Lateral movement is a series of techniques used by threat actors to gain progressively greater access to IT systems and data once they infiltrate a network.
The goal of threat actors is to eventually gain access to sensitive data or endpoints. As attack paths can vary, that makes lateral movement a goal as much as it is a series of moves. Hackers have already entered the compromised network, so how can they continue to move throughout it? Stealing credentials, snooping for opportunities, and escalating privileges allow threat actors to steadily increase their presence in a compromised system. If they make it far enough, they can steal credentials for privileged accounts and valuable data.
Lateral movement is challenging to detect if an attacker uses legitimate credentials and system tools. We’ll look at lateral movement techniques and ways to detect and prevent attacks to give your IT and security teams a starting point for locating subtle but malicious traffic within your computer systems.
Table of Contents
How Lateral Movement Works
One of the scariest things about lateral movement is that most organizations don’t know just how easily they could be breached.
An XM Cyber study last year found that 63% of critical assets are just a single “hop” away from initial breach to compromise; 81% of critical assets are no more than two attack techniques away from disaster; and 94% of critical assets can be compromised in four or fewer moves by a hacker after the initial attack vector. About 75% of an organization’s critical assets can be compromised in their current security state, and 78% of businesses are open to compromise every time a new Remote Code Execution (RCE) technique is found.
An attack might combine, say, credential gathering techniques followed by a file injection technique and then use a vulnerability to compromise an asset. Lateral movement techniques can be used across on-premises and cloud environments and even combine the two in a hybrid environment. In the example below, the attack started with a Windows machine breach, stole credentials, and then used a compromised Azure access token to execute commands on a critical on-premises asset.
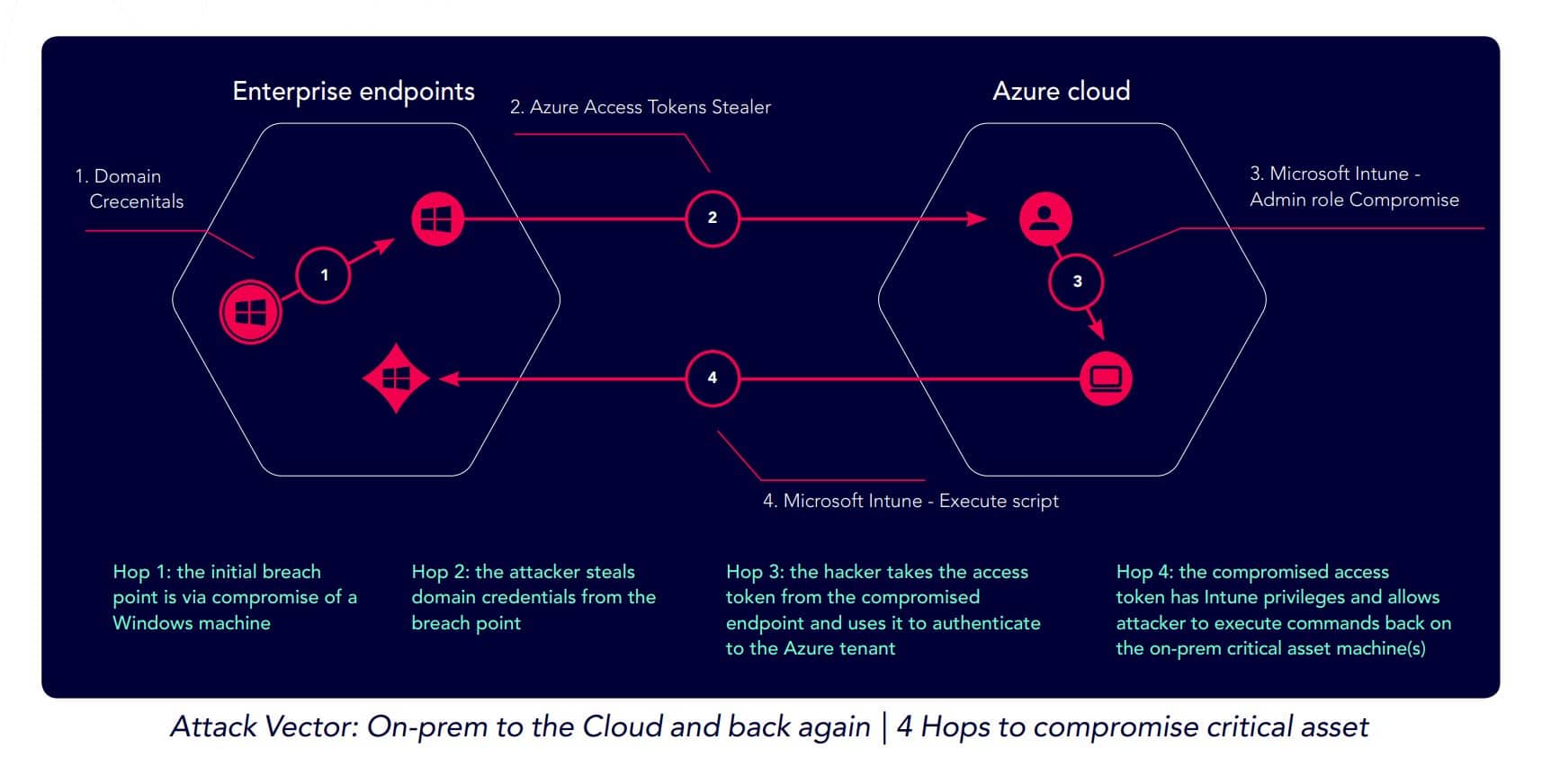
Hackers often use legitimate tools like PowerShell to carry out their attacks, called living off the land (LOTL) attacks and difficult to detect because of the use of legitimate tools. Threat groups use their own tools and custom scripts to carry out attacks in addition to commonly used pentesting tools. Active Directory is often a target of hackers because of the sensitive credentials it contains.
MITRE protection tests are a very good example of lateral movement in action, as the tests emulate advanced threat actors working their way through a compromised environment.
Also read: How to Tell if Active Directory is Compromised
4 Security Attacks That Use Lateral Movement
Many attacks involve lateral movement, especially sophisticated ones that require time and patience on the part of hackers, often called Advanced Persistent Threats (APTs) when they infiltrate an organization with the intention of moving toward high-value targets. The following attacks and vulnerabilities are notable for using lateral movement to gain further access to applications.
Passing the Ticket Attacks
In a passing-the-ticket attack, an attacker steals Kerberos tickets and injects the ticket into another process. By using the stolen ticket, the attacker bypasses any password authentication required to access a file, application, or system. Once in the system, they’ll explore other avenues to access higher-privilege accounts.
Pass-the-Hash Attack
Similar to a pass-the-ticket attack, a threat actor steals a hash that they can use to authenticate themselves. Depending on the level of access the stolen credentials provide, this theft may give the threat actor access to other privileged accounts, too — like when they steal an admin’s hash. A threat actor will hunt for other credentials once they’ve gained access to an account, moving laterally through the system.
For a look at “Kerberoasting” and pass-the-hash attacks in action, see Testing & Evaluating SIEM Systems: A Review of Rapid7 InsightIDR.
Phishing
When a threat actor sends an email with a malicious link and the target user clicks on that link, the compromised link can install malware onto the user’s machine or give the threat actor access to the user’s credentials, depending on the attack. Some may do both. Once the threat actor has access to credentials, they can enter the system and look for opportunities to escalate their privileges. Some threat actors may spend dedicated time researching their phishing victims. As most cyber attacks begin with phishing, organizations can always do more here to protect themselves.
Backdoor or vulnerability exploitation
An attacker may find a backdoor in a computer system, and once they enter the system, they scavenge for opportunities to continue moving through it. Additionally, zero-day vulnerabilities and other unpatched weaknesses may allow a threat actor to enter a system before the issue can be patched.
Stages of Lateral Movement Attacks
A typical completed cyberattack that uses lateral movement consists of the following general steps: initial theft, initial access, gathering information, escalation, and end theft. Some attacks may only use a few steps or not make it the whole way, but this overview shows the complete cycle.
Initial Theft or Research
A threat actor may steal user credentials through phishing, brute force a password, or locate an unpatched vulnerability in a networking device. Once they have the information they need, they’re free to breach a system.
Initial Breach
After stealing legitimate credentials or hashes, brute forcing, or exploiting an existing vulnerability, the threat actor is able to enter the network or computer system. They may not yet have access to any other account, but they have at least breached the overall system.
Gathering Information
Once inside the network or computer system, the threat actor gathers data, stealing additional credentials where possible and moving between programs to which they gain access. This process can take weeks or months; an undetected threat actor, including a strain of malware, is often free to roam throughout the network and observe.
Privilege Escalation
Often, privilege escalation goes hand in hand with the snooping process: the additional credentials or hashes stolen may belong to increasingly sensitive accounts. The attacker will be looking for privileged access accounts, like IT admin accounts or databases with sensitive company information.
End Theft
For some lateral movement attacks, the end goal is a payload of sensitive information. For others, it’s endpoint takeover: if a threat actor can control multiple endpoints, they can use those devices to their advantage, whether that’s to compromise a particular company initiative or conduct a denial-of-service attack.
Lateral Movement Benefits for Attackers
Lateral movement can help threat actors access systems on a network less intrusively than other attack methods, depending on the methods they use to steal credentials. If they enter undetected, it also allows them to bide their time, exploiting multiple applications at their leisure.
Easier Access to Credentials
Often, a threat actor is able to access multiple systems without having to guess or brute force all credentials. This depends on the credentials or hashes they’re able to steal, but some tickets or passwords provide access to multiple applications, not just one.
Easier to Escalate
Rather than having to guess the password to the chief information officer’s admin account, threat actors can move laterally and work their way up to privileged accounts. If they enter a system undetected, they may also have weeks or months to worm their way into a more sensitive account than the one from which they initiated the attack.
Multiple Weak Systems to Exploit
Unfortunately, many programs and networks have unpatched vulnerabilities and backdoors that give threat actors an easy in. But once they’re inside the network, they also have opportunities to keep accessing programs because often the network hasn’t been properly segmented.
Learn more about major network security threats.
How to Detect Lateral Movement Attacks
Because lateral movement often requires threat actors to find legitimate credentials, it can be more difficult to detect than other attacks. Also, attackers can hover in a system for weeks or months at a time, waiting for an opportunity to escalate privileges. Businesses often need sophisticated tools that identify the relationships between suspicious activity.
Advanced Endpoint Detection
Endpoint detection and response tools develop large-scale maps of the connections between endpoint devices. While a remote user accessing their IT admin account on their laptop at 4:30 PM might not be suspicious, an EDR platform could observe that the same user then accessed a remote server in another region’s data center. If that’s an unusual pattern for that user, the EDR tool should flag it. It’s critical to use broader context to determine when a set of actions are more suspicious together than separate.
Network Traffic Monitoring
Similarly, consistent network monitoring gives your IT and security teams better context for strange behavior on the network. While one event by a threat actor might not be an apparent cause for concern, a set of activities may be anomalous when executed in order.
Behavioral Analytics
User entity and behavioral analytics (UEBA) specifically focuses on the actions of users, including strange ones. UEBA tools compile user data over time to determine what is standard, what is anomalous, and what is suspicious. Long-term data, examined and analyzed by machine learning, offers better information overall than one-time alerts. Behavioral analytics is increasingly becoming part of other tools such as EDR.
SIEM Tools
As a central security management tool with visibility across networks, devices, and even cloud environments, SIEM systems are another good tool for detecting indicators of compromise.
How to Prevent Lateral Movement Attacks
Your IT and security teams should consider the following prevention methods to halt and mitigate the effects of lateral movement in your IT infrastructure. Threat actors often use very advanced attack techniques and tools, and you’ll need to implement equally strong protection to defend your endpoints and secure your network.
Network Segmentation
Gone are the days when presenting a single set of credentials (or even MFA) should grant users access to all systems on a network. All applications and programs on the network should require their own credentials.
While this may not be enough to stop an attacker who has multiple sets of credentials (and some do in lateral movement scenarios), it’ll delay and halt many threat actors. If they can’t escalate their privileges, the effects of the breach are minimized. Zero trust plays a key role in segmentation — traffic is considered untrusted until the user proves they are authorized and authenticated, the opposite of legacy security approaches.
You may also want to consider microsegmentation, more specifically for sensitive applications. These types of segmentation are similar, but microsegmentation is focused on all accounts, not just network traffic. If you have many sensitive accounts, microsegmentation might be the way to go.
Just-in-Time Access
Intended to mitigate the problem of exploited admin privileges, just-in-time access only permits authorized users to access their accounts at designated times. The privileges are granted and withdrawn dynamically. Legacy IT infrastructure doesn’t do a good job of zero trust access, but just-in-time access would reduce the attack surface because a threat actor wouldn’t be able to use legitimate credentials unless they’re dynamically granted access. And the window in which they could receive access would be small.
Endpoint Detection and Response
We listed this earlier and we’ll list it again. EDR is both a detection and a prevention tool. It’s a cornerstone method of identifying breaches across many devices. If you’re a large enterprise looking for a full network solution, we recommend extended detection and response (XDR), which goes beyond endpoints to the entire network.
Bottom Line: Zero Trust is Critical for Lateral Attack Prevention
We’ll plug zero trust frameworks once again because they are one of the best possible answers to sophisticated lateral movement attacks. Zero trust isn’t everything, but it’s one of the only ways to stymie threat actors who enter a network undetected. Make sure that every subnetwork and application is isolated and requires different sets of credentials. While this may seem time-consuming to set up, it’ll pay off for your enterprise in the end. Same for small businesses — they need to implement segmentation for networks and applications, too. Lateral movement is a significant threat and difficult to prevent, but implementing zero trust can reduce its impact on business systems.
Read our guide to securing your network next.








