Volt Typhoon, a notorious cyber group linked to the People’s Republic of China, has expanded its operations beyond illegal access and data theft. This state-backed hacker collective, also known as Vanguard Panda, BRONZE SILHOUETTE, Dev-0391, UNC3236, Voltzite, and Insidious Taurus, has infiltrated the networks of critical infrastructure sectors ranging from aviation to maritime in a strategic bid for future catastrophic cyberattacks.
With a joint advisory from the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and Federal Bureau of Investigation (FBI) published on February 7, 2024, exposing their tactics, international collaboration sponsored by these agencies emphasizes the importance of worldwide vigilance against the harmful cyberthreats targeting key systems.
Table of Contents
Timeline of Volt Typhoon’s Cyber Intrusions
In 2021, BRONZE SILHOUETTE, later dubbed “Volt Typhoon” by Microsoft, targeted U.S. government and defense institutions for intelligence gathering. Using web shells, they attacked weak internet servers, specifically a Houston port. Attacks on telecom corporations, government institutions, and utilities then followed in a predictable pattern.
In November 2021, the FBI disclosed a FatPipe VPN exploit that enabled backdoor access via web shells. Despite initial suspicions, encrypted communications with specific keys linked the attacks to the previous ones, indicating an organized effort.
A year after the Houston port incident, Guam’s two major telecoms faced overlapping cyberattacks. Guam’s geopolitical significance makes telecoms key targets; compromising them results in widespread access to their crucial infrastructure.
Volt Typhoon struck again on several U.S. sectors in 2023, which raised concerns about its main goal: a widespread disruption. Microsoft then dubbed the group “Volt Typhoon,” describing its meticulous approach to identifying and exploiting vulnerabilities.
In February 2024, the CISA, NSA, and FBI warned of PRC cyber actors pre-positioning themselves again to disrupt the IT networks of U.S. critical infrastructure in the case of a major U.S. crisis.
How Volt Typhoon Attacks
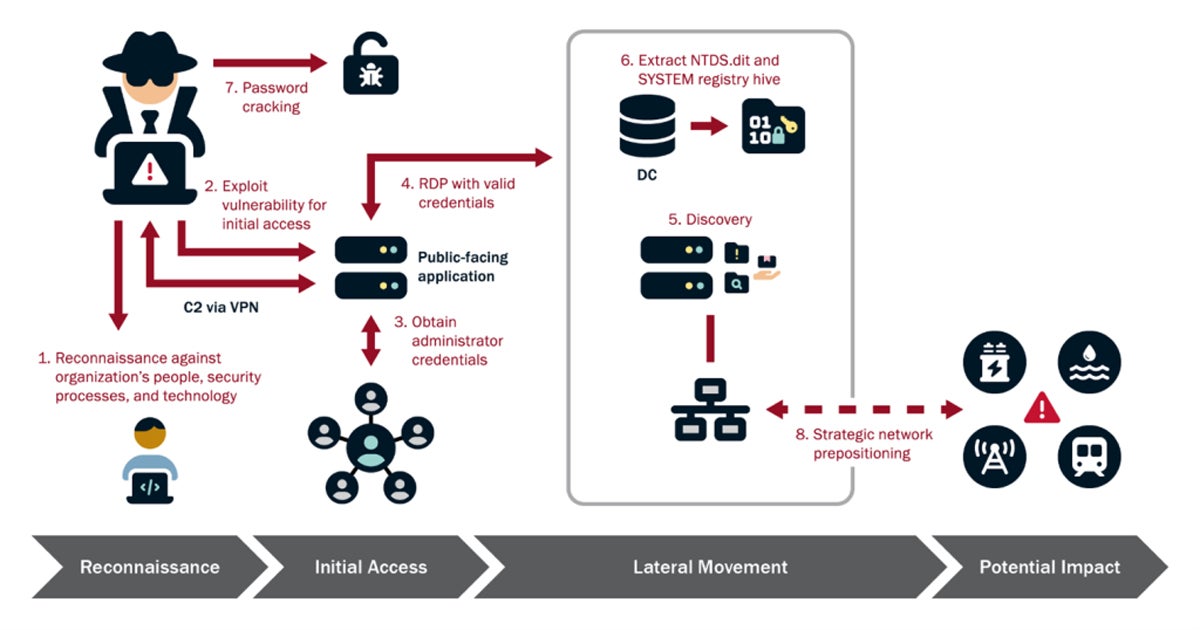
The Cybersecurity and Infrastructure Security Agency (CISA) has revealed the complexities of Volt Typhoon’s cyberattacks, listing their typical activities into four steps: reconnaissance, initial access, lateral movement, and potential impact.
Reconnaissance
Reconnaissance is the starting point of Volt Typhoon’s cyber campaign, characterized by thorough planning and data collection. They use advanced tools and techniques to scan the internet for vulnerable devices within their target networks, leveraging resources such as Shodan, a search engine specifically designed for locating and accessing Internet-connected devices and services, to identify potential entry points.
It’s an in-depth assessment of the target’s network infrastructure, with a focus on discovering vulnerable devices such as routers and VPNs. Volt Typhoon prepares for future stages of operation by gathering vital knowledge on network security and topology, system configurations, and potential vulnerabilities. This enables them to adapt their approach, identifying weak places in the target’s defenses and increasing the impact of their infiltration attempts.
Initial Access
Armed with extensive reconnaissance data, Volt Typhoon moves on to the initial access step, exploiting identified vulnerabilities to penetrate the target network’s perimeter. This phase gains them critical access to the target environment, made possible by exploiting known or zero-day vulnerabilities in public-facing network appliances. They exploit routers, VPNs, and other network devices, using them as entry points for Volt Typhoon to get a foothold in the network.
Once inside, they quickly establish their presence, frequently using backdoors or other persistence techniques to keep access and avoid discovery. This gives Volt Typhoon what they need to move on to the next phase of their operation, allowing them to enter important systems and infrastructure with ease.
Lateral Movement
Following initial access, Volt Typhoon begins the phase of lateral movement within the target network. Using stolen credentials obtained during reconnaissance or existing vulnerabilities, they browse the network’s interconnected systems, gradually expanding their reach and obtaining access to other key assets.
This phase involves a systematic and methodical approach to escalating privileges, maneuvering discreetly, and blending into normal network traffic to escape detection. Volt Typhoon’s goal in moving laterally throughout the network is to widen their foothold, deepen their penetration, and optimize their capacity to influence and corrupt vital infrastructure components.
Potential Impact
The culmination of Volt Typhoon’s intricate tactics might have a tremendous impact on the targeted systems and infrastructure. With increased network access and control, they have the capacity to alter operational technology (OT) assets and disrupt critical services.
They strengthen their control and avoid discovery by stealthily gathering security event logs and corrupting Active Directory data, escalating the severity of their damage. Their acts might cause widespread disruption of key services like electricity grids and water treatment facilities, as well as compromise sensitive data and undermine national security.
Living off the Land Techniques
Volt Typhoon uses living-off-the-land (LotL) tactics, leveraging valid system tools to maintain long-term, undetected access to the target environment. They execute harmful acts using built-in operating system functions, such as Windows, rather than traditional malware. They conceal their actions by combining them with normal network traffic using native system utilities like Windows Management Instrumentation (WMI) and command-line functions.
Using “living off the land binaries,” they conceal their operations within ordinary system characteristics, bypassing simple endpoint security protections. Volt Typhoon may undertake operations discreetly without the need for custom tools, further gaining stealth and persistence.
LotL emerged in 2018 and became a popular strategy among malicious actors due to its effectiveness in ensuring covert persistence and discovery evasion. Analysts and security software frequently struggle to spot malicious activity disguised as normal ones, complicating intrusion detection and mitigation efforts.
LotL tactics are not only used by nation-state entities such as Volt Typhoon. It’s also used by ransomware actors that want to propagate malware using remote monitoring and management tools. As attackers continue to develop, LotL is projected to expand further. This could offer substantial difficulties to cybersecurity experts in the coming years.
Mitigations
Mickey Bresman, CEO of the Active Directory security and recovery platform Semperis, emphasizes the significance of adopting an “assume breach mindset” and establishing strong mitigations to improve the resilience of important systems. He also points out that the ease and frequency with which Volt Typhoon hackers infiltrate and exit networks should raise alarms.
To combat the network security threats brought by Volt Typhoon, Bresman proposes several critical mitigations:
- Assess critical systems: Organizations must identify and prioritize critical systems, including infrastructure such as Active Directory (AD), which is a common target for cyberattacks.
- Assume breach mindset: If one compromised environment or malware is detected, there are certainly more to come.
- Monitor unauthorized changes: Set up real-time monitoring of AD infrastructure, particularly elevated network accounts and groups.
- Perform clean recovery: Back up systems on a regular basis and carry out clean recoveries after any security issues. This entails doing extensive forensics and inspections to guarantee that the environment is clear of compromise.
- Conduct forensics investigation: Save the compromised environment for a thorough forensics investigation to determine the scope of the breach and any vulnerabilities.
From Semperis’ incident response experiences, state-sponsored actors from nations like China and Russia are relentless in their attempts to compromise networks. There’s a growing threat caused by cyber adversaries such as Volt Typhoon. Despite countless warnings over the years, malicious actors have operated with no consequence, emphasizing that organizations should operate under the assumption that their security will be compromised.
The intricate techniques deployed by Volt Typhoon serve as an alarming indicator of the ongoing cybersecurity dangers to our network infrastructures. To keep ahead of harmful actors, stakeholders must remain watchful and constantly improve their security measures while enhancing their threat intelligence.
Want to strengthen your organization’s digital defenses? Read the common types of network security solutions next.








