A distributed denial-of-service (DDoS) attack is a type of cyberattack in which multiple compromised systems are used to target a single system, usually with the goal of overwhelming its resources and making it unavailable to its users. DDoS attacks can be launched from anywhere in the world using any type of device that can be compromised, including laptops, desktops, routers, smartphones, and even internet-connected appliances.
Table of Contents
Intent, Prevalence, and Severity of DDoS Attacks
DDoS perpetrators can range from single individuals working alone to organized criminal groups and even foreign governments. The intention of a DDoS attack can vary but often includes causing financial damage to a targeted organization or simply causing disruption and chaos.
DDoS attacks have become increasingly common in recent years, with numerous high-profile websites and online services falling victim to successful attacks. For example, in 2016, the website of security journalist Brian Krebs was hit with the largest DDoS attack ever recorded at the time, with an estimated peak of 665 gigabits per second (Gbps) of traffic.
Recent attacks have been of much greater magnitude. For example, in February 2020, Amazon thwarted a DDoS attack that peaked at 2.3 terabits per second. And in late 2021, Russia’s Yandex was also hit by a DDoS attack that flooded it with millions of web page requests at a rate of 21.8 million requests per second, among other record attacks.
Over the past year, DDoS attacks have been politically motivated, with many linked to the Russia-Ukraine conflict. According to Kaspersky, some of the organizations targeted by massive DDoS attacks in the first half of 2022 include NATO, Israel’s Airport Authority, the U.K.’s Port of London Authority, the Turkish ministry of defense, the Czech government and public transportation websites, Ukraine’s government websites, and even major U.S. airports.
The severity of DDoS attacks can vary, but they can have significant consequences for targeted organizations. In addition to the potential loss of revenue and damage to reputation, victims may also face fines or penalties if they are unable to fulfill their obligations due to an attack. According to Ponemon, the average DDoS attack costs an average of $22,000 a minute, with the typical attack lasting just under an hour, for an average cost of more than $1 million. That damage will vary considerably by company size.
See also: How to Stop DDoS Attacks in Three Stages
How Do Distributed Denial-of-service Attacks Work?
DDoS attacks use a network of compromised computers and devices, known as a botnet, to flood the targeted system with overwhelming amounts of traffic. By sending multiple requests simultaneously from numerous sources, the attacker can overload the target’s resources and prevent legitimate users from accessing it.
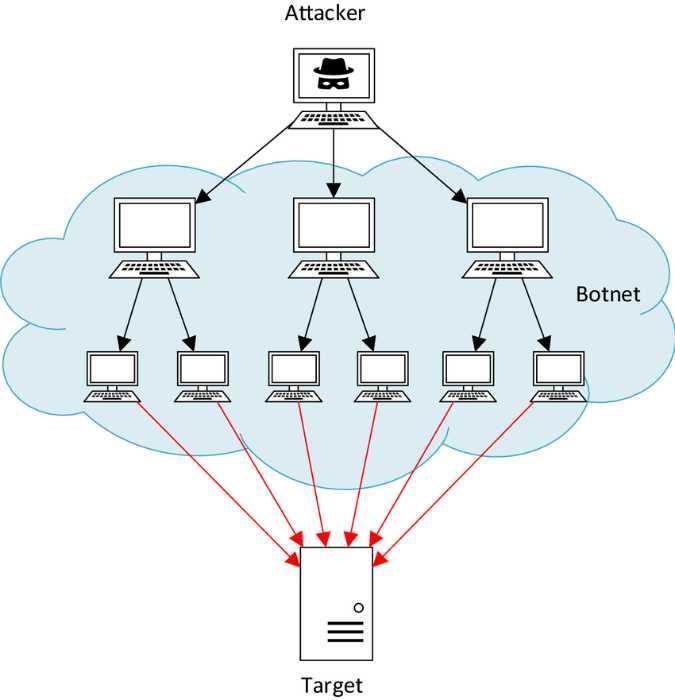
How do attackers create a botnet?
Attackers typically infect devices with malware that gives them hidden control. Once they have control of enough devices, they can instruct them to all send traffic to the same target at the same time, creating a DDoS attack.
However, the commoditization of DDoS attacks has made them more prevalent and more damaging. There are now services that allow anyone to launch a DDoS attack without having to create their own botnet. These services, known as DDoS-for-hire or DDoS as a service, provide attackers with the capability to launch powerful DDoS attacks without any technical expertise.
For example, a 33-year-old man in Illinois was recently sentenced to two years in prison for running a subscription-based DDoS attack service.
Categories and types of DDoS attacks
There are three primary categories of DDoS attacks: volumetric, protocol, and application.
Volumetric
Volumetric attacks are the most common type of DDoS attack. They work by flooding the target with traffic until it can no longer cope with the volume of incoming requests and becomes overwhelmed. There are several volumetric attacks, including UDP flood attacks, CharGEN flood, ICMP (Ping) flood, ICMP fragmentation flood, and misused application attacks.
Protocol
Protocol attacks exploit vulnerabilities in the protocols themselves to cause a DoS condition. The most common type of protocol attack is the SYN flood attack. Other protocol attacks include TCP flood attacks, session attacks, slowloris, ping of death, smurf attacks, fraggle attacks, Low Orbit Ion Cannon (LOIC), and High Orbit Ion Cannon (HOIC).
Application
Application attacks target vulnerabilities in specific applications or services running on a server. The most common type of application attack is the HTTP Flood attack.
Other types of DDoS attacks
Other types of DDoS attacks don’t fall neatly into one of the three primary categories. These include:
- Regular Expression DoS (ReDoS): ReDoS attacks target the regular expressions used by a particular application to process data. By sending specially crafted input that takes a long time for the application’s regular expression to process, the attacker can overload and crash the server or slow it down significantly.
- Advanced Persistent DoS (APDoS): APDoS attacks are similar to DDoS attacks, but they are longer and more sophisticated in nature. The attacker will launch a relatively small attack to gain access to the target’s resources and then use that foothold to continuously launch attacks and exhaust the target’s resources over a long period.
- Multi-Vector Attacks: A multi-vector attack uses multiple types of attacks, such as volumetric and protocol attacks, simultaneously to overwhelm the target’s resources from multiple angles.
- Zero-Day DDoS Attacks: These attacks exploit previously unknown vulnerabilities in a system or application, making them particularly difficult to defend against.
Read more: Complete Guide to the Types of DDoS Attacks
Identifying DDoS attacks
It can be difficult to distinguish between a sudden spike in traffic from legitimate users and a DDoS attack. However, there are some red flags to look for.
- An unusually high amount of traffic coming from a single source or IP address
- Traffic coming from multiple sources at unusual times or patterns
- Requests that seem out of place or malformed
- A sudden decrease in website or network performance
- Slowness or unresponsiveness in specific services or applications
- Inability to access certain websites or services
What if it is genuine traffic?
It could be a sudden surge in popularity or a viral marketing campaign. In these cases, it’s crucial to have proper network monitoring and scaling capabilities in place to ensure your infrastructure can handle the increased traffic without impacting performance.
How Can You Mitigate DDoS Attacks?
Prevention of DDoS attacks hinges on IT security teams adopting basic preparation, reaction, and recovery principles.
Preparing for DDoS Attacks
There are various actions and best practices that security teams can take to prepare for and prevent DDoS attacks. These include:
- Deploy Firewalls and Intrusion Detection Systems (IDS): Next-generation firewalls can block unusual or suspicious traffic, while intrusion detection and prevention systems can identify and alert on potential attacks.
- Use Secure Protocols: Secure protocols such as Secure Shell (SSH) and Transport Layer Security (TLS) can help prevent protocol attacks.
- Keep Software and Systems up to Date: Regularly patching and updating software and operating systems helps mitigate vulnerabilities attackers can exploit.
- Network Segmentation: Segmenting your network can limit the impact of a successful attack and make it easier to isolate and mitigate the attack.
- Restrict Access: Only allowing authorized users to access certain services and applications can limit the potential attack surface, a principle of zero trust architectures.
- Use Load Balancers: Load balancers can distribute traffic evenly across multiple servers and prevent a single server from being overwhelmed by an attack.
- Consider Infrastructure Overprovisioning: Having extra bandwidth and resources available can help maintain performance in the event of a DDoS attack.
- Consider Infrastructure Hardening: By making adjustments to how settings are configured, removing any unnecessary features and adding security-enhancing optional features, servers, gateways, firewalls, and other IT infrastructure can be made much more secure against attacks.
- Enable Anti-DDoS Features: Many network devices and services offer anti-DDoS features, such as rate limiting and filtering, which can help mitigate attacks.
- Purchase Extra DDoS Protection: Some service providers offer DDoS protection as an additional service. If you’re looking for protection against DDoS attacks, various vendors offer software and hardware solutions and services that can help.
- Create a DDoS Playbook: Developing an incident response plan for what to do in the event of a DDoS attack can help ensure a fast and effective response. This includes identifying key individuals and roles, establishing communication channels, documenting mitigation procedures, and conducting regular testing and drills.
- Continuous DDoS Monitoring: Regularly monitoring network performance, traffic, and logs can help identify potential attacks in their early stages and allow for a faster response.
Responding to DDoS Attacks
In the event of a DDoS attack, it’s important to quickly identify and confirm the attack, gather information about its impact and severity, and contain and mitigate the attack. Some specific responses you can take include:
- Notify Your ISP or a Third-Party DDoS Mitigation Service: Your internet service provider (ISP) or a third-party DDoS mitigation service may be able to help redirect and filter malicious traffic.
- Attack Characterization: Gathering information about the attack, including what type of attack it is and what systems or services are being targeted, can help inform mitigation efforts.
- Attack Traceback: Tracing the attack back to its source can help identify the attacker and potentially gather evidence for legal action.
- Attack Tolerance and Mitigation: Implementing steps to mitigate the attack, such as rate limiting or filtering, can help minimize its impact and restore services.
Recovering from DDoS Attacks
Once a DDoS attack has been mitigated, it’s essential to review what happened and what could be done differently in the future to prevent or better handle similar attacks.
This could include implementing any necessary security updates, adjusting network and infrastructure configurations, revisiting your DDoS playbook, and conducting employee training. It’s also important to monitor for any lingering effects and continue monitoring for future attacks.
DDoS Software Solutions & Services
There are various software solutions and services designed to protect against DDoS attacks. These can include network devices with anti-DDoS features, firewalls and intrusion prevention systems, and specialized DDoS protection software and services. It’s important to research and consider what solution is best carefully.
When shopping for a DDoS solution, we recommend that potential solutions include the following abilities:
- Filter and monitor incoming web traffic.
- Handle high levels of malicious traffic.
- Regulate traffic flow or set a minimum/maximum level for traffic.
- Provide reporting and analytics.
- Be easy to set up and configure.
- Come with a traffic management dashboard.
- Have a service-level agreement (SLA) with guaranteed uptime and support.
- Offer integrations with infrastructure as code (IaS) software and other application programming interfaces (APIs).
- Offer continual updates and technical support.
Some of the leading DDoS software & services vendors include:
- Akamai
- Imperva
- Radware
- Cloudflare
- Neustar
- NetScout
- Ribbon
- Amazon Web Services
The prevalence and severity of DDoS attacks continues to grow, making it vital for individuals and organizations to understand what DDoS attacks are and how they can protect against them. While there is no one-size-fits-all solution, implementing a combination of prevention measures and a response plan can help defend against these disruptive attacks.








