Packet filtering is a firewall feature that allows or drops data packets based on simple, pre-defined rules regarding IP addresses, ports, or protocols. Once a type of firewall, packet filtering now provides a fundamental feature of nearly all firewalls and some network equipment (routers, smart switches, etc.). The feature involves key principles, as well as pros and cons, and there are four packet filtering types to be aware of, which determine its best use cases.
Table of Contents
How Packet Filtering Works
Every time two IT assets (e.g., computers, phones, routers, security cameras) need to communicate, they send data packets to each other. Each data packet consists of three components: a header to provide information about the data packet, a payload of data, and a trailer to show the end of the packet.
The sending computer creates the initial data payload, adds header information about the local device, and sends the data packet to the local network router. The local network router and other connecting network devices (router, firewall, etc.) add additional information to the header so that the receiving device can send return message packets accurately.
Packet filtering analyzes the information within each data packet header and compares it against the rules to determine whether to allow or deny the packet. The typical header information that filters packets includes the sender’s IP address, receiver’s IP address, protocol, source port, destination port, and transmission control protocol (TCP) sequence numbers.
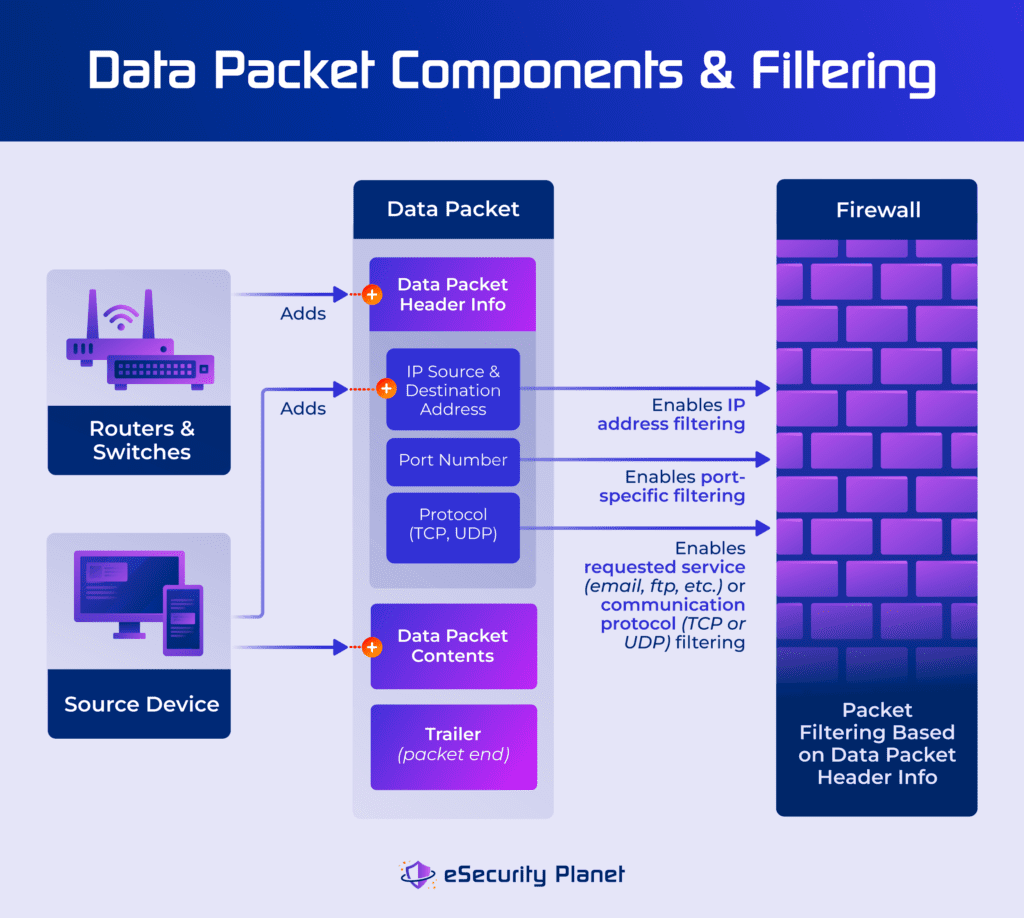
Filtering typically drops denied packets, sometimes with little to no information regarding the violated packet rules in log files. The filter process delivers allowed packets to the destination device or passes the packet on to the next security screening feature. Administrators often apply tailored packet filtering rules to regulate inbound and outbound traffic differently.
The first firewalls created performed packet filtering; inexpensive network firewalls and host firewalls installed on network routers can still focus on packet filtering. However, most vendors also incorporate packet filtering as one of many features incorporated into other types of firewalls, such as next-generation firewalls (NGFW), operating system host firewalls, cloud firewalls, and web application firewalls (WAF).
Principles of Packet Filtering Rules
Packet filtering rules encompass a subset of general firewall rules focused on header information in the data packet. Most rules established by administrators enforce strict Boolean, allowing or denying instructions that enable quick decisions without nuance or subtlety.
The header categories used to make rules include:
- Direction: Informs the filter to apply either inbound or outbound rules for filtering.
- Firewall interface: Applies to the specific physical network interface card receiving data.
- IP address: Provides a destination or source device address (server, workstation, etc.).
- IP flags: Contain TCP protocol connection information, such as connection requests or data packet sequence numbers.
- Network protocol: Defines the standard used for transmission (TCP, UDP, etc.).
- Port number: Directs the destination or source data to specific ports associated with services such as email, FTP, or web browsing (HTTP, HTTPS traffic).
Admins establish specific rules to prevent specific attacks or to enact specific protections. The rules generally apply in a hierarchy, but certain rules, such as “allow all traffic,” may cause conflicts or dangerously nullify other rules. A set of rules composes an overall policy that can be applied to multiple devices performing packet filtering throughout an organization.
For example, the following firewall policy enables a connection to an FTP server if the data header meets all of the following conditions: the traffic source originates outside the network (inbound), the traffic source is a trusted IP address, the traffic source isn’t a blocked IP address, the IP flag requests a connection, and the destination port is port 20.
Access control lists (ACLs) define both trusted and blocked (aka allowlist and denylist or whitelist and blacklist) IP addresses, devices (MAC addresses), and even user groups or users. Rules may consult static ACLs defined by admins or integrate dynamically with active directory, identity and access management (IAM), or privileged access management (PAM) tools.
5 Advantages of Packet Filtering
As a feature, packet filtering offers five key advantages:
- Easy setup: Utilizes understandable options that decrease installation time and that can be implemented without change on many different types and brands of firewalls.
- Fast defense: Enables simple, efficient, and quick allow and drop decisions, which maintains high data throughput for time-sensitive applications and processes.
- Inexpensive deployment: Often already included in the cost of operating systems and firewalls and a basic feature even in the least expensive firewall options.
- Light resources: Uses minimal compute resources (memory, CPU processing, etc.) which frees up resources for more computationally intensive features and capabilities.
- Verifiable performance: Provides easily testable conditions for allow and drop rules that verify minimum security capabilities and baseline risk mitigation.
These cost and performance advantages drive the use of packet filtering for a spectrum of solutions from complex NGFWs to simple routers that include a host firewall.
5 Disadvantages of Packet Filtering
Packet filtering suffers from five significant security disadvantages:
- Clumsy rule lists: Becomes bulky over time as different admins add new rules, which can lead to inadvertent gaps in security or conflicts between old and new rules.
- Incomplete security: Provides narrow security protections that will be vulnerable to more advanced attack methods, such as placing malicious payloads in legitimate traffic.
- Inflexible rules: Misses understanding of context related to users or packet context and can’t adapt to changing circumstances or notice abnormal behavior.
- Misplaced trust: Treats all communication traffic that can pass the basic packet filtering rules, even malicious content, as safe traffic to be trusted.
- Primitive data logging: Uses simple rules that allow or drop packets without details needed for security monitoring, log analysis, or post-breach forensic investigation.
Only a small number of commercial firewalls still focus on packet filtering. Most commercial firewalls package packet filtering alongside advanced features for more dynamic and complex analysis of packets to improve security. Additionally, these robust firewall offerings offer more advanced logging and management consoles that help minimize these weaknesses.
4 Types of Packet Filtering
Packet filtering functions classify as either static, dynamic, stateless, or stateful. All four features can be deployed simultaneously in the same firewall, but only two apply to a rule at the same time. Static rules only pair with stateless packet filtering, and stateful packet filtering rules require dynamic packet filtering. However, stateless filtering can apply to either static or dynamic filtering, and dynamic filtering can pair with either static or dynamic rules.
Static Packet Filtering
Static packet filtering uses fixed and unchangeable rules. Once set by an administrator, these simple rules operate without fail on all packets unless changed again by the administrator.
Examples of static filtering rules include always-closed ports, trusted users in access control lists (ACLs), and always-blocked devices on an IP address denylist (aka blacklist). All firewalls use static filtering capabilities to some degree in established firewall rules to quickly analyze and discard obviously malicious or unwanted data packets.
Dynamic Packet Filtering
Dynamic packet filters adjust rules based on changing conditions, flexible rules, or dynamic protocols. Simple dynamic rules include opening or closing ports based on the time of day or adding bad IP addresses to a deny list after detecting a distributed denial of service (DDoS) attack. Port knocking makes use of more complex dynamic filtering capabilities to drop all packets to a port unless preceded by a pre-defined sequence of packets.
The FTP protocol provides a more complex example and keeps a control port, defined by the protocol as port 21, open and listening for connection attempts. Once an FTP session establishes, the FTP protocol then executes dynamic rules to open port 20 (assigned transmission port) or randomly switch to any port between 60000 and 65535 for the data transmission connection.
Stateless Packet Filtering
Stateless packet filtering relies completely on pre-defined filtering rules to decide whether to allow or drop a packet. These simple rules process quickly to minimize memory and processor usage for the firewall, router, or other solution performing the filtering.
Stateless filtering applies to both static and dynamic filtering rules and treats each packet independently from other packets. The filtering solution retains no data, even information regarding malicious packets previously dropped, as context for future filtering decisions. This type of rule saves memory and maintains high data throughput speeds.
Stateful Packet Filtering
Stateful packet filtering considers packets in the context of established transmission connections during the allow or drop decision-making process. This advancement capitalizes on the sequence information and synchronization-acknowledgement handshake requirements within the transmission control protocol (TCP), but sacrifices speed and consumes more memory and processor time to execute.
Stateful features recognize and drop many DDoS attacks that attempt to use corrupted TCP processes, such as sending replies to non-existent connections to consumer server memory. This feature tracks and automatically blocks or quarantines IP addresses and domains previously involved in attacks or suspicious behavior.
Use Cases for Packet Filtering
Nearly all firewalls and many modern network components use packet filtering. Admins use the feature to execute specific use cases that capitalize on the advantages of packet filtering. Specifically, simple rules enable high-speed filtering to provide initial security for assets and networks or provide simple solutions for network segregation.
High-Speed Data Throughput
Complex security analysis using next-generation firewalls (NGFWs) may cause unacceptable delays for applications, databases, and time-sensitive protocols (videoconferencing, etc.). Implement strict but simple packet filtering to dramatically reduce packets for security analysis and maintain speed. However, also deploy a specialty security solution such as a web application firewall (WAF) or database firewall to block attacks that packet filtering will ignore.
Asset Hardening
Most computer assets (servers, laptops, etc.), cloud resources, firewalls, and network devices with host firewalls require some form of hardening to prevent attacks. Data transmission and protocols require open ports, but devices with specialized roles may automatically block data to most ports to simplify security. For example, an email server won’t need FTP ports open, and an FTP server won’t need email ports open.
Initial Packet Screening
Packet screening provides a rapid first line of defense to drop obviously malicious or unnecessary traffic and reduce the number of packets for deeper, more resource-consuming inspection. For example, packet filtering quickly identifies and drops external IP spoofing attacks that claim to originate from internal network sources when enforcing a rule that no traffic outside the network can claim to be a device from within the network.
Simple Network Segregation
Add inexpensive low-feature packet filtering firewalls to a network to provide simple segregation for subnets or departments. These firewalls prevent communication based on strict and static rules for the IP addresses allowed to send and receive data. However, firewall changes tend to be time-consuming, so some organizations use other solutions for this use case, such as software-defined wide area networking (SD-WAN) or zero trust network access (ZTNA).
Bottom Line: Packet Filtering Is the Start for Firewall Protection
Packet filtering provides fast data packet filtering for networks and devices and is the first critical layer of security. However, many attackers evade packet filtering, so this protection must integrate into a deeper security stack of features or tools to provide robust protection. For most enterprises, packet filtering provides one of many features within a more robust firewall solution tailored to the assets and resources to protect.
To understand more firewall options, learn about the full spectrum of firewall types and when to use them.








