russia-based cybercrime group (also known as APT29 and CozyBear) behind the high-profile SolarWinds supply chain breach, according to Saumitra Das, CTO of cybersecurity firm Blue Hexagon. In the latest Nobelium phishing campaign reported by Microsoft in May, the group used the legitimate Constant Contact email marketing service.
“They leveraged a compromised end-user account from Constant Contact, a legitimate email marketing software company, to send phishing emails to more than 7,000 accounts across approximately 350 government organizations, IGOs and NGOs,” Das told eSecurity Planet.
He said spoofing usually involves making up a source to look legitimate or using typosquatting.
“There are ways to detect spoofing but in this case the emails look authentic and are also coming from where they say they are coming from,” Das said, adding that in the case of the Salesforce example, “this means that attackers have got through the first email firewall both from a threat intelligence signature perspective of blocking known bad sources and also in some sense the instinct of the user themselves to be suspicious of what something is. It is common for attacks to get through email security solutions, but then well-trained or savvy users are the next line of defense. This [use of a legitimate email service] increases the chances of those users also clicking on links or downloading attachments.”
A key difference is that unlike Nobelium with Constant Contact, the attackers using Salesforce’s service didn’t hack into the email system but instead signed up for the service, Stephen Banda, senior manager of security solutions at cybersecurity vendor Lookout, told eSecurity Planet.
“The practice of legitimately signing up for an email service with the full intention of using it for malice is an innovative strategy,” Banda said. “This breach should be a warning to all service providers to conduct extensive due diligence into who is requesting access to their services so that this type of scam can be avoided in the future.”
Adopting Zero Trust is Key
The phishing strategy is another reason for adopting a zero-trust architecture, which means assuming that an email from outside the organization is malicious until proven otherwise, according to Stefano De Blasi, cyber threat intelligence analyst with digital risk protection company Digital Shadows.
“Although more time-consuming than the traditional approach, zero-trust architecture can significantly reduce the potential impact of these malicious mass phishing campaigns and should always be considered the first option when possible,” De Blasi told eSecurity Planet.
In addition, along with having in place such standard solutions such as secure email gateways, spam filters and phishing protection, organizations need to invest in security training so employees are more educated of the threats that might come their way, Banda said, adding that phishing simulations are a way to provide training that gives people a safe real-world experience.
“Organizations also need to have a mobile security solution in place that detects and blocks phishing attacks,” he said. “The solution should also educate the users on phishing every time a link is detected. Over time, this will raise awareness so that users question even the most effective phishing attack.”
Further reading:








