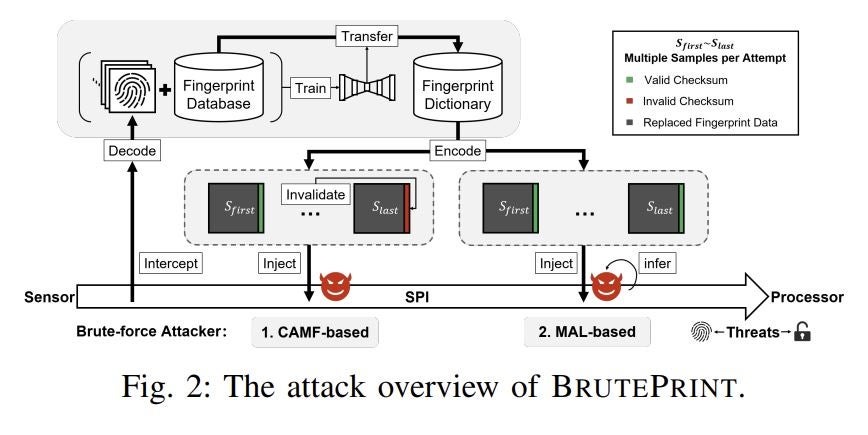
5G is on the cusp of widespread adoption.
Consumers and organizations are enthused about the operational benefits of more robust mobile connectivity, but the shift to 5G networks doesn’t come without risks. Service providers and 5G-enabled device manufacturers both have critical roles to play in the success and sustainability of this wireless network rollout. Beyond that, network administrators must be aware of 5G-enabled vulnerabilities and prepare for threat actors seeking to take advantage of a changing ecosystem.
Here we’ll discuss the most significant risks posed by 5G, how U.S. agencies are approaching the shift, what makes 5G different, and an analysis of deployment to date.
Table of Contents
What Are the Cybersecurity Risks of 5G?
Exposing the Internet of Things (IoT) Universe
Consumer electronics, business, network appliances, and industrial IoT (IIoT) devices are all driving the exponential growth of IoT systems. 5G technology will improve some IoT use cases, thereby adding to the proliferation of IoT devices – a phenomena individuals and organizations aren’t prepared to fully defend in the immediate future.
IoT products are notoriously vulnerable appliances because the build prioritizes ease of use and connectivity. Whether it’s a misconfiguration or inadequate security or patching, new vulnerabilities found in IoT systems seem to make the news every week.
Unfortunately, threat actors can also take advantage of 5G’s enhanced connectivity, executing network attacks faster than ever before. Hackers can spread malware via IoT networks, disrupt supply chains in development, and use a fleet of routers as an IoT botnet to launch a DDoS attack.
Also Read: Cloudflare Fended Off Mirai Botnet DDoS Attack
Network Slice Compromise
One benefit of 5G technology that enterprises are sure to take advantage of is creating private wireless networks in a process dubbed “network slicing.” By multiplexing virtualized and independent logical networks on a physical network, organizations can isolate network segments to specific client verticals.
SAP National Security Services (NS2) CISO Ted Wagner told eSecurityPlanet that network slicing “adds complexity, which may lend itself to insecure implementation. There are no secure implementation guides or standards for network operators. Insecure implementations may result in unauthorized access to threat actors and potential data breaches.”
In instances where network administrators operate several slices, including shared and dedicated network functions, this hybrid approach creates a deficiency in mapping between the application and transport layer identities. To be successful, an attacker must gain access to the 5G Service Based Architecture. From there, the risks posed are data access and a DoS attack on other network slices.
Another attack vector to be aware of is the prospect of CUPS hijacking. The CUPS model, or Control and User Plane Separation, isn’t new, but it shows how 5G relies on more virtualized workloads and cloud-based systems. Because CUPS enables network slicing and can distribute resources throughout the network, its compromise also presents a severe risk.
Also Read: How to Implement Microsegmentation
Give and Take: NFV, SDN, and Microservices
Network Functions Virtualization (NFV) is a virtualized network infrastructure where typical network functions – like firewalls, routing, and SD-WAN – can be installed as software through abstraction. NFV consists of virtual machines or containers and offers reduced costs, flexibility, faster deployment, and automation capabilities.
So how does NFV relate to 5G? Using virtualization, NFV systems enable network slicing. Like so much else, virtualization comes with inherent risk, as several systems could be running and controlled on a single physical device.
Complementary to NFV, software-defined networking (SDN) separates the control plane from the forwarding plane. Great for microservices developing and deploying 5G, SDN also poses threats to the network like traffic spoofing and forwarding device attacks. API security will be a critical concern, as APIs linking microservices across multiple virtualized systems are vulnerable to compromise. This instance can result in NFV data breaches, resource exhaustion, or DDoS attacks.
Attacks at the Network Edge
Edge computing is the relatively new focus on traffic as close as possible to the client device and user. Naturally, IoT devices and the advanced connectivity via 5G are essential parts of edge computing’s evolution. And on the edge security front, secure access to devices, safe application use, threat detection, vulnerability management, and patching cycles are all edge security objectives.
Addressing concerns with multi-access edge computing (MEC), Wagner added, “The lack of a trusted computing environment of 5G components into the MEC could introduce unmitigated risk.”
One such threat posed for 4G that remains a source of concern for 5G is rogue base station (RBS) threats. Also known as international mobile subscriber identity (IMSI) catchers, an RBS spoofs a cell phone tower and diverts cell phone traffic to its desired location. This man-in-the-middle (MiTM) technique places the attacker between the mobile client and the mobile network. They can steal sensitive information, tamper with data, track users, execute packet injections, or cause DoS for 5G services.
Also read: Mobile Malware: Threats and Solutions
NTIA and CISA: Memos from the Feds
In a year where cybersecurity’s gotten its share of major media attention, the U.S. federal government is actively seeking opportunities to assist private and public organizations in meeting the cyber challenges of today.
The NTIA and CISA published reports defining the national strategy for effectively developing and implementing 5G infrastructure and the threat vectors posed by this change.
National Strategy to Secure 5G (NTIA)
The National Telecommunications and Information Administration (NTIA) released its National Strategy to Secure 5G implementation plan starting in January. The program includes four initiatives for U.S. interests now and in the years to come:
- Facilitate domestic rollout of 5G: Research and develop advanced communications to maintain 5G leadership and incentivize and leverage trusted supply chain partners
- Assess and identify 5G Infrastructure security principles: Evaluate risks and vulnerabilities of domestic/international suppliers, 5G infrastructure, and supply chains
- Address 5G risks to U.S. infrastructure in deployment: Identify incentives and policies to close gaps, build economic viability, and incorporate the private sector
- Promote responsible global development of 5G: Engage diplomatically with international partners to ensure risk mitigation, standards, collaboration, and more
Also read: Best Third-Party Risk Management (TPRM) Tools
5G Infrastructure Threat Vectors (CISA)
In May, the ever-growing Cybersecurity and Infrastructure Security Agency (CISA) published a white paper entitled, Potential Threat Vectors to 5G Infrastructure. Together, the report outlines established 5G threat vectors and threat scenarios for 1) policy and standards, 2) supply chains, and 3) 5G system architectures.
Policy and Standards
Global standards set for 5G must be open, transparent, and consensus-driven. Untrusted proprietary technologies that fail to meet these standards pose lingering threats to their clients and inefficiencies. Within telecommunications, standards bodies should be more vigilant in mandating optional security controls that reduce the risk of cyberattacks.
Supply Chains
Information and communications technologies (ICT) have a diverse supply chain vulnerable to added exposure when adopting 5G infrastructure machinery and systems. With billions of devices in the prospective 5G pool, the threat of malicious counterfeit or inherited components from compromised vendors or tools enables the spread of malware.
5G Systems Architecture
While it’s still the early days of 5G deployment, there’s already much to learn about the threats posed. A list of sub-threat vectors exists for the network architecture, including network slicing, multi-access edge computing (MEC), spectrum sharing, software-defined networking (SDN), and the switch from 4G legacy communications to 5G networks.
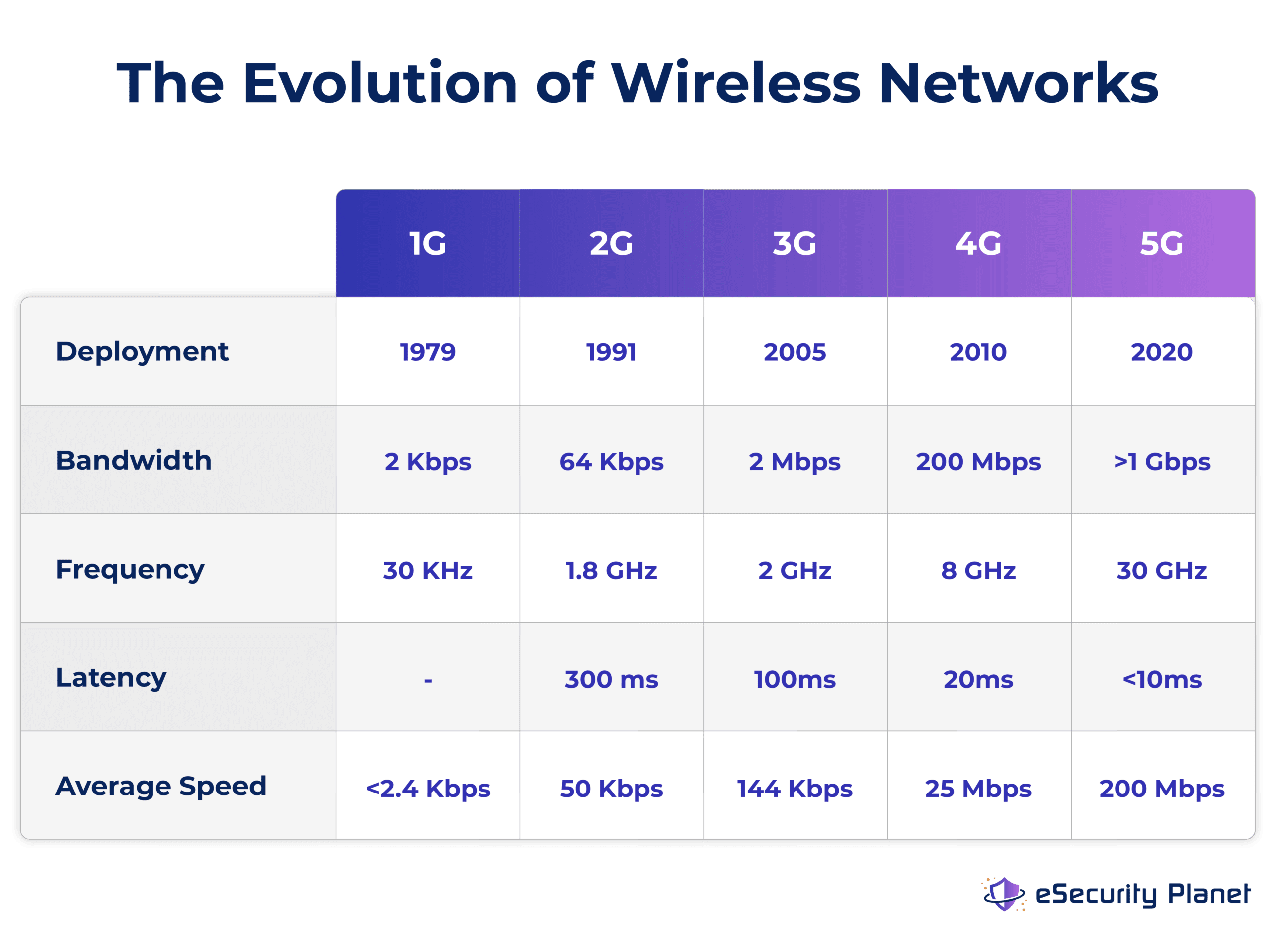
What is 5G? How is 5G Different?
4G LTE (Long-Term Evolution) and 5G NR (New Radio) are examples of radio access networks (RAN), where wireless device data can move from receiver to mobile core network services like the internet. Both protocols are owed to the Generation Partnership Project (3GPP), a consortium of international telecommunications standards organizations.
The above graphic shows how wireless capabilities like latency, average data transfer speeds, and bandwidth have changed over time.
Exponential growth in capabilities like lower latency, more substantial bandwidth, and higher average speeds present a new world of opportunities for mobile connectivity. Today’s RANs, using 5G frequencies, open the door for service providers to offer cloud gaming, extended reality (XR), and autonomous device management.
How 5G Goes Beyond 4G
5G adds a number of advancements over 4G:
- Data transfer rates up to 10 Gbps
- A new generation of satellites offering 100% coverage of Earth
- Lower latency that increases speeds from 20-50 milliseconds to less than 10ms
- Shorter frequencies and more band types mean 1000x bandwidth per unit area
- Up to 90% more energy efficient per traffic unit (Nokia)
- 5G can support up to 1 million devices per square kilometer, up from 4G’s 4,000 devices
Objectives for 5G Implementation
In September 2019, former FCC chairman Tom Wheeler and retired Rear Admiral David Simpson, USN, wrote Why 5G requires new approaches to cybersecurity for the Brookings Institute. Two years later, we reflect on their insights then and what’s changed.
At the time, implementation was on the horizon, while today, we are amidst 5G deployment globally. With federal officials’ recent uptick in cybersecurity strategy, the two overarching recommendations Wheeler and Simpson made were reasonably prudent.
Incentivizing a Cyber Duty of Care
Companies everywhere must develop a culture where cyber risk receives treatment as an essential corporate duty – and further, organizations get rewarded for such behavior. To accomplish this, proposed solutions included:
- Proactive investment in cyber risk reduction for organizations of all sizes
- Utilizing cognitive technologies to combat more complex, software-based attacks
- Transparent access to up-to-date indicators of compromise (IoC) and threat intelligence
- More and robust cybersecurity processes to meet the needs of 5G network complexity
- Inserting security into the DevOps cycle, including design, deployment, and sustainment
- Implementing the NIST Cybersecurity Framework for best practices (see graphic below)
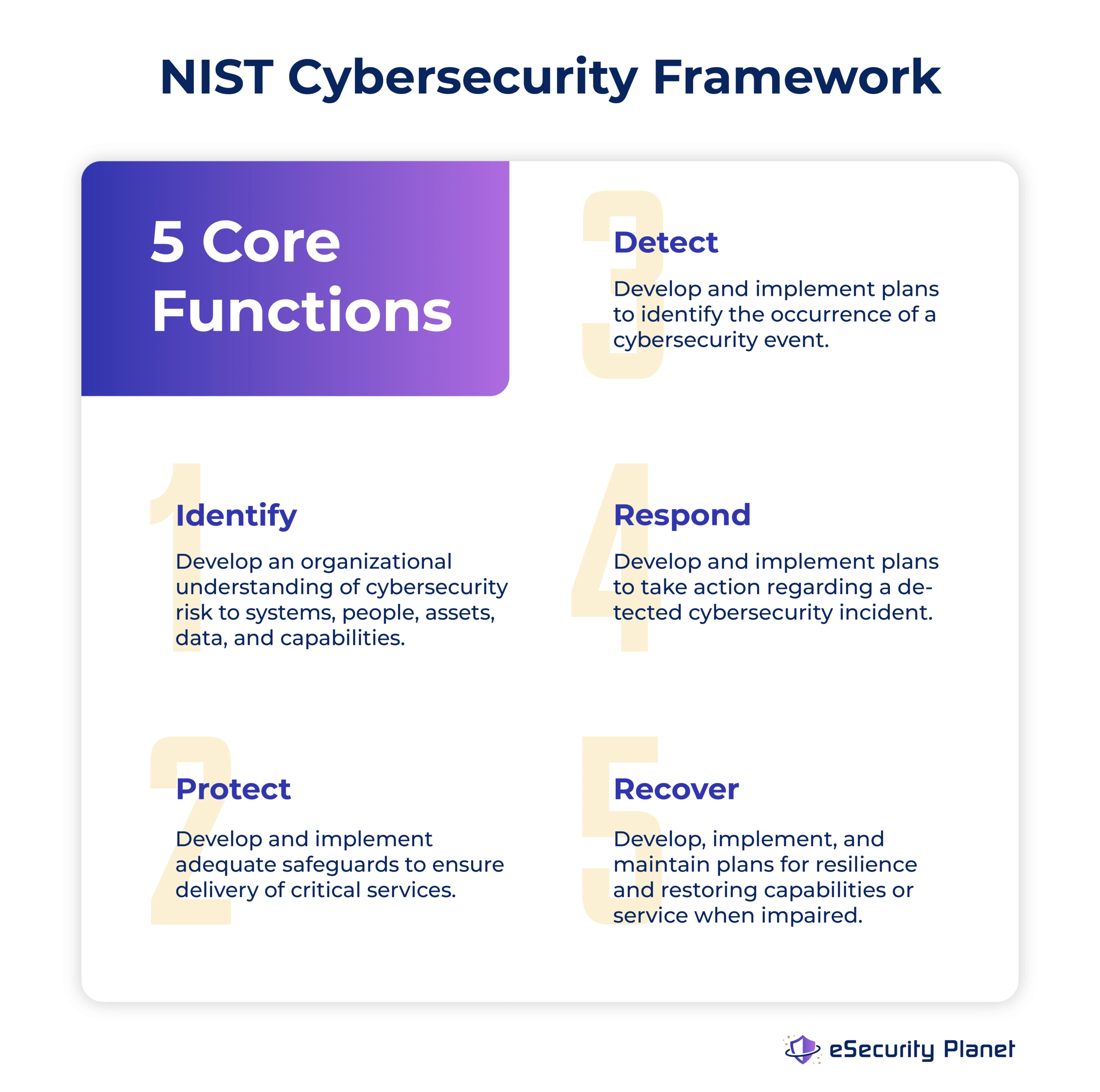
A New Cyber Paradigm
While public and regulatory agencies have long been reactive institutions, the speed of innovation in the digital age requires swifter action. Wheeler and Simpson’s second point was traditional public institutions must do the work to meet the prospects of an ever-digital society. These considerations include:
- Mandate standards for non-government suppliers considering integrated supply chains
- Increase inspection and certification of critical network and infrastructure devices
- Enhance consumer transparency about cyber risks with spec standards and labeling
- Recognize market shortcomings and develop incentives for cyber duty of care adoption
- Continue oversight and participate in the secure development of 5G with 3GPP
- Establish a more effective public-private partnership for collective security
Analyzing Progress and What’s To Come
Two years later, there’s much to cheer about and concerns that remain. Touching on the authors’ recommendations, here is where we stand today:
Progress Points
- Rapid increases in cybersecurity spending, with Gartner forecasting total security and risk management spending to exceed $150 billion in 2021 (up 12.4% from 2020)
- Cybersecurity products and service providers are inserting AI and ML into security capabilities to meet attacks of growing complexity
- U.S. federal agencies like CISA gain authority with rising cyberattacks requiring public support, an increasing budget from Congress, and political lobbying
- DevOps is increasingly adopting cybersecurity to establish DevSecOps processes
- The announcement of the U.S. Joint Cyber Defense Collaborative at Black Hat 2021 is promising for a growing collective response to cybersecurity threats
To Be Continued
- Last December, the U.S. Congress passed the IoT Cybersecurity Act applying to government contractors, but regulation for industry vendors remains inefficient
- Transparency for consumers is a work in progress that would mean more federal policies or standards relating to product specifications, labeling, and proper use of devices
- While beneficial, NIST and CISA frameworks are only recommendations and do not hold organizations accountable to a cyber duty of care
- Critical network and infrastructure devices continue to lack inspection and certification designations that could curb vulnerabilities
- Lack of rewards-based system for organizations meeting cybersecurity objectives
In June, the Ericsson Mobility Report projected over 580 million devices would have 5G subscriptions. By 2026, that number grows to near 3.5 billion 5G mobile subscriptions covering every region of the globe. Though full implementation won’t be fully realized for some time, CSPs and public and private stakeholders are all responsible for the sustainable development, deployment, and maintenance of 5G networks.
Between now and then, we continue to learn and develop adequate security systems to defend the next generation of wireless networks. Efforts like to shore up identity, leverage zero trust frameworks, and authenticate devices will remain best practices for the immediate future.