In a year in which ransomware attacks seem to get worse by the day, companies have made surprising progress defending themselves against attacks.
But the attention paid to the malware by journalists, cybersecurity vendors and increasingly, government agencies, has pushed companies to improve their preparedness to defend themselves against ransomware gangs, according to a report this week by security solutions vendor Cymulate.
That preparedness has led to a reduction in the damage done by some of these attacks and in the amount of downtime they cause, giving organizations some hope at a time when they feel vulnerable and under assault, Cymulate officials said.
“The survey data indicates that, while everyone may be a target, most of those who are hit are doing an excellent job defending themselves and recovering gracefully,” the authors of the report, Ransomware Study: Unexpected Reasons for Optimism, wrote. “When taking a closer look at the damages incurred by the respondent victims of an attack, overall, they suffered limited damage both in severity and duration, with over half the respondents proactive enough to stop the attack before it could cause any damage, and the vast majority of those even before it could cause any downtime.”
Companies Invest More in Security
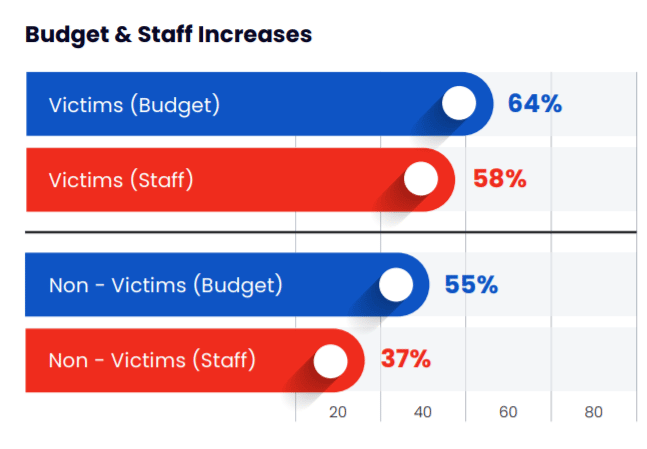
For the report, Cymulate queried 900 IT professionals worldwide and found that 28 percent of companies had been the victim of a ransomware attack over the last few years and in 70 percent there had been an increased awareness among top executives and business managers of the threats that ransomware pose. Overall, more than half of all companies are investing more in security budgets and headcount and almost half are creating new or modified incident response plans.
In addition, 82 percent said they are adopting offensive cybersecurity solutions.
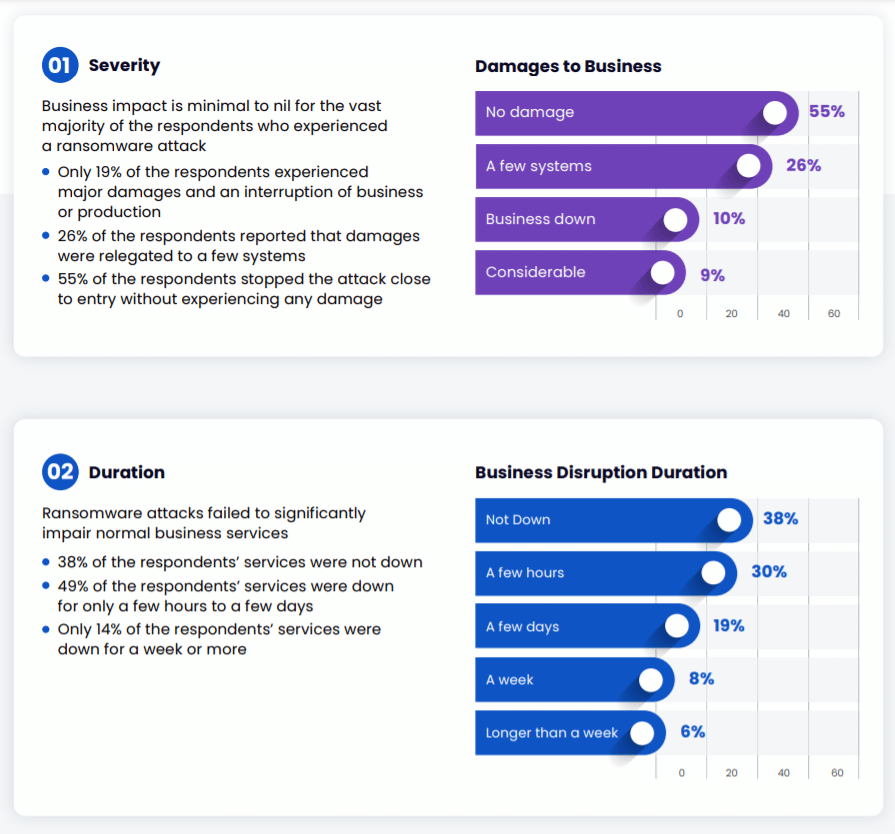
Where the greatest optimism comes in is in what tends to happen when a company is hit with ransomware, according to the report. Among the respondents, 55 percent said they suffered no damage after experiencing a ransomware attack, and another 26 percent said they only lost a few systems. Only 19 percent said their business went down or that they sustained considerable damage.
About 68 percent of respondents said their business didn’t go down or did for a few hours. Others said their businesses were down for a few days (19 percent), a week (8 percent) or longer than a week (6 percent).
Overall, organizations are spending more on budget and staff, upgrading incident response planning, spending more on security products and procedures and are being more aggressive in their protections, from penetration testing, breach and attack simulations and attack surface management, according to the report.
“Paradoxically, ransomware’s ill-gotten fame might be pushing the development of security measures covering other potential dangers,” the authors wrote. “Concern about ransomware is felt by all, and the result of fear is increased budget and resources that are invested in improving security posture management. Though ransomware is at the source of these security posture improvements, the end-result is a better defense against all types of attacks.”
Also read: Best Backup Solutions for Ransomware Protection
Threats Evolve Too
The results reflect what some others in the cybersecurity industry are seeing, although most agree that any optimism needs to be tempered by the realization that ransomware isn’t going anywhere and that just as vendors and enterprises are getting better at defending against it, bad actors also are evolving.
“As organizations move forward on their journey towards cloud transformation, there’s a lot of resilience that comes along for the ride,” Tim Wade, technical director for the CTO team at Vectra, told eSecurity Planet. “The farther along we get in this journey, the more I would expect to find pockets for encouragement with respect to organizational resilience.
“The challenge [is] that adversaries haven’t fully adopted their tactics to exploit the speed and the scale that the cloud offers their own disruptive operations,” Wade said. “For organizations that still haven’t shaken off the ‘set and forget’ mindset of legacy IT, they’ll get bitten again. But for organizations that have internalized the need for their core security strategy to emphasize visibility, detection and response, I expect this positive trend is the down payment on a more resilient future.”
Chris Morgan, senior cyber threat intelligence analyst at DigitalShadows, said he agrees that awareness of the threat posed by ransomware is starting to pay off for larger and well-resourced companies, but that bad actors also will target smaller organizations that may not have the same resources and people.
Also read: Best Ransomware Removal and Recovery Services
Damage and Downtime
Morgan also told eSecurity Planet that it’s difficult to comment on damages and downtime.
“Most companies impacted by a ransomware attack will likely aim to provide only the minimal amount of information surrounding an attack to reduce the reputational and regulatory impact that might follow,” he said. “Transparency following such incidents is rare, but refreshing given that added context and insights can greatly assist incident responders and security researchers.”
He also pointed to a report last month from ThycoticCentrify that found as many as 83 percent of victims of ransomware attacks have paid the ransom, adding that “given that such a high percentage reportedly concede to attackers’ demands, it’s likely that the damages and downtimes have not become any less impactful.”
Threats Continue to Accumulate
Cymulate’s report noted that the U.S. Treasury Financial Crimes Enforcement Network said that in the first half of the year, more than $590 million in ransoms were paid, more than the $416 million paid during all of 2020. With that type of money being paid, ransomware is too lucrative for cybercriminals to move away from.
Just this week, cybersecurity firm Sophos detailed a new Python ransomware called Momento, which locks files in a password-protected archive if the ransomware itself can’t encrypt the targeted data.
In addition, Russian ransomware gangs reportedly may be looking to collaborate with Chinese hackers, according to a report from cybersecurity vendor Flashpoint.
It’s a continuing cycle of cybersecurity professionals and cybercriminals acting and reacting to what the other side is doing, according to OJ Ngo, co-founder and CTO of network security firm DH2i.
“Ransomware attacks are an important bullet point for many modern corporations,” Ngo told eSecurity Planet. “Fortunately, companies are getting better at mitigating ransomware attacks by strengthening their HA/DR [high availability/disaster recovery] plans.”
With such hardware and software solutions in place, as seen in the Cymulate report, downtime and damages are being reduced, he said.
“It’s a never-ending cat-and-mouse chase,” Ngo said. “But organizations are getting better and better at establishing and following security best practices, such as offering internal risk education and mitigation courses to employees and doing regular security audits [and] drills. As long as we continue to take these attacks [and] issues seriously, we all can move forward.”
Further reading: Cybersecurity Mesh, Decentralized Identity Lead Emerging Security Technology: Gartner








