New cybersecurity buzzwords are always in abundance at the Gartner Security & Risk Management Summit, and the concepts that took center stage this week, like cybersecurity mesh and decentralized identity, seem well suited for new threats that have exploded onto the scene in the last year.
Gartner analyst Ruggero Contu noted that security risks are becoming external: the software supply chain, the public cloud, the trading of breached data, and IoT and operational technology (OT) are all threats outside of traditional perimeter security.
Those threats are inspiring innovations in security technology, chief among them the security mesh, which has at its core distributed policy enforcement and “pluggable, composable tools that can be plugged anywhere into the mesh,” Contu said.
He said security mesh fabric enabler technology uses foundational services such as:
- Centralized policy management and orchestration
- Security analytics, intelligence and triggers
- A distributed identity fabric
What is Cybersecurity Mesh?
Gartner analyst Felix Gaehtgens said the security mesh is still a strategy rather than a defined architecture, but he said the concept better aligns organizations with threats: “Attackers don’t think in silos. Organizations do,” he noted.
By 2024, Gaehtgens predicted that security mesh technology will lead to huge savings in the cost of breaches. “Organizations adopting a cybersecurity mesh architecture to integrate security tools to work as a cooperative ecosystem will reduce the financial impact of individual security incidents by an average of 90%,” he said.
Instead of SIEM and SOAR integrating security tools, the security mesh will use security analytics and intelligence, he said. The mesh will also include identity, policy, posture and dashboard layers.
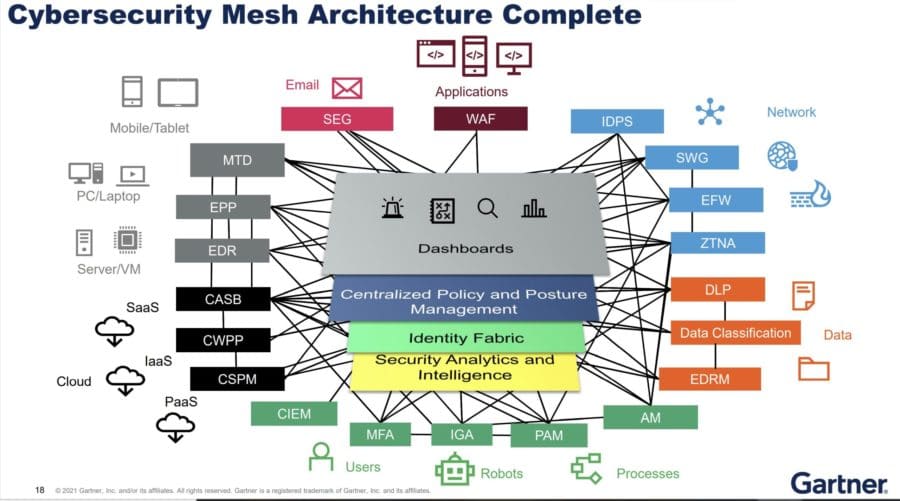
Cybersecurity mesh architecture, or CSMA, “is more than XDR,” Gaehtgens said.
XDR, or extended detection and response, has emerged as a new way for security vendors to tie their products together in a unified platform. Gaehtgens said XDR is a “potential foundation” for the security analytics and intelligence that CSMA requires, as are SIEM and SOAR, which “can add value” to the security analytics/intelligence layer in a security mesh.
He called secure access service edge (SASE) technology “a meshy approach of delivering distinct functions in an integrated manner,” but the security mesh has “a broader scope.”
A number of cybersecurity companies have CSMA-like approaches today, he said, among them Fortinet, IBM, McAfee, Microsoft, Palo Alto Networks and Broadcom-Symantec. Those platforms “can provide benefit and scale and cost in the intermediate term,” but have the potential for vendor lock-in and lack of interoperability.
Gaehtgens recommended that organizations start building the supportive layers for a cybersecurity mesh strategy, including security analytics, identity fabric, policy management, and dashboards. Distributed security technologies offering interoperability will be key to the security mesh, so users should evaluate features such as inversion of control APIs, standards support, and extensible analytics.
He also told conference attendees to “familiarize yourself with current and emerging standards, and open source code projects as a potential alternative to supplement vendor interoperability gaps.” He listed more than 20:
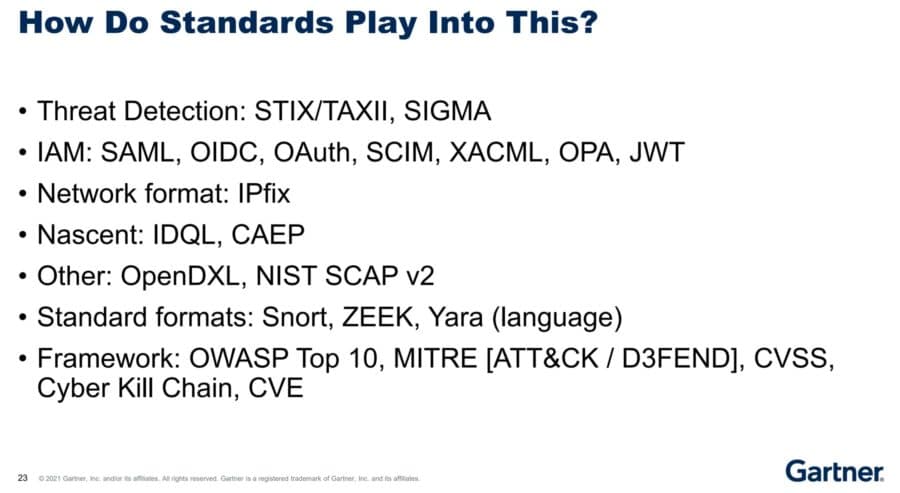
See also: Top XDR Security Solutions
What is Decentralized Identity?
Decentralized identity will be key to the security mesh. Contu said that under decentralized identity, identities are linked to system elements, with a low reliance on centralized identity (see image below).
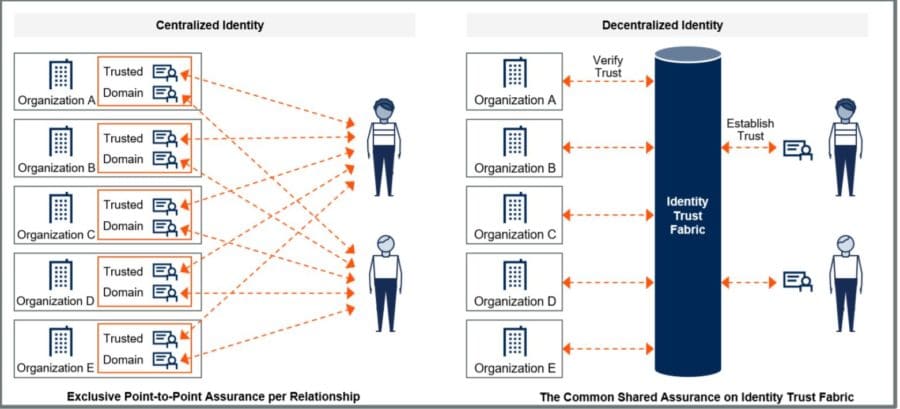
Traditional identity and access management (IAM) has “issues with security, scalability, reliability and privacy,” Contu said. [Gartner analyst Peter Firstbrook later noted that IAM has itself become a target in credential theft and other attack techniques.]
However, decentralized identity is as yet an “unproven technology,” held back by Blockchain understanding and skills and the difficulty of assessing risks across Blockchain services.
Also read: The State of Blockchain Applications in Cybersecurity
Where Security Buyers Are At
Contu said the technologies buyers are interested in now include OT security, cloud workload protection, cloud security posture management, and behavior monitoring, with integrated and digital risk management, container-based network defense, passwordless authentication, SASE and zero trust networking gaining traction in the next one to three years.
Contu recommended that organizations “position the enterprise for a more secure future by choosing cybersecurity technologies that offer high levels of integration capability. The security of the composable enterprise requires flexible cybersecurity mechanisms with a rich set of APIs, based on interoperability standards.”
Buyers need to rethink network and server security priorities and “invest in solutions that are truly designed for cloud first and zero trust,” he said.
Lastly, he said, organizations should invest in people, process and organizational change to address the expanding role of security to address “external threats, digital trust and safety that arise from the digitalization of business.”
See also: Best Zero Trust Security Solutions
Supply Chain Threats to Grow
Firstbrook said in a press briefing at the conference that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021.
He listed nine supply chain attack methods and some of their victims:
- Authenticated partner compromise (Target, Stuxnet)
- Outsourced IT based attacks (Kaseya, CloudStar)
- Source code modification (SolarWinds, NotPetya, CC cleaner)
- Modified applications in production (Web CC scraping)
- Stolen Certificates (Codecov, Bit9, Mimecast)
- Stolen source code (RSA)
- Open-source code components (RubyGems)
- App store and browser plug in trojans (Exodus, Great Suspender)
APIs are a growing target and often ignored attack point, Firstbrook said.
Also read: The Biggest Lessons about Vulnerabilities at RSAC 2021
Endpoint Security ‘Critical’
Firstbrook called endpoint detection and remediation “critical first responder tools, even if they fail to detect the initial intrusion.”
Endpoint security tools are a cornerstone of IT security, and Firstbrook said he expected the market to grow 26% to $16 billion this year.
Firstbrook noted that the “the configuration of security products is as important as the quality of the product.” Among his recommendations, he said “developer machines must be secured” and that “privileged servers must be profiled and the behavior monitored.”
See also: Top Endpoint Detection & Response (EDR) Solutions
Ransomware Attacks and Defense
Gartner analyst Jon Amato discussed ransomware defenses. His slides on the anatomy of ransomware attacks and ransomware data protection strategies are worth reproducing here:
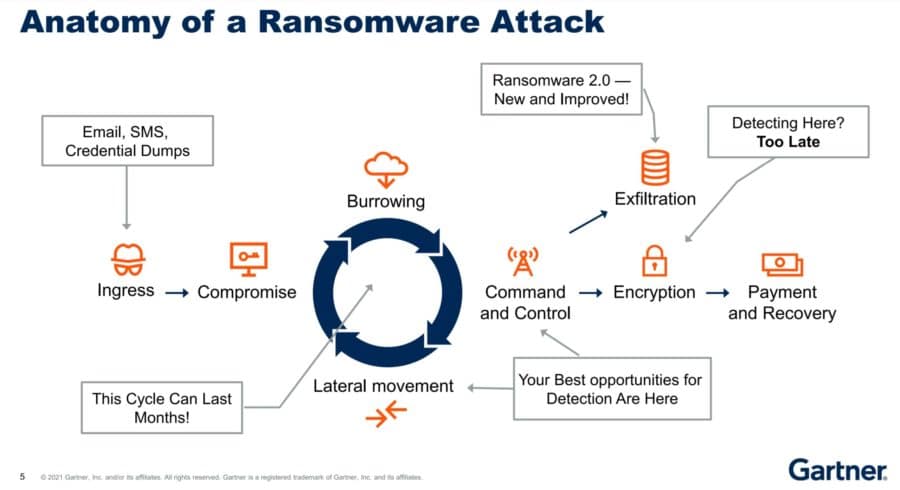
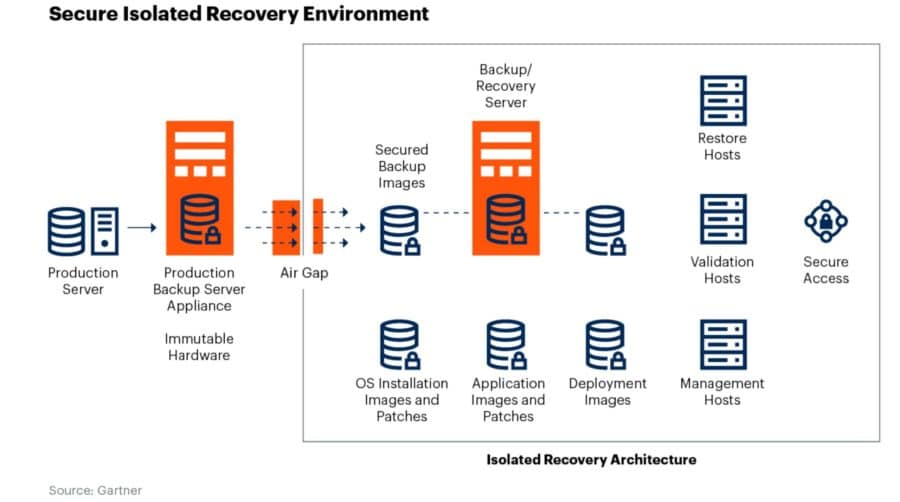
Further reading:








