Palo Alto Networks says current zero trust solutions don’t go far enough, so today the cybersecurity leader urged the industry to transition to what it’s calling Zero Trust Network Access 2.0 (ZTNA 2.0), an approach that involves continuously reassessing user trust and network traffic.
The massive shift to remote work brought on by the pandemic has revealed weaknesses in access management and insufficient controls over uncontrolled devices and networks, Palo Alto says. While replacing VPN access with zero trust has been a start, the network security vendor thinks that’s just the beginning, and it’s offering up its new Prisma Access product as a model.
Zero trust revolves around the principle that nothing on a network should be trusted and access restricted to only the resources necessary. It accomplishes this through network segmentation that prevents lateral movement within a network, offering layer 7 threat deterrence, and streamlining granular “least access” rules. A zero-trust architecture, when implemented correctly, leads to higher levels of security while also reducing security complexity and operational overhead.
Even though the zero trust strategy has been a step up from existing VPN applications, ZTNA 1.0 has some shortcomings that Palo Alto Networks says need to be addressed and rectified.
Also read: Zero Trust Can’t Protect Everything. Here’s What You Need to Watch.
The Shortcomings of ZTNA 1.0
Palo Alto’s main concerns about current zero trust implementations revolve around the lack of visibility, least privilege access, access controls, and an “allow and ignore” model that confirms but doesn’t authenticate trust frequently, so the principles of zero trust are not being imposed correctly. Here are the are the drawbacks the vendor sees in the current ZTNA 1.0 approach:
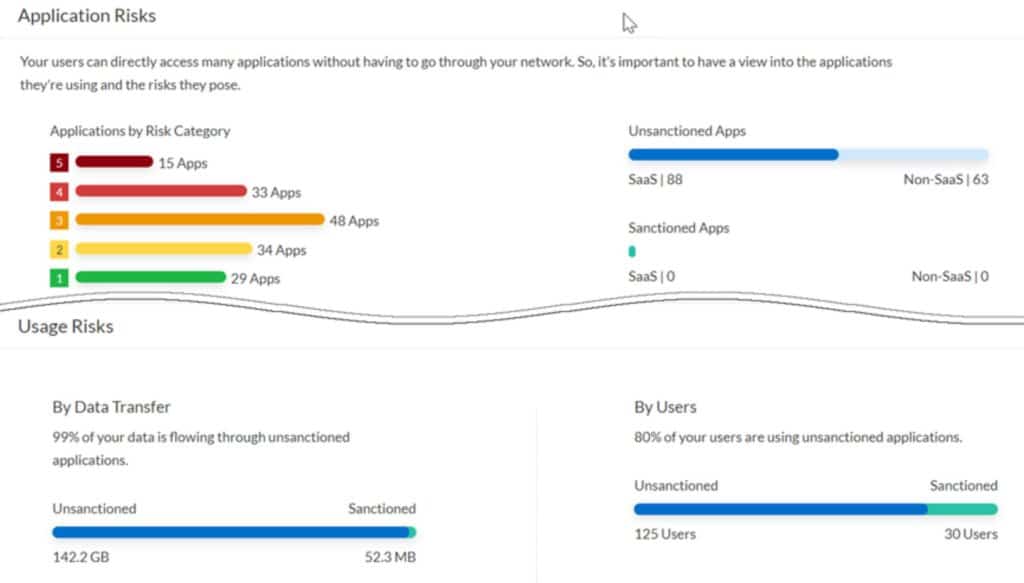
- “Allow and ignore” model: When application access is granted, that communication is typically trusted from that moment onwards. This means the user and the application will always act in a very trusted manner. The “allow and ignore” model is not suitable for current security challenges, and definitely not for zero trust because many breaches occur on the activity, which is given a free pass, and this model cannot prevent them.
- Lack of data security: There is a diminished amount of visibility and control over sensitive information by current solutions. Organizations are dependent on a variety of solutions to safeguard sensitive data across SaaS and internet applications. This leads to a siloed approach that contributes to complexity and makes the organization vulnerable to data exfiltration by malicious hackers.
- Least privilege: The ZTNA 1.0 solutions are there to control access with the help of coarse-grained access controls. They treat applications as network control at layer 3-4, violating the principle of least privilege and giving users access to more than what they require.
- Lack of security inspections: Current solutions assume that traffic is secure and are unable to stop lateral movement once a user is allowed access to an application. The solutions make the organization vulnerable to data breaches when they grant access without ongoing visibility or traffic control.
- Different platforms for on-premises and cloud applications: Current ZTNA solutions are built for either cloud applications or on-premises applications, not both. The new approach should be all-inclusive and must take everything under consideration to reduce complications and the risk of data breaches, Palo Alto says.
John Grady, a senior analyst at ESG, said in an accompanying report that “once access is granted in ZTNA 1.0 solutions, the connection is implicitly trusted forever, allowing a handy exploit route for sophisticated threats and/or malicious actions and behavior. It is time to embrace a new approach to ZTNA, one that has been designed from the ground up to meet the specific challenges of modern applications, threats, and a hybrid workforce.”
Also read: Best Zero Trust Security Solutions
Palo Alto Positions Prisma Access as ZTNA 2.0
Palo Alto Networks is positioning its Prisma Access product as a unified ZTNA 2.0 security solution. The vendor says Prisma addresses the drawbacks of ZTNA 1.0 with a number of key features:
- Least Privilege Access: This is accomplished by assessing applications at Layer 7, allowing for accurate access control at the application and sub-application levels, separate from the rest of network constructs such as IP and port numbers.
- Constant Trust Verification: Once permission is given, trust is constantly reevaluated based on changes in device posture, user behavior, and application behavior.
- Constant Security Inspection: Deep and continuous inspection of all traffic, including permitted connections and protection against all threats, including zero-day threats.
- Security of All Data: Using a single DLP policy, Palo Alto says the solution provides consistent data control throughout all enterprise applications, including private apps and SaaS.
- Protection for All Apps: Protecting all enterprise applications, including cloud-native apps, legacy private apps, and SaaS apps. This includes applications that use dynamic ports and applications that rely on server-initiated links.
Also read: CNAP Platforms: The Next Evolution of Cloud Security
A Necessary Upgrade?
Palo Alto Networks says Prisma Access is the first solution that meets the ZTNA 2.0 demands of least privilege access, zero trust capabilities, continuous security and trust verification based on user and app behavior, and consistent data control across all applications. To ensure consistently high performance and user experience, Prisma Access offers additional advantages of a management model and a unified platform that secures data regardless of location, while easing demands on security teams.
Palo Alto’s leadership will likely give the product traction in a competitive market, but the cybersecurity space is loaded with innovation so expect challengers to make a case too.
Read next: Best Identity and Access Management (IAM) Solutions








