The Microsoft 365 Defender Research Team has revealed several new Linux vulnerabilities collectively dubbed “Nimbuspwn.” Like the Dirty Pipe vulnerability, they only need a local user with low capabilities to elevate privileges, but this time the exploit seems much more specific and focuses on “networkd-dispatcher,” a systemd component that handles connection status changes.
The Nimbuspwn collection of vulnerabilities is recorded as CVE-2022-29799 (Directory Traversal) and CVE-2022-29800 (TOCTOU race conditions). The researchers found that the logic implemented in the networkd-dispatcher component does not sanitize critical elements used to build the script path, which could be exploited to escape the /etc/networkd-dispatcher/ directory.
In addition, the Microsoft researchers discovered a dangerous delay (hence the TOCTOU, time-of-check-time-of-use) between the scripts being discovered by the component and the time they’re actually run. Hackers could exploit such intervals to replace the scripts with their own.
The researchers concluded attackers might use these vulnerabilities to send an arbitrary signal. It’s possible only under specific conditions, but they can make networkd-dispatcher execute some scripts blindly and as root. Attackers may use it to perform additional tasks such as distributing malware or deploying ransomware.
See the Top 10 Open Source Vulnerability Assessment Tools
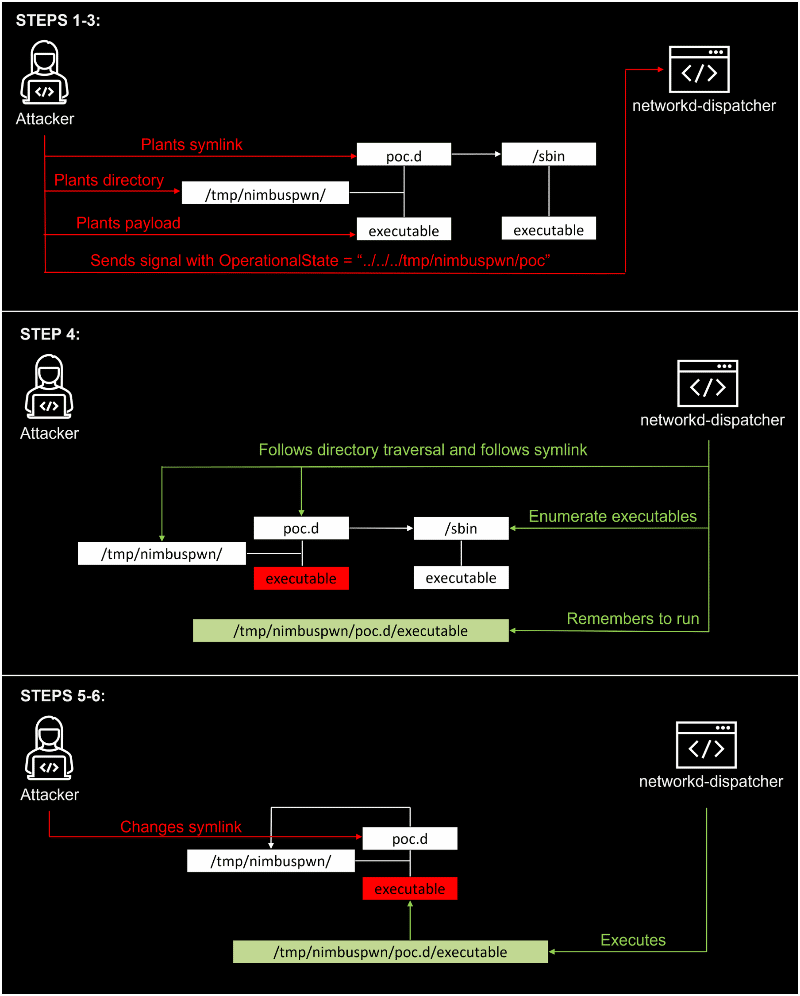
Nimbuspwn Exploit Steps
The Microsoft researchers described all the steps in a very explanatory schema (image below) that shows how attackers could chain the exploits to divert networkd-dispatcher and gain root privileges:
Daemons and D-Bus
To understand how Nimbuspwn works, you need a basic overview of the Linux components involved, like daemons and buses.
Daemons are utility programs that run in the background to monitor and maintain some subsystems. They execute very specific actions at predefined times or they trigger for some events. Every time you see a process that ends with the letter d, it’s a daemon. You can test it with the ps command or by using built-in utilities such as top.
So “networkd” means “network daemon,” and researchers were intrigued by the fact that the networkd-dispatcher daemon runs at boot time with root privileges on the system. If you have the component, you can verify that with the following command in the terminal:
ps -U root -u root u | grep networkd-dispatcher
D-Bus stands for “Desktop Bus” and allows communications between processes. This mechanism is developed by the freedesktop project and provides the necessary abstraction (or “software bus”, a model that facilitates communications between software modules) to guarantee that all processes connected to the bus can communicate with each other efficiently.
Linux systems (e.g., desktop environments) use D-Bus to instantiate multiple buses, including a single system bus available to all users and processes of the system, that provide access to system services.
Because system services owned by root are listening and responding to the system bus, it’s an attractive target for hackers.
Owning the org.freedesktop.network1 bus
To achieve their exploit, researchers had to own the org.freedesktop.network1 bus name under a privileged service:
Such a bus name is normally owned by the service systemd-networkd, but hackers can change that if they manage to get a rogue D-Bus.
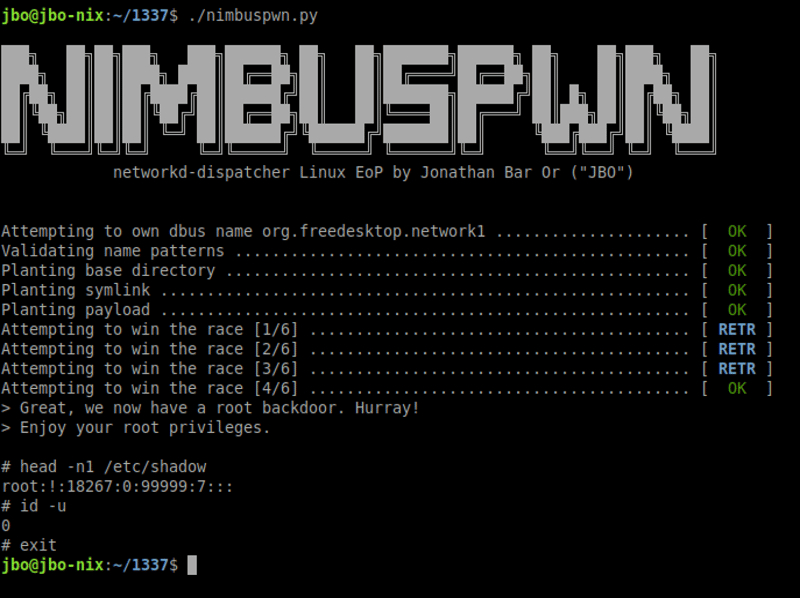
These vulnerabilities may seem a bit hard to chain and exploit, and the researchers needed to plant multiple files and make several attempts to win the TOCTOU race condition. However, they delivered a backdoor using Nimbuspwn, which allowed them to skip the exploit when they wanted to use root commands again.
Any vulnerability that allows root privilege escalation should be taken seriously, regardless of difficulty to exploit.
See the Top Vulnerability Management Tools
How to Protect Against Nimbuspwn
At the time of writing, there’s no official list of affected environments and distributions but the Microsoft Research Team mentioned Linux Mint, a light distribution based on Ubuntu, a Debian-based operating system and possibly the most popular Linux distro.
A quick search might help you identify all distributions that could have the vulnerable component. Clayton Craft, the maintainer of networkd-dispatcher, has patched the vulnerabilities, so if you have the component enabled, you are strongly encouraged to update.
However, and it’s good news in this case, the component might not be installed by default in all distributions. You might check it manually but there’s already a free open source detector available on GitHub that will check if the process is currently running on your system.
More generally, Nimbuspwn shows how important it is to monitor all endpoints, including Linux devices. There’s a growing number of vulnerabilities and exploits in Linux systems and components, and it won’t stop soon, as Linux is prevalent in many cloud-based architectures and servers.
To me, the major problem with such flaws is that they’re often underestimated, mainly because they require a local user, so hackers need to be already in a machine to exploit them. It’s not a valid reason to neglect the risk, as lateral movements and privilege escalations are now part of the hacker’s routine.
You can’t rely on only one layer of security, and companies need to prepare for post-exploitation techniques.
Read next: Top Endpoint Detection & Response (EDR) Solutions








