Microsoft’s Patch Tuesday for April 2023 targets 97 vulnerabilities, seven of them rated critical – as well as one that’s currently being exploited in the wild.
The one flaw that’s currently being exploited, CVE-2023-28252, is an elevation of privilege vulnerability in the Windows Common Log File System (CLFS) Driver that could provide an attacker with SYSTEM privileges. Qualys director of vulnerability and threat research Bharat Jogi noted that the flaw, which has a CVSS score of 7.8, is already being used by cybercriminals to deploy Nokoyawa ransomware.
The seven critical vulnerabilities, all of them remote code execution (RCE) flaws, are as follows:
- CVE-2023-21554, a flaw in Microsoft Message Queuing with a CVSS score of 9.8
- CVE-2023-28219 and CVE-2023-28220, a pair of flaws in the Layer 2 Tunneling Protocol with a CVSS score of 8.1
- CVE-2023-28231, a flaw in DHCP Server Service with a CVSS score of 8.8
- CVE-2023-28232, a flaw in the Windows Point-to-Point Tunneling Protocol with a CVSS score of 7.5
- CVE-2023-28250, a flaw in Windows Pragmatic General Multicast (PGM) with a CVSS score of 9.8
- CVE-2023-28291, a flaw in the Raw Image Extension with a CVSS score of 8.4
Two of the seven are particularly noteworthy. “CVE-2023-28231 (DHCP Server Service Remote Code Execution Vulnerability) and CVE-2023-21554 (Microsoft Message Queuing Remote Code Execution Vulnerability) are both critical-severity RCEs submitted to Microsoft by external security researchers, and both are flagged by Microsoft as more likely to be exploited within the next 30 days,” Sophos senior threat researcher Angela Gunn observed.
Also read: Is the Answer to Vulnerabilities Patch Management as a Service?
Nokoyawa Ransomware Leverages Flaw
Nokoyawa ransomware “is a relatively new strain for which there is some open-source intel to suggest that it is possibly related to Hive ransomware – one of the most notable ransomware families of 2021 and linked to breaches of over 300+ organizations in a matter of just a few months,” said Jogi said.
“While it is still unclear who the exact threat actor or APT group is using Nokoyawa, targets have been observed in South and North America, regions across Asia, and SMBs in the Middle East,” he added.
Jogi noted that this isn’t the first time a flaw in the Windows Common Log File System Driver has been leveraged by threat actors. “In September 2022, Microsoft fixed another vulnerability – CVE-2022-37969, which was known to be exploited in the wild – that affected this same component,” he said. “CVE-2022-37969 was leveraged by an unknown threat actor to gain elevated privileges once they had a foothold on the system.”
Also read: Ransomware Protection: How to Prevent Ransomware Attacks
Two Additional Vulnerabilities of Note
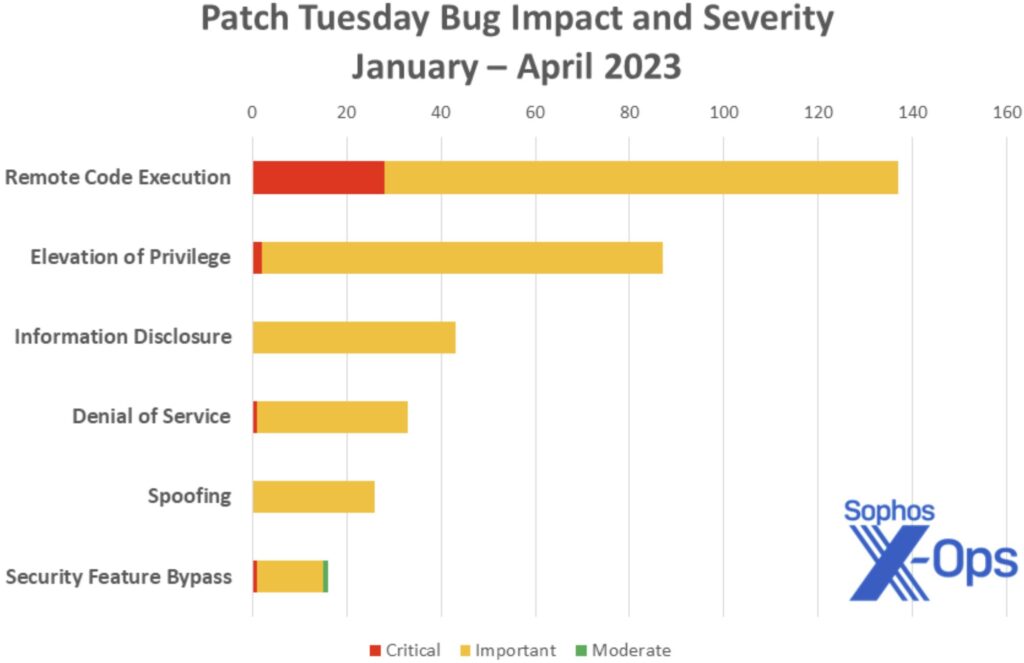
RCE flaws have comprised most of the critical Microsoft flaws so far this year (image below from Sophos).
Action1 vice president of vulnerability and threat research Mike Walters highlighted two additional RCE flaws from the current updates. The first, CVE-2023-28311, is a remote code execution vulnerability in Microsoft Word with a CVE score of 7.8.
“Although it is considered low complexity and does not require privileges to exploit, it does require user interaction and cannot be exploited through the Preview pane,” Walters wrote. “This means that an attacker must send a malicious file to the user and convince them to open it. While Microsoft says this vulnerability is less likely to be exploited, it is still recommended to update your Microsoft 365 applications to the latest version as a precaution.”
The second, CVE-2013-3900, is a decade-old remote code execution vulnerability in WinVerifyTrust Signature Validation that Microsoft is republishing “to inform customers that the EnableCertPaddingCheck is available in all currently supported versions of Windows 10 and Windows 11,” according to the company.
“An attacker who successfully exploited this vulnerability could take complete control of the affected system,” Microsoft added.
“While the current patches don’t directly address this vulnerability, the mitigation is already built into the latest OS versions, and can be enabled manually in the registry if desired,” Walters noted. “Microsoft suggests that developers ensure their signed binaries conform to the new verification standard by eliminating any extraneous information in the WIN_CERTIFICATE structure, and recommends that customers test this change to evaluate its impact in their own environments.”








