The BlackByte ransomware group is actively exploiting a vulnerability in RTCore32.sys and RTCore64.sys, the drivers of a widely used graphic card utility called Micro-Star MSI AfterBurner (version 4.6.2.15658). Recorded as CVE-2019-16098, the flaw allows any authenticated user to read and write to arbitrary memory, I/O ports and model-specific registers (MSRs).
Cybercriminals can abuse it to elevate their privileges, execute arbitrary commands under high privileges, exfiltrate data, or bypass Microsoft driver-signing policy to deploy malware. Researchers observed one particularly troubling exploit, as BlackByte recently used the vulnerability to jam security solutions such as EDR and antivirus software.
Dubbed “Bring Your OwnVulnerable Driver” (BYOVD), the tactic has been used by various attackers in the wild, including APT groups such as InvisiMole and LoJax. These attacks target Windows systems.
Because Windows doesn’t allow unsigned drivers, cybercriminals hijack existing signed drivers to reach the Windows kernel or load an unsigned driver. Such an approach is also used by game cheaters to circumvent anti-cheat systems, such as Capcom’s vulnerable driver.
Also read: How Hackers Evade Detection
How BlackByte Carried Out the Attack
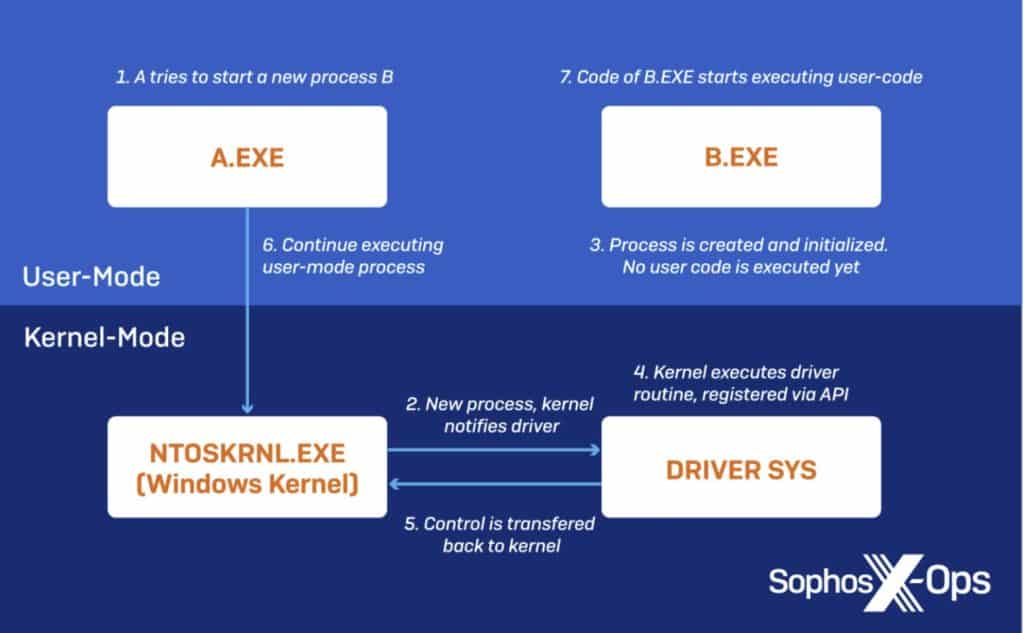
It’s essential to know what kernel memory is to understand the hack. In Windows, a process initiated by a user gets its own memory space that is only available to that process. In kernel memory, there’s no such isolation. All code that runs in kernel mode shares the same space.
As a result, a vulnerable driver can compromise other drivers, making them crash or removing some of their routines.
The term “User land” refers to programs that interact with a small part of the kernel that is exposed on purpose, such as through APIs. “Kernel” refers to what runs at high privileges, behind hardware protection. Code that runs in kernel mode is trusted and executed.
If attackers manage to inject malicious code in the kernel, it’s game over.
Sophos researchers reported that the vulnerable drivers violate Microsoft’s security guidelines by allowing user-mode processes to access the I/O control codes. This risky approach allows reading or writing in kernel memory directly without any shellcode or additional exploit.
After identifying the kernel version to determine offsets that match the kernel ID and installing its Service, BlackByte dropped the vulnerable driver in AppData\Roaming and removed the specific Kernel Notify Routines used by security tools.
Notify routines handle critical interactions between the kernel of system activity and loaded drivers, for example, when a new process should be created to execute some task. A quick control transfer can happen when the driver has registered a specific callback function (PsSetCreateProcessNotifyRoutine).
Security tools often use these routines to collect data about the system, but attackers cannot simply remove them directly. That’s why they use existing drivers that interact with the kernel memory to bypass the OS protection.
However, to identify whether the callback function is used by EDR products, BlackByte must calculate “the most likely driver from the callback address itself.” Sophos researchers discovered BlackByte has a procedure that fetches all base addresses and compares them to the callback function address.
The base address with the “smallest delta to the callback function” is selected and passed to GetDeviceDriverBaseNameW to retrieve the name of the driver. Then the name is compared to a list of more than 1,000 driver names. If there’s a positive match, the callback will be removed by overwriting its memory container with zeros.
“The evasion technique supports disabling a whopping list of over 1,000 drivers on which security products rely to provide protection,” the Sophos researchers wrote.
How to Mitigate BYOVD Attacks
Sophos researchers listed Indicators of Compromise (IoCs) here and recommended keeping up with vulnerability announcements to maintain a blocklist of actively exploited drivers.
Listing and monitoring all drivers installed is strongly recommended, and, of course, the system must be updated to patch known security flaws.
Any vulnerability that allows reading and writing in kernel memory should be addressed as soon as possible.
It should be noted that BlackByte has included additional measures to evade detection. For example, it tries to hide itself from debugging processes or even stops if the debugger is on, such as by using the IsDebuggerPresent API.
It also looks into the system to find DLLs used by popular antivirus software like Avast or Comodo Internet Security, and stop those processes before it gets flagged.
See the top Vulnerability Management and Patch Management tools








