Microsoft is shutting a couple of security holes, including one that has been a favored target of attackers for years and another that the enterprise software giant recently learned could be exploited to install a malicious package.
At the same time, the federal government is now adding another Microsoft flaw to its list of known vulnerabilities, giving federal agencies until Feb. 18 to patch a bug in all unpatched versions of Windows 10 and urging private and commercial organizations to remediate all flaws listed in its Known Exploited Vulnerabilities Catalog.
In its alert, the Cybersecurity and Infrastructure Security Agency (CISA) said the decision to add the flaw – tracked as CVE-2022-21882 – was “based on evidence that threat actors are actively exploiting the vulnerabilities listed in the table below. These types of vulnerabilities are a frequent attack vector for malicious cyber actors of all types and pose significant risk to the federal enterprise.”
“It appears CISA added this as due diligence, rather than because the attack is a high threat,” Mike Parkin, an engineer at cybersecurity vendor Vulcan Cyber, told eSecurity Planet. “Microsoft’s explanation indicates that the attack requires local access and is of high complexity, both of which reduce the likelihood of it being widely used in the wild. Patches are available and they should be deployed as part of any organization’s standard maintenance procedure.”
Also read: Best Patch Management Software
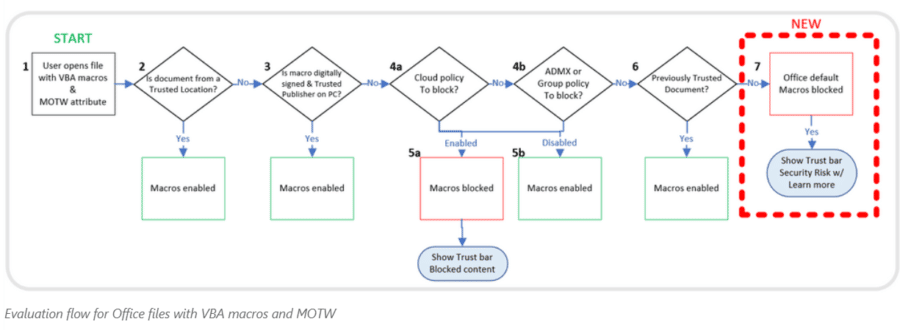
Disabling VBA Macros
One of the moves Microsoft officials announced this week is the plan to block Visual Basic for Applications (VBA) macros by default in a range of Office applications. The change is directed at VBA macros obtained from the internet. Users will no longer be able to enable certain content by a simple click of a button. If they try, a message bar will appear directing them to learn more about the situation.
“The default is more secure and is expected to keep more users safe including home users and information workers in managed organizations,” Kellie Eickmeyer, a principal program manager at Microsoft, wrote in a blog post. “For years Microsoft Office has shipped powerful automation capabilities called active content, the most common kind are macros. While we provided a notification bar to warn users about these macros, users could still decide to enable the macros by clicking a button.”
Threat actors can send macros in Office files to users who could easily enable them, causing malicious payloads to be delivered.
“The impact can be severe including malware, compromised identity, data loss, and remote access,” Eickmeyer wrote.
The change is part of a recent pattern by Microsoft, which has begun taking security into its own hands, as users can be slow to install critical patches (see Microsoft Makes Exchange Server Patches Less Optional).
Security By Default
The change will begin rolling out in Version 2203, starting with the preview of Current Channel in early April and later in other update channels, such as Current Channel, Monthly Enterprise Channel and Semi-Annual Enterprise Channel. It will impact Office on devices that are running Windows and affects Access, Excel, PowerPoint, Word and Visio.
Security professionals applauded Microsoft’s decision.
“One of the important but underappreciated aspects of cybersecurity is that defaults matter – and sometimes matter a lot,” Oliver Tavakoli, CTO at cybersecurity firm Vectra, told eSecurity Planet. “Seemingly 50-50 decisions made by product managers at application and platform providers can expose their customers to extraordinary risk. As the example of VBA macros demonstrates, once such a choice has been made, it’s a difficult and lengthy process to change the default to something more secure as the fear of breaking things creates a form of institutional paralysis.”
The equation is a simple one, Tavakoli said: “Leave features which may have security implications off by default and let customers choose whether the benefit of the feature outweighs the security risk of having it on.”
Overdue Security Change
Ray Kelly, a Fellow at NTT Application Security, told eSecurity Planet that “VBA macros have been a target for hackers for over two decades, easy to code and run with the current users’ permissions. Blocking macros by default is a good move at the cost of inconvenience and can potentially protect a user from ransomware or data loss.”
Jon Gaines, senior application security consultant at nVisium, noted that for red teams at many organizations, macros have been a useful tool in security training. He also dinged Microsoft for taking too long to disable VBA macros.
“Macros have been a threat to Office users for many years,” Gaines told eSecurity Planet. “Good on [Microsoft] for finally implementing this, but I don’t think it gets end users out of danger completely. It’s important to note that this only affects Office files downloaded from the internet, which have already had a warning if it contains a macro at this time. However, making it more than one click to execute the macros is a great step.”
Also read: Top Secure Email Gateway Solutions
Temporary Shutdown for MSIX
Late last week, Microsoft also announced it was temporarily turning off the MSIX ms-appinstaller protocol handler in its Windows AppX Installer after learning that a security flaw was being exploited by cybercriminals to deliver such malware as Emotet (a Trojan spread via emails), TrickBot (a banking Trojan) and Bazaloader (which can result in stolen data or ransomware).
In a blog post, Dian Hartono, a program manager at Microsoft, wrote that the vendor learned an attacker could spoof App Installer to install a package that a user didn’t want to install. The vulnerability is being tracked as CVE-2021-43890.
“We are actively working to address this vulnerability,” Hartono wrote. “For now, we have disabled the ms-appinstaller scheme (protocol). This means that App Installer will not be able to install an app directly from a web server. Instead, users will need to first download the app to their device, and then install the package with App Installer. This may increase the download size for some packages.”
With the MSIX app package, some legacy Windows applications can get “modern packaging and deployment features,” giving enterprises a way to ensure their applications are up-to-date and ensure an easy installation process.
“The ms-appinstaller protocol handler was introduced to enable users to seamlessly install an application by simply clicking a link on a website,” Hartono wrote. “What this protocol handler provides is a way for users to install an app without needing to download the entire MSIX package. This experience is popular, and we are thrilled that it has been adopted by so many people today.”
The protocol will be re-enabled after ensuring it is secure. Microsoft is considering bringing in a group policy that will enable IT administrators to re-enable the protocol and control its use inside their organizations.
Read next: Top Vulnerability Management Tools








